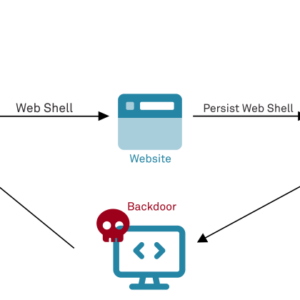
Exploiting HTTP file servers: Sounds like something out of a cyberpunk thriller, right? But the reality is far more mundane—and […]
Tag: Data Exfiltration
Kematian Stealer Abuses PowerShell A Deep Dive
Kematian Stealer abuses PowerShell, leveraging its scripting capabilities for malicious purposes. This sophisticated malware utilizes PowerShell’s inherent flexibility to bypass […]
Beware of Weaponized Notezilla
Beware of Weaponized Notezilla: This seemingly innocent note-taking app harbors a dark side. Its ease of use and seemingly harmless […]
North Korean Hackers HappyDoor Malware A Deep Dive
North Korean hackers HappyDoor malware: The name alone conjures images of shadowy figures hunched over glowing screens, orchestrating digital heists. […]
Fickle Stealer Windows Data Theft Exposed
Fickle stealer windows data theft – Fickle Stealer: Windows Data Theft Exposed. This sneaky malware is silently stealing sensitive information […]
Beware of Weaponized PDFs A Digital Danger
Beware of weaponized PDFs: that seemingly innocent document on your screen could be a Trojan horse, silently delivering malware, stealing […]
Hackers Abuse Windows Search Sneaky Attacks
Hackers abuse Windows Search; it’s not the sci-fi thriller you think, but a very real threat. They’re exploiting vulnerabilities in […]