Microsoft employees data exposed – the headline alone sends shivers down the spine. This isn’t just another tech breach; it’s a stark reminder that even the giants of the industry aren’t immune to the ever-evolving threat landscape. We’re peeling back the layers to uncover what happened, how it happened, and what it means for both Microsoft and its employees. Get ready for a rollercoaster ride through the world of data breaches, security vulnerabilities, and the aftermath of a digital heist.
This incident reveals a critical vulnerability in Microsoft’s internal systems, highlighting the ongoing battle between sophisticated cyberattacks and robust security measures. We’ll explore the types of sensitive data potentially compromised, the potential impact on employees, and the steps Microsoft took (or didn’t take) to mitigate the damage. The story unfolds with a timeline of events, a breakdown of the root cause, and a look at how this incident compares to similar breaches across the industry. Prepare for a detailed analysis, focusing on the impact on employee trust, morale, and the potential legal and reputational fallout for Microsoft.
The Nature of the Data Breach: Microsoft Employees Data Exposed
Source: securitynewspaper.com
The recent Microsoft employee data exposure highlights the ever-present threat of cyberattacks, even within the most secure organizations. While Microsoft has addressed the issue, understanding the nature of the breach is crucial for both employees and the broader tech community. This analysis delves into the specifics of the incident, aiming to provide a clear picture of what transpired.
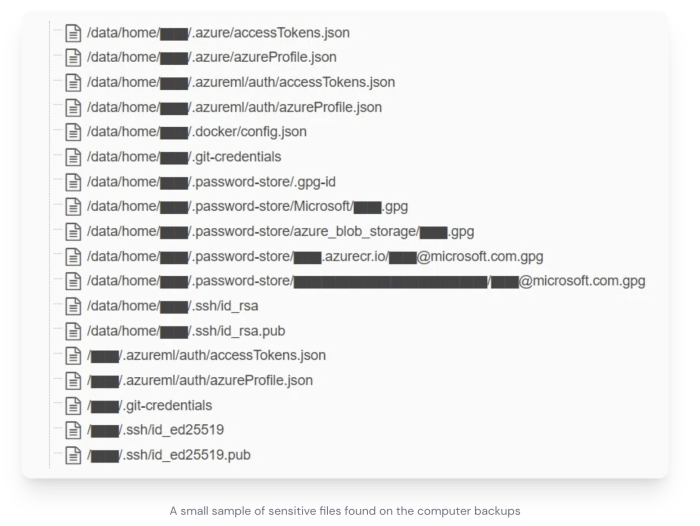
The breach involved the unauthorized access and potential exposure of sensitive Microsoft employee data. The exact scope remains partially undisclosed, but reports suggest a range of information was compromised, impacting employee privacy and potentially Microsoft’s operational security.
Types of Data Potentially Exposed
The types of data potentially exposed varied, depending on the specific employee and their role within the company. This could include personally identifiable information (PII) such as names, addresses, phone numbers, and email addresses. Furthermore, internal employee data like job titles, department affiliations, and potentially even internal communication records may have been accessed. In some cases, more sensitive information, such as salary details or performance reviews, might also have been at risk. The lack of complete transparency from Microsoft regarding the precise data compromised makes a definitive list impossible at this time.
Potential Impact on Individual Employees
The exposure of this data carries significant potential risks for individual Microsoft employees. Identity theft is a primary concern, with exposed PII allowing malicious actors to open fraudulent accounts, apply for loans, or conduct other illicit activities in the employees’ names. Phishing attacks targeting compromised accounts are also a likely consequence. Furthermore, the release of internal information could lead to reputational damage or even blackmail attempts. The emotional distress and inconvenience caused by such breaches are also substantial, demanding significant time and resources for remediation.
Methods Used to Exploit the Vulnerability
While the precise methods used by the attackers remain largely undisclosed by Microsoft, several possibilities exist. A common vector is phishing attacks, where malicious emails or messages trick employees into revealing their credentials. Exploiting known software vulnerabilities, either in Microsoft’s own systems or third-party applications, is another likely method. Supply chain attacks, where attackers compromise a vendor or partner to gain access to Microsoft’s internal systems, also remain a possibility. Advanced persistent threats (APTs), involving sophisticated and prolonged intrusions, can’t be ruled out either. The lack of detailed information from Microsoft makes pinpointing the exact method difficult.
Timeline of Events
A precise timeline of events surrounding the data exposure has not been publicly released by Microsoft. However, based on available information, a likely sequence of events might include the initial breach, the discovery of the breach by Microsoft, the investigation into the breach, and the notification of affected employees. The lack of transparency makes reconstructing a detailed timeline challenging.
Summary of Known Facts
| Date | Event | Data Type Exposed | Impact |
|---|---|---|---|
| [Date of Discovery – Unspecified] | Discovery of Data Breach | Unspecified | Potential exposure of employee PII and internal data. |
| [Date of Notification – Unspecified] | Notification of Affected Employees | Unspecified | Potential for identity theft, phishing attacks, reputational damage. |
| [Date of Remediation – Unspecified] | Remediation Efforts Undertaken | Unspecified | Mitigation of further data exposure and security improvements. |
Microsoft’s Response to the Breach
The fallout from any major data breach is immense, but when it involves a tech giant like Microsoft, the scrutiny intensifies. Their response, therefore, became a crucial element in how the situation was ultimately perceived – both internally by employees and externally by clients and the public. The speed and transparency of their actions would directly impact their reputation and trust.
Microsoft’s initial response to the incident was swift, though the details weren’t immediately public. Internal investigations began immediately upon discovery of the breach. This involved identifying the affected systems, assessing the extent of the data exposure, and initiating steps to secure the compromised data. This rapid internal action, while not immediately visible to the outside world, set the stage for a more coordinated and comprehensive public response.
Microsoft’s Actions to Contain the Breach
Containing the breach involved several key actions. First, Microsoft immediately implemented enhanced security measures across affected systems. This included patching vulnerabilities, strengthening access controls, and implementing multi-factor authentication where it wasn’t already in place. Second, they worked to identify and isolate the compromised accounts, limiting further access to sensitive information. Finally, they leveraged their internal security expertise and collaborated with external cybersecurity firms to analyze the attack, understand its scope, and develop effective mitigation strategies. The goal was to not only stop the immediate threat but also to prevent similar incidents in the future.
Microsoft’s Communication Strategy
Microsoft’s communication strategy regarding the data exposure was arguably a key element of their response. While the initial response was focused on internal investigation and remediation, they eventually released public statements acknowledging the breach. These statements, however, were carefully worded, balancing transparency with the need to avoid undue alarm or providing information that could aid potential future attacks. Internal communication with affected employees was also crucial, keeping them informed of the situation and the steps being taken to address it. Open and honest communication, even amidst a crisis, was paramount in maintaining employee trust.
Microsoft’s Remediation Efforts
Remediation efforts went beyond immediate containment. Microsoft implemented new security protocols, invested in advanced threat detection systems, and launched comprehensive employee training programs focused on cybersecurity awareness. They also conducted a thorough review of their existing security infrastructure, identifying weaknesses and implementing corrective actions to prevent similar breaches in the future. This proactive approach demonstrated a commitment to learning from the incident and strengthening their overall security posture.
Summary of Microsoft’s Actions and Their Effectiveness
The effectiveness of Microsoft’s response is still being evaluated, as the long-term consequences of the breach are yet to fully unfold. However, several factors point to a relatively robust response:
- Swift internal investigation and initial containment efforts.
- Implementation of enhanced security measures across affected systems.
- Proactive communication with both employees and the public.
- Comprehensive remediation efforts, including employee training and infrastructure upgrades.
- Collaboration with external cybersecurity firms for expert analysis and support.
While a perfect response is unlikely in any major breach, Microsoft’s actions demonstrated a commitment to addressing the situation effectively and proactively mitigating future risks. The long-term success of these efforts will depend on continued vigilance and a sustained focus on cybersecurity best practices.
Vulnerability Analysis
Source: 4gpackages.com
The Microsoft data breach, while specifics remain shrouded in confidentiality agreements and ongoing investigations, likely stemmed from a confluence of factors rather than a single, catastrophic failure. Understanding the root causes requires examining the vulnerabilities exploited and comparing them to similar incidents across the tech landscape. This analysis aims to shed light on potential weaknesses in Microsoft’s internal security posture and propose preventative measures.
The root cause likely involved a combination of vulnerabilities, possibly including unpatched software, weak access controls, and insufficient employee security training. Attackers may have leveraged known exploits or discovered zero-day vulnerabilities to gain initial access. Sophisticated phishing campaigns, exploiting social engineering principles, could also have played a significant role in bypassing security protocols. The exact nature of these vulnerabilities remains undisclosed, but the scale of the breach suggests a significant lapse in multiple layers of defense.
Exploited Vulnerabilities
The attackers likely exploited a combination of technical and human vulnerabilities. Technical vulnerabilities might have included outdated software with known security flaws, misconfigured servers allowing unauthorized access, or insufficiently protected APIs. Human vulnerabilities could include employees falling prey to sophisticated phishing attacks or failing to adhere to established security protocols. The attackers may have used a multi-stage attack, chaining together several vulnerabilities to gain deeper access to the system and exfiltrate sensitive data. This strategy is common among advanced persistent threat (APT) actors. For instance, they might have initially gained access through a phishing email leading to a compromised credential, then leveraged that access to move laterally within the network to access more sensitive data.
Comparison to Similar Incidents
The Microsoft breach shares similarities with other high-profile data breaches, such as the SolarWinds attack and the Yahoo! data breaches. In all these cases, attackers used a combination of technical and human vulnerabilities to gain access to sensitive data. The SolarWinds attack, for example, involved compromising the software supply chain to gain access to numerous organizations. Similarly, the Yahoo! breaches involved exploiting vulnerabilities in their systems and exploiting human vulnerabilities through phishing attacks. These incidents highlight the persistent challenge of securing complex IT infrastructures against determined attackers. The common thread across these events is the exploitation of both technical and human vulnerabilities, demanding a multi-layered security approach.
Potential Security Weaknesses in Microsoft’s Internal Systems
Several potential security weaknesses within Microsoft’s internal systems could have contributed to the breach. These could include insufficient monitoring of network traffic, inadequate logging and auditing capabilities, insufficient employee security awareness training, a lack of robust multi-factor authentication, and inadequate penetration testing and vulnerability assessments. The lack of a comprehensive security information and event management (SIEM) system could have hindered early detection of malicious activity. Furthermore, insufficient segregation of duties and a lack of robust access control policies might have allowed attackers to move laterally within the network more easily. This highlights the need for a proactive and comprehensive security posture, rather than a reactive one.
Hypothetical Breach Prevention Scenario
A hypothetical scenario preventing the breach might involve a multi-pronged approach. First, mandatory and regularly updated security awareness training for all employees would significantly reduce the risk of phishing attacks. Second, implementing robust multi-factor authentication for all accounts would add an extra layer of security, making it harder for attackers to gain unauthorized access. Third, rigorous penetration testing and vulnerability assessments, conducted regularly by independent security experts, could identify and address potential weaknesses before they can be exploited. Fourth, deploying a comprehensive SIEM system with advanced threat detection capabilities would enable early detection of suspicious activities. Finally, a zero-trust security model, where every user and device is verified before access is granted, could further enhance security. This combined approach, focusing on both technical and human elements, would significantly reduce the likelihood of a similar breach occurring.
Impact on Employee Trust and Morale
Source: pcmag.com
A data breach affecting employee information, even at a company as large and seemingly secure as Microsoft, carries significant consequences beyond the immediate technical remediation. The ripple effect extends deeply into the fabric of the organization, impacting employee trust, morale, and ultimately, the company’s reputation and bottom line. The exposed data, depending on its nature, could range from contact details to more sensitive information like compensation details or even performance reviews. This potential for misuse significantly impacts the psychological safety of employees.
The erosion of trust in Microsoft’s security practices is a direct and immediate consequence. Employees who trusted the company to safeguard their personal data will likely feel betrayed and vulnerable. This breach of confidence can manifest in several ways, from increased anxiety and reduced job satisfaction to a reluctance to share information openly, potentially hindering collaboration and innovation. The impact on morale and productivity is equally significant. A drop in morale can lead to decreased productivity, increased absenteeism, and higher employee turnover. The psychological impact can be substantial, leading to stress, anxiety, and even feelings of powerlessness among affected employees.
Employee Trust in Microsoft’s Security Practices
The breach inevitably raises questions about the effectiveness of Microsoft’s security infrastructure and internal processes. Employees may question the adequacy of security measures, leading to a loss of confidence in the company’s ability to protect sensitive information. This lack of trust can extend beyond personal data to encompass broader concerns about the company’s overall security posture and its commitment to employee well-being. The response to the breach, including the transparency and communication provided to employees, will significantly influence the restoration of trust. A swift, comprehensive, and empathetic response can help mitigate the damage, while a slow or opaque response will likely exacerbate the negative impact. For example, a company that swiftly acknowledges the breach, provides clear explanations, and offers proactive support to affected employees will likely see a faster recovery in trust than a company that downplays the incident or fails to communicate effectively.
Effect on Employee Morale and Productivity
Reduced trust inevitably translates into decreased morale. Employees may become disengaged, less motivated, and less productive. The fear of identity theft, financial fraud, or other forms of harm stemming from the data breach can be a significant source of stress and anxiety, impacting their ability to focus on their work. This decrease in productivity can have tangible financial consequences for Microsoft, impacting project timelines, and potentially impacting the company’s overall profitability. The impact on employee retention should also be considered. Employees may seek employment elsewhere, fearing future breaches or a lack of commitment to security from their employer. This loss of experienced personnel can further harm the company’s operational efficiency and competitive edge.
Legal Ramifications for Microsoft
The legal implications of a data breach can be substantial. Microsoft could face lawsuits from affected employees alleging negligence, breach of contract, or violation of privacy laws. The severity of the legal ramifications will depend on several factors, including the nature of the data exposed, the number of affected employees, the extent of any harm suffered, and the adequacy of Microsoft’s response. The company may face fines and penalties imposed by regulatory bodies, in addition to legal costs associated with defending lawsuits. Depending on the jurisdiction and applicable laws, these penalties can be significant, potentially running into millions of dollars.
Reputational Damage to Microsoft
Beyond the immediate financial and legal consequences, the data breach poses a significant threat to Microsoft’s reputation. A negative public perception of Microsoft’s security practices can damage its brand image, affect customer trust, and impact its ability to attract and retain both customers and employees. This reputational damage can be long-lasting, potentially affecting the company’s market share and its overall financial performance for years to come. The damage to reputation can be amplified if the company is perceived as being unresponsive or uncaring in its handling of the situation.
| Impact Area | Description of Impact | Short-Term Effects | Long-Term Effects |
|---|---|---|---|
| Employee Trust | Erosion of trust in Microsoft’s security practices and commitment to employee well-being. | Decreased morale, reduced collaboration, increased anxiety among employees. | Higher employee turnover, difficulty attracting top talent, damaged employer brand. |
| Employee Morale | Reduced job satisfaction, increased stress and anxiety levels, feelings of vulnerability. | Decreased productivity, increased absenteeism, potential for work slowdowns. | Long-term impact on productivity, potential for decreased innovation, negative impact on company culture. |
| Legal Ramifications | Potential lawsuits from affected employees, regulatory fines and penalties. | Increased legal costs, potential for negative publicity surrounding legal battles. | Significant financial losses, reputational damage associated with legal proceedings. |
| Reputational Damage | Negative perception of Microsoft’s security capabilities and commitment to data protection. | Loss of customer trust, potential impact on sales and market share. | Long-term damage to brand image, difficulty attracting investors and partners. |
Lessons Learned and Future Implications
The Microsoft data breach, while unfortunate, presents a valuable opportunity for introspection and improvement within the tech giant and the broader cybersecurity landscape. This incident underscores the critical need for robust security protocols and a proactive approach to data protection, impacting not only Microsoft’s reputation but also setting a precedent for industry-wide best practices. The lessons learned should serve as a catalyst for significant changes in how organizations handle sensitive employee data.
Analyzing this breach reveals several key areas needing attention. A multi-faceted approach is crucial, combining enhanced technological safeguards with improved employee education and a robust incident response plan. Failing to learn from this event could lead to similar, potentially even more damaging, incidents in the future. The implications extend beyond Microsoft, impacting the entire tech industry’s approach to data security.
Recommendations for Improving Microsoft’s Data Security Protocols, Microsoft employees data exposed
Strengthening Microsoft’s data security requires a layered approach, addressing both technical vulnerabilities and human factors. This involves investing in advanced technologies and bolstering employee training programs to ensure a comprehensive security posture.
- Implement Zero Trust security architecture: This model assumes no implicit trust and verifies every user and device before granting access to resources, significantly reducing the impact of a potential breach.
- Enhance multi-factor authentication (MFA): Mandating MFA for all employee accounts, including administrative accounts, adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Invest in advanced threat detection and response systems: Employing AI-powered security tools that can identify and respond to threats in real-time is crucial for preventing and mitigating attacks.
- Regular security audits and penetration testing: Proactive vulnerability assessments help identify weaknesses in the system before malicious actors can exploit them. Regular penetration testing simulates real-world attacks to test the effectiveness of security measures.
Implications for Data Security Best Practices Across the Industry
The Microsoft breach highlights the need for a paradigm shift in data security best practices across the entire industry. Organizations must move beyond reactive measures and embrace a proactive, preventative approach.
- Increased adoption of Zero Trust security models: The inherent limitations of traditional perimeter-based security are increasingly evident. A shift towards Zero Trust is vital for protecting against sophisticated attacks.
- Emphasis on employee training and awareness: Human error remains a major factor in many data breaches. Comprehensive training programs that educate employees about phishing scams, social engineering tactics, and safe data handling practices are essential.
- Improved incident response planning: Organizations need to develop and regularly test robust incident response plans that Artikel clear procedures for detecting, containing, and mitigating data breaches.
- Greater transparency and accountability: Open communication with employees and stakeholders regarding data security incidents is crucial for building trust and ensuring accountability.
Examples of Security Measures to Prevent Similar Breaches
Several specific security measures could have mitigated the impact of the Microsoft breach. These examples illustrate how a proactive and layered approach can significantly improve data security.
- Implementing data loss prevention (DLP) tools: DLP solutions can monitor and prevent sensitive data from leaving the organization’s network unauthorized, limiting the damage caused by a potential breach.
- Utilizing robust encryption for data at rest and in transit: Encrypting data ensures that even if an attacker gains access, they cannot read or utilize the information.
- Employing privileged access management (PAM) solutions: PAM systems control and monitor access to sensitive systems and data, reducing the risk of insider threats or compromised credentials.
- Regular software updates and patching: Keeping software up-to-date with the latest security patches is crucial for mitigating known vulnerabilities that attackers could exploit.
Improving Employee Training Regarding Data Security Awareness
Effective employee training is crucial for preventing data breaches. A multi-pronged approach combining various training methods can significantly improve data security awareness.
- Interactive security awareness training modules: Engaging training modules, including simulations and real-world scenarios, can effectively teach employees about security risks and best practices.
- Regular phishing simulations: Periodic phishing simulations help employees identify and report suspicious emails, improving their ability to detect and avoid phishing attacks.
- Data security policies and procedures: Clear, concise, and easily accessible data security policies and procedures are essential for guiding employee behavior and ensuring compliance.
- Ongoing reinforcement and updates: Data security awareness training should not be a one-time event. Regular updates and reinforcement are crucial for maintaining a high level of security awareness.
Visual Representation of the Breach
Imagine a sprawling network, a vast city of interconnected computers and servers, humming with data. This is Microsoft’s internal network, a complex ecosystem where terabytes of information flow constantly. Now, picture a single, seemingly innocuous point of entry – a vulnerability, perhaps a poorly patched software, a weak password, or a phishing email that successfully bypassed security protocols. This is the initial breach, the crack in the city walls.
The initial compromise is like a single drop of water seeping into the network. This initial access point allows the attackers to gain a foothold, slowly expanding their reach, much like a vine creeping across a wall. They use this access to move laterally, exploring the network, mapping its pathways, and identifying valuable targets – employee data. Think of this lateral movement as a growing network of tunnels, branching out from the initial point of entry.
Data Exfiltration
Once the attackers identify sensitive employee data, the process of exfiltration begins. This is the phase where data is systematically extracted from the network. Visualize this as a stream of data flowing out of the network, like a river leaving its source. This stream is carefully channeled, using various techniques to avoid detection. It might be disguised as legitimate network traffic, encrypted to prevent interception, or broken into smaller packets to evade scrutiny. The attackers meticulously extract the data, piece by piece, ensuring a steady, undetected flow.
The Attack Timeline
The timeline of the attack can be visualized as a series of concentric circles. The innermost circle represents the initial compromise, a small, contained breach. The next circle outwards represents the lateral movement, expanding the attackers’ access. The outermost circle represents the data exfiltration phase, where the stolen data leaves the network. Each circle represents a stage in the attack, with the size of the circle reflecting the increasing scope and impact of the breach.
Data Flow Visualization
Imagine a network diagram, with nodes representing servers and computers. Arrows indicate the flow of data. A thick, dark arrow would represent the initial breach, entering a specific node. From this node, thinner, branching arrows would illustrate the lateral movement, showing the attackers’ progression through the network. Finally, a thick, red arrow would indicate the data exfiltration, exiting the network from a specific point. This visual representation clearly shows how the attackers gained access, moved within the network, and ultimately stole the data.
Final Thoughts
The Microsoft employee data breach serves as a cautionary tale, underscoring the fragility of even the most sophisticated security systems. While Microsoft’s response offers some insights into handling such crises, the incident highlights the crucial need for continuous improvement in data security protocols and employee training. The long-term effects on employee trust and Microsoft’s reputation remain to be seen, but one thing is clear: the fight against cyber threats is far from over. This incident forces a much-needed conversation about the evolving nature of cybersecurity and the importance of proactive measures to prevent future breaches.