Hackers Compiled V8 JavaScript Malware: It sounds like something out of a cyberpunk thriller, right? But the reality is far more sinister. This isn’t some fictional dystopia; it’s a very real threat leveraging the vulnerabilities of the ubiquitous V8 JavaScript engine to unleash malicious code upon unsuspecting victims. We’re diving deep into the shadowy world of how hackers exploit these weaknesses, the clever ways they hide their attacks, and what you can do to protect yourself from this insidious threat. This isn’t just about code; it’s about the human element, the social engineering tricks, and the devastating consequences of a successful attack.
From understanding the specific vulnerabilities within the V8 engine to dissecting the delivery mechanisms and the sophisticated obfuscation techniques employed by hackers, we’ll explore the entire lifecycle of this dangerous malware. We’ll examine real-world examples, dissect malicious code snippets, and arm you with the knowledge to recognize and mitigate these attacks. Get ready to uncover the dark secrets behind this increasingly prevalent threat.
V8 JavaScript Engine Vulnerabilities
Source: bleepstatic.com
The V8 JavaScript engine, a cornerstone of Chrome and Node.js, isn’t immune to vulnerabilities. These flaws, often exploited by malicious actors, can lead to the creation of sophisticated malware capable of hijacking systems and stealing sensitive data. Understanding these vulnerabilities is crucial for developers and security professionals alike.
Common V8 JavaScript Engine Vulnerabilities Exploited in Malware
Hackers leverage several weaknesses in V8 to inject and execute malicious code. These vulnerabilities often stem from memory management issues, type confusion, and flaws in the engine’s parsing and interpretation of JavaScript code. For instance, memory corruption vulnerabilities can allow attackers to overwrite critical memory regions, potentially leading to arbitrary code execution. Type confusion exploits occur when the engine misinterprets the type of data, leading to unexpected behavior and potentially allowing attackers to bypass security checks. Furthermore, vulnerabilities in the way V8 handles external resources, such as network requests or file access, can be exploited to compromise system integrity.
Historical Evolution of V8 Engine Vulnerabilities in Malware
The history of V8 vulnerabilities used in malware creation reflects a constant arms race between security researchers and attackers. Early exploits often focused on simpler vulnerabilities, such as buffer overflows. As V8’s security improved, attackers shifted towards more sophisticated techniques, such as exploiting type confusion and memory corruption vulnerabilities that are harder to detect and patch. The evolution of these exploits is marked by an increasing level of sophistication and obfuscation, making them harder to identify and mitigate. For example, the use of polymorphism and code generation techniques has made malware analysis and detection significantly more challenging.
Obfuscation Techniques for Malicious V8 JavaScript Code
Obfuscation is a crucial tactic for attackers seeking to conceal malicious V8 JavaScript code. Several techniques are employed to make reverse engineering and analysis difficult. These include code packing, which compresses and encrypts the code, making it harder to understand. Control flow obfuscation alters the program’s execution flow, making it difficult to trace the code’s logic. String encryption hides sensitive data within the code, making it more difficult to identify malicious commands. Finally, polymorphism allows the malware to adapt its behavior, making it harder to detect using signature-based methods. These techniques are often layered, making the process of uncovering the malware’s true nature exceptionally challenging.
Vulnerability Types, Exploits, Impacts, and Mitigation Strategies
| Vulnerability Type | Exploit Method | Impact | Mitigation Strategy |
|---|---|---|---|
| Memory Corruption | Overwriting memory regions to execute arbitrary code | Arbitrary code execution, system compromise | Regular security updates, memory safety techniques (e.g., ASLR, DEP) |
| Type Confusion | Misinterpreting data types to bypass security checks | Security bypass, privilege escalation | Strict type checking, input validation |
| Improper Input Handling | Injecting malicious data through vulnerable input processing | Code injection, cross-site scripting (XSS) | Input sanitization, escaping special characters |
| External Resource Handling | Exploiting vulnerabilities in how V8 handles network requests or file access | Data breaches, malware downloads | Secure coding practices, validation of external data |
Malware Delivery Mechanisms
Slipping V8 JavaScript malware into unsuspecting systems requires cunning and a variety of approaches. Hackers leverage various methods, exploiting vulnerabilities in software and human psychology to achieve their malicious goals. Understanding these delivery mechanisms is crucial for effective cybersecurity.
Hackers employ several strategies to deliver V8 JavaScript-based malware, exploiting both software weaknesses and human vulnerabilities. These methods often involve a combination of technical expertise and social engineering.
Attack Vectors for V8 JavaScript Malware
The delivery of V8 JavaScript malware relies on exploiting vulnerabilities in web browsers, email clients, and other applications that handle JavaScript code. Common attack vectors include malicious websites, compromised legitimate websites, drive-by downloads, and malicious email attachments. For example, a seemingly innocuous link in a phishing email might redirect a user to a website hosting a malicious JavaScript script, or a seemingly harmless email attachment could contain a JavaScript file designed to install malware. Another approach involves exploiting vulnerabilities in web applications to inject malicious JavaScript code into legitimate websites, allowing attackers to target a broader audience without requiring direct user interaction beyond visiting a compromised site.
Social Engineering Techniques
Social engineering plays a critical role in the success of V8 JavaScript malware attacks. Hackers use deceptive tactics to trick users into executing malicious code. Phishing emails, often disguised as legitimate communications from banks, online retailers, or other trusted entities, are frequently used to lure victims into clicking malicious links or opening infected attachments. These emails may contain urgent requests, threats of account suspension, or promises of rewards to increase the likelihood of user engagement. Another technique involves creating fake websites that mimic legitimate online services, such as login portals or online banking sites. Users who unknowingly enter their credentials on these fake websites risk having their sensitive information stolen, which can be subsequently used to deliver further malware, including V8 JavaScript-based attacks.
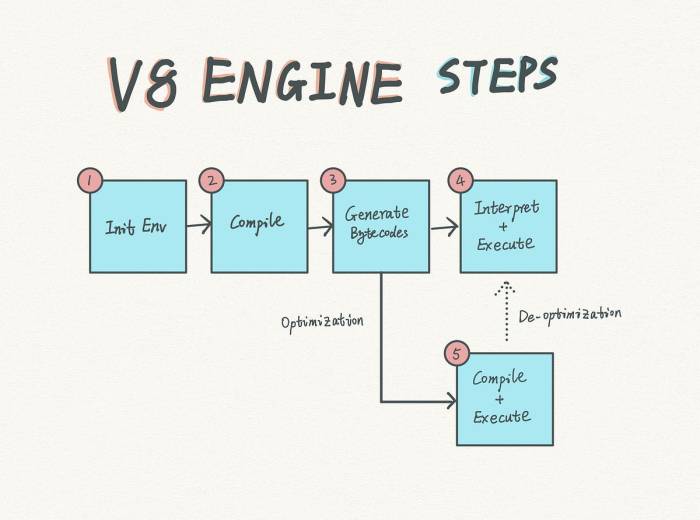
Stages of a Typical V8 JavaScript Malware Attack, Hackers compiled v8 javascript malware
The following diagram illustrates the typical stages of an attack using V8 JavaScript malware:
Diagram: Imagine a flowchart. Stage 1: Initial Contact shows an arrow pointing from a “Malicious Email/Website” box to a “User” box. Stage 2: Exploitation shows an arrow from the “User” box to a “Compromised System” box, illustrating the user clicking a malicious link or opening a harmful attachment. Stage 3: Malware Delivery shows an arrow from the “Compromised System” box to a “V8 JavaScript Payload” box, representing the malicious JavaScript code being downloaded and executed. Stage 4: Payload Execution shows an arrow from the “V8 JavaScript Payload” box to a “System Compromise” box, depicting the malware establishing itself on the system. Stage 5: Command and Control shows an arrow from the “System Compromise” box to a “Hacker Server” box, signifying the malware communicating with the attacker’s server to receive further instructions or exfiltrate data. The final arrow points from the “Hacker Server” box back to the “Malicious Email/Website” box, creating a cycle.
Caption: This diagram illustrates the lifecycle of a typical V8 JavaScript malware attack, starting with initial contact via a malicious email or website, proceeding through exploitation, malware delivery, payload execution, system compromise, and culminating in communication with the attacker’s command-and-control server. The cyclical nature highlights the ongoing threat and the need for robust security measures.
Malware Functionality and Capabilities
Source: medium.com
V8 JavaScript malware, leveraging the power and ubiquity of the V8 engine, presents a significant threat. Its capabilities extend far beyond simple annoyances, enabling sophisticated attacks that compromise systems, steal data, and disrupt networks. Understanding the functionalities and techniques employed by these malicious scripts is crucial for effective defense. This section delves into the common functionalities, interaction methods, persistence strategies, and evasion tactics used by this type of malware.
These malicious JavaScript scripts often operate subtly, leveraging the V8 engine’s integration within browsers and other applications to execute their payload. They achieve this by exploiting vulnerabilities or utilizing legitimate functionalities for nefarious purposes. This allows them to interact with the operating system and applications at various levels, from accessing files and manipulating the registry to establishing network connections and executing commands.
Data Exfiltration Techniques
Data exfiltration is a core functionality of many V8 JavaScript malware variants. These scripts can stealthily collect sensitive information, such as login credentials, personal data, and financial information, and transmit it to a remote server controlled by the attacker. Techniques employed include using hidden iframes to make covert HTTP requests to Command and Control (C&C) servers, encoding data within seemingly innocuous website elements, and utilizing various obfuscation techniques to evade detection by security software. The exfiltrated data can then be used for identity theft, financial fraud, or other malicious purposes. For example, a script might intercept form submissions, capturing usernames and passwords before they reach the legitimate server.
System Compromise and Persistence Mechanisms
V8 JavaScript malware often aims to establish persistence on the compromised system, ensuring its continued operation even after a reboot. This is achieved through various techniques, including modifying browser settings to automatically execute the malicious script on startup, creating scheduled tasks or services, and injecting code into legitimate processes. Persistence mechanisms ensure the malware’s longevity and ability to continue its malicious activities without requiring re-infection. For instance, a script could modify the registry to automatically launch itself upon system startup, effectively ensuring its continued presence.
Network Attacks Facilitated by V8 JavaScript Malware
While not always the primary function, some V8 JavaScript malware can be used to launch network attacks. This could involve creating botnets by recruiting infected machines, acting as proxies for Distributed Denial-of-Service (DDoS) attacks, or scanning for vulnerabilities on other systems within a network. The malware might use the compromised system as a launching pad for further attacks, expanding the attacker’s reach and impact. Imagine a scenario where a seemingly harmless website contains malicious JavaScript code; upon visiting this site, a user’s machine becomes part of a botnet, unknowingly participating in a DDoS attack against a target server.
Evasion Techniques
To remain undetected, V8 JavaScript malware employs a range of evasion techniques. These include code obfuscation, polymorphism (changing the code’s structure without altering its functionality), and anti-analysis techniques designed to hinder reverse engineering efforts. The malware may also use techniques like packing or encryption to make analysis more difficult. Obfuscation makes the code extremely difficult to understand, hindering analysis by security researchers. Polymorphism makes it difficult for signature-based detection systems to identify the malware effectively.
Prevalent Types of V8 JavaScript Malware and Their Capabilities
Understanding the specific capabilities of different types of V8 JavaScript malware is crucial for effective mitigation.
The following list Artikels some prevalent types and their capabilities. Note that this is not an exhaustive list, and new variants are constantly emerging.
- Browser hijackers: These scripts modify browser settings, redirecting users to malicious websites or displaying unwanted advertisements.
- Credential stealers: These scripts target login credentials and other sensitive information, often targeting online banking and email accounts.
- Keyloggers: These scripts record user keystrokes, capturing passwords, credit card numbers, and other sensitive data.
- Ransomware: While less common in pure JavaScript form, JavaScript can be used as a delivery mechanism or initial stage for ransomware, encrypting files and demanding a ransom for their release.
- Information stealers: These scripts gather various types of information from the compromised system, such as cookies, browsing history, and local files.
Obfuscation and Anti-Analysis Techniques
V8 JavaScript malware, like a digital chameleon, constantly adapts to evade detection. Hackers employ a range of sophisticated obfuscation techniques to make reverse engineering and analysis incredibly difficult, turning what should be a straightforward process into a complex puzzle. Understanding these methods is crucial for security professionals striving to stay ahead of the curve.
Obfuscation techniques aim to make the code’s purpose and functionality as unclear as possible. This involves transforming the code while preserving its original functionality, making it incredibly difficult for analysts to understand the malicious actions the code will perform. This makes identifying and neutralizing the threat significantly more challenging.
String Encoding
String encoding is a common obfuscation technique. Instead of using plain text strings directly within the code, hackers encode them using various algorithms. This could involve base64 encoding, hexadecimal encoding, or custom encoding schemes. The decoded strings often contain sensitive information like URLs for Command & Control servers, file paths, or even the malicious payload itself. The encoded strings appear as meaningless sequences of characters to a casual observer, obscuring their true nature. For example, the string “http://malicious.com/payload.exe” might be encoded as “aHR0cDovL21hbGljaW91cy5jb20vcGF5bG9hZC5leGU=” (base64 encoded). Decoding requires reversing the encoding algorithm.
Control Flow Flattening
Control flow flattening significantly alters the program’s execution path. Instead of a clear, linear sequence of instructions, the code is restructured into a complex, tangled web of jumps and conditional statements. This makes it much harder to follow the program’s logic and understand how it reaches its malicious objectives. The code might be broken into many small, seemingly unrelated functions, making it incredibly challenging to trace the overall execution flow. Imagine a simple “if-then-else” statement transformed into a labyrinth of nested loops and conditional checks, making the original intent nearly impossible to determine without extensive analysis.
Polymorphism
Polymorphic malware uses techniques to change its own code while maintaining its functionality. This makes it very difficult to detect using signature-based antivirus software, which relies on identifying specific code patterns. The malware might alter its code each time it runs, making it a moving target. This could involve changing the names of variables and functions, altering the order of instructions, or using different encryption methods for the payload. The goal is to make each instance of the malware unique, thus bypassing traditional detection methods. This is similar to a virus mutating to evade the body’s immune system.
Deobfuscation Example
Let’s consider a simple example of base64 encoded string:
var encodedString = "aHR0cDovL21hbGljaW91cy5jb20vcGF5bG9hZC5leGU=";
var decodedString = atob(encodedString);
console.log(decodedString); // Outputs: http://malicious.com/payload.exe
This code snippet demonstrates how a base64 encoded string can be easily decoded using the `atob()` function in JavaScript. More complex obfuscation techniques require more sophisticated deobfuscation tools and techniques.
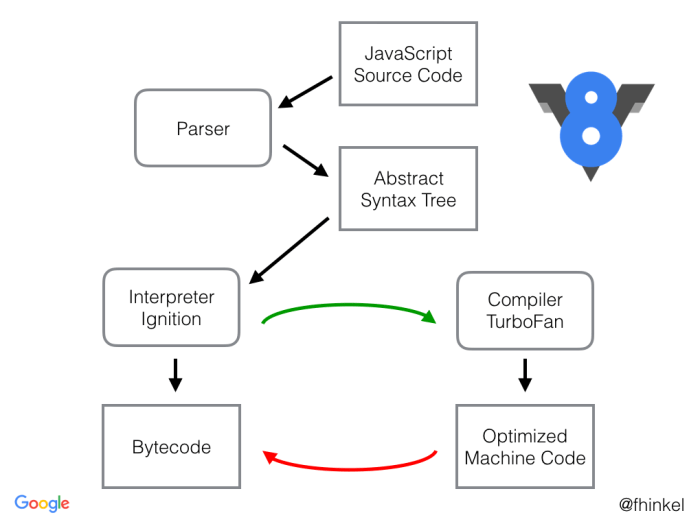
Analyzing Obfuscated V8 JavaScript Malware
A flowchart illustrating the analysis process would show sequential steps:
1. Initial Assessment: Identify the malware sample and its potential impact.
2. Static Analysis: Examine the code without executing it. This involves using tools to deobfuscate the code, identify suspicious functions, and analyze the control flow.
3. Dynamic Analysis: Execute the code in a controlled environment (like a sandbox) to observe its behavior. This helps identify network connections, file system access, and other malicious activities.
4. Deobfuscation: Apply various techniques to remove obfuscation layers, making the code more understandable. This often involves using decompilers, disassemblers, and custom scripts.
5. Code Reconstruction: Piece together the deobfuscated code to understand its functionality and malicious intent.
6. Threat Assessment: Determine the potential damage the malware can cause and develop mitigation strategies.
Impact and Mitigation Strategies
Source: medium.com
V8 JavaScript malware, leveraging the ubiquitous nature of JavaScript and the power of the V8 engine, poses a significant threat to both individual users and large organizations. The potential for widespread damage is amplified by the often-unseen nature of these attacks, making early detection and remediation crucial. Understanding the potential impact and implementing robust mitigation strategies are paramount for maintaining digital security.
The potential impact of V8 JavaScript malware varies greatly depending on the specific malware’s capabilities and the target system. For individuals, this could range from minor annoyances like unwanted pop-ups and browser redirects to more severe consequences such as data theft, identity fraud, and ransomware infections. Organizations face a much broader spectrum of risks, including data breaches leading to financial losses, reputational damage, legal repercussions, and operational disruptions. Critically, sophisticated V8-based malware can exploit vulnerabilities to gain complete control of a system, potentially leading to network-wide compromises.
Preventing V8 JavaScript-Based Attacks
Proactive measures are the first line of defense against V8 JavaScript malware. This involves a multi-layered approach encompassing software updates, secure browsing practices, and robust security software. Regularly updating your operating system, web browsers, and all installed software patches known vulnerabilities that malicious actors could exploit. Practicing safe browsing habits, such as avoiding suspicious websites and downloading files only from trusted sources, significantly reduces the risk of infection. Employing a reputable antivirus and anti-malware solution with real-time protection and regular scanning capabilities is crucial for detecting and removing malicious code. Furthermore, enabling browser security features like sandboxing and content blocking can further mitigate risks.
Detecting and Removing V8 JavaScript Malware
Detection and removal of V8 JavaScript malware often requires a combination of techniques. Modern antivirus software utilizes signature-based detection, identifying known malicious code patterns. However, sophisticated malware often employs obfuscation techniques, making signature-based detection less effective. Behavioral analysis, monitoring the actions of running processes, can detect suspicious activities indicative of malware, even if the code itself is obfuscated. Static analysis, examining the code without execution, can reveal malicious code structures and functions. Sandboxing environments allow for safe execution of suspicious code to analyze its behavior without risking the main system. In cases of severe infection, a complete system reinstallation may be necessary to ensure complete removal of the malware. Specialized security tools, such as network intrusion detection systems (NIDS) and security information and event management (SIEM) systems, can play a critical role in identifying and responding to attacks.
Security Recommendations for JavaScript Developers
Secure coding practices are essential to minimize vulnerabilities in JavaScript applications. Developers should adhere to strict input validation procedures, ensuring that all user-supplied data is thoroughly sanitized before processing. Implementing robust error handling mechanisms helps prevent unexpected behavior that could be exploited by attackers. Minimizing the use of eval() and similar functions, which can execute arbitrary code, is crucial. Regular security audits and penetration testing can identify and address potential vulnerabilities before they can be exploited. Following secure coding best practices and utilizing linters and static analysis tools can significantly reduce the risk of introducing vulnerabilities into the codebase. Furthermore, regularly updating dependencies and libraries to their latest versions patches known security flaws.
Closing Summary: Hackers Compiled V8 Javascript Malware
The threat posed by hackers compiling V8 JavaScript malware is real and evolving. While the technical details can be daunting, understanding the fundamental principles—the vulnerabilities, the attack vectors, and the obfuscation techniques—is crucial for effective defense. By staying informed about the latest threats and adopting proactive security measures, both individuals and organizations can significantly reduce their risk. Remember, the fight against malicious code is an ongoing battle, and knowledge is your most powerful weapon. Stay vigilant, stay informed, and stay secure.



