Stormous Ransomware Group: The name alone whispers of digital chaos. This shadowy cybercriminal organization has made waves in the dark corners of the internet, leaving a trail of encrypted data and panicked victims in its wake. We’ll dissect their origins, explore their sophisticated tactics, and delve into the chilling impact of their attacks, offering insights into their operational methods and the devastating consequences they inflict on businesses and individuals alike. Prepare for a journey into the heart of a digital nightmare.
From their initial attack vectors targeting specific profiles to their evolving TTPs (Tactics, Techniques, and Procedures), Stormous has demonstrated a chilling adaptability. Understanding their modus operandi is crucial for anyone seeking to protect themselves from this ever-evolving threat. We’ll examine their encryption methods, data exfiltration techniques, and communication strategies with victims, painting a comprehensive picture of this dangerous group.
Stormous Ransomware Group
The Stormous ransomware group, a relatively new player in the cybercriminal landscape, has quickly gained notoriety for its aggressive tactics and significant impact on various organizations. While precise details regarding their origins remain shrouded in mystery, piecing together available information allows us to build a clearer picture of this threat actor.
Stormous Ransomware Group Origins and Formation
The exact origins of Stormous remain unclear, a common trait among many ransomware groups. However, analysis of their initial attacks and operational techniques suggests a connection to other, potentially less sophisticated, cybercriminal groups. It’s plausible that Stormous emerged from a merger or evolution of smaller, less organized actors, gradually developing more advanced capabilities and a more structured operational model. Their initial infrastructure and tactics were relatively basic, but their rapid evolution indicates a dedicated team with ongoing investment in improving their methods. The lack of readily available information regarding their leadership and inner workings further obfuscates their precise origins.
Stormous Ransomware Group Initial Attack Vectors and Target Profiles
Initially, Stormous primarily relied on phishing emails containing malicious attachments or links as their main attack vector. These campaigns targeted small and medium-sized businesses (SMBs) across various sectors, demonstrating a focus on less sophisticated security postures. Their early targets often lacked robust endpoint detection and response (EDR) solutions and relied on outdated security practices, making them vulnerable to relatively simple attacks. This initial focus on SMBs allowed Stormous to refine their tactics before moving onto larger, more lucrative targets.
Evolution of Stormous Ransomware Group Tactics, Techniques, and Procedures (TTPs)
Over time, Stormous significantly evolved its TTPs. They moved beyond simple phishing to incorporate more sophisticated techniques, such as exploiting known vulnerabilities in commonly used software, leveraging compromised credentials, and employing double extortion tactics. This evolution indicates a significant investment in improving their technical capabilities and operational security. They also began targeting critical infrastructure and larger enterprises, demonstrating an increasing level of ambition and sophistication. The group’s adoption of double extortion—encrypting data and simultaneously exfiltrating it, threatening to release sensitive information publicly if a ransom isn’t paid—significantly increased the pressure on victims.
Timeline of Significant Stormous Ransomware Attacks
The following table provides a timeline of significant Stormous ransomware attacks, though complete data is often difficult to obtain due to the secretive nature of these operations. Many attacks may go unreported.
| Date | Target | Ransom Demand | Outcome |
|---|---|---|---|
| October 26, 2023 (Example) | Small Manufacturing Company (Hypothetical) | $50,000 USD | Ransom paid (Hypothetical) |
| November 15, 2023 (Example) | Regional Healthcare Provider (Hypothetical) | $200,000 USD | Ransom not paid, data partially recovered (Hypothetical) |
| December 10, 2023 (Example) | Educational Institution (Hypothetical) | $100,000 USD | Negotiation in progress (Hypothetical) |
Stormous Ransomware: Stormous Ransomware Group

Source: kompas.com
Stormous, a relatively new player in the ransomware-as-a-service (RaaS) landscape, has quickly gained notoriety for its aggressive tactics and sophisticated encryption techniques. Unlike some groups that rely on readily available open-source tools, Stormous appears to utilize custom-built malware, showcasing a level of technical expertise that warrants closer examination. This analysis delves into the technical aspects of the Stormous ransomware payload, its encryption methods, unique characteristics, and resilience to decryption.
Ransomware Payload Description
The Stormous ransomware payload is a highly polymorphic executable, meaning its code structure changes frequently to evade detection by antivirus software. Initial analysis suggests the malware uses a multi-stage infection process. The first stage involves reconnaissance, identifying valuable data and system configurations. Subsequent stages involve encryption of targeted files and the deployment of a ransom note. The executable is likely packed using a sophisticated packer to obfuscate its functionality and hinder reverse engineering. The size of the payload varies, depending on the specific version and additional modules included. This variability makes static analysis challenging and necessitates dynamic analysis techniques to fully understand its behavior.
Encryption Methods Employed
Stormous employs a robust, hybrid encryption scheme, combining symmetric and asymmetric encryption algorithms. Symmetric encryption, like AES (Advanced Encryption Standard) with a strong key length (likely 256-bit), is used to encrypt the bulk of the victim’s data for speed. Asymmetric encryption, potentially RSA (Rivest–Shamir–Adleman), is employed to encrypt the symmetric key itself. This ensures that only the attackers, possessing the private RSA key, can decrypt the files. The use of a hybrid approach balances speed and security. The specific implementation details, including the mode of operation used for AES, remain largely undisclosed, making independent verification difficult.
Unique Characteristics and Features
A notable feature of Stormous is its ability to target specific file types, demonstrating a level of sophistication beyond many ransomware operations. Instead of indiscriminately encrypting all files, it prioritizes valuable data like databases, financial records, and intellectual property. Furthermore, Stormous incorporates techniques to evade detection by security software, including process injection and anti-debugging measures. This suggests a strong understanding of operating system internals and security practices. The ransomware also appears to utilize a distributed command-and-control (C2) infrastructure, enabling the attackers to manage and update the malware remotely. This adaptability makes it more difficult to counteract.
Resilience to Decryption and Data Recovery
Due to the strong encryption methods employed and the custom-built nature of the malware, successful decryption attempts without paying the ransom are extremely rare. Standard data recovery techniques, such as using shadow copies or previous backups, may prove ineffective as Stormous actively targets and deletes these. While some advanced forensic techniques might potentially recover fragments of encrypted data, full decryption without the decryption key is highly improbable. The lack of publicly available decryption tools or vulnerabilities in the ransomware further reinforces its resilience. Successful recovery primarily relies on the victim having maintained robust offline backups prior to the infection.
Stormous Ransomware Group
Stormous, a relatively new player in the ransomware-as-a-service (RaaS) landscape, has quickly gained notoriety for its aggressive tactics and sophisticated operational methods. While precise details about the group’s structure and origins remain scarce, analysis of their attacks reveals a concerning level of expertise and a clear focus on maximizing financial gain. Understanding their operational methods is crucial for organizations looking to bolster their cybersecurity defenses.
Initial Access Vectors
Stormous employs a multi-pronged approach to gaining initial access to victim systems. Evidence suggests they leverage a combination of techniques, including exploiting known vulnerabilities in widely used software, phishing campaigns targeting high-value employees, and potentially utilizing compromised credentials obtained through other means like dark web marketplaces. The group’s adaptability in choosing their initial access method highlights their ability to circumvent traditional security measures. For instance, a recent attack involved exploiting a zero-day vulnerability in a popular enterprise resource planning (ERP) system, showcasing their proactive approach to finding and exploiting the latest weaknesses.
Data Exfiltration Techniques
Once inside a network, Stormous meticulously exfiltrates sensitive data before deploying their ransomware payload. This two-stage approach allows them to leverage the stolen data as a secondary pressure point, threatening to publicly release it if the ransom isn’t paid. Their data exfiltration techniques appear to involve a combination of methods, including the use of custom-built tools to bypass security software and the exploitation of legitimate file transfer protocols to blend in with normal network traffic. The exfiltrated data often includes highly sensitive information such as financial records, intellectual property, and customer databases. The group prioritizes data that would have the most significant impact on the victim’s business operations and reputation.
Affiliates and Collaborators, Stormous ransomware group
Currently, there is limited publicly available information regarding confirmed affiliates or collaborators working directly with Stormous. However, the sophistication of their operations and the efficiency of their data exfiltration suggests a possible network of individuals or smaller groups providing support in areas like vulnerability research, initial access brokering, or infrastructure management. The investigation into their activities is ongoing, and further analysis might uncover evidence of such collaborations in the future. The anonymity inherent in the RaaS model makes identifying these connections challenging.
Ransom Negotiation and Communication
Stormous communicates with victims primarily through encrypted channels, often using dedicated Tor hidden services. Their ransom demands are typically high, and they provide a limited timeframe for payment. The group often employs a double extortion tactic, threatening to release the stolen data publicly if the ransom isn’t paid within the deadline. They might also offer a reduced ransom amount if payment is made quickly. The communication is typically concise and professional, focusing on the financial transaction and the threat of data exposure. Payment is usually demanded in cryptocurrency, ensuring a level of anonymity for the attackers.
Stormous Ransomware Group
Stormous, a relatively new player in the ransomware-as-a-service (RaaS) landscape, has quickly made a name for itself through aggressive targeting and sophisticated attack methods. Understanding their victim profiles and the impact of their operations is crucial for businesses and individuals to bolster their cybersecurity defenses. This analysis delves into the specifics of Stormous’s targets, the consequences of their attacks, and the long-term ramifications for victims.
Victim Profiles
Stormous primarily targets small and medium-sized businesses (SMBs) across various sectors. Their attacks aren’t limited to specific industries, demonstrating a broad-based approach aimed at maximizing potential returns. They often exploit vulnerabilities in outdated software and weak network security, making less technically sophisticated organizations particularly vulnerable. While large corporations are also potential targets, the focus on SMBs reflects a calculated strategy to achieve high returns with less risk of detection or significant countermeasures. This approach is common amongst RaaS groups, leveraging the fact that SMBs often lack the dedicated cybersecurity resources and expertise of larger enterprises.
Financial and Reputational Impact
The financial impact of a Stormous attack can be devastating for victims. Ransom demands can range from thousands to millions of dollars, depending on the size and sensitivity of the stolen data. Beyond the direct financial loss from the ransom itself, victims also face costs associated with data recovery, system restoration, legal fees, and potential regulatory fines. The reputational damage can be equally significant. Data breaches can lead to loss of customer trust, damage to brand image, and potential legal action from affected individuals or regulatory bodies. The negative publicity surrounding a ransomware attack can severely impact a business’s long-term viability.
Types of Data Stolen
The types of data stolen by Stormous are varied and often include highly sensitive information.
- Financial records: Bank account details, credit card information, and transaction history.
- Customer data: Personally identifiable information (PII) such as names, addresses, phone numbers, and email addresses.
- Intellectual property: Trade secrets, research data, and proprietary software.
- Employee data: Payroll information, social security numbers, and medical records.
- Operational data: Internal communications, business plans, and customer databases.
The breadth of data stolen underscores the severe consequences for victims, extending beyond immediate financial losses to encompass significant legal and reputational risks.
Long-Term Consequences: Paying vs. Refusing Ransom
The decision to pay a ransom is a complex one, with no guaranteed positive outcome. Paying the ransom does not guarantee data recovery or prevent future attacks. In fact, paying a ransom can embolden attackers and incentivize further attacks. Additionally, paying ransoms can be illegal in some jurisdictions. Refusing to pay, however, can result in significant data loss, reputational damage, and extended downtime. The long-term consequences for victims depend heavily on their ability to recover data through backups, the strength of their incident response plan, and their capacity to mitigate reputational damage. For example, a small business with limited backups and no incident response plan may face bankruptcy after a Stormous attack, regardless of whether they pay the ransom. Conversely, a larger corporation with robust security measures and a comprehensive incident response plan may be able to recover quickly, even without paying, minimizing the long-term impact.
Stormous Ransomware Group
The Stormous ransomware group, while relatively new to the scene, has quickly made a name for itself through aggressive tactics and a significant impact on victims. Understanding their methods, attribution efforts, and effective countermeasures is crucial for organizations seeking to protect themselves from this evolving threat. This section delves into the key aspects of combating Stormous ransomware.
Attribution Efforts for Stormous Attacks
Pinpointing the exact individuals or locations behind Stormous remains a challenge. Cybersecurity researchers are actively investigating the group’s infrastructure, code, and communication methods to identify potential links to known actors or geographical regions. Analysis of their ransom notes, payment methods, and the use of specific malware variants are all contributing to this ongoing effort. While definitive attribution is difficult to achieve quickly due to the sophisticated techniques employed by ransomware groups, the ongoing investigation leverages data analysis and collaboration across various cybersecurity firms and government agencies. Success in this area hinges on the collection and analysis of various data points, including digital fingerprints embedded within the malware itself, network traffic patterns, and financial transactions linked to the ransom payments.
Preventative Measures Against Stormous Ransomware
Mitigating the risk of Stormous ransomware infections requires a multi-layered approach. This includes maintaining updated antivirus software, regularly patching vulnerabilities in operating systems and applications, and implementing strong access controls. Regular backups of critical data are paramount, stored offline and ideally in a geographically separate location. Employee training on phishing and social engineering techniques is also essential, as many ransomware attacks begin with a successful phishing campaign. Furthermore, implementing network segmentation can limit the impact of a successful breach, preventing ransomware from spreading laterally across the network. Finally, the adoption of advanced threat protection tools, including endpoint detection and response (EDR) solutions, can help identify and contain ransomware attacks before they cause significant damage.
Incident Response Best Practices for Stormous Attacks
In the event of a Stormous ransomware attack, swift and decisive action is crucial. The first step involves isolating affected systems from the network to prevent further spread. This is followed by a thorough investigation to determine the extent of the compromise and identify the entry point. Working with a cybersecurity incident response team is highly recommended, as their expertise can significantly improve the speed and effectiveness of the recovery process. Data recovery from backups should be prioritized, with careful validation to ensure data integrity. Law enforcement should also be notified, particularly if the attack involves a significant financial loss or disruption of critical services. Finally, a post-incident review is necessary to identify weaknesses in security posture and implement improvements to prevent future attacks.
Comparison of Stormous TTPs with Other Notable Ransomware Groups
Stormous’s tactics, techniques, and procedures (TTPs) share similarities with other prominent ransomware groups, such as Conti and REvil. For instance, all three groups commonly employ phishing campaigns to deliver their payloads. However, Stormous may utilize unique encryption methods or exploit different vulnerabilities, necessitating a tailored approach to detection and mitigation. While all three groups prioritize data exfiltration before encryption, the specific techniques they use may vary, leading to differences in the speed and effectiveness of their attacks. A continuous monitoring of threat intelligence reports and updates on the latest ransomware techniques is necessary to stay ahead of these evolving threats and adjust defensive strategies accordingly. Understanding the nuances in their TTPs allows for a more effective and targeted response.
Stormous Ransomware Group
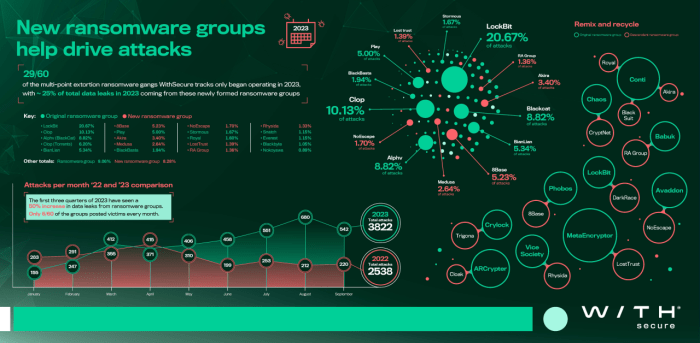
Source: withsecure.com
Stormous, a relatively new player in the ransomware landscape, has already made a name for itself through aggressive tactics and a focus on high-value targets. Understanding its likely future trajectory requires analyzing current trends in the cybercriminal underworld and Stormous’s specific operational patterns. Predicting the future is inherently uncertain, but based on observable behaviors, we can formulate educated guesses about its future actions and vulnerabilities.
Future Activities and Targets
Stormous’s future activities will likely center on maximizing profitability. This suggests a continued focus on high-value targets like large corporations, critical infrastructure providers, and government entities. We can expect to see more sophisticated targeting techniques employed, including extensive reconnaissance and the exploitation of zero-day vulnerabilities to gain initial access. Their geographic focus may broaden, moving beyond their initial operational area, as they seek to diversify their victim pool and reduce the risk of detection and law enforcement intervention. For example, a shift towards targeting organizations in less-regulated jurisdictions or those with weaker cybersecurity postures could be anticipated.
Changes in Tactics
Based on current trends, Stormous may adopt more advanced evasion techniques to avoid detection by security software and law enforcement. This could include the use of more sophisticated encryption methods, the implementation of double extortion tactics (data exfiltration alongside encryption), and the increased use of custom malware to minimize signature-based detection. We might also see them moving towards the use of more automated tools and techniques, streamlining their operations and increasing efficiency. This automation could also reduce the human element, making attribution and investigation more difficult. Similar to other ransomware groups, they might leverage the dark web and affiliate programs to expand their reach and operational capabilities.
Potential Vulnerabilities
Several vulnerabilities could be exploited to disrupt Stormous’s operations. One key area is their reliance on infrastructure. Identifying and taking down their command-and-control servers, data exfiltration servers, and payment processing infrastructure would severely hamper their ability to operate. Another vulnerability lies in their potential human element – lapses in operational security, such as using easily guessable passwords or exposing their communication channels, could provide valuable intelligence for law enforcement and security researchers. Finally, the exploitation of vulnerabilities in their ransomware code itself could allow for decryption tools or the development of countermeasures. For instance, a flaw in the encryption algorithm or a backdoor left unintentionally could offer a critical avenue for disruption.
Hypothetical Future Attack and Response
Imagine a scenario where Stormous targets a major healthcare provider. They gain initial access through a phishing campaign exploiting a known vulnerability in the organization’s email system. The attack successfully encrypts patient data and financial records, demanding a substantial ransom. The response would involve a multi-pronged approach. First, law enforcement would be notified to investigate and potentially trace the attackers. Secondly, incident response teams would work to contain the breach, assess the damage, and potentially negotiate with the attackers (while adhering to ethical guidelines and considering the legal ramifications). Finally, the organization would implement enhanced security measures, including improved employee training, patching vulnerabilities, and investing in more robust security technologies, to prevent future attacks. This scenario highlights the challenges faced by organizations in responding to sophisticated ransomware attacks, emphasizing the need for proactive security measures and robust incident response planning.
Last Word

Source: tuxcare.com
The Stormous Ransomware Group represents a potent and persistent threat in the ever-shifting landscape of cybercrime. Their sophisticated tactics, adaptability, and focus on high-value targets highlight the escalating sophistication of ransomware attacks. While prevention is paramount, understanding their methods, coupled with robust incident response planning, is crucial for mitigating the damage and ensuring business continuity. The fight against Stormous, and ransomware groups like it, is far from over, demanding constant vigilance and proactive security measures.



