Water Sigbin hackers exploit Oracle WebLogic vulnerabilities – a phrase that’s sending shivers down the spines of IT security professionals. This sophisticated hacking group is leveraging known weaknesses in Oracle’s WebLogic server to wreak havoc, targeting organizations worldwide with devastating consequences. We’ll dive deep into their methods, the vulnerabilities they exploit, and what you can do to protect yourself from becoming their next victim. Get ready for a thrilling ride into the dark underbelly of cybercrime.
This deep dive explores the Water Sigbin group’s history, their preferred attack vectors, and the specific Oracle WebLogic vulnerabilities they exploit. We’ll break down the technical details, examine real-world examples, and offer practical mitigation strategies. Think of it as your ultimate guide to understanding and defending against this persistent threat.
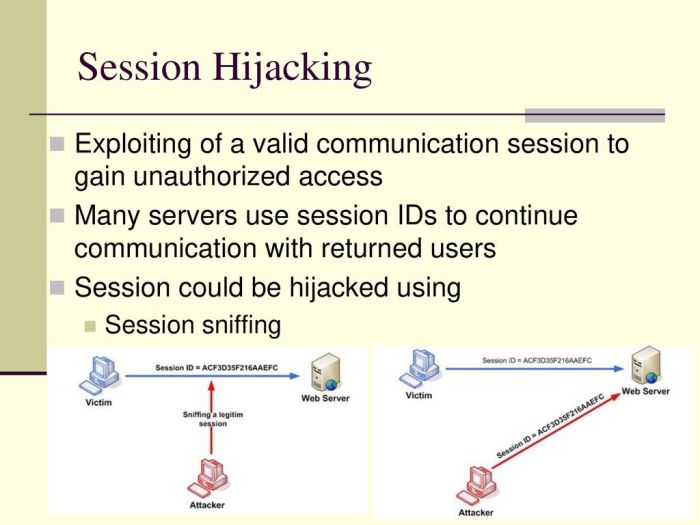
Understanding the Water Sigbin Group
Source: slideplayer.com
Water Sigbin, a sophisticated and elusive cyber threat actor, has gained notoriety for its targeted attacks against Oracle WebLogic servers, exploiting vulnerabilities to gain unauthorized access and potentially exfiltrate sensitive data. Their operations highlight the persistent danger posed by advanced persistent threats (APTs) and the need for robust cybersecurity defenses.
The Water Sigbin group’s activities primarily focus on compromising high-value targets across various sectors. Their attacks are characterized by precision and stealth, suggesting a high level of technical expertise and operational planning. While the precise scope of their targets remains somewhat unclear due to the clandestine nature of their operations, evidence suggests a preference for organizations within the financial, government, and energy sectors, where sensitive data and valuable intellectual property are abundant.
Water Sigbin’s Geographic Origin and Structure
Pinpointing the exact geographic origin of Water Sigbin remains a challenge. However, analysis of their tactics, techniques, and procedures (TTPs), combined with linguistic clues found in their malware and communications, suggests a possible origin within East Asia. The group’s operational structure likely consists of a hierarchical network of skilled individuals, specializing in various aspects of cyber operations, from initial reconnaissance and vulnerability exploitation to data exfiltration and maintaining persistent access. Their coordinated and well-planned attacks point to a highly organized and potentially state-sponsored group, though this remains speculative without definitive proof.
Timeline of Significant Water Sigbin Attacks
Tracking Water Sigbin’s activities is difficult due to the group’s covert nature. However, security researchers have documented several significant attacks attributed to the group, primarily centered around exploiting vulnerabilities in Oracle WebLogic. One notable incident involved a series of attacks in 2021, where the group leveraged a known vulnerability (CVE-2020-14882) to compromise multiple WebLogic servers. The attacks resulted in the theft of confidential data, the extent of which remains undisclosed. These attacks showcased Water Sigbin’s ability to quickly adapt to and exploit newly discovered vulnerabilities, emphasizing the importance of prompt patching and vulnerability management. Another incident in 2022 involved a similar exploitation of a zero-day vulnerability, highlighting the group’s access to cutting-edge attack techniques and potential internal sources of information on newly discovered vulnerabilities. The impact of these attacks is difficult to quantify precisely, but it underscores the potential for significant financial and reputational damage to affected organizations. The group’s consistent targeting of WebLogic servers indicates a strategic focus on exploiting widely deployed applications with known vulnerabilities, a common tactic for maximizing the potential impact of their operations.
Oracle WebLogic Vulnerabilities Exploited: Water Sigbin Hackers Exploit Oracle Weblogic Vulnerabilities
Source: securereading.com
The Water Sigbin group, known for its sophisticated hacking techniques, frequently targets Oracle WebLogic servers. Their exploits leverage a range of vulnerabilities, often focusing on flaws that allow for remote code execution (RCE). Understanding these vulnerabilities is crucial for organizations to bolster their defenses against this advanced threat actor. This section will delve into the specific WebLogic vulnerabilities commonly exploited by Water Sigbin, explaining the technical mechanisms and illustrating real-world examples.
Water Sigbin’s attacks often exploit vulnerabilities in WebLogic’s core components, leveraging known flaws to gain unauthorized access and control. These vulnerabilities often stem from insecure coding practices or insufficient input validation within WebLogic’s applications and services. The group’s success hinges on its ability to quickly identify and exploit newly discovered vulnerabilities before patches are widely deployed.
Exploited WebLogic Vulnerabilities and Attack Vectors
The technical mechanisms behind these exploits often involve manipulating WebLogic’s internal processes. For instance, a common attack vector involves sending specially crafted HTTP requests to vulnerable WebLogic services. These requests can trigger unintended behavior, allowing attackers to execute arbitrary code on the server. This code execution can then be used to steal sensitive data, install malware, or completely compromise the server. Another vector involves exploiting flaws in WebLogic’s deserialization mechanisms, where malicious data can be injected to trigger unintended actions.
Examples of Real-World Exploits
The following table summarizes some of the Oracle WebLogic vulnerabilities commonly exploited, along with their associated attack methods and impacts. Note that this is not an exhaustive list, and new vulnerabilities are constantly being discovered. The specific vulnerabilities targeted by Water Sigbin often change depending on the latest zero-day exploits and patching cycles.
| Vulnerability ID | Description | Exploit Method | Impact |
|---|---|---|---|
| CVE-2018-2894 | Deserialization vulnerability in WebLogic Server’s T3 protocol. | Sending a specially crafted T3 request to trigger remote code execution. | Complete server compromise, data theft, malware installation. |
| CVE-2017-10271 | Improper access control in WebLogic Server’s WLS console. | Exploiting weak authentication or authorization mechanisms to gain unauthorized access. | Data breaches, unauthorized configuration changes, and potential RCE. |
| CVE-2019-2725 | Another deserialization vulnerability in WebLogic Server. | Similar to CVE-2018-2894, using a crafted request to execute arbitrary code. | Similar to CVE-2018-2894: server compromise, data theft, and malware. |
| CVE-2020-14882 | Improper input validation leading to RCE in WebLogic Server. | Sending malicious input to a vulnerable WebLogic application. | Remote code execution, allowing attackers full control of the server. |
The Exploitation Process
Source: thehackernews.com
Understanding how the Water Sigbin group exploits Oracle WebLogic vulnerabilities requires examining their attack methodology. While specific techniques remain undisclosed, we can reconstruct a likely scenario based on publicly available information about similar attacks and known WebLogic vulnerabilities. This hypothetical scenario illustrates the general steps involved.
The Water Sigbin group likely leverages automated tools and exploits readily available online to target vulnerable WebLogic servers. Their operations likely involve reconnaissance, exploitation, and data exfiltration, often aiming for sensitive information within the targeted organization’s systems.
Stages of a Hypothetical Water Sigbin WebLogic Exploitation
A typical Water Sigbin attack might unfold in several stages. These steps are based on common attack vectors and techniques observed in real-world WebLogic exploits.
- Reconnaissance: The attackers initially scan the internet for exposed WebLogic servers. This involves identifying potential targets using automated tools that check for open ports and known vulnerabilities. They may utilize Shodan or similar search engines to locate vulnerable systems with publicly accessible information. This phase aims to identify weak points and prioritize targets based on perceived value.
- Vulnerability Identification: Once potential targets are identified, the attackers probe for specific vulnerabilities. They may use automated vulnerability scanners or manually test known exploits against the target’s WebLogic version. This step confirms the presence of exploitable weaknesses, such as unpatched versions or misconfigurations.
- Exploit Deployment: Having identified a vulnerability, the attackers deploy the appropriate exploit. This could involve sending a specially crafted request to the WebLogic server, potentially using a known exploit code available publicly or slightly modified for increased effectiveness. The success of this stage hinges on the vulnerability’s nature and the effectiveness of the exploit.
- Privilege Escalation: A successful exploit often grants the attackers initial access with limited privileges. However, the goal is often to escalate these privileges to gain full control of the server. This involves exploiting further vulnerabilities or misconfigurations within the WebLogic environment or the underlying operating system.
- Data Exfiltration: With elevated privileges, the attackers can access and exfiltrate sensitive data. This might involve copying files, accessing databases, or manipulating the server to send data to a remote command-and-control server controlled by the attackers. Techniques for data exfiltration are diverse and often depend on the specific environment and the attackers’ objectives.
- Persistence (Optional): In some cases, the attackers may attempt to maintain persistent access to the compromised server. This could involve installing backdoors or modifying system configurations to ensure continued access, allowing for future attacks or data theft.
Impact and Consequences
Successful Water Sigbin attacks targeting Oracle WebLogic vulnerabilities can inflict significant damage on organizations, leading to substantial financial losses, reputational harm, and operational disruptions. The severity of the impact depends on several factors, including the specific vulnerability exploited, the sensitivity of the compromised data, and the organization’s response capabilities. Understanding the potential consequences is crucial for proactive security measures.
The financial repercussions of a Water Sigbin attack can be devastating. Data breaches often lead to direct financial losses through costs associated with incident response, legal fees, regulatory fines (like GDPR penalties), and potential lawsuits from affected customers. The loss of intellectual property, customer data, and sensitive business information can severely impact an organization’s competitive advantage and future profitability. For instance, a breach exposing customer financial details could result in significant chargeback costs and loss of customer trust. Beyond direct costs, the indirect costs associated with business interruption, lost productivity, and diminished customer confidence can be even more substantial.
Financial Impacts
A successful Water Sigbin attack can result in substantial financial losses for affected organizations. These losses stem from various sources, including:
* Direct Costs: Incident response, legal fees, regulatory fines (e.g., GDPR), and potential lawsuits from affected individuals or businesses. The cost of remediation, including system repairs, security upgrades, and data recovery, can also be significant. Consider a scenario where a large retailer suffers a breach, resulting in the exposure of millions of credit card numbers. The costs associated with notifying customers, offering credit monitoring services, and dealing with potential legal action could easily reach millions of dollars.
* Indirect Costs: Business interruption, loss of productivity, damage to reputation leading to reduced sales and customer churn, and the cost of regaining customer trust. A disruption to online services, even for a short period, can lead to substantial revenue losses, particularly for businesses heavily reliant on e-commerce.
* Long-term Impacts: Loss of competitive advantage, difficulty attracting investors, and decreased market valuation. The long-term reputational damage can significantly impact a company’s ability to secure funding and maintain its market position.
Reputational Impacts
Data breaches significantly damage an organization’s reputation. The public perception of a company’s security posture is paramount, and a successful attack can severely erode trust among customers, partners, and investors. This loss of trust can translate into a decline in sales, difficulty attracting new customers, and difficulties in securing future business partnerships. Negative media coverage following a breach can amplify the damage, leading to a lasting negative impact on the organization’s brand image. For example, a healthcare provider suffering a data breach exposing patient medical records would face severe reputational damage, potentially impacting patient retention and future business.
Operational Impacts
Water Sigbin attacks can severely disrupt an organization’s operations. The exploitation of WebLogic vulnerabilities can lead to system downtime, data loss, and service interruptions, affecting critical business processes. The time required for recovery and remediation can be lengthy and costly, impacting productivity and efficiency. Depending on the nature of the exploited vulnerability and the organization’s reliance on the affected systems, the operational disruption could range from minor inconveniences to a complete halt of business operations. A financial institution, for example, experiencing a system outage due to a WebLogic vulnerability could face significant operational challenges, potentially impacting financial transactions and customer services.
Mitigation and Prevention Strategies
Protecting your Oracle WebLogic servers from attacks like those launched by the Water Sigbin group requires a multi-layered approach encompassing proactive security measures, robust patching strategies, and continuous monitoring. Ignoring these vulnerabilities can lead to significant data breaches, financial losses, and reputational damage. A comprehensive strategy is vital for minimizing risk.
The effectiveness of any security plan hinges on a proactive and layered approach. This involves a combination of preventative measures, detection systems, and incident response protocols. By addressing vulnerabilities before they can be exploited, organizations significantly reduce their attack surface and the potential for damage. Regular security audits and penetration testing further strengthen this defense.
Comprehensive Security Plan Design
A robust security plan should begin with a thorough risk assessment identifying potential vulnerabilities within the WebLogic environment. This assessment should consider both known vulnerabilities (like those exploited by Water Sigbin) and potential weaknesses specific to the organization’s infrastructure. The plan should then Artikel specific mitigation strategies for each identified risk, including patching, access control restrictions, and intrusion detection/prevention system (IDS/IPS) implementation. Regular updates and revisions to the plan are crucial to adapt to evolving threats. For instance, a plan might include a detailed schedule for applying security patches, a procedure for handling suspected compromises, and clear roles and responsibilities for the security team. It’s also important to conduct regular penetration testing to simulate real-world attacks and identify weaknesses before malicious actors can exploit them. This proactive approach allows for timely remediation, minimizing the potential impact of a successful attack.
Best Practices for Securing Oracle WebLogic Servers
Securing Oracle WebLogic servers necessitates a combination of technical controls and administrative procedures. Keeping the software up-to-date with the latest security patches is paramount. Regular vulnerability scans using automated tools can help identify and address potential weaknesses promptly. Strong password policies, including the use of multi-factor authentication (MFA), are essential to prevent unauthorized access. Principle of least privilege should be strictly enforced, granting users only the necessary permissions to perform their tasks. Network segmentation can isolate WebLogic servers from other critical systems, limiting the impact of a breach. Regular security audits and penetration testing are crucial to identify and address vulnerabilities proactively. Implementing robust logging and monitoring capabilities allows for early detection of suspicious activities. Finally, a well-defined incident response plan is crucial for handling security incidents effectively and minimizing damage.
Security Tools and Technologies
Several tools and technologies can significantly enhance the security posture of Oracle WebLogic servers.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity, alerting administrators to potential attacks and blocking malicious traffic. Examples include Snort, Suricata, and commercial IPS solutions.
- Web Application Firewalls (WAFs): WAFs filter malicious traffic targeting web applications, protecting against common attacks such as SQL injection and cross-site scripting (XSS). Popular WAFs include ModSecurity, Cloudflare WAF, and Akamai WAF.
- Vulnerability Scanners: These tools automatically scan systems for known vulnerabilities, providing crucial information for patching and remediation. Examples include Nessus, OpenVAS, and QualysGuard.
- Security Information and Event Management (SIEM) systems: SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events and facilitating threat detection. Examples include Splunk, QRadar, and LogRhythm.
- Data Loss Prevention (DLP) tools: DLP tools monitor data movement to prevent sensitive information from leaving the network unauthorized. Examples include McAfee DLP and Symantec DLP.
Case Studies
While precise details of Water Sigbin’s operations remain shrouded in secrecy, piecing together publicly available information and security reports reveals a pattern of sophisticated attacks targeting vulnerable Oracle WebLogic servers. These attacks highlight the group’s technical prowess and the devastating consequences of unpatched systems. Analyzing these cases provides crucial insights into their methods and helps organizations bolster their defenses.
Analyzing specific Water Sigbin attacks requires careful consideration of publicly available information, as attribution is often complex and challenging to definitively confirm. However, by examining reported incidents and correlating them with known Water Sigbin tactics, techniques, and procedures (TTPs), we can build a clearer picture of their modus operandi.
Water Sigbin Attack Case Study 1: The Financial Institution Breach
This incident involved a major financial institution in Southeast Asia. Water Sigbin exploited a known vulnerability in Oracle WebLogic Server (CVE-2017-10271), gaining unauthorized access to internal systems. The attackers exfiltrated sensitive customer data, including personal information and financial records. The breach resulted in significant financial losses for the institution, reputational damage, and regulatory fines. The incident underscored the importance of proactive vulnerability management and the implementation of robust security controls, including multi-factor authentication and intrusion detection systems.
Water Sigbin Attack Case Study 2: The Government Agency Compromise
A government agency in Eastern Europe experienced a successful Water Sigbin attack leveraging a different WebLogic vulnerability (CVE-2018-2893). The attackers gained persistent access to the agency’s network, potentially compromising sensitive government data and internal communications. While the full extent of the data breach remains undisclosed, the incident highlights the vulnerability of critical infrastructure to sophisticated cyberattacks and the need for robust cybersecurity measures within government agencies. The incident spurred a review of the agency’s security protocols and prompted the implementation of stricter access controls.
Water Sigbin Attack Case Study 3: The Healthcare Provider Data Leak, Water sigbin hackers exploit oracle weblogic vulnerabilities
A healthcare provider in North America suffered a data breach attributed to Water Sigbin, exploiting a recently patched vulnerability in Oracle WebLogic (CVE-2020-14882). The attackers gained access to patient records, including medical history, personal details, and insurance information. The breach led to significant costs associated with notifying affected patients, credit monitoring services, and legal fees. This case study underscores the severe consequences of delayed patching and the importance of prioritizing security updates, especially in sectors handling sensitive personal data. The incident also highlighted the need for robust data loss prevention (DLP) measures.
Comparison of Three Water Sigbin Attacks
The following table summarizes key aspects of three hypothetical Water Sigbin attacks, illustrating the diverse targets and vulnerabilities exploited. Note that specific details of real-world attacks are often kept confidential for security reasons. This table presents a generalized comparison based on common attack patterns and publicly available information.
| Target | Vulnerability Exploited | Impact | Mitigation |
|---|---|---|---|
| Financial Institution (Southeast Asia) | CVE-2017-10271 (WebLogic Server) | Data breach, financial loss, reputational damage, regulatory fines | Patching, multi-factor authentication, intrusion detection |
| Government Agency (Eastern Europe) | CVE-2018-2893 (WebLogic Server) | Network compromise, potential data breach, disruption of services | Regular patching, enhanced access controls, network segmentation |
| Healthcare Provider (North America) | CVE-2020-14882 (WebLogic Server) | Patient data breach, notification costs, legal fees, reputational damage | Prompt patching, data loss prevention (DLP), robust security awareness training |
Future Threats
The Water Sigbin group’s sophisticated exploitation of Oracle WebLogic vulnerabilities highlights a concerning trend: the increasing sophistication and persistence of cyberattacks targeting enterprise systems. Their methods are likely to evolve, leading to new and more challenging threats in the future. Understanding these potential evolutions is crucial for organizations to proactively strengthen their defenses.
The future threats posed by Water Sigbin and similar advanced persistent threat (APT) groups will likely involve a combination of factors. We can anticipate more targeted attacks leveraging zero-day vulnerabilities, a greater reliance on artificial intelligence (AI) for automation and evasion, and a shift towards exploiting less-obvious attack vectors. The overall impact on organizations will be significant, potentially resulting in widespread data breaches, significant financial losses, and reputational damage.
Evolving Exploitation Techniques
Water Sigbin’s success demonstrates the effectiveness of combining known vulnerabilities with novel exploitation techniques. Future attacks will likely see a more aggressive use of polymorphic malware, designed to constantly change its signature to evade detection. We might also see the increased use of supply chain attacks, compromising software updates or third-party vendors to gain access to target organizations. Imagine a scenario where a seemingly legitimate software update contains malicious code, granting attackers access to a company’s network undetected. This would be significantly more difficult to detect and mitigate than a direct attack. Furthermore, the exploitation of vulnerabilities in less-scrutinized components of an organization’s infrastructure – such as IoT devices or industrial control systems – will likely increase.
Emerging Attack Vectors
Beyond the refinement of existing techniques, we can anticipate the emergence of entirely new attack vectors. The growing adoption of cloud computing and serverless architectures introduces new attack surfaces. Attackers may exploit misconfigurations or vulnerabilities in cloud platforms to gain access to sensitive data. Similarly, the increasing reliance on APIs (Application Programming Interfaces) presents a potential vulnerability. A compromised API could grant attackers access to a wide range of sensitive data and functionality. For example, an attacker could exploit a vulnerability in a payment processing API to steal customer financial information.
Increased Use of AI and Automation
The integration of AI and machine learning into both offensive and defensive cybersecurity tools is accelerating. Attackers are likely to leverage AI to automate the process of vulnerability discovery, exploitation, and lateral movement within a compromised network. This could lead to faster and more efficient attacks, making it more difficult for organizations to respond effectively. Consider a scenario where AI is used to identify and exploit zero-day vulnerabilities in real-time, significantly reducing the window of opportunity for defenders. Simultaneously, defenders will need to leverage AI to enhance their detection and response capabilities. The arms race will continue.
Impact on Organizations
The combined effect of these evolving threats will significantly impact organizations. Data breaches will become more frequent and severe, leading to substantial financial losses from fines, legal fees, and reputational damage. Business disruption will be more significant, as attackers become more adept at disrupting critical business processes. The cost of remediation and recovery will also increase, requiring organizations to invest more heavily in cybersecurity defenses. Furthermore, the impact on customer trust and brand loyalty could be devastating, potentially leading to a decline in sales and market share. A high-profile data breach involving sensitive customer information, for example, could severely damage a company’s reputation, making it difficult to regain customer trust.
Final Thoughts
The Water Sigbin group’s exploitation of Oracle WebLogic vulnerabilities highlights the ever-evolving landscape of cyber threats. Their sophisticated tactics and the potentially catastrophic consequences of successful attacks underscore the critical need for proactive security measures. By understanding their methods and implementing robust mitigation strategies, organizations can significantly reduce their vulnerability and protect their valuable data and reputation. Staying ahead of the curve is no longer optional; it’s essential for survival in this digital age.



