Telegram Users Beware SpyMax: Your seemingly secure chats might not be so private after all. This insidious malware, SpyMax, is silently infiltrating Telegram accounts, stealing data, and leaving users vulnerable. We’ll dive deep into how SpyMax works, the telltale signs of infection, and, most importantly, how to protect yourself from this digital threat. This isn’t your grandma’s phishing scam; this is a sophisticated attack targeting one of the world’s most popular messaging apps.
SpyMax leverages vulnerabilities in different Telegram clients, exploiting weaknesses to gain access to your private messages, photos, contacts, and even location data. Understanding its methods is crucial to safeguarding your privacy. We’ll break down the various ways SpyMax infiltrates your device, from malicious links in seemingly harmless messages to vulnerabilities in less secure Telegram apps. Prepare to arm yourself with the knowledge to fight back.
Understanding SpyMax’s Threat to Telegram Users
SpyMax, a sophisticated piece of malware, poses a significant threat to Telegram users’ privacy and security. While details about its exact functionality remain scarce due to its clandestine nature, understanding its potential capabilities is crucial for safeguarding your digital life. This exploration delves into the ways SpyMax might compromise your Telegram account and the data it could potentially access.
SpyMax’s Functionality and Impact on User Privacy
SpyMax likely operates as a sophisticated keylogger and data exfiltration tool specifically targeting Telegram. Its primary goal is to steal sensitive information from unsuspecting users. This could involve intercepting messages, accessing contact lists, stealing media files, and even monitoring user activity within the app. The impact on privacy is substantial, ranging from minor inconveniences to severe breaches of confidentiality and potential identity theft. Imagine a scenario where your financial details, shared privately via Telegram, fall into the wrong hands – the consequences could be devastating.
Methods of Data Access
SpyMax might employ various methods to gain access to user data. One common tactic is through phishing campaigns, where users are tricked into downloading malicious attachments or clicking on compromised links disguised as legitimate Telegram updates or messages. Another potential route is via compromised third-party apps or Telegram clients. These apps might contain hidden malware that grants SpyMax access to your account and data without your knowledge. Finally, zero-day exploits, vulnerabilities in the Telegram app itself (though rare), could also be leveraged by SpyMax to infiltrate user accounts.
Types of Information Stolen
The range of information SpyMax could steal is extensive. This includes, but is not limited to: text messages, voice notes, photos, videos, contact lists, location data, and even sensitive financial information exchanged through the platform. The potential for damage extends beyond the individual; stolen data could also be used to target organizations or groups through compromised communications. Consider the impact of a malicious actor gaining access to confidential business discussions or strategic planning within a company’s Telegram group.
Vulnerabilities of Different Telegram Clients
The table below highlights the potential vulnerabilities of various Telegram clients in relation to SpyMax. It’s crucial to remember that these are potential vulnerabilities, and the actual level of risk depends on various factors, including the specific version of the client and the user’s security practices. Always prioritize using the official Telegram app from reputable sources.
| Client Name | Vulnerability Level | Description of Vulnerability | Mitigation Strategies |
|---|---|---|---|
| Official Telegram App (Android/iOS) | Low | While generally secure, zero-day exploits are always a possibility. | Keep the app updated to the latest version. Enable two-factor authentication. |
| Third-party Telegram Clients (Unofficial) | Medium to High | These clients often lack rigorous security audits and may contain vulnerabilities. | Avoid using unofficial clients. Stick to the official app from trusted sources. |
| Modified/Cracked Telegram Apps | High | These apps are highly susceptible to malware and data breaches. | Never download or use modified or cracked versions of the Telegram app. |
| Telegram Web | Medium | Vulnerable if accessed through untrusted networks or compromised devices. | Use Telegram Web only on trusted networks and devices. Ensure your device is protected with strong anti-malware software. |
Identifying Indicators of SpyMax Compromise
SpyMax, a sophisticated piece of Telegram malware, operates subtly, making detection challenging. Understanding the telltale signs of compromise is crucial for protecting your account and data. Recognizing these indicators early allows for swift action, minimizing potential damage. This section details the key warning signs to watch out for.
A compromised Telegram account can exhibit various anomalies, from unexpected message activity to changes in privacy settings. Suspicious links and unusual login attempts are also strong indicators. Prompt identification of these signs is essential to prevent further exploitation.
Suspicious Activity in Telegram Chats and Groups
Unusual behavior within your Telegram chats and groups can signal a SpyMax infection. This includes unexpected messages sent from your account, joining groups you didn’t authorize, or sharing content you wouldn’t typically post. Pay close attention to any messages you don’t remember sending, especially those containing links or requesting personal information. A sudden increase in the number of groups you’re a member of, without your explicit action, is another significant red flag. Consider the context of any unexpected messages – are they consistent with your usual communication style? If not, investigate further.
Warning Signs of SpyMax Compromise
Several warning signs can indicate a potential SpyMax compromise. These signs, taken individually or collectively, should prompt immediate action.
- Unauthorized messages sent from your account: Messages you didn’t send, often containing links or spam.
- Unexpected group additions: Your account joining groups without your knowledge or consent.
- Changes in privacy settings: Alterations to your profile visibility, contact list access, or two-factor authentication settings.
- Unusual login attempts: Notifications of logins from unfamiliar devices or locations.
- Slow performance or app crashes: SpyMax might consume significant resources, leading to performance issues.
- High data usage: Unexplained increases in data consumption could point to background activity by SpyMax.
- Battery drain: Excessive battery drain can indicate malicious processes running in the background.
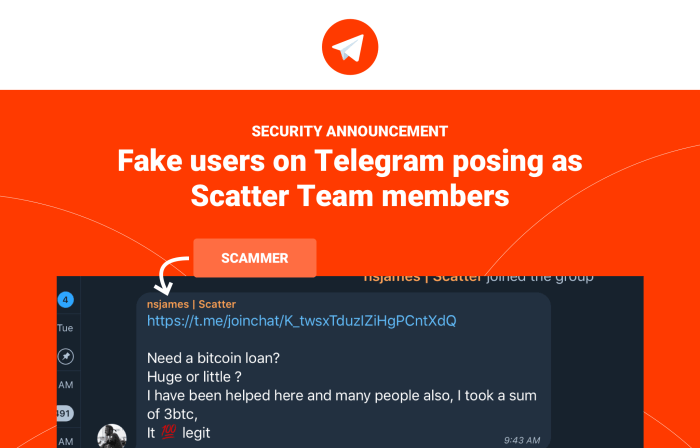
Identifying Phishing Attempts and Malicious Links
SpyMax often spreads through phishing attempts and malicious links. These are designed to trick users into revealing sensitive information or downloading the malware. Be cautious of any links received from unknown sources or links that seem out of context within a conversation.
Examples include links disguised as legitimate Telegram updates, promising exclusive content or offering enticing rewards. These links often lead to websites designed to steal your login credentials or install SpyMax on your device. Always verify the authenticity of links before clicking them. Hovering over the link to see the actual URL is a simple yet effective precaution.
One example of a phishing attempt might be a message claiming your Telegram account has been flagged for suspicious activity and requesting you to click a link to verify your details. Another might be a message containing a link to a supposed “new Telegram feature” which actually downloads malware.
Flowchart for Suspected SpyMax Compromise
This flowchart Artikels the steps to take if you suspect your Telegram account has been compromised by SpyMax.
Step 1: Identify suspicious activity (unusual messages, group additions, etc.)
Step 2: Check for unauthorized login attempts.
Step 3: Review privacy settings for any unauthorized changes.
Step 4: Change your Telegram password immediately.
Step 5: Enable two-factor authentication.
Step 6: Scan your device for malware using a reputable antivirus program.
Step 7: Report the compromise to Telegram support.
Step 8: Contact your device manufacturer for additional support if necessary.
Protecting Yourself from SpyMax
Source: medium.com
SpyMax, a malicious Telegram bot, poses a significant threat to user privacy and security. Understanding its tactics is crucial, but equally important is knowing how to actively defend yourself. By implementing robust security practices, you can significantly reduce your risk of compromise. This section Artikels practical steps to safeguard your Telegram account.
Protecting your Telegram account from SpyMax and similar threats requires a multi-layered approach. It’s not about one single action, but rather a combination of best practices that work together to create a robust defense. Think of it like building a fortress: strong walls (passwords), sturdy gates (two-factor authentication), and vigilant guards (anti-malware).
Strong Passwords and Two-Factor Authentication
A strong password is the first line of defense against unauthorized access. It should be long (at least 12 characters), complex (using a mix of uppercase and lowercase letters, numbers, and symbols), and unique to your Telegram account. Avoid using easily guessable information like birthdays or pet names. Crucially, never reuse passwords across different accounts. If one account is compromised, the attacker might gain access to others using the same password. Two-factor authentication (2FA) adds an extra layer of security. This typically involves receiving a code via SMS or an authenticator app to your phone each time you log in, even if someone knows your password. Enabling 2FA makes it exponentially harder for attackers to access your account, even if they obtain your password through phishing or other means. Think of it as a second lock on your digital front door.
Reputable Anti-Malware Software
Employing reputable anti-malware software is vital. Such software actively scans your devices for malicious code, including spyware like SpyMax. Regularly updating your anti-malware software is crucial, as new threats emerge constantly. A well-maintained anti-malware program acts as a crucial shield against malicious downloads or links that might compromise your device and, subsequently, your Telegram account. Imagine it as a security system that constantly monitors for intruders and alerts you to potential threats. Remember that SpyMax often spreads through malicious links or files, so proactively scanning any suspicious content before interaction is essential.
Security Best Practices for Telegram
Prioritizing security on Telegram involves more than just strong passwords and 2FA. Regularly reviewing your connected devices and sessions is key. Telegram allows you to see all the devices currently logged into your account; if you spot an unfamiliar device, immediately log out of that session. Avoid clicking on suspicious links or downloading files from untrusted sources. Treat every unfamiliar message or request with extreme caution. Phishing attempts are common; legitimate Telegram representatives will never ask for your password or other sensitive information. Be mindful of the privacy settings within Telegram; carefully review and adjust them to control the information shared with others. Keeping your Telegram app updated to the latest version is crucial as updates often include security patches that address newly discovered vulnerabilities.
Reporting SpyMax Activity
So, you suspect SpyMax is messing with your Telegram? Don’t panic, but definitely don’t ignore it. Reporting suspicious activity is crucial, not just for your own security but for the safety of the entire Telegram community. Taking swift action can help prevent others from falling victim to this sneaky malware.
Reporting a potential SpyMax infection isn’t just about clicking a button; it’s about providing Telegram with the information they need to take down the threat and improve their security measures. The more detailed your report, the better equipped they are to respond effectively.
Telegram’s Reporting Channels
Telegram offers various avenues for reporting security breaches. These channels ensure that your concerns reach the right people, allowing for a coordinated response to threats like SpyMax. While Telegram doesn’t publicly list a specific “SpyMax reporting” channel, utilizing their general security reporting methods is the best approach.
Reporting Security Breaches
The primary method is through Telegram’s in-app reporting features. This usually involves navigating to the settings, finding a section related to “Report a Problem” or “Help,” and then detailing your suspicions about SpyMax. Be sure to include as much detail as possible, such as: when you first noticed suspicious activity, any unusual messages or links you received, and any changes in your account behavior. Screenshots are also incredibly helpful.
Resources for Compromised Accounts, Telegram users beware spymax
If you believe your account has been compromised by SpyMax, immediate action is necessary. Beyond reporting the incident, you should change your Telegram password immediately. Consider enabling two-factor authentication (2FA) for an extra layer of security. Review your connected devices and revoke access from any unfamiliar ones. Finally, inform your contacts about the potential compromise and warn them about suspicious messages or links that might originate from your account.
Securing a Compromised Account
Securing your account after a SpyMax attack involves several crucial steps. First, immediately change your password to something strong and unique. Then, enable two-factor authentication (2FA) to add an extra layer of security. This usually involves receiving a code via another method, like your email or a dedicated authentication app, before logging in. Next, review your connected devices and revoke access to any that you don’t recognize. This helps prevent unauthorized access from compromised devices. Finally, scan your devices with a reputable antivirus program to remove any lingering SpyMax malware.
The Broader Implications of SpyMax: Telegram Users Beware Spymax

Source: indiatvnews.com
SpyMax, initially identified as a threat targeting Telegram users, possesses a far-reaching potential for malicious activities extending beyond the confines of this single messaging platform. Its modular design and capabilities suggest a versatility that could easily adapt to other communication channels and operating systems, posing a significant threat to digital security on a wider scale.
The insidious nature of SpyMax lies in its ability to silently infiltrate devices, granting malicious actors access to sensitive personal data and communications. This capability transcends the boundaries of Telegram, potentially compromising other apps, files, and systems on the infected device. Understanding its broader implications is crucial for developing effective countermeasures and mitigating the risk of widespread exploitation.
SpyMax’s Potential for Wider Malicious Use
SpyMax’s architecture, likely designed for covert surveillance and data exfiltration, could easily be repurposed for various malicious activities. Imagine its use in corporate espionage, where sensitive business information is stolen, or in targeted attacks against individuals, where personal data is harvested for identity theft or blackmail. The potential for financial fraud is also significant, with SpyMax potentially facilitating access to banking apps and online payment systems. The adaptability of its core functionality makes it a potent tool in the hands of malicious actors, posing a significant threat across numerous sectors.
Comparison with Similar Malware
SpyMax shares similarities with other malware targeting messaging apps, such as Pegasus and various stalkerware applications. However, a key difference might lie in its specific capabilities and the sophistication of its evasion techniques. While other malware might focus primarily on data exfiltration, SpyMax’s potential for remote control and command execution suggests a more advanced and dangerous profile. This highlights the need for continuous vigilance and the development of advanced security measures to combat evolving threats. The constant arms race between malware developers and security researchers underscores the dynamic nature of this threat landscape.
Legal Ramifications of SpyMax Use and Distribution
The creation, distribution, and use of SpyMax carry severe legal consequences. Depending on the jurisdiction, individuals involved could face charges ranging from unauthorized access to computer systems and data theft to conspiracy and fraud. The penalties can include substantial fines and imprisonment. International cooperation is crucial in tracking down those responsible for developing and disseminating such malicious software, as SpyMax’s potential impact transcends national borders. The severity of the consequences underscores the importance of ethical considerations in the development and use of any software.
Visual Representation of SpyMax’s Spread
Imagine a spiderweb. The center represents the initial source of SpyMax, perhaps a compromised website or a malicious email attachment. From this center, radiating outwards are various threads representing different vectors of infection. Some threads might represent phishing emails, others compromised apps or malicious links shared on social media platforms. Each intersection point on the web signifies a new infected device, which then becomes a potential source of further spread, extending the web’s reach further. The web’s intricate design illustrates the rapid and unpredictable nature of SpyMax’s dissemination. The constant expansion of the web represents the escalating threat posed by this malware if left unchecked.
Final Summary
Source: voi.id
In the ever-evolving landscape of online security, staying ahead of the curve is paramount. SpyMax serves as a stark reminder that even seemingly secure platforms can be vulnerable. By understanding the threats, implementing robust security practices, and staying vigilant, you can significantly reduce your risk of becoming a victim. Don’t wait until it’s too late; take control of your digital security today. Remember, your privacy is worth fighting for.



