eSIM and physical SIM card security: These tiny pieces of plastic and embedded chips hold the keys to our digital lives. But how safe are they, really? From the potential for theft and cloning to the vulnerabilities of remote provisioning, the security landscape surrounding both eSIMs and their traditional counterparts is surprisingly complex. This deep dive explores the strengths and weaknesses of each, revealing the surprising ways they differ—and the crucial security measures you need to know.
We’ll dissect the security features of both eSIMs and physical SIMs, comparing their vulnerabilities to unauthorized access, theft, and cloning. We’ll also explore the roles of mobile network operators, device manufacturers, and users in maintaining a secure mobile ecosystem. Get ready to level up your understanding of SIM card security!
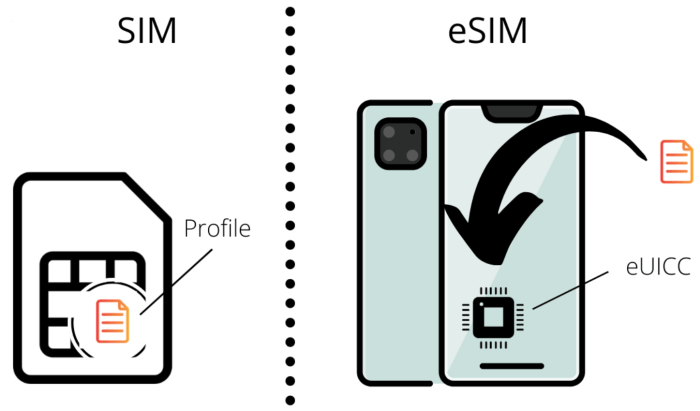
eSIM vs. Physical SIM
The debate between eSIM and physical SIM cards often centers around convenience, but a crucial aspect frequently overlooked is security. Both technologies present unique vulnerabilities, and understanding these differences is vital for making informed choices about mobile security. This comparison delves into the security implications of each, examining the potential risks and comparing their inherent strengths and weaknesses.
Both eSIM and physical SIM cards store sensitive information, including your mobile phone number and network credentials. However, the way this information is accessed and protected differs significantly, leading to varying levels of security risk. Physical SIM cards, being tangible objects, are susceptible to a different set of threats than their embedded counterparts.
Physical Security Vulnerabilities of eSIM and Physical SIM Cards
Physical SIM cards, due to their physical nature, are vulnerable to theft, loss, and physical damage. A stolen SIM card can be easily inserted into another phone, granting unauthorized access to the associated account. Furthermore, cloning a physical SIM card, though technically challenging, is possible, allowing malicious actors to duplicate the card and gain access to the account. Physical damage can also render the card unusable, potentially leading to service disruption.
eSIMs, while offering a more integrated solution, are not immune to security risks. While they are less susceptible to physical theft or damage, malicious software or a compromised device could potentially allow unauthorized access to the eSIM profile. Furthermore, vulnerabilities in the device’s operating system or the eSIM management system could theoretically be exploited to gain control over the eSIM and associated account.
Potential Risks Associated with Each SIM Card Type, Esim and physical sim card security
The potential risks associated with each SIM type extend beyond simple theft. For physical SIM cards, cloning remains a significant concern. Sophisticated techniques can create near-perfect replicas, granting access to the account and potentially allowing interception of communications or unauthorized data access. For eSIMs, the risk is more centered on software vulnerabilities and remote attacks. A compromised device or a flaw in the eSIM management system could potentially allow remote access and control of the eSIM profile, leading to similar consequences as physical SIM cloning.
Comparison of eSIM and Physical SIM Card Security Features
The following table provides a direct comparison of the security features of eSIM and physical SIM cards, highlighting their relative strengths and weaknesses.
| Feature | eSIM Security | Physical SIM Security | Overall Security Assessment |
|---|---|---|---|
| Physical Theft/Loss | Very Low (integrated) | High (easily stolen/lost) | eSIM significantly more secure |
| Cloning | Low (requires sophisticated software exploits) | Moderate (technically possible, but challenging) | eSIM more secure |
| Software Vulnerabilities | Moderate (dependent on device and eSIM management system security) | Low (less susceptible to software attacks) | Physical SIM more secure |
| Unauthorized Access | Moderate (requires device compromise or system exploit) | High (easily accessible if physically obtained) | eSIM more secure |
| Data Encryption | High (typically utilizes strong encryption) | Moderate (encryption level varies depending on the SIM card and carrier) | eSIM generally more secure |
Remote SIM Provisioning Security
Remote SIM Provisioning (RSP) offers incredible convenience, allowing you to activate eSIMs remotely without needing a physical SIM card. However, this convenience comes with increased security risks. The entire process, from initial request to profile installation, presents a juicy target for cybercriminals looking to exploit vulnerabilities and gain unauthorized access to your mobile device and its associated services. Understanding these risks and implementing robust security measures is crucial.
The core of RSP security lies in ensuring only authorized parties can provision eSIM profiles. This involves a complex interplay of authentication, authorization, and secure communication channels. A compromised RSP system could lead to unauthorized access to your mobile network, data breaches, and even identity theft. Think of it like this: your phone is a fortress, and RSP is the gatekeeper. If the gatekeeper is compromised, the fortress is vulnerable.
Attack Vectors in Remote SIM Provisioning
Several points of attack exist within the RSP process. Malicious actors could target the mobile network operator’s (MNO) servers responsible for managing eSIM profiles, attempting to intercept or manipulate provisioning commands. They might also try to compromise the eSIM itself through firmware vulnerabilities or by targeting the device’s operating system. Another attack vector involves phishing or social engineering attacks aimed at tricking users into revealing their credentials or installing malicious software. Imagine a sophisticated phishing campaign disguised as a legitimate eSIM activation email, leading unsuspecting users to a fake website where their data is harvested. The consequences could be severe.
Authentication and Authorization in Securing RSP
Robust authentication and authorization mechanisms are paramount in securing RSP. Multi-factor authentication (MFA), combining something you know (password), something you have (phone), and something you are (biometrics), significantly strengthens security. Authorization ensures that only legitimate requests are processed. This involves verifying the identity of the requesting entity (e.g., the MNO or a trusted third-party) and ensuring that the requested action is permitted. Think of it as a double-layered security system – one to verify your identity and another to check if you have permission to perform the requested action. Without these checks, a malicious actor could potentially impersonate an authorized entity and gain access to sensitive information.
Best Practices for Securing Remote SIM Provisioning
Implementing strong security measures is crucial for mitigating the risks associated with RSP. Here are some best practices:
- Employ strong encryption throughout the entire RSP process, protecting sensitive data in transit and at rest.
- Implement robust authentication mechanisms, such as MFA, to verify the identity of both the user and the requesting entity.
- Regularly update and patch the eSIM firmware and the device’s operating system to address known vulnerabilities.
- Utilize secure communication protocols, such as TLS 1.3 or higher, to protect data transmitted during the RSP process.
- Implement rigorous access control measures to limit access to the RSP system and sensitive data.
- Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
- Educate users about phishing and social engineering attacks to prevent them from falling victim to malicious actors.
eSIM and Mobile Network Operator Security
The shift towards eSIM technology presents both opportunities and challenges for mobile network operators (MNOs). While offering greater flexibility and convenience for users, it also necessitates robust security measures to protect sensitive subscriber data and prevent fraud. MNOs play a crucial role in ensuring the secure implementation and operation of eSIM technology, safeguarding their network and their customers.
eSIM security is not solely reliant on the technology itself; it’s heavily dependent on the security practices and protocols implemented by the MNOs. These operators are responsible for the entire lifecycle of the eSIM, from its initial provisioning to its eventual deactivation. A failure in any part of this process can lead to significant security vulnerabilities.
MNO Responsibilities in eSIM Security
MNOs have a multi-faceted responsibility in eSIM security. This includes establishing secure processes for eSIM profile creation, distribution, and management. They must implement strong authentication and authorization mechanisms to prevent unauthorized access and modification of eSIM data. Furthermore, MNOs need to regularly update their security protocols and conduct thorough security audits to identify and address any vulnerabilities. Failure to do so could lead to SIM swapping attacks, unauthorized access to user data, and other serious security breaches. The reputational damage and financial losses from such breaches could be substantial.
Security Protocols and Measures Employed by MNOs
Several security protocols and measures are commonly employed by MNOs to protect eSIM data. These often involve the use of strong encryption algorithms to protect sensitive information during transmission and storage. For instance, AES-256 encryption is widely used to secure eSIM profile data. Furthermore, MNOs typically implement secure remote provisioning systems, employing techniques like digital signatures and certificates to authenticate the origin and integrity of eSIM profiles. Multi-factor authentication (MFA) is another crucial element, adding an extra layer of security to the eSIM provisioning and management processes. This could involve a one-time password (OTP) sent to the user’s registered email or phone number.
eSIM Profile Management and Security
MNOs manage eSIM profiles using specialized systems that incorporate several security controls. These systems usually include robust access control mechanisms to limit who can access and modify eSIM data. Detailed audit trails are maintained to track all actions performed on eSIM profiles, enabling the detection of unauthorized activity. Regular security updates and patches are applied to these systems to address any newly discovered vulnerabilities. Furthermore, MNOs typically implement procedures for remotely deactivating or locking eSIM profiles in case of suspected compromise or theft. This ensures that even if an eSIM is stolen, the MNO can quickly prevent its misuse. For example, if a user reports their device lost or stolen, the MNO can remotely disable the eSIM, preventing access to their mobile services. This process is often integrated with the MNO’s broader customer support systems to ensure a swift and efficient response to security incidents.
Device-Level Security for eSIMs
eSIM technology, while offering convenience, introduces new security challenges. The security of your eSIM isn’t solely reliant on network operators or the eSIM profile itself; a significant portion rests on the security features built into your device by the manufacturer. Think of it like this: the eSIM is the key, but the device is the secure vault protecting it. Let’s delve into how manufacturers bolster eSIM security.
Device manufacturers employ a multi-layered approach to protect eSIMs, integrating hardware and software safeguards to create a robust security posture. This involves secure hardware components, tamper-resistant designs, and sophisticated software mechanisms working in concert to prevent unauthorized access and manipulation.
Hardware Security Measures
Hardware security plays a crucial role in protecting eSIM data. This involves the use of dedicated, secure elements (SEs) – specialized chips designed to protect cryptographic keys and sensitive data. These SEs are physically isolated from the rest of the device’s circuitry, making them significantly more difficult to compromise. They often incorporate features like anti-tamper mechanisms that render the chip unusable if someone attempts to physically access or modify it. For instance, some SEs might include sensors that detect physical intrusion attempts, immediately wiping the data or rendering the chip inoperable. This physical isolation, combined with strong cryptographic algorithms, creates a strong barrier against unauthorized access. Furthermore, the manufacturing process itself often includes rigorous quality control measures to prevent vulnerabilities from being introduced during the production process.
Software Security Measures: Secure Boot and Beyond
Beyond hardware, robust software security is paramount. Secure boot is a critical component, ensuring that only authorized software is loaded during the device’s startup process. This prevents malicious software from gaining control before the security mechanisms are fully operational. This is achieved through a chain of trust, verifying each component’s digital signature before allowing it to execute. A compromised secure boot process could allow attackers to load modified firmware that bypasses eSIM security measures. Additional software safeguards often include regular software updates that patch known vulnerabilities, as well as sandboxing of the eSIM application to limit its access to other parts of the device’s operating system, preventing malicious code from interfering with the eSIM’s operation.
Risks Associated with Compromised Device Firmware
Compromised device firmware presents a significant threat to eSIM security. If an attacker gains control of the device’s firmware, they could potentially bypass the hardware and software security measures designed to protect the eSIM. This could allow them to access the eSIM profile, clone it, or even remotely control the device’s cellular connectivity. For example, a compromised firmware could disable the secure element’s protection mechanisms, granting access to the cryptographic keys used to protect the eSIM. This scenario highlights the critical need for manufacturers to prioritize firmware security and implement robust update mechanisms to quickly address vulnerabilities. The implications of such a compromise can be severe, including identity theft, unauthorized access to sensitive data, and even potential surveillance.
Secure Boot and its Role in eSIM Protection
Secure boot plays a pivotal role in preventing unauthorized access to the eSIM. By verifying the authenticity of each software component during startup, secure boot ensures that only trusted software, including the eSIM management software, can run. This prevents attackers from injecting malicious code that could manipulate the eSIM or access its data. A well-implemented secure boot process significantly enhances the overall security of the eSIM by creating a trusted foundation for the entire system. Any attempt to bypass the secure boot process would trigger security alerts, potentially preventing a successful attack. This layered approach, combining secure hardware and a robust secure boot process, creates a much more resilient security posture than relying on a single security mechanism.
Software Security Vulnerabilities and eSIMs
Source: esimdb.com
eSIMs, while offering convenience and flexibility, introduce a new attack surface for malicious actors. Unlike physical SIMs which are largely protected by their physical form, the software-based nature of eSIMs makes them susceptible to various software vulnerabilities that could compromise user data and privacy, potentially leading to identity theft, unauthorized access to accounts, and financial fraud. Understanding these vulnerabilities and implementing robust mitigation strategies is crucial for ensuring the secure adoption of eSIM technology.
The software running on a device and interacting with the eSIM, including the operating system and associated applications, presents several potential entry points for attacks. These vulnerabilities can range from simple coding errors to sophisticated exploits targeting specific functionalities within the eSIM management system. Exploiting these vulnerabilities could allow attackers to gain unauthorized access to the eSIM profile, clone it, or even remotely control the device.
The Role of the Secure Element in Mitigating Software Vulnerabilities
The Secure Element (SE) acts as a hardware-based fortress within the device, protecting sensitive cryptographic keys and eSIM profile data from software-based attacks. Even if an attacker compromises the device’s software, the data stored within the SE remains relatively secure. The SE uses specialized hardware and tamper-resistant design to prevent unauthorized access and manipulation. This isolation significantly limits the impact of software vulnerabilities, preventing attackers from directly accessing or modifying the eSIM profile. The SE performs cryptographic operations in a trusted environment, ensuring the integrity and confidentiality of the eSIM data. Think of the SE as a highly secure vault within the device, safeguarding the eSIM’s most valuable assets. The effectiveness of the SE depends on its robust design and proper implementation, including regular security updates and patches.
Best Practices for Developers to Enhance eSIM Security in Mobile Applications
Developers play a vital role in securing eSIM technology. Implementing robust security practices during the development process is crucial for mitigating potential vulnerabilities.
Below are some best practices that developers should adhere to:
- Employ Secure Coding Practices: Developers should rigorously follow secure coding guidelines to minimize the risk of introducing vulnerabilities into the applications that interact with the eSIM. This includes techniques such as input validation, output encoding, and secure memory management. Regular code reviews and penetration testing are essential to identify and address potential weaknesses.
- Utilize Secure Communication Channels: All communication between the application and the eSIM, including profile provisioning and authentication requests, should be encrypted using strong, industry-standard protocols such as TLS/SSL. This prevents eavesdropping and manipulation of sensitive data during transmission.
- Implement Robust Authentication and Authorization Mechanisms: Strong authentication mechanisms, such as multi-factor authentication, should be implemented to verify the identity of users and applications accessing the eSIM. Fine-grained authorization controls should be in place to restrict access to specific eSIM functionalities based on user roles and permissions.
- Regular Security Updates and Patching: Regularly updating the operating system and applications interacting with the eSIM is crucial for addressing known vulnerabilities. Promptly applying security patches is essential to minimize the risk of exploitation.
- Minimize Data Exposure: Applications should only access and process the minimum amount of eSIM data necessary for their functionality. This limits the potential impact of a data breach, reducing the amount of sensitive information that could be compromised.
- Employ Secure Storage Mechanisms: Sensitive data related to the eSIM, such as profile information and cryptographic keys, should be stored securely using hardware-backed security mechanisms whenever possible, leveraging the capabilities of the SE.
User-Level Security Practices for eSIMs

Source: gigago.com
Your eSIM, while offering convenience, is a digital key to your mobile connectivity. Protecting it requires a proactive approach that goes beyond simply keeping your phone safe. Think of it like guarding your front door – you wouldn’t leave it unlocked, would you? The same vigilance applies to your eSIM. This section details essential practices to safeguard your eSIM from unauthorized access and malicious attacks.
Protecting your eSIM involves a multi-layered approach, combining robust password practices, awareness of potential threats, and vigilant monitoring of your device’s health. Ignoring these steps could leave your mobile data and personal information vulnerable.
Strong Passwords and Multi-Factor Authentication
Strong passwords are the first line of defense against unauthorized access to your eSIM. Avoid easily guessable passwords like “password123” or your birthday. Instead, opt for complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Aim for a minimum length of 12 characters, and consider using a password manager to generate and securely store these complex passwords. Furthermore, enabling multi-factor authentication (MFA) adds an extra layer of security. MFA typically involves a second verification step, such as a code sent to your email or a notification on a trusted device, making it significantly harder for unauthorized individuals to gain access even if they obtain your password. Think of MFA as adding a second lock to your front door – it’s an extra hurdle for intruders to overcome.
Protecting Devices from Malware
Malware, or malicious software, can compromise your device and potentially target your eSIM. Regularly updating your device’s operating system and apps is crucial. These updates often include security patches that address known vulnerabilities. Avoid downloading apps from untrusted sources and be wary of phishing attempts that may try to trick you into installing malicious software. A reputable antivirus app can also provide an additional layer of protection by scanning your device for malware and removing any threats it detects. Consider it a security guard for your digital life, constantly scanning for potential threats. Regularly backing up your data is also crucial. This ensures that you can restore your information if your device becomes compromised.
Best Practices for eSIM Security
Implementing a few key practices can significantly enhance your eSIM’s security. Regularly review your device’s security settings to ensure that all security features are enabled. Be cautious when connecting to public Wi-Fi networks, as these networks can be vulnerable to attacks. Consider using a VPN (Virtual Private Network) when connecting to public Wi-Fi to encrypt your data and protect your privacy. Avoid jailbreaking or rooting your device, as this can compromise its security and make it more vulnerable to attacks. Finally, be aware of suspicious activity on your account, such as unexpected charges or changes to your settings. Report any suspicious activity to your mobile network operator immediately. These practices are like regularly servicing your car – preventative measures that help avoid major issues down the road.
Future Trends in eSIM Security
The world of eSIM security is constantly evolving, driven by the increasing adoption of connected devices and the expansion of high-bandwidth networks like 5G. Future advancements will focus on strengthening existing security measures and implementing innovative technologies to counter emerging threats. This involves a multi-layered approach encompassing hardware, software, and network security protocols.
Emerging technologies and enhanced security protocols will play a pivotal role in shaping the future of eSIM security. The convergence of hardware-based security elements with advanced cryptographic techniques will create a more robust and resilient ecosystem. This will involve a shift towards more sophisticated authentication methods and improved protection against cloning and unauthorized access.
Hardware-Based Security Enhancements
Future eSIMs will likely incorporate more advanced hardware security modules (HSMs) offering stronger cryptographic capabilities and tamper-resistance. These HSMs will be designed to withstand increasingly sophisticated attacks, including physical attacks aimed at extracting sensitive data. For example, we might see the integration of secure enclaves, similar to those used in modern smartphones, to protect the eSIM’s cryptographic keys and operational data from unauthorized access, even if the device itself is compromised. This approach ensures a higher level of protection compared to software-only solutions.
Advanced Cryptographic Techniques
The reliance on robust cryptographic algorithms is paramount. We can expect to see wider adoption of post-quantum cryptography algorithms, designed to withstand attacks from quantum computers, which pose a significant threat to current encryption standards. This proactive measure ensures long-term security against future computational advances. Furthermore, the use of more sophisticated key management systems, including distributed ledger technologies, will enhance the overall security posture.
eSIM Security in IoT and 5G Networks
The Internet of Things (IoT) and 5G networks present both opportunities and challenges for eSIM security. The sheer volume of connected devices in IoT necessitates efficient and scalable security solutions. 5G’s high bandwidth and low latency capabilities, while beneficial, also expand the attack surface. Secure remote provisioning and lifecycle management of eSIMs within these environments will be crucial. This will require the development of standardized security protocols and frameworks specifically tailored to the unique requirements of these networks. For instance, a system that uses blockchain to securely manage eSIM profiles across a large network of IoT devices could be implemented, ensuring authenticity and preventing unauthorized access.
Blockchain Technology in eSIM Security
Blockchain technology offers a promising avenue for enhancing eSIM security. Its decentralized and immutable nature can be leveraged to create a tamper-proof record of eSIM lifecycle events, from provisioning to deactivation. This transparent and auditable system makes it difficult to alter or forge eSIM profiles. A blockchain-based system could track the ownership and usage history of each eSIM, reducing the risk of fraud and unauthorized access. Imagine a scenario where each eSIM’s entire lifecycle – activation, profile updates, and deactivation – is recorded on a blockchain, making any attempt at unauthorized modification immediately apparent. This creates an undeniable audit trail that strengthens security and accountability.
Outcome Summary: Esim And Physical Sim Card Security

Source: airalo.com
Ultimately, the security of your SIM card—whether eSIM or physical—depends on a multi-layered approach. From the robust security measures implemented by MNOs and device manufacturers to your own proactive security habits, every element plays a crucial role. Understanding the unique vulnerabilities of each type, and implementing best practices, is key to safeguarding your personal data and maintaining your digital privacy in an increasingly interconnected world. Stay informed, stay secure.
