Zyxel NAS devices under attack? Yeah, it’s happening more than you think. These seemingly innocuous network-attached storage units, often holding sensitive personal and business data, are becoming prime targets for cybercriminals. From brute-force password cracking to exploiting zero-day vulnerabilities, the methods are diverse and increasingly sophisticated. This isn’t just a tech problem; it’s a potential disaster waiting to happen for anyone relying on these devices for data storage and backup.
This article dives deep into the vulnerabilities, attack vectors, and potential consequences of these attacks, offering practical mitigation strategies and real-world case studies to help you protect your data. We’ll explore how attackers gain access, the types of malware they deploy, and the devastating impact a successful breach can have. Get ready to level up your NAS security game.
Vulnerability Assessment of Zyxel NAS Devices: Zyxel Nas Devices Under Attack
The increasing reliance on Network Attached Storage (NAS) devices for data storage and sharing has unfortunately made them prime targets for cyberattacks. Zyxel NAS devices, while popular for their features and affordability, are not immune to vulnerabilities. Understanding these vulnerabilities and the methods used to exploit them is crucial for bolstering the security of these devices and protecting valuable data.
Common Vulnerabilities Exploited in Zyxel NAS Devices
Several common vulnerabilities have been identified in various Zyxel NAS models, often stemming from outdated firmware, weak default passwords, and insufficient security configurations. These vulnerabilities can range from simple credential stuffing attacks to more sophisticated exploits leveraging remote code execution flaws. Attackers frequently target known vulnerabilities to gain unauthorized access, install malware, or even use the devices as part of larger botnets. One prevalent issue is the lack of robust input validation, allowing attackers to inject malicious code through seemingly innocuous input fields.
Methods Used by Attackers to Compromise Zyxel NAS Devices
Attackers employ various methods to compromise Zyxel NAS devices. These range from brute-force attacks targeting default or weak passwords to exploiting known vulnerabilities in the device’s firmware or web interface. Phishing attacks can also trick users into revealing their credentials, providing attackers with direct access. Once compromised, attackers can gain control over the device, potentially accessing sensitive data, installing ransomware, or using the device as a launchpad for further attacks against other systems on the network. For example, a known vulnerability in older Zyxel NAS models allowed attackers to remotely execute arbitrary code by simply sending a crafted HTTP request.
Comparison of Security Features Across Zyxel NAS Models
Security features vary significantly across different Zyxel NAS models. Newer models generally offer improved security features compared to their older counterparts. Key differences include the availability of HTTPS encryption, robust password policies, and regular firmware updates addressing known vulnerabilities. However, even newer models may still have vulnerabilities if not properly configured or updated. Some models offer advanced features like two-factor authentication and access control lists, which significantly enhance security. Users should carefully review the security features offered by each model before purchasing and ensure they are configured correctly.
Common Vulnerabilities, CVSS Scores, and Potential Impact
| Vulnerability | CVSS Score | Potential Impact |
|---|---|---|
| Remote Code Execution (RCE) | 9.8 (High) | Complete compromise of the device, data theft, ransomware infection |
| Cross-Site Scripting (XSS) | 7.5 (High) | Session hijacking, data theft, malicious code injection |
| Weak Default Credentials | 7.0 (High) | Unauthorized access to the device and its data |
| SQL Injection | 9.0 (Critical) | Database compromise, data theft, system disruption |
Attack Vectors and Techniques
Securing your Zyxel NAS device requires understanding how attackers operate. They employ a range of methods to breach security, from simple brute-force attempts to sophisticated exploitation of vulnerabilities. Knowing these techniques is crucial for effective defense.
Attackers utilize various methods to gain unauthorized access to Zyxel NAS devices, often exploiting weaknesses in the device’s security configuration or software. This section details these common attack vectors and the techniques employed.
Common Attack Vectors
Attackers employ several strategies to penetrate Zyxel NAS devices. These include leveraging known vulnerabilities, brute-forcing credentials, and employing social engineering tactics like phishing. Successful attacks often involve a combination of these methods.
- Brute-force attacks: Attackers use automated tools to try numerous password combinations until they guess the correct credentials. Weak or default passwords are particularly vulnerable to this type of attack. This often targets the administrator account, granting full control.
- Exploiting known vulnerabilities: Attackers actively scan for and exploit publicly known security flaws (vulnerabilities) in the Zyxel NAS firmware. These vulnerabilities can allow for remote code execution, granting complete control of the device.
- Phishing attacks: These attacks trick users into revealing their credentials by sending deceptive emails or messages that appear legitimate. Users might be tricked into clicking malicious links or entering their login details on fake login pages.
Malware Used in Attacks
While specific malware targeting solely Zyxel NAS devices is less common than general-purpose NAS malware, attackers often leverage existing malware families adapted for this purpose. The malware’s goal is typically data exfiltration, ransomware deployment, or establishing a foothold for further attacks.
- Generic NAS malware: Many malware strains are designed to infect various Network Attached Storage devices, regardless of brand. These often target weak security configurations or vulnerabilities in the underlying operating system.
- Ransomware: Attackers may deploy ransomware to encrypt the data stored on the Zyxel NAS, demanding a ransom for its release. This type of attack causes significant data loss and operational disruption.
- Cryptojacking malware: This type of malware uses the NAS’s processing power to mine cryptocurrency without the owner’s knowledge or consent. While not directly damaging data, it consumes resources and can impact performance.
Maintaining Persistent Access
Once an attacker gains access, they often employ techniques to maintain persistent access, even after a system reboot or password change. This allows them to continue their malicious activities undetected for extended periods.
- Backdoors: Attackers might install backdoors—hidden access points—allowing them to regain access even if their initial entry point is compromised.
- Rootkit installation: Rootkits are designed to hide the attacker’s presence on the system, making detection difficult. They provide persistent access and can be used to cover tracks.
- Compromised accounts: Attackers might change the administrator password, granting themselves continued access even after the initial vulnerability is patched.
Typical Attack Stages
A successful attack on a Zyxel NAS device typically follows a series of stages, from initial reconnaissance to data exfiltration. Understanding these stages helps in developing effective security measures.
- Reconnaissance: Attackers identify vulnerable Zyxel NAS devices through network scanning or publicly available information.
- Initial compromise: Exploiting a vulnerability or using brute force to gain initial access.
- Privilege escalation: Gaining higher-level access to the system, often administrator privileges.
- Persistence: Establishing a backdoor or other method to maintain access over time.
- Data exfiltration: Stealing sensitive data from the compromised NAS device.
- Further compromise: Using the NAS as a launching point to attack other devices on the network.
Impact of Successful Attacks
Source: zyxel.eu
A successful attack on a Zyxel NAS device can have devastating consequences, ranging from minor inconveniences to complete business disruption. The impact extends beyond simple data loss; it encompasses financial repercussions, reputational damage, and legal liabilities. Understanding these potential outcomes is crucial for implementing robust security measures.
The severity of the impact depends on several factors, including the type of attack, the sensitivity of the data stored on the NAS, and the organization’s ability to recover from the incident. For example, a ransomware attack encrypting critical business files will have a far greater impact than a simple denial-of-service attack that temporarily disrupts access. The speed and effectiveness of the response also play a significant role in mitigating the damage.
Data Breaches and Data Misuse
A successful attack can lead to a significant data breach, exposing sensitive information such as customer data, financial records, intellectual property, and employee details. This stolen data can be misused in various ways. For instance, customer data could be sold on the dark web for identity theft, financial records could be used for fraudulent transactions, and intellectual property could be copied and used by competitors. The consequences can be severe, leading to financial losses, legal penalties, and damage to the company’s reputation. Consider a scenario where a small business’s customer database, containing names, addresses, credit card numbers, and purchase history, is compromised. The ensuing identity theft and financial fraud could cost the business significant sums in compensation and legal fees, while severely damaging its reputation and customer trust.
Financial and Reputational Damage
The financial implications of a successful attack can be substantial. Costs associated with data recovery, system restoration, legal fees, regulatory fines, and customer compensation can quickly add up. Furthermore, the loss of business due to downtime and reputational damage can lead to a significant decrease in revenue. The reputational damage resulting from a data breach can be long-lasting, impacting future business opportunities and investor confidence. A compromised company may struggle to attract new customers and retain existing ones, leading to a decline in market share and profitability.
Hypothetical Scenario: Small Business Attack
Imagine “Cozy Corner Cafe,” a small bakery with a Zyxel NAS device storing customer orders, financial records, and employee information. A ransomware attack encrypts all data on the NAS, demanding a ransom for decryption. The cafe is forced to shut down temporarily, losing revenue from sales and potentially facing legal action if customer data was compromised. The cost of data recovery, if possible, along with the loss of business during downtime, could cripple the small business, potentially leading to closure. The cafe’s reputation suffers, impacting future customer loyalty and potentially driving away investors. The long-term impact on the cafe’s viability would be severe, illustrating the devastating potential of a successful attack on even a small business.
Mitigation Strategies and Best Practices
Securing your Zyxel NAS device isn’t just about protecting your precious photos and videos; it’s about safeguarding your entire digital life. A compromised NAS can be a gateway to your entire network, exposing sensitive data and leaving you vulnerable to a range of cyber threats. Let’s explore practical steps to significantly bolster your NAS’s security.
Implementing robust security measures for your Zyxel NAS involves a multi-pronged approach focusing on hardware, software, and network configurations. Ignoring even one aspect can leave your system exposed. A layered security approach is key, building multiple barriers to deter and prevent attacks.
Strong Passwords and Account Management
Choosing a strong, unique password for your Zyxel NAS is paramount. Avoid easily guessable passwords like “password123” or your birthday. Instead, opt for a complex password combining uppercase and lowercase letters, numbers, and symbols. Password managers can help you generate and securely store these complex passwords. Additionally, enable two-factor authentication (2FA) if your Zyxel NAS supports it, adding an extra layer of protection. Regularly review and update user accounts, disabling or deleting accounts that are no longer needed.
Regular Firmware Updates
Keeping your Zyxel NAS firmware up-to-date is crucial. Firmware updates often include critical security patches that address known vulnerabilities. Check for updates regularly and install them promptly. Zyxel typically announces updates on their support website. Failing to update leaves your device susceptible to exploits that could have been patched.
Network Segmentation
Isolate your Zyxel NAS from the rest of your network whenever possible. This can be achieved through the use of a virtual LAN (VLAN) or by placing the NAS on a separate, less-accessible subnet. This limits the impact of a successful breach, preventing attackers from easily accessing other devices on your network. Consider placing your NAS behind a firewall for an additional layer of protection.
Security Tools and Techniques
Employing additional security tools can significantly enhance your NAS’s protection. A robust firewall, either integrated into your router or a standalone device, can block malicious traffic from reaching your NAS. Intrusion detection systems (IDS) can monitor network traffic for suspicious activity, alerting you to potential attacks. Regular security scans using vulnerability scanners can help identify and address weaknesses in your NAS’s configuration.
Comparison of Security Solutions
Various security solutions are available, each with its strengths and weaknesses. Some routers offer built-in NAS security features, while others require third-party solutions. Consider factors such as ease of use, cost, and the level of protection offered when choosing a security solution. A comprehensive approach, combining multiple layers of security, is often the most effective strategy. For example, a combination of a strong firewall, regular firmware updates, and a robust antivirus solution offers a higher level of protection than relying on a single security measure.
Implementing Robust Security Measures: A Step-by-Step Guide
- Change Default Credentials: Immediately change the default administrator password and username to a strong, unique combination upon initial setup.
- Enable Two-Factor Authentication (2FA): If available on your Zyxel NAS model, activate 2FA for an additional layer of security.
- Update Firmware Regularly: Check for and install firmware updates as soon as they are released by Zyxel.
- Configure Network Segmentation: Isolate your NAS on a separate VLAN or subnet to limit the impact of a potential breach.
- Implement a Firewall: Utilize a firewall, either integrated into your router or a standalone device, to control network traffic.
- Enable Regular Security Scans: Conduct periodic vulnerability scans to identify and address potential weaknesses.
- Monitor System Logs: Regularly review your NAS’s system logs for any suspicious activity.
- Use Strong Encryption: Enable encryption for all data stored on your NAS, protecting your data even if the device is compromised.
Case Studies of Zyxel NAS Attacks

Source: hackread.com
Real-world attacks against Zyxel NAS devices highlight the critical need for robust security practices. These incidents demonstrate how vulnerabilities, if left unpatched, can be exploited by malicious actors to gain unauthorized access and compromise sensitive data. Analyzing these cases reveals common attack vectors, the techniques used, and the consequences for affected users.
Zyxel NAS Device Compromise via Default Credentials
One common attack vector involves exploiting the use of default or easily guessable administrator credentials. Many users fail to change the default password upon initial setup, leaving their devices vulnerable. Attackers leverage readily available lists of common passwords or brute-force techniques to gain access. Once inside, they can install malware, steal data, or use the device as a stepping stone to attack other systems on the network. A reported incident involved a small business whose Zyxel NAS device was compromised using the default password “admin.” The attacker gained access to sensitive financial records and customer data. Remediation involved changing the password to a strong, unique one and implementing multi-factor authentication.
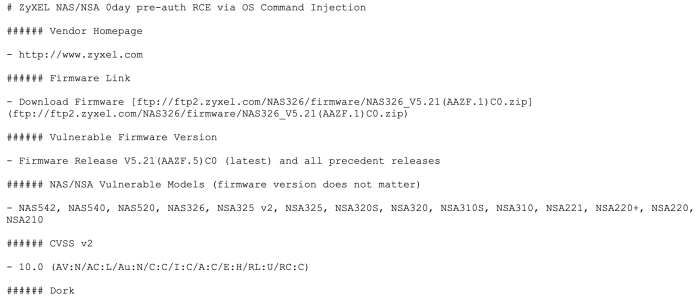
Exploitation of Known Vulnerabilities in Zyxel NAS Firmware
Several publicly disclosed vulnerabilities in Zyxel NAS firmware have been exploited in real-world attacks. These vulnerabilities, often related to insecure coding practices or insufficient input validation, allow attackers to remotely execute code on the device. This can lead to complete control of the NAS, enabling data theft, ransomware deployment, or the creation of a botnet node. One such case involved a researcher who discovered a remote code execution vulnerability in an older Zyxel NAS model. They responsibly disclosed the vulnerability to Zyxel, which subsequently released a security patch. However, many users failed to update their firmware, leaving their devices vulnerable to exploitation. The attacker used this vulnerability to install a cryptocurrency miner, consuming significant system resources and generating revenue for the attacker. Remediation required updating the NAS firmware to the latest version and implementing regular security updates.
Phishing Attacks Targeting Zyxel NAS Administrators
Social engineering attacks, particularly phishing, remain a significant threat. Attackers craft convincing emails or messages designed to trick users into revealing their NAS credentials. These emails often mimic legitimate communications from Zyxel or other trusted sources. Once the credentials are obtained, attackers can access the NAS and perform malicious actions. A case study reported by a cybersecurity firm involved a university whose Zyxel NAS device was compromised after an administrator clicked on a malicious link in a phishing email. The attacker gained access to sensitive research data and student records. Remediation involved implementing security awareness training for all users, focusing on identifying and avoiding phishing attempts, along with strengthening password policies.
“The attackers gained access to the NAS by exploiting a known vulnerability in the firmware and subsequently exfiltrated sensitive data.” – Excerpt from a cybersecurity incident report.
Visual Representation of Attack Surface
Source: krebsonsecurity.com
Understanding the attack surface of a Zyxel NAS device requires visualizing its interconnectedness and exposed points of vulnerability. This visual representation helps security professionals and users alike identify potential weaknesses and implement effective mitigation strategies. Think of it like a map highlighting all the possible entry points for a burglar targeting your home – the more doors and windows, the greater the risk.
A comprehensive visualization would depict the NAS device at the center, radiating outwards to show its various connections and exposed services. This model allows for a clear understanding of the potential attack vectors and their consequences.
Network Connections and Exposed Services
The visual representation should clearly illustrate the network connections of the Zyxel NAS. This includes its connection to the internet (often through a router), its connection to the local network (via Ethernet or Wi-Fi), and any connections to external services (like cloud storage or remote access). Each connection point represents a potential entry point for an attacker. Exposed services, such as FTP, SSH, SMB, and web interfaces (HTTP/HTTPS), should be clearly indicated with their respective port numbers (e.g., port 21 for FTP, port 22 for SSH, port 80/443 for HTTP/HTTPS). The visualization should also highlight whether these services are properly secured (e.g., using strong passwords, encryption, and firewalls).
Entry Points for Attackers
Attackers can exploit various entry points to compromise a Zyxel NAS. These entry points are often related to vulnerabilities in the exposed services mentioned above. For example, a weak password on the web interface (port 80/443) allows for unauthorized access, while unpatched vulnerabilities in the firmware itself can create backdoors for remote exploitation. Outdated or improperly configured services like FTP (port 21) without secure encryption (FTPS) can expose sensitive data to attackers. Similarly, vulnerabilities in the SMB service (port 445) can allow for ransomware attacks or data exfiltration. The visual representation should depict these entry points as clear pathways leading to the core of the NAS device.
Potential Consequences of Exploited Vulnerabilities, Zyxel nas devices under attack
The consequences of a successful attack vary depending on the exploited vulnerability and the attacker’s goals. However, common consequences include: data breaches, where sensitive personal or business information is stolen; ransomware attacks, where data is encrypted and a ransom is demanded for its release; denial-of-service (DoS) attacks, where the NAS becomes unavailable; and the use of the compromised device as a stepping stone to attack other devices on the network. The visual representation could use icons or color-coding to illustrate the severity of these consequences, with data breaches and ransomware attacks depicted with higher severity levels. For instance, a data breach might be represented by a symbol of a leaking data stream, while a ransomware attack could be shown with a padlock icon overlaid with a skull.
Structured Format for Visual Representation
A useful visual representation could take the form of a layered diagram. The central element is the Zyxel NAS device, represented by an icon. Radiating outwards are lines representing network connections, each labeled with the connection type (e.g., Internet, LAN) and any relevant information like IP address or subnet mask. Branching off these connections are smaller icons representing the exposed services (e.g., FTP, SSH, SMB, HTTP/HTTPS), each labeled with its port number and security status (e.g., secured, unsecured). Finally, arrows could illustrate potential attack vectors, leading from the exposed services to the central NAS icon, and additional icons could be used to visually represent the consequences of a successful attack (data breach, ransomware, etc.). The severity of the consequences could be indicated using different colors or sizes of the consequence icons. For example, a large, red icon would represent a critical consequence like a data breach, while a smaller, yellow icon might represent a less critical consequence. This structured visual representation would provide a clear and concise overview of the Zyxel NAS device’s attack surface.
Final Review
The threat to Zyxel NAS devices is real, and it’s evolving. While the potential consequences—from data breaches and ransomware to complete system compromise—are significant, proactive measures can dramatically reduce your risk. By understanding the vulnerabilities, implementing robust security practices, and staying informed about the latest threats, you can significantly bolster the security of your Zyxel NAS and protect your valuable data. Don’t wait until it’s too late—take control of your digital security today.



