Fickle stealer windows data theft – Fickle Stealer: Windows Data Theft Exposed. This sneaky malware is silently stealing sensitive information from unsuspecting Windows users, employing clever evasion tactics to stay hidden. We delve into the dark underbelly of this digital thief, exploring its methods, the vulnerabilities it exploits, and the devastating consequences it leaves in its wake. Prepare to uncover the secrets of this elusive threat and learn how to protect yourself.
From understanding the characteristics of Fickle Stealer malware to mastering detection and mitigation strategies, this deep dive explores the entire lifecycle of an attack. We’ll examine real-world examples, dissect data exfiltration techniques, and provide actionable steps to safeguard your valuable data. Get ready to arm yourself with the knowledge to combat this persistent threat.
Defining “Fickle Stealer”
Source: balbix.com
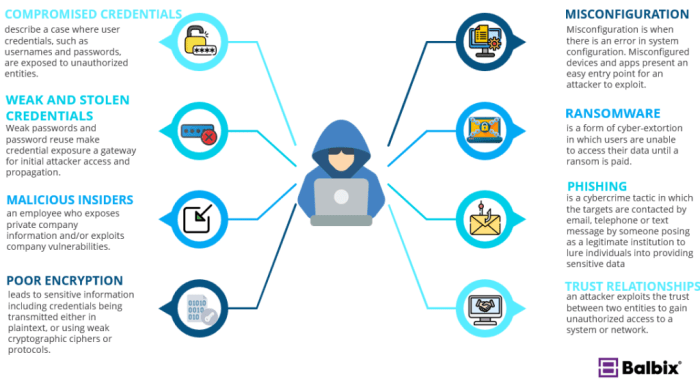
Fickle Stealer isn’t a single, well-defined piece of malware, but rather a category encompassing various sophisticated information-stealing Trojans. These malicious programs are characterized by their adaptability and evasiveness, constantly changing their behavior to avoid detection by antivirus software and security systems. Understanding their characteristics is crucial for effective defense.
Fickle stealers are designed to remain undetected for extended periods, silently exfiltrating sensitive data from compromised systems. Their primary goal is to steal valuable information, which they then sell on underground marketplaces or use for malicious purposes like identity theft or financial fraud. This makes them a significant threat to both individuals and organizations.
Methods of Evasion
Fickle stealers employ a range of techniques to avoid detection. These often include polymorphism, where the malware’s code is constantly modified to evade signature-based detection; obfuscation, making the code difficult to understand and analyze; and the use of advanced anti-analysis techniques, which hinder reverse engineering efforts by security researchers. They might also use rootkit capabilities to hide their presence within the operating system. Furthermore, they often communicate with command-and-control (C&C) servers using encrypted channels, making it difficult to intercept and analyze their communications.
Comparison with Other Malware
Compared to simpler keyloggers or ransomware, fickle stealers are significantly more advanced. Keyloggers only record keystrokes, while ransomware encrypts files and demands a ransom. Fickle stealers, on the other hand, are capable of stealing a far broader range of data, including credentials, financial information, and sensitive personal details. They also exhibit greater sophistication in their evasion techniques. Unlike simpler malware that might rely on easily detectable methods, fickle stealers utilize advanced techniques to blend into the system and remain undetected for prolonged periods. This makes them a more persistent and dangerous threat.
Targeted Data
Fickle stealers target a wide variety of sensitive data. The specific data stolen depends on the malware’s configuration and the targets it infects. However, some common targets include login credentials (usernames and passwords), credit card details, banking information, personal identification information (PII), and intellectual property.
| Malware Name | Target Data | Evasion Technique | Detection Difficulty |
|---|---|---|---|
| Example Stealer A | Login credentials, credit card details, PII | Polymorphism, process injection | High |
| Example Stealer B | Banking information, cryptocurrency wallets | Obfuscation, encrypted communication | Medium-High |
| Example Stealer C | System files, sensitive documents | Rootkit capabilities, anti-analysis techniques | High |
| Example Stealer D | Cookies, browser history, autofill data | Self-modification, stealthy network communication | Medium |
Windows Vulnerabilities Exploited: Fickle Stealer Windows Data Theft
Source: lifehacker.com
Fickle stealers, those sneaky digital bandits, don’t just waltz into your system; they exploit weaknesses. Understanding these vulnerabilities is key to bolstering your defenses and keeping your precious data safe. They’re like digital pickpockets, looking for the easiest targets – and Windows, despite its robust security features, has its share of vulnerabilities.
Windows vulnerabilities exploited by fickle stealers are often related to outdated software, misconfigured settings, or unpatched security flaws. These vulnerabilities act as entry points, allowing malicious code to sneak past the system’s defenses and gain unauthorized access. Once inside, the fickle stealer can freely roam, collecting sensitive data and exfiltrating it unnoticed. This process often involves a combination of technical exploits and social engineering tactics.
Exploited Vulnerabilities and Data Exfiltration
Common vulnerabilities include flaws in the Windows operating system itself, such as buffer overflows, privilege escalation bugs, or vulnerabilities in specific services or applications running on the system. For example, a buffer overflow vulnerability might allow an attacker to inject malicious code into the system’s memory, granting them control. Once access is granted, the fickle stealer uses various methods for data exfiltration. This could involve directly copying files, using compromised credentials to access cloud storage services, or even establishing a backdoor for persistent access and future data theft. Data exfiltration techniques often involve stealthy methods like using encrypted channels or leveraging existing network traffic to mask the stolen data. Think of it as a digital heist where the thief carefully hides their loot among legitimate traffic.
The Role of Social Engineering
Social engineering plays a crucial role in many successful fickle stealer attacks. Attackers often use phishing emails, malicious links, or other deceptive tactics to trick users into installing malware or revealing their credentials. Imagine a seemingly innocuous email claiming to be from your bank, urging you to update your account information by clicking a link. This link could download a fickle stealer, granting the attacker access to your system and its valuable data. This human element often makes the difference between a successful attack and a failed one, as technical vulnerabilities are useless without a way to initially compromise the target.
Hypothetical Scenario: Zero-Day Exploit
Let’s imagine a scenario involving a zero-day vulnerability in a Windows component responsible for handling image files. This hypothetical zero-day, unknown to Microsoft and thus unpatched, allows a specially crafted image file to execute arbitrary code when opened. A fickle stealer is packaged within this seemingly harmless image. A user, perhaps a graphic designer, receives this image via email – a cleverly disguised phishing attempt. Upon opening the image, the zero-day vulnerability is exploited, silently installing the fickle stealer. The stealer then proceeds to steal sensitive data, such as project files, client information, and potentially even financial details, before exfiltrating it through an encrypted connection to a remote server controlled by the attacker. The entire process happens without the user’s knowledge, highlighting the insidious nature of zero-day exploits and the importance of robust security practices.
Data Exfiltration Techniques
Fickle Stealer, like other malware, relies on sneaky data exfiltration methods to get your sensitive information out of your system and into the hands of malicious actors. These methods vary widely in sophistication and how easily they’re detected, making a comprehensive understanding crucial for effective cybersecurity. The goal is always the same: to steal your data without you noticing.
Data exfiltration techniques can be broadly categorized based on their complexity and how easily they can be detected by security software. Simpler methods are often easier to implement but also easier to detect, while more complex methods require more technical expertise but offer a higher chance of success without raising alarms.
Low-Complexity Exfiltration Methods, Fickle stealer windows data theft
These methods are relatively straightforward and often used by less sophisticated malware or as a first attempt. They’re easier to detect because they often involve predictable patterns or readily available tools.
Examples include using readily available file-sharing services like email, cloud storage, or even FTP. Imagine a Fickle Stealer uploading stolen files to a free email account. While seemingly simple, the sheer volume of data being transferred or the unusual timing of these transfers might trigger security alerts. Another example is using publicly available web servers as drop points. The malware simply uploads the data to a compromised or publicly accessible server, controlled by the attackers.
Medium-Complexity Exfiltration Methods
These methods are more sophisticated and attempt to evade detection by using more covert channels or techniques. They require a bit more technical knowledge to implement but offer increased chances of success.
One common tactic involves using legitimate software features in unexpected ways. For instance, Fickle Stealer might exploit a company’s internal file sharing system to upload stolen data, blending in with legitimate activity. Another example is using HTTP POST requests to send data in small chunks to a command-and-control server. These small packets can easily be disguised as normal web traffic, making them difficult to identify as malicious.
High-Complexity Exfiltration Methods
These are the most advanced techniques, often involving custom-built tools and intricate methods designed to bypass security measures. Detection is significantly harder due to their stealthy nature.
One example is using Domain Generation Algorithms (DGAs) to dynamically generate a constantly changing list of domains used for communication. This makes it very difficult for security systems to track and block the communication channels. Another technique involves using steganography, hiding stolen data within seemingly innocuous files like images or audio files. This requires specialized tools and a deep understanding of data encoding to successfully extract the hidden information. Finally, using compromised legitimate services (like cloud storage accounts) is a powerful method, blending malicious activity within a trusted environment.
A Typical Data Exfiltration Process: The Case of Email Exfiltration
Let’s illustrate a typical exfiltration process using a simple, yet effective, example: email.
1. Data Acquisition: Fickle Stealer first infiltrates the target system, gaining access to sensitive data like credentials, documents, or images.
2. Data Encoding/Compression: The stolen data is then compressed or encoded to reduce its size and potentially make it harder to analyze.
3. Data Staging: The compressed data might be temporarily stored in a hidden location on the infected machine.
4. Exfiltration Initiation: The malware then uses the system’s email client to send the compressed data to a pre-determined email address controlled by the attackers. This could involve crafting an email with the attachment, using SMTP commands directly, or exploiting vulnerabilities in the email client itself.
5. Data Receipt and Analysis: The attackers receive the email and extract the data, analyzing its contents for valuable information.
Impact and Consequences
A successful Fickle Stealer attack can have devastating consequences for both individuals and organizations, ranging from financial losses and reputational damage to legal repercussions and operational disruptions. The severity of the impact depends on the type and sensitivity of the stolen data, the attacker’s motives, and the victim’s response capabilities. Understanding these potential impacts is crucial for effective prevention and mitigation.
The consequences of a Fickle Stealer attack extend far beyond the initial data breach. The stolen information can be used for various malicious purposes, including identity theft, financial fraud, blackmail, corporate espionage, and even sabotage. The long-term effects can be significant, leading to lost productivity, eroded customer trust, and hefty legal fees. The ripple effect can be felt across multiple aspects of an organization’s operations, damaging its overall stability and future prospects.
Real-World Incidents and Their Consequences
Several real-world incidents highlight the severe consequences of data theft facilitated by malware like Fickle Stealer. For instance, the NotPetya ransomware attack in 2017, while not directly a Fickle Stealer incident, demonstrates the cascading effect of a widespread cyberattack. Initially targeting Ukrainian companies, it quickly spread globally, causing billions of dollars in damage across various industries. The disruption to supply chains and the cost of recovery highlighted the significant financial impact of such events. Similarly, the SolarWinds supply chain attack showcased the vulnerability of large organizations to compromised software, resulting in the theft of sensitive government and corporate data. While not using a tool explicitly named “Fickle Stealer,” the attack demonstrates the potential for far-reaching consequences from a seemingly minor breach. These examples underscore the importance of robust security measures and incident response plans.
Financial and Reputational Damage
The financial repercussions of a Fickle Stealer attack can be substantial. Direct costs include the expenses associated with incident response, data recovery, legal fees, regulatory fines, and potential compensation to affected individuals or organizations. Indirect costs encompass lost productivity, damage to reputation, and the loss of future business opportunities. The reputational damage can be particularly severe, leading to a decline in customer trust, investor confidence, and overall brand value. This damage can be difficult and costly to repair, even after the immediate crisis has subsided. For example, a company experiencing a data breach that exposes customer financial information might face lawsuits, regulatory penalties, and a significant loss of market share.
Preventative Measures
It is imperative to proactively implement preventative measures to mitigate the risk of Fickle Stealer attacks. A layered security approach is essential, combining multiple strategies to create a robust defense.
- Regular Software Updates: Keeping operating systems, applications, and antivirus software up-to-date patches vulnerabilities that attackers could exploit.
- Strong Passwords and Multi-Factor Authentication (MFA): Employing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Employee Security Awareness Training: Educating employees about phishing scams, malware, and other social engineering tactics can significantly reduce the risk of human error, a major factor in many successful attacks.
- Network Security: Implementing firewalls, intrusion detection/prevention systems, and robust network segmentation helps to contain the spread of malware and limit the impact of a successful attack.
- Data Backup and Recovery: Regularly backing up critical data to an offline location ensures business continuity in the event of a data breach or ransomware attack.
- Security Audits and Penetration Testing: Regular security assessments help identify vulnerabilities in systems and processes, allowing for proactive mitigation before attackers can exploit them.
Detection and Mitigation Strategies
So, your system’s been hit by Fickle Stealer. Now what? Detecting this sneaky malware requires a multi-pronged approach, combining proactive security measures with reactive incident response. Think of it like a detective’s toolkit – you need the right tools and the right know-how to catch the culprit.
Detecting Fickle Stealer activity isn’t always straightforward. It often hides its tracks, making identification a challenge. However, by combining vigilant monitoring with a solid understanding of its behavior, you significantly increase your chances of catching it in the act. This involves a blend of technical analysis and security awareness.
Indicators of Compromise (IOCs)
Identifying the telltale signs of a Fickle Stealer infection is crucial for a swift response. These indicators, or IOCs, can range from unusual system behavior to suspicious network activity. Recognizing these patterns is the first step towards neutralizing the threat. Common IOCs include unusual process activity, such as unexpected connections to external servers, especially those known for hosting malicious software. Anomalous file creation or modification in system directories, particularly those associated with sensitive data, is another key indicator. Furthermore, unexplained spikes in network traffic, especially outgoing traffic to unknown destinations, should raise immediate suspicion. Lastly, changes to system configurations, particularly those related to security settings, might indicate malicious activity. For example, the disabling of antivirus software or firewall rules would be a clear red flag.
Methods for Detecting Fickle Stealer Activity
Several methods can be employed to detect Fickle Stealer’s malicious activities. Regular system scans using updated antivirus software are paramount. These scans can detect known malware signatures and potentially remove the threat. Furthermore, employing intrusion detection and prevention systems (IDPS) can monitor network traffic for suspicious patterns, providing an early warning system for potential attacks. Regular security audits are also vital. These audits analyze system logs and configurations for anomalies, revealing potential compromises. Finally, employing endpoint detection and response (EDR) solutions offers real-time monitoring of system activity, providing detailed insights into processes, files, and network connections. This allows for immediate detection and response to malicious activity. For instance, an EDR solution might flag unusual access to sensitive files or communication with known malicious IP addresses.
Mitigation Strategies
Preventing Fickle Stealer infections requires a layered security approach. Regular software updates are crucial, patching known vulnerabilities that the malware might exploit. Strong password policies and multi-factor authentication (MFA) significantly reduce the risk of unauthorized access. Restricting administrative privileges to only necessary users limits the impact of potential compromises. Regular backups of critical data ensure business continuity in case of an attack. Finally, implementing robust network security measures, including firewalls and intrusion prevention systems, can prevent malicious traffic from reaching your systems. A strong firewall, for instance, can block connections to known malicious IP addresses, preventing Fickle Stealer from communicating with its command-and-control server.
Security Awareness Training Program
A comprehensive security awareness training program is essential in mitigating the risk of Fickle Stealer attacks. This program should educate users about phishing scams, social engineering tactics, and the importance of safe browsing habits. Training should include practical examples of phishing emails and websites, teaching users how to identify and report suspicious activity. Regular simulations and quizzes can reinforce learning and ensure users retain the knowledge. Furthermore, clear guidelines on password management, data security, and acceptable use of company resources should be provided. The program should also explain the consequences of falling victim to such attacks, both for the individual and the organization. For example, a role-playing exercise simulating a phishing attack could be incredibly effective in demonstrating the real-world consequences of clicking a malicious link.
Forensic Analysis of Fickle Stealer Attacks

Source: vecteezy.com
Uncovering the digital fingerprints left behind by Fickle Stealer requires a meticulous forensic investigation. This process involves a systematic approach to identify the attack vector, the extent of data compromise, and the recovery of stolen information. The success of the investigation hinges on the speed and thoroughness of the response, minimizing further damage and maximizing the chances of recovering valuable data.
Steps Involved in a Forensic Investigation
A forensic investigation of a Fickle Stealer incident typically follows a structured methodology. This involves securing the compromised system, preserving evidence, and conducting a detailed analysis of system logs, registry entries, and network traffic. The goal is to reconstruct the timeline of the attack, identify the attacker’s methods, and recover any stolen data. This process often requires specialized tools and expertise in digital forensics.
Evidence Collection and Analysis
Investigators should prioritize the collection of various types of evidence to build a comprehensive picture of the attack. This includes examining system logs for suspicious activity, such as unusual network connections or file access attempts. Registry keys associated with the malware should be scrutinized for clues about its installation and execution. Memory dumps can reveal running processes and potentially uncover the malware’s presence even if it’s already been deleted. Analysis of network traffic logs can identify data exfiltration attempts and pinpoint the attacker’s command-and-control servers. Finally, examining the file system for remnants of the malware, including configuration files and stolen data, is crucial. The presence of unusual or newly created files, especially those hidden or disguised, warrants close inspection.
Data Recovery Techniques
Recovering stolen data depends heavily on the attacker’s methods and the persistence of the malware. If the data was exfiltrated to a remote server, collaboration with law enforcement and digital forensic specialists may be necessary to seize the server and retrieve the data. If the data remains on the compromised system, specialized data recovery tools can be employed to recover deleted or overwritten files. Careful analysis of file system metadata can also provide clues about the location and content of stolen data. However, the success of data recovery is not guaranteed, especially if the attacker used strong encryption or data destruction techniques. For example, if the attacker used a technique like wiping the hard drive securely, recovery may be impossible.
Flowchart of Analyzing a Compromised System
The following flowchart illustrates a simplified process:
[Imagine a flowchart here. The flowchart would start with “Incident Detection,” branching to “System Isolation and Preservation.” This would then branch to “Evidence Collection (Logs, Registry, Memory, Network Traffic, File System),” which feeds into “Malware Analysis (Identification, Behavior, Persistence).” This analysis would inform “Data Recovery Attempts,” which in turn leads to “Report Generation and Remediation.” Finally, there would be a feedback loop from “Report Generation and Remediation” back to “Incident Detection,” signifying the ongoing nature of cybersecurity and the need for continuous monitoring.]
The flowchart depicts the iterative nature of forensic analysis. The findings from one stage often inform the subsequent steps, leading to a more comprehensive understanding of the attack. It highlights the importance of a structured approach to ensure no critical steps are missed.
Illustrative Example: A Fictional Fickle Stealer
Let’s delve into the specifics of a hypothetical Windows data thief, christened “Fickle Stealer,” to illustrate the concepts discussed previously. This fictional malware showcases advanced evasion techniques and a modular architecture, making it a formidable threat. It’s designed to target high-value financial and personal data from unsuspecting users.
Fickle Stealer Capabilities and Targets
Fickle Stealer is designed to be highly versatile. Its primary targets include banking credentials, cryptocurrency wallets, email accounts, and personal identifying information (PII). It achieves this by employing a multi-pronged approach, utilizing keylogging, process injection, and screen scraping techniques. It’s also capable of lateral movement within a network if it gains initial access through a compromised machine. Its modular design allows for easy expansion of its capabilities; new modules can be added remotely to incorporate new data theft methods or evasion strategies. The malware is particularly adept at targeting users of popular financial applications and online banking platforms. This focus reflects the high value of the data obtained and the potential for significant financial gain for its creators.
Fickle Stealer Evasion Techniques
To avoid detection, Fickle Stealer employs several advanced evasion techniques. These include process hollowing, where it injects its malicious code into a legitimate process to mask its activity; rootkit functionality to hide its presence from system tools and security software; and polymorphic code generation to constantly change its signature, making it difficult for antivirus software to identify and remove it. Furthermore, it utilizes anti-analysis techniques to hinder reverse engineering efforts by security researchers. It checks for the presence of debuggers and virtual machines, altering its behavior or terminating itself if detected. The malware also communicates with its command-and-control (C2) server using encrypted channels and employs techniques like domain generation algorithms (DGAs) to dynamically generate new domains, making it harder to track and block its communication.
Fickle Stealer Attack Lifecycle
The Fickle Stealer’s attack lifecycle unfolds in several distinct stages:
1. Initial Infection: The malware is typically delivered through phishing emails containing malicious attachments or links to compromised websites. Once executed, it establishes persistence by adding itself to the system’s startup registry.
2. Data Collection: After gaining a foothold, Fickle Stealer begins its data collection phase. It utilizes a combination of keylogging, screen scraping, and process injection to steal sensitive information. Keylogging passively records keystrokes, while screen scraping captures data displayed on the user’s screen. Process injection allows it to inject its code into running processes, providing it with elevated privileges and potentially bypassing security measures.
3. Data Exfiltration: The stolen data is encrypted and exfiltrated to the C2 server using various techniques, including HTTP POST requests disguised as legitimate web traffic, and covert channels within seemingly innocuous applications.
4. Persistence and Evasion: The malware actively works to maintain persistence on the infected system and evade detection. This involves regularly updating its code to avoid detection by antivirus software and employing techniques to hide its presence from system monitoring tools.
5. Command and Control Communication: The malware maintains regular communication with its C2 server to receive commands, upload stolen data, and download updates. This communication is encrypted to prevent detection.
Fickle Stealer Architecture
Fickle Stealer adopts a modular architecture, comprising several key components:
* Core Module: This is the main component responsible for managing other modules, maintaining persistence, and communicating with the C2 server.
* Data Acquisition Module: This module handles the collection of data using keylogging, screen scraping, and process injection techniques.
* Exfiltration Module: This module is responsible for encrypting and transmitting the stolen data to the C2 server.
* Evasion Module: This module implements the various evasion techniques employed by the malware to avoid detection.
Hypothetical Code Snippet (Pseudocode)
The following pseudocode illustrates a key function of the Fickle Stealer’s data exfiltration module:
“`
function exfiltrateData(data, C2ServerAddress)
encryptedData = encryptData(data, encryptionKey);
httpPostRequest(C2ServerAddress, encryptedData);
if (httpRequestSuccessful)
log(“Data successfully exfiltrated.”);
else
log(“Data exfiltration failed. Retrying…”);
// Implement retry mechanism with exponential backoff
“`
This function demonstrates the basic process of encrypting the stolen data and sending it to the C2 server using an HTTP POST request. Error handling and retry mechanisms are also included to ensure reliable data exfiltration.
Epilogue
The threat of Fickle Stealer and similar malware highlights the ever-evolving landscape of cybercrime. While the methods employed may be sophisticated, proactive measures and a strong security posture remain our best defense. By understanding the tactics used by these digital thieves, individuals and organizations can significantly reduce their vulnerability and protect themselves from the devastating consequences of data breaches. Staying informed and vigilant is key in this ongoing battle for digital security.



