Smokeloader modular malware capabilities represent a significant threat in the cybersecurity landscape. This sophisticated malware leverages a modular architecture, allowing for adaptability and evasion of detection. Its ability to infect systems, propagate across networks, and deliver diverse payloads makes it a particularly dangerous threat. Understanding its intricate mechanisms is crucial for effective mitigation and defense.
The modular design of Smokeloader allows for easy updates and expansion of its functionality. New modules can be added or existing ones modified without affecting the core structure, making it difficult to track and neutralize. This, coupled with advanced evasion techniques, makes Smokeloader a persistent and challenging adversary for security professionals.
Smokeloader Architecture

Source: lumu.io
Smokeloader’s modular design is a key factor in its effectiveness and adaptability. Unlike monolithic malware, which is a single, large executable file, Smokeloader operates as a collection of independent modules, each with a specific function. This allows for greater flexibility, easier updates, and more evasive techniques. Understanding its architecture is crucial to comprehending its capabilities and potential threats.
Smokeloader’s modularity allows for a highly adaptable and evasive malware campaign. The core functionality is divided into discrete modules, enabling attackers to easily modify or update specific components without recompiling the entire program. This modular approach also allows for the creation of custom payloads, tailored to specific targets or objectives.
Smokeloader Component Breakdown
The following table details the key components of Smokeloader’s architecture, their functions, interactions, and potential vulnerabilities. The modular nature introduces both advantages and disadvantages, which are explored later.
| Component Name | Function | Interaction with other components | Potential Vulnerabilities |
|---|---|---|---|
| Loader | Initializes the malware, loads other modules, and establishes persistence. | Interacts with all other modules; responsible for their execution and communication. | Vulnerable to anti-malware detection at the initial infection stage; failure to load other modules could cripple the entire operation. |
| Downloader | Downloads additional modules or payloads from a Command and Control (C2) server. | Interacts with the Loader and the C2 server; dependent on network connectivity. | Vulnerable to network monitoring and intrusion detection systems; susceptible to blocking by firewalls. |
| Payload Manager | Manages the execution of different payloads, based on instructions from the C2 server. | Interacts with the Downloader and various payloads; determines which malicious actions to perform. | A compromise in this module could prevent the execution of critical payloads; a failure point for the overall attack. |
| Communication Module | Facilitates communication between Smokeloader and the C2 server, enabling updates and command execution. | Interacts with the Loader, Downloader, and Payload Manager; crucial for maintaining persistence and receiving instructions. | Vulnerable to network analysis and traffic filtering; detection of communication patterns can lead to malware identification. |
| Payload Modules (e.g., Keylogger, Data Exfiltration, Ransomware) | Perform the actual malicious actions. These are highly variable and can be swapped out easily. | Interact with the Payload Manager; dependent on the instructions received from the C2 server. | Specific vulnerabilities depend on the individual payload; anti-malware solutions may detect specific payload functionalities. |
Advantages and Disadvantages of Modular Design
The modular architecture of Smokeloader offers significant advantages to the attacker. The ability to easily update individual components allows for rapid adaptation to new security measures and the deployment of varied payloads for different targets. However, this same modularity introduces vulnerabilities. A failure in one module can disrupt the entire operation, and the increased complexity makes reverse engineering and analysis more challenging but not impossible. For example, a compromised communication module could severely limit the malware’s capabilities. Furthermore, the numerous components increase the surface area for detection by anti-malware software. A successful attack on one module could reveal the existence of others.
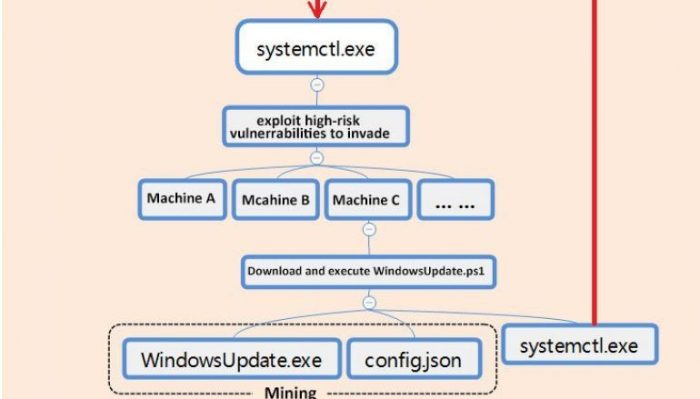
Infection and Propagation Mechanisms
Smokeloader, a modular malware family, utilizes a sophisticated arsenal of techniques to infiltrate systems and spread across networks. Understanding these mechanisms is crucial for effective defense against this persistent threat. Its infection vectors are diverse, reflecting a design aimed at maximizing its reach and impact. Propagation, meanwhile, leverages established lateral movement strategies to compromise additional targets within the infected network.
Smokeloader’s Infection Vectors and Lateral Movement Strategies
Infection Vectors
Smokeloader employs a variety of infection vectors to gain initial access to target systems. These vectors are carefully chosen to exploit vulnerabilities and bypass security measures. Successful infection often relies on the element of surprise and exploiting human error.
Examples include spear-phishing emails containing malicious attachments or links leading to drive-by downloads. Compromised websites may also serve as vectors, silently injecting malware onto visiting machines. Exploiting known vulnerabilities in software applications is another common tactic. In some cases, Smokeloader may even leverage physical access to infected systems, installing itself directly onto the machine. The diversity of its infection vectors makes it a particularly challenging threat to defend against.
Lateral Movement Techniques
Once a system is compromised, Smokeloader uses several techniques to propagate within a network. These techniques aim to maintain persistence and expand the malware’s reach.
Common strategies include using stolen credentials to access other systems, exploiting vulnerabilities in network services like RDP (Remote Desktop Protocol), and leveraging shared network resources. It may also employ techniques like pass-the-hash or pass-the-ticket to move laterally without needing to obtain clear-text passwords. The use of legitimate tools and protocols, abused for malicious purposes, is also a common tactic, making detection more difficult.
Typical Smokeloader Infection Cycle
The steps involved in a typical Smokeloader infection cycle illustrate its cunning and multifaceted approach. Understanding these steps helps in building effective preventative measures.
- Initial Compromise: The infection begins with a successful exploit of a vulnerability, typically through a phishing email, malicious website, or software flaw. This delivers the initial malware payload.
- Establishment of Persistence: Smokeloader ensures its continued presence by installing itself as a service or modifying system startup processes. This allows it to survive reboots.
- Data Exfiltration: Stolen credentials and sensitive data are often exfiltrated from the compromised system, providing further access and intelligence for future attacks.
- Lateral Movement: Using stolen credentials or exploiting vulnerabilities, the malware spreads to other systems within the network, expanding its control.
- Command and Control (C2) Communication: The malware communicates with a remote command and control server to receive instructions and report back on its activities. This enables attackers to maintain control and direct further actions.
- Payload Delivery: Depending on the attacker’s goals, additional malicious payloads may be downloaded and executed, leading to further compromise and data theft.
Payload Delivery and Execution
Smokeloader, a modular malware family, employs a sophisticated approach to deliver and execute its malicious payloads. Understanding this process is crucial to comprehending its overall impact and the threat it poses. The delivery mechanism is intricately linked to the payload type, creating a dynamic and adaptable infection strategy.
Smokeloader delivers its payloads through various methods, often leveraging already established infection vectors. Once inside a system, it uses a combination of techniques to ensure successful execution, often relying on legitimate system processes or services to mask its activities. The payloads themselves are diverse, ranging from simple information stealers to complex backdoors capable of extensive system control. This adaptability makes Smokeloader a particularly resilient and difficult threat to neutralize.
Payload Delivery Mechanisms
Smokeloader’s payload delivery isn’t a one-size-fits-all approach. It adapts its techniques based on the target system and the specific payload being deployed. For instance, a payload might be injected directly into a running process, leveraging the process’s privileges to execute without raising suspicion. Alternatively, it could use the creation of a new process to load and run the malicious code. This contrasts with some simpler malware families that rely heavily on a single, easily detectable delivery method. More advanced families, like some sophisticated APT groups, may use similar multi-stage techniques, but often with a focus on evasion that differs significantly in terms of the specific tools and tactics employed. Smokeloader’s approach demonstrates a blend of established techniques adapted to its specific needs.
Payload Types and Their Impact
The table below categorizes the different payload types observed in Smokeloader infections, outlining their functions, delivery methods, and the resulting impact on compromised systems.
| Payload Type | Function | Delivery Method | Impact |
|---|---|---|---|
| Information Stealer | Collects sensitive data (credentials, files, etc.) | Process injection, file execution | Data breach, identity theft, financial loss |
| Remote Access Trojan (RAT) | Provides remote control over the infected system | DLL side-loading, service installation | System compromise, data exfiltration, persistent threat |
| Keylogger | Records keystrokes entered by the user | Kernel-level driver installation, user-mode hook | Password theft, sensitive data exposure |
| Downloader | Downloads and executes additional malware | HTTP requests, file system manipulation | Escalation of privilege, increased system compromise |
| Persistence Mechanism | Ensures the malware remains active even after reboot | Registry key modification, scheduled tasks | Difficult removal, long-term system compromise |
Command and Control (C2) Communication
Source: cybercureme.com
Smokeloader’s ability to maintain persistent communication with its command-and-control (C2) server is crucial for its operation. This communication allows the malware to receive instructions, upload stolen data, and receive updates, ensuring its longevity and effectiveness. The methods employed by Smokeloader to achieve this are complex and designed to evade detection.
Smokeloader utilizes a variety of communication channels and techniques to interact with its C2 server, prioritizing stealth and resilience. These channels often leverage established protocols to blend in with legitimate network traffic, making detection challenging. The malware employs sophisticated obfuscation and encryption methods to further hinder analysis and reverse engineering efforts. This makes understanding the communication flow a critical aspect of effectively combating this threat.
Communication Channels and Obfuscation Techniques
Smokeloader’s communication with its C2 server isn’t limited to a single method. Instead, it exhibits flexibility, employing various techniques to enhance its survivability. These can include using HTTP or HTTPS requests to seemingly benign websites, DNS tunneling to leverage DNS queries for covert communication, or even utilizing more obscure protocols to evade detection. The actual C2 server’s address is frequently dynamically generated or obfuscated within the malware’s code, making static analysis difficult. Encryption, often using strong ciphers, further protects the communication content from prying eyes. Furthermore, the malware may use techniques like data encoding and steganography to hide its communications within seemingly innocuous data streams.
Indicators of Compromise (IOCs)
Identifying Smokeloader’s C2 communication requires a multi-faceted approach. Key IOCs include suspicious domain names and IP addresses, unusual network traffic patterns (e.g., high volume of short-lived connections to uncommon ports), and the presence of encoded or encrypted communication within network packets. Analysis of network logs and system events for unusual activity, especially related to known Smokeloader infrastructure, is crucial. Observing consistent communication with specific domains or IP addresses, particularly those exhibiting unusual characteristics, can be a strong indicator of Smokeloader infection. Furthermore, the detection of specific strings or patterns within the malware’s code that relate to C2 communication protocols can help pinpoint infected systems.
C2 Communication Flowchart
The following describes a typical Smokeloader C2 communication process. Imagine a flowchart where:
1. Infection: The malware initially infects a system, perhaps via a phishing email or malicious website.
2. Initial Contact: The malware establishes contact with a C2 server, potentially using a hardcoded address initially or through a more complex lookup mechanism. This communication may be encrypted and obfuscated.
3. Command Reception: The C2 server sends commands to the infected system, these commands could be anything from data exfiltration instructions to updates to the malware itself. The commands are typically encrypted and obfuscated to evade detection.
4. Data Exfiltration: The infected system sends stolen data back to the C2 server. This data is often encrypted and segmented to avoid detection and suspicion.
5. Command Execution: The malware executes the commands received from the C2 server, carrying out actions such as data theft, system reconnaissance, or further propagation.
6. Feedback and Control: The C2 server monitors the infected system’s activity and sends further instructions based on its needs and the overall campaign objectives. This creates a continuous feedback loop, allowing for dynamic control and adaptation.
7. Persistence: The malware establishes persistence on the infected system to ensure continuous communication and control.
Evasion Techniques and Anti-Analysis Measures

Source: socprime.com
Smokeloader, like a seasoned ninja, employs a range of cunning techniques to evade detection and analysis. These methods blur its tracks, making it incredibly difficult for security researchers and analysts to understand its inner workings and ultimately neutralize its threat. The malware’s resilience is a testament to the sophistication of its creators, highlighting the ongoing arms race between malware developers and security professionals.
Smokeloader’s evasion strategy is multi-layered, combining various techniques to create a robust defense against detection. This layered approach makes it significantly harder to unravel its malicious activities. Understanding these techniques is crucial for developing effective countermeasures.
Code Obfuscation and Packing
Smokeloader uses several techniques to obfuscate its code, making reverse engineering a challenging endeavor. These techniques make the code significantly harder to understand and analyze. One common method is string encryption, where strings used in the malware are encrypted and decrypted only when needed. This prevents static analysis tools from easily identifying malicious strings or commands. Another technique is control flow obfuscation, which makes the code’s execution path difficult to follow by inserting irrelevant or confusing jumps and loops. This obscures the malware’s logic and makes it harder to determine its functionality. Packing techniques compress the malware’s code, making it smaller and harder to analyze. This can also hinder dynamic analysis by making it more difficult to set breakpoints or single-step through the code. For instance, the malware might employ packers like UPX or Themida, adding another layer of protection. The effectiveness of these techniques lies in their ability to significantly increase the time and effort required to understand the malware’s behavior. Imagine trying to assemble a jigsaw puzzle with many pieces that look almost identical—that’s the challenge presented by code obfuscation.
Process Injection and Hiding Techniques
To further evade detection, Smokeloader frequently employs process injection. This technique involves injecting its malicious code into a legitimate running process. This allows the malware to operate within the context of a trusted process, thereby masking its malicious activity and making it appear less suspicious to security tools. One common method is using techniques like CreateRemoteThread to inject code into another process’s address space.
Example (pseudocode):
OpenProcess(PROCESS_ALL_ACCESS, FALSE, TargetProcessID);
AllocateMemory(TargetProcess, CodeSize);
WriteProcessMemory(TargetProcess, AllocatedMemory, MaliciousCode, CodeSize);
CreateRemoteThread(TargetProcess, NULL, 0, (LPTHREAD_START_ROUTINE)AllocatedMemory, NULL, 0, NULL);
CloseHandle(TargetProcess);
This pseudocode illustrates how Smokeloader might inject its malicious code. By executing within a legitimate process, the malware’s activity is harder to distinguish from the normal behavior of that process, making it difficult for security solutions to identify it as malicious. Furthermore, Smokeloader might employ rootkit techniques to hide its files, registry keys, and network connections, making it even harder to detect its presence on an infected system. These techniques further enhance the malware’s ability to remain undetected, highlighting the sophistication of its design. The use of process hollowing, where a legitimate process is replaced with the malware, is another powerful method used to conceal its activity.
Capabilities and Functionality
Smokeloader, a modular malware family, boasts a diverse range of capabilities designed to achieve maximum impact and persistence on compromised systems. Its functionality extends beyond simple data theft, encompassing sophisticated techniques for system compromise and establishing a persistent presence, making eradication challenging. Understanding these capabilities is crucial for effective defense against this threat.
Smokeloader’s functionality revolves around three key pillars: data exfiltration, system compromise, and persistence. The modular nature of the malware allows attackers to tailor its capabilities to specific targets and objectives, making it a highly adaptable and dangerous threat. This adaptability makes predicting its exact behavior difficult, necessitating a robust security posture.
Data Exfiltration Capabilities
Smokeloader’s data exfiltration capabilities are extensive. It can steal a wide range of sensitive information, including credentials, financial data, intellectual property, and confidential communications. The exfiltrated data is often transmitted to a Command and Control (C2) server using various techniques to evade detection. For example, it might use encrypted channels, segmented data transfers, or leverage legitimate services to mask its malicious activity. The scale of data theft depends on the specific modules deployed and the attacker’s objectives. A large corporation might experience the loss of gigabytes of sensitive data, while a smaller business could see the theft of crucial customer records.
System Compromise Techniques
Beyond data theft, Smokeloader can severely compromise a system’s integrity and functionality. It achieves this through various methods, including privilege escalation, disabling security software, and installing additional malicious payloads. These payloads can range from keyloggers and remote access trojans (RATs) to ransomware and destructive malware. The level of system compromise can vary widely depending on the attacker’s goals and the specific modules utilized. A successful attack might lead to complete system shutdown, rendering it unusable, or result in subtle, persistent backdoors that allow for long-term access and control.
Persistence Mechanisms
Smokeloader employs sophisticated persistence mechanisms to ensure its continued presence on the compromised system. This could involve modifying system startup processes, creating registry entries, or injecting its code into legitimate processes. These techniques make it difficult to remove the malware, even after a seemingly successful cleanup. The malware might re-establish itself after a system reboot or after security software attempts to remove it. This persistent nature increases the risk of long-term damage and data breaches, potentially allowing attackers to maintain access to sensitive information indefinitely.
Potential Impact of a Successful Smokeloader Infection
A successful Smokeloader infection can have devastating consequences, ranging from minor disruptions to catastrophic damage depending on the target and the attacker’s objectives. Potential damage scenarios include significant financial losses due to data theft or ransomware attacks, reputational damage from data breaches, operational disruptions due to system compromise, and legal repercussions from regulatory non-compliance.
Hypothetical Smokeloader Attack Scenario, Smokeloader modular malware capabilities
Imagine a scenario where a company’s employee opens a seemingly innocuous email attachment. This attachment contains the Smokeloader malware, which immediately begins its infection process. The malware silently installs itself, establishes persistence, and begins exfiltrating sensitive data, including customer records and financial information. Simultaneously, it installs a RAT, giving attackers remote access to the company’s network. Over several weeks, the attackers systematically steal data and gradually escalate their privileges, potentially gaining access to even more sensitive systems. Eventually, the attackers deploy ransomware, encrypting critical data and demanding a ransom for its release. The result: significant financial losses, reputational damage, and a prolonged period of recovery. The company faces legal repercussions, potential lawsuits, and loss of customer trust.
Mitigation and Detection Strategies: Smokeloader Modular Malware Capabilities
Smokeloader, with its modular design and sophisticated evasion techniques, presents a significant challenge to cybersecurity professionals. Effective mitigation requires a multi-layered approach combining preventative measures, proactive monitoring, and rapid response capabilities. Understanding the malware’s attack vectors and identifying key indicators of compromise are crucial for successful defense.
Effective mitigation strategies against Smokeloader hinge on a robust security posture and proactive threat hunting. This involves strengthening defenses at multiple points in the kill chain, from preventing initial infection to containing and eradicating the malware once it’s established itself. Early detection is paramount, allowing for swift remediation and minimizing potential damage.
Effective Mitigation Strategies
Preventing Smokeloader infections requires a proactive approach focusing on several key areas. A layered security strategy is essential, combining various techniques to create a robust defense against this advanced threat. This includes strong network security, endpoint protection, and user education.
- Regular Software Updates: Patching vulnerabilities promptly is crucial. Smokeloader often exploits known vulnerabilities in software applications and operating systems. Keeping all software updated to the latest versions significantly reduces the attack surface.
- Robust Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection capabilities, monitoring system activity for malicious behavior indicative of Smokeloader’s actions. Real-time alerts and automated responses can contain infections before significant damage occurs. Features such as behavioral analysis and memory forensics are particularly valuable.
- Network Segmentation: Isolating sensitive systems and data from the rest of the network limits the impact of a successful infection. If Smokeloader compromises a less critical system, its ability to spread laterally and access sensitive data is reduced.
- Application Whitelisting: Only allowing approved applications to run on systems prevents unauthorized software, including Smokeloader, from executing. This is a highly effective preventative measure.
- Advanced Threat Protection: Utilizing sandboxing and threat intelligence feeds can identify and block malicious files and URLs associated with Smokeloader before they reach end-users or systems. This proactive approach significantly reduces the risk of infection.
- Security Awareness Training: Educating users about phishing scams and other social engineering tactics is critical. Smokeloader often uses these methods to initially gain access to systems. Training should focus on identifying suspicious emails, links, and attachments.
Key Indicators of Compromise (IOCs)
Identifying Smokeloader infections relies on recognizing specific indicators of compromise. These IOCs can range from suspicious network traffic patterns to unusual system behavior. Effective monitoring and analysis are crucial for early detection. Note that IOCs are dynamic and can change over time as the malware evolves.
- Suspicious Network Connections: Smokeloader communicates with its command-and-control (C2) servers. Monitoring network traffic for unusual connections to unknown or suspicious IP addresses or domains is crucial.
- Unusual Process Activity: The malware creates and manipulates processes to evade detection. Monitoring for unusual process creation, injection, or termination can be indicative of an infection. Looking for processes with unusual names or locations is also important.
- Registry Key Modifications: Smokeloader may modify registry keys to persist on the system and maintain its presence. Monitoring registry changes for suspicious entries or modifications to auto-start locations can help identify the infection.
- File System Changes: The malware may create or modify files on the system. Monitoring for new or modified files in unusual locations or with suspicious names is essential.
- Memory Artifacts: Advanced analysis of system memory can reveal the presence of Smokeloader even if it’s not directly visible on the file system. Memory forensics is a powerful technique for detecting hidden malware.
Security Best Practices
Implementing robust security best practices is crucial for preventing Smokeloader infections and minimizing the impact of any successful attacks. A comprehensive approach encompassing multiple layers of defense is essential.
- Regular Vulnerability Scanning and Penetration Testing: Proactively identify and address security vulnerabilities in systems and applications before they can be exploited by Smokeloader or other malware.
- Strong Password Policies: Enforce strong, unique passwords for all accounts to prevent unauthorized access. Multi-factor authentication adds an extra layer of security.
- Data Backup and Recovery: Regularly back up critical data to ensure business continuity in case of a successful attack. Having a robust recovery plan is essential.
- Incident Response Plan: Develop and regularly test an incident response plan to handle Smokeloader infections or other security incidents effectively. This includes procedures for containment, eradication, and recovery.
End of Discussion
Smokeloader’s modularity, coupled with its advanced evasion techniques and diverse payload delivery methods, highlights the ever-evolving nature of malware threats. Understanding its architecture, infection vectors, and communication channels is paramount for effective defense. Proactive security measures, including regular patching, robust endpoint protection, and threat intelligence, are essential in mitigating the risks associated with this sophisticated malware.



