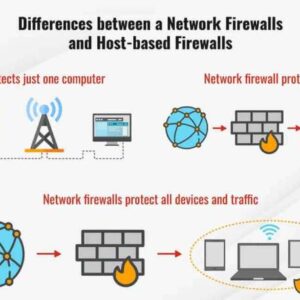
Cisco nx os zero day flaw – Cisco NX-OS zero-day flaw – sounds scary, right? It should. Imagine a hidden […]
Tag: Vulnerability Management
Rise of AI in Cybersecurity A New Era
Rise of AI in cybersecurity isn’t just a buzzword; it’s a revolution. We’re witnessing a dramatic shift in how we […]
Multiple VMware vCenter Server Flaws A Deep Dive
Multiple VMware vCenter Server flaws are a serious threat, potentially exposing your entire virtual infrastructure to malicious actors. This isn’t […]
Cyber Security News Weekly Roundup June 2
Cyber security news weekly round up june 2 – Cyber Security News Weekly Roundup June 2: Dive into the week’s […]
FortiOS Vulnerability Unauthorized Commands
FortiOS vulnerability unauthorized commands: A chilling prospect, right? Imagine malicious actors remotely controlling your supposedly secure network infrastructure. This isn’t […]
EmailGPT Vulnerability A Deep Dive
EmailGPT vulnerability – the phrase itself sends shivers down the spine of any security-conscious individual. This isn’t just another tech […]