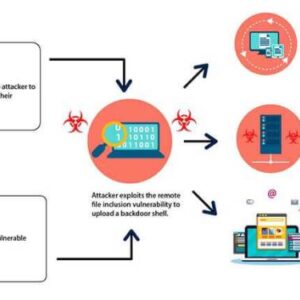
Oracle WebLogic Server vulnerability: It sounds kinda techy, right? But trust us, this isn’t just some geeky problem. A weakness […]
Tag: Vulnerability Management
Spawned Vulnerability Cloud Access A Deep Dive
Sapwned vulnerability cloud access – Spawned vulnerability cloud access—it sounds like a sci-fi thriller, right? But this isn’t fiction; it’s […]
Ivanti Endpoint Manager SQLi Vulnerability A Deep Dive
Ivanti Endpoint Manager SQLi vulnerability: The mere mention sends shivers down the spines of IT security professionals. This critical flaw […]
VMware Aria Automation SQL Injection A Deep Dive
VMware Aria Automation SQL injection: the mere mention sends shivers down the spine of any security professional. This isn’t just […]
Logsign Unified SECOps RCE Vulnerabilities
Logsign Unified SECOps RCE vulnerabilities: Think your security is airtight? Think again. This isn’t your grandpappy’s SIEM; we’re diving deep […]
SOC Best Practices A Deep Dive
SOC Best Practices: Think of your company’s data as a fortress under siege. Constant attacks, sneaky breaches, and the ever-present […]
CocoaPods Vulnerability iOS & macOS Risks
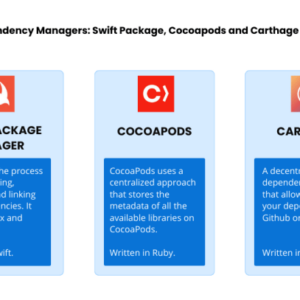
CocoaPods vulnerability iOS macOS: The seemingly innocuous act of managing dependencies in your iOS and macOS projects through CocoaPods can […]