Threat actor claiming access—it sounds like a scene from a cyberpunk thriller, right? But the reality is far more unsettling. […]
Tag: threat intelligence
RedJuliett Exploiting Firewalls
RedJuliett exploiting firewalls: It sounds like a scene from a cyberpunk thriller, doesn’t it? This isn’t fiction, though. This deep […]
Best SOC Tools Your Ultimate Guide
Best SOC tools aren’t just software; they’re the unsung heroes safeguarding your digital fortress. This isn’t your grandpappy’s security system […]
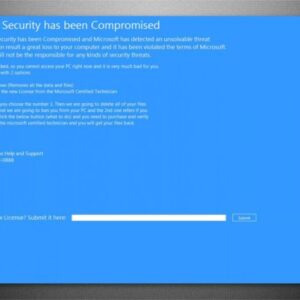
Microsoft Detect Compromised Devices
Microsoft Detect Compromised Devices: It’s a digital battlefield out there, and your precious data is the prize. This isn’t some […]
Smokeloader Modular Malware Capabilities
Smokeloader modular malware capabilities represent a significant threat in the cybersecurity landscape. This sophisticated malware leverages a modular architecture, allowing […]
Threat Claiming API Database A Deep Dive
Threat Claiming API Database: Ever wondered how we track and manage cyber threats at scale? Imagine a central hub, a […]
Sandbox Malware Analysis Essential Tools
Tools for conducting malware traffic analysis in a sandbox are crucial for understanding the behavior of malicious software. Think of […]