DDoS protection tools are your first line of defense against the digital onslaught of distributed denial-of-service attacks. These attacks can […]
Tag: Network Security
RedJuliett Exploiting Firewalls
RedJuliett exploiting firewalls: It sounds like a scene from a cyberpunk thriller, doesn’t it? This isn’t fiction, though. This deep […]
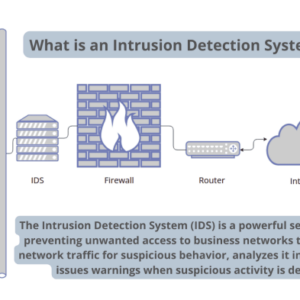
Intrusion Detection Prevention Systems A Deep Dive
Intrusion detection prevention systems (IDPS) are the unsung heroes of cybersecurity, silently guarding our digital fortresses against a relentless barrage […]
Gored DNS ICMP Tunneling C2 Communication
Gored DNS ICMP tunneling C2 communication: Think of it as a high-stakes game of digital hide-and-seek. Attackers are using increasingly […]
Attacking Telcos Using Espionage A Deep Dive
Attacking telcos using espionage isn’t just a movie plot; it’s a chilling reality. From state-sponsored cyberattacks to financially motivated data […]
Critical Asus Router Flaw Attacker Exploits
Critical Asus router flaw attacker: Your seemingly secure home network might be more vulnerable than you think. A critical vulnerability […]
BondNet High Performance Bots C2 Server
BondNet High Performance Bots C2 Server: Dive into the heart of a sophisticated network where high-powered bots dance to the […]