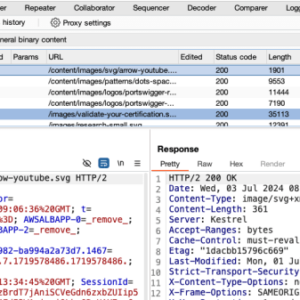
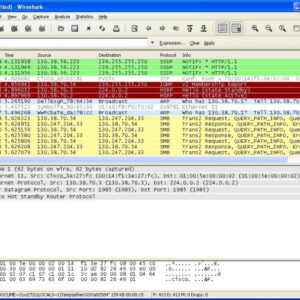
VPN port shadow traffic interception: Ever wondered how your supposedly anonymous online activity might be tracked, even with a VPN? […]
Tag: Network Security
Cisco SSM Password Change Vulnerability A Security Threat
Cisco SSM password change vulnerability: The phrase alone sends shivers down the spines of network admins everywhere. This isn’t your […]
LiFi Protocol Hack Security Risks & Solutions
Li fi protocol hack – LiFi protocol hack: It sounds like something out of a sci-fi thriller, right? But the […]
Netgear Vulnerabilities Bypass Authentication
Netgear vulnerabilities bypass authentication: Think your home network is safe? Think again. We’re diving deep into the shadowy world of […]
Juniper Junos Flaw Root Access Vulnerability
Juniper junos flaw root access – Juniper Junos flaw: root access. Sounds scary, right? It should. This isn’t your average […]
Blast Radius Man-in-the-Middle Attack
Blast radius man in the middle attack – Blast radius man-in-the-middle attack: Ever wondered how far the damage from a […]
Threat Actors Claiming Nokia Database Breach
Threat actors claiming breach of nokia database – Threat actors claiming breach of Nokia’s database? This isn’t your average tech […]