APK packer to hide malware file structure? Sounds like a digital cat-and-mouse game, right? Malicious actors are constantly finding new […]
Tag: Malware Analysis
Malware Dissection with Gemini A Deep Dive
Malware dissection with Gemini: Forget clunky, outdated methods. We’re diving headfirst into the future of malware analysis, leveraging the power […]
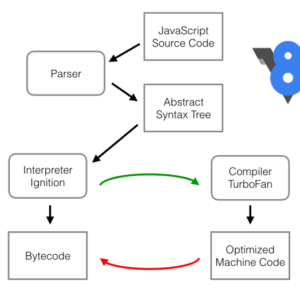
Hackers Compiled V8 JavaScript Malware
Hackers Compiled V8 JavaScript Malware: It sounds like something out of a cyberpunk thriller, right? But the reality is far […]
Kimsuky Hackers EXE & DOCX Attack Deep Dive
Kimsuky hackers exe docx attacks: Think North Korean state-sponsored hacking, sophisticated social engineering, and some seriously nasty malware. We’re diving […]
Researchers Decrypt Donex Ransomware
Researchers decrypt Donex ransomware—a major win in the ongoing battle against cybercrime. This sophisticated ransomware strain, known for its robust […]
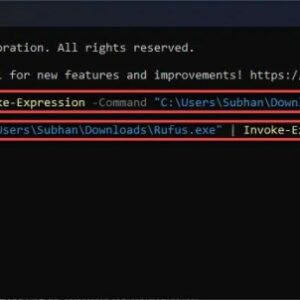
Kematian Stealer Abuses PowerShell A Deep Dive
Kematian Stealer abuses PowerShell, leveraging its scripting capabilities for malicious purposes. This sophisticated malware utilizes PowerShell’s inherent flexibility to bypass […]
Cyber Security Search Engines Your Digital Shield
Cyber security search engines: Forget Google; these aren’t your average search bars. They’re the digital sheriffs of the internet, hunting […]