TeamViewer discloses investigation: The remote access giant is under the microscope, sparking a whirlwind of speculation and concern. This isn’t […]
Tag: Cybersecurity
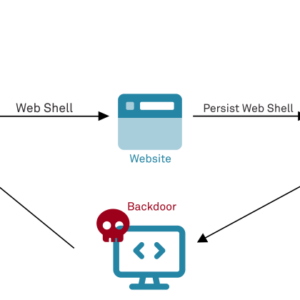
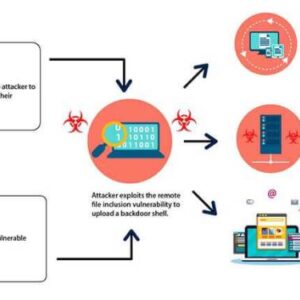
Exploiting HTTP File Servers A Deep Dive
Exploiting HTTP file servers: Sounds like something out of a cyberpunk thriller, right? But the reality is far more mundane—and […]
Team ARXU Attacks Schools, Banks
Team arxu attacks schools banks – Team ARXU attacks schools and banks—a chilling scenario that plunges us into the dark […]
Logsign Unified SECOps RCE Vulnerabilities
Logsign Unified SECOps RCE vulnerabilities: Think your security is airtight? Think again. This isn’t your grandpappy’s SIEM; we’re diving deep […]
SOC Best Practices A Deep Dive
SOC Best Practices: Think of your company’s data as a fortress under siege. Constant attacks, sneaky breaches, and the ever-present […]
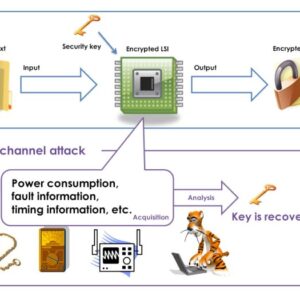
Snailload Side Channel Attack Unveiling the Threat
Snailload side channel attacks: Ever heard of them? These sneaky digital ninjas exploit hidden pathways in your system, revealing sensitive […]
Ransomware Threats Via Phone Calls
Ransomware threats via phone calls: Think it’s a thing of the past? Think again. These sneaky attacks are evolving, using […]