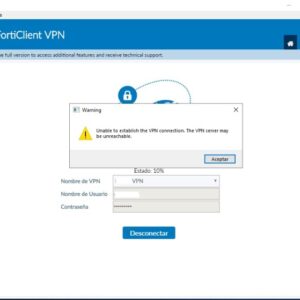
Claims to have unauthorized Fortinet VPN access? Whoa, hold up. That’s a seriously spicy cybersecurity situation. This isn’t just some […]
Cryptotech
Fishxproxy Fuels Phishing Attacks
Fishxproxy fuels phishing attacks, escalating the threat landscape for individuals and organizations alike. This insidious proxy service masks the origin […]
PHP Vulnerability Exploited A Deep Dive
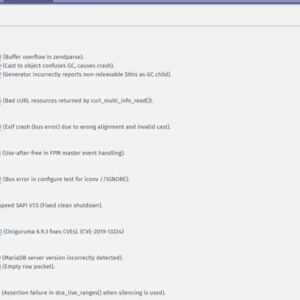
PHP vulnerability exploited – that’s the chilling reality facing many websites. From sneaky SQL injections to devastating cross-site scripting attacks, […]
Phishing Attack SharePoint Servers A Deep Dive
Phishing attack SharePoint servers? Yeah, it’s a bigger deal than you think. These seemingly innocuous platforms, vital for countless businesses, […]
Apple Warns of Users A Deep Dive
Apple Warns of Users: That ominous notification pops up, and suddenly your carefully curated digital world feels a little less […]
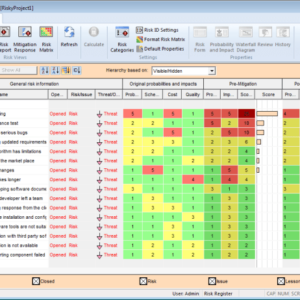
Enterprise Risk Management Tools Your Business Shield
Enterprise risk management tools aren’t just software; they’re your company’s safety net. They’re the unsung heroes preventing costly mistakes and […]
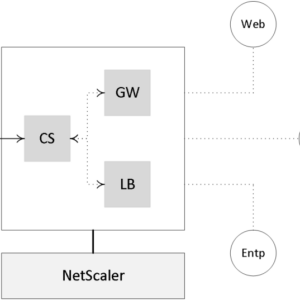
NetScaler ADC Gateway Regression A Deep Dive
Netscaler adc gateway regresshion – NetScaler ADC gateway regression: sounds kinda techy, right? But trust us, understanding how to prevent […]