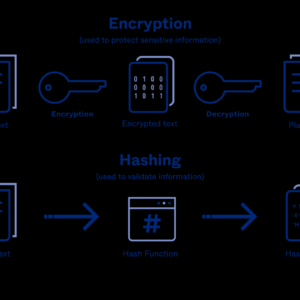
Encryption algorithms used in malware: It’s a digital cat-and-mouse game, a constant arms race between cybercriminals and security experts. Malware […]
Cryptotech
LiFi Protocol Hack Security Risks & Solutions
Li fi protocol hack – LiFi protocol hack: It sounds like something out of a sci-fi thriller, right? But the […]
Massive Data of 361M Emails & Passwords Exposed
Massive data of 361m emails passwords – Massive data of 361 million emails and passwords—that’s the chilling reality we’re facing. […]
Cynet Revolutionizing Cybersecurity for MSPs
Cynet is revolutionizing cybersecurity for MSPs. Tired of juggling multiple client security needs and struggling to stay ahead of ever-evolving […]
BMW Hong Kong Faces Major Data Breach
BMW Hong Kong faces major data breach – a shocking revelation that throws the spotlight on the vulnerability of even […]
Apache HugeGraph Server RCE Vulnerability Explored
Apache HugeGraph Server RCE Vulnerability: Imagine a digital fortress breached, data scattered, and systems crippled. This isn’t science fiction; it’s […]
Malware Dissection with Gemini A Deep Dive
Malware dissection with Gemini: Forget clunky, outdated methods. We’re diving headfirst into the future of malware analysis, leveraging the power […]