Passkeys via AITM phishing attacks: Think you’re safe with passkeys? Think again. These next-gen logins, touted as password killers, are […]
Cryptotech
Multiple Flaws Splunk Enterprise A Deep Dive
Multiple flaws Splunk Enterprise? Yeah, we’ve dug deep into the issues plaguing this popular SIEM. From crippling security vulnerabilities in […]
Developers Beware Hackers Are Lurking
Developers beware hackers! The digital world is a wild west, and developers are increasingly becoming prime targets for sophisticated cyberattacks. […]
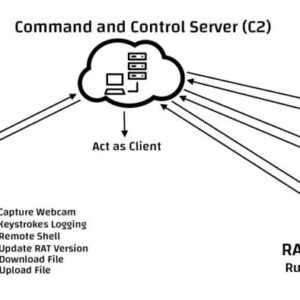
Spymax Rat Telegram Android Attack A Deep Dive
Spymax Rat Telegram Android attack: Think your phone’s safe? Think again. This sneaky malware uses Telegram as its secret weapon, […]
Androids Security Update A Deep Dive
Androids security update: It’s the silent guardian, the watchful protector, the thing that keeps your precious digital life from becoming […]
CocoaPods Vulnerability iOS & macOS Risks
CocoaPods vulnerability iOS macOS: The seemingly innocuous act of managing dependencies in your iOS and macOS projects through CocoaPods can […]
Indirector Side Channel Attacks Unveiling the Secrets
Indirector side channel attacks are the sneaky ninjas of the cybersecurity world, silently extracting sensitive data through indirect means. Unlike […]