CISA warns of hackers exploiting OS command injection—a seriously scary situation. Think of it like this: hackers are finding sneaky […]
Cryptotech
Lulu Hypermarket Data Breach What Happened?
Lulu Hypermarket data breach: the words alone send shivers down your spine, right? Imagine thousands of customers’ personal details – […]
Wireshark 4.2.6 Released Whats New?
Wireshark 4 2 6 released – Wireshark 4.2.6 released—and the network analysis world just got a whole lot snappier. This […]
VMware Aria Automation SQL Injection A Deep Dive
VMware Aria Automation SQL injection: the mere mention sends shivers down the spine of any security professional. This isn’t just […]
Cyber Security Teams Should React to a Potential Breach
Cyber security teams should react to a potential breach—it’s not a matter of *if*, but *when*. A single successful attack […]
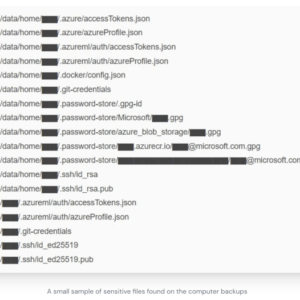
Microsoft Employees Data Exposed A Deep Dive
Microsoft employees data exposed – the headline alone sends shivers down the spine. This isn’t just another tech breach; it’s […]
The Ultimate Guide to PDF Manipulation
The Ultimate Guide to PDF Manipulation: Dive into the world of PDFs and unlock their full potential! From simple edits […]