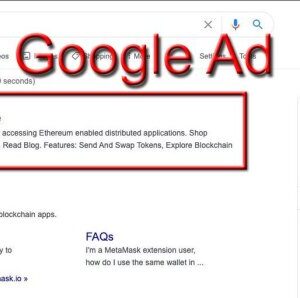
Weaponized documents QR code phishing: Sounds like a sci-fi thriller, right? It’s not. This sneaky tactic uses everyday QR codes […]
Category: Cybersecurity
IntelBroker Claiming Leak Data Breach Fallout
IntelBroker claiming leak – the words alone send shivers down the spine. This isn’t your average data mishap; we’re talking […]
Weaponized Cisco Webex Meetings App A Deep Dive
Weaponized Cisco Webex Meetings App: Think your video conference is just a harmless meeting? Think again. From sneaky phishing attacks […]
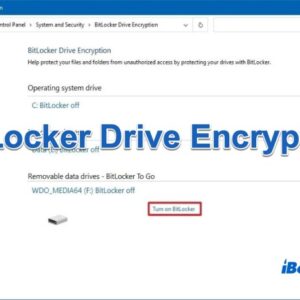
ShrinkLocker BitLocker Ransomware A Deep Dive
ShrinkLocker BitLocker ransomware: the name itself sounds like a digital nightmare, right? This insidious malware targets systems supposedly protected by […]
AI-Powered Detecting Zero-Day Exploits
Ai powereds detecting zero day – AI-Powered Detecting Zero-Day Exploits: Forget the Wild West of cybersecurity – the age of […]
Beware of Weaponized PDFs A Digital Danger
Beware of weaponized PDFs: that seemingly innocent document on your screen could be a Trojan horse, silently delivering malware, stealing […]
New SatanStealer Malware A Deep Dive
New SatanStealer malware is causing serious headaches for cybersecurity professionals. This insidious threat isn’t just another run-of-the-mill virus; it’s a […]