SOC Best Practices: Think of your company’s data as a fortress under siege. Constant attacks, sneaky breaches, and the ever-present […]
Category: Cybersecurity
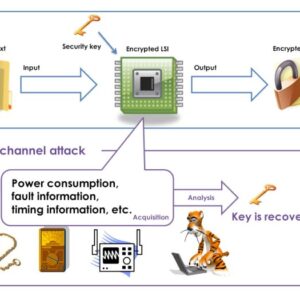
Snailload Side Channel Attack Unveiling the Threat
Snailload side channel attacks: Ever heard of them? These sneaky digital ninjas exploit hidden pathways in your system, revealing sensitive […]
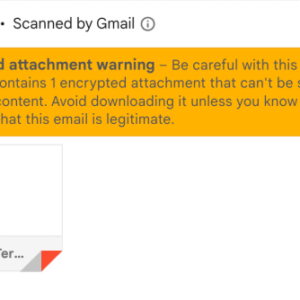
Malicious PDF Microsoft 2FA Warning A Deep Dive
Malicious PDF Microsoft 2FA warning: Sounds scary, right? It should. These aren’t your average printer-friendly documents; they’re sophisticated traps designed […]
Ransomware Threats Via Phone Calls
Ransomware threats via phone calls: Think it’s a thing of the past? Think again. These sneaky attacks are evolving, using […]
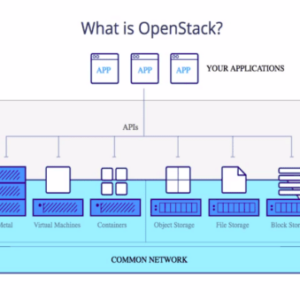
OpenStack Arbitrary File Access Flaw
OpenStack arbitrary file access flaw: A chilling vulnerability that could grant unauthorized access to sensitive data, potentially leading to a […]
Kematian Stealer Abuses PowerShell A Deep Dive
Kematian Stealer abuses PowerShell, leveraging its scripting capabilities for malicious purposes. This sophisticated malware utilizes PowerShell’s inherent flexibility to bypass […]
Malicious QR Reader A Sneaky Threat
Malicious QR reader: Sounds kinda sci-fi, right? But it’s a real threat lurking in plain sight. These sneaky little codes, […]