Hackers attacking hotels—it’s a headline that’s becoming increasingly common. From sneaky phishing scams targeting unsuspecting guests to sophisticated malware infections […]
Author: admin
Hackers Leveraging Social Engineering Malware
Hackers leveraging social engineering malware are increasingly sophisticated, blending psychological manipulation with technological prowess. This insidious combination allows them to […]
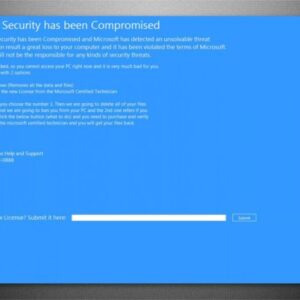
Microsoft Detect Compromised Devices
Microsoft Detect Compromised Devices: It’s a digital battlefield out there, and your precious data is the prize. This isn’t some […]
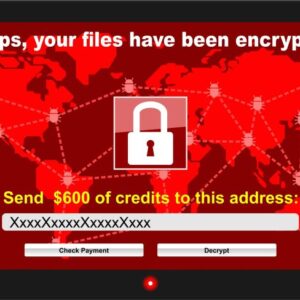
New Opix Ransomware Encrypting Files
New Opix ransomware encrypting files? Yeah, it’s happening. This nasty piece of malware is locking up data, leaving victims scrambling […]
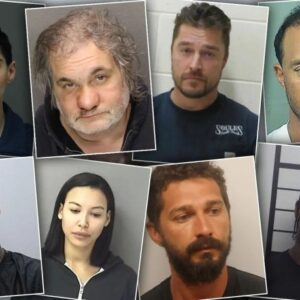
Empire Market Founders Charged Bust!
Empire Market founders charged? Yeah, you heard right. The shadowy figures behind one of the dark web’s biggest illegal marketplaces […]
Multiple VMware vCenter Server Flaws A Deep Dive
Multiple VMware vCenter Server flaws are a serious threat, potentially exposing your entire virtual infrastructure to malicious actors. This isn’t […]
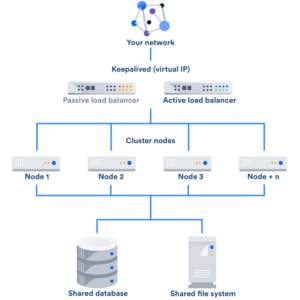
Chinese Actors, F5 Load Balancers A Tech Tale
Chinese actors f5 load balancers – Chinese actors, F5 load balancers—a seemingly odd pairing, right? But delve deeper, and you’ll […]