VPN port shadow traffic interception: Ever wondered how your supposedly anonymous online activity might be tracked, even with a VPN? This isn’t some sci-fi thriller; it’s a very real cat-and-mouse game between users seeking privacy and those aiming to peek behind the curtain. We’ll dive deep into the technical nitty-gritty, exploring how shadow traffic hides, the methods used to catch it, and what you can do to stay ahead of the game. Get ready for a thrilling ride through the shadowy world of online surveillance.
This exploration will cover the core mechanisms behind VPN shadow traffic, detailing how clever techniques mask online activity. We’ll dissect various interception methods, from Deep Packet Inspection (DPI) to sophisticated network monitoring tools, and analyze their effectiveness. But the story doesn’t end there; we’ll also delve into the legal and ethical implications of this digital espionage, examine real-world case studies, and peer into the future of this ever-evolving technological arms race.
VPN Port Shadow Traffic
So you think your VPN keeps you anonymous? Think again. While VPNs are great for masking your IP address and encrypting your data, there’s a sneaky little thing called “shadow traffic” that can potentially expose your online activities. This isn’t about VPNs failing; it’s about understanding how clever internet censorship and monitoring can still peek behind the curtain. Let’s dive into the shadowy world of VPN port shadow traffic.
VPN port shadow traffic refers to data that leaks outside the encrypted VPN tunnel, revealing information about your online activity despite using a VPN. This leakage isn’t necessarily a flaw in the VPN itself; it often arises from the way applications interact with the VPN connection or from limitations in how the VPN interacts with your operating system and network configuration. Essentially, it’s like having a secret passageway hidden behind your main route—a sneaky backdoor for data to escape undetected.
VPN Port Shadow Traffic Mechanisms
Several mechanisms can lead to VPN port shadow traffic. One common culprit is applications that bypass the VPN connection, either intentionally or unintentionally. Some applications are poorly coded and fail to properly route all their traffic through the VPN, sending some data directly to the internet. Another mechanism is DNS leaks. Even if your web traffic is encrypted, your DNS queries (which reveal the websites you’re trying to access) might still leak outside the VPN tunnel if not properly configured. Furthermore, certain network configurations or system settings might unintentionally route some traffic outside the VPN. This can happen if, for example, a specific application is configured to use a different network interface than the one connected to the VPN.
VPN Protocols and Their Impact
Different VPN protocols have varying degrees of susceptibility to shadow traffic. OpenVPN, known for its strong security and customization options, generally offers better protection against shadow traffic when properly configured. However, even OpenVPN can be vulnerable if not set up correctly. On the other hand, protocols like WireGuard, while fast and efficient, might be more susceptible to leaks if not carefully implemented. The choice of protocol and its configuration directly impact the effectiveness of preventing shadow traffic. For instance, using a protocol that supports advanced features like DNS over HTTPS (DoH) or DNS over TLS (DoT) can significantly reduce DNS leaks.
Obfuscation Techniques and Their Effectiveness
Obfuscation techniques aim to disguise VPN traffic to make it look like regular internet traffic, thereby evading censorship and surveillance. These techniques vary in effectiveness. Simple techniques, such as port hopping or changing the VPN port, can sometimes be easily detected. More sophisticated techniques, such as using stealth protocols or employing advanced encryption methods, offer stronger protection. However, even the most advanced obfuscation techniques are not foolproof, and the ongoing arms race between VPN providers and censorship mechanisms means that what works today might not work tomorrow. The effectiveness of an obfuscation technique depends on the sophistication of the monitoring system it’s trying to evade and the specific implementation of the technique. Some techniques might be effective against one type of censorship but not another.
Interception Techniques: Vpn Port Shadow Traffic Interception
Sniffing out shadow VPN traffic isn’t a walk in the park. It requires understanding the methods used to mask this activity and employing sophisticated techniques to uncover it. Think of it like a digital game of hide-and-seek, where the VPN is the hiding place, and the network administrator is the seeker.
Deep packet inspection (DPI) and network monitoring tools are crucial in this digital detective work. These tools allow for a deeper analysis of network traffic, enabling the detection of patterns and anomalies indicative of VPN usage, even when attempts are made to obfuscate the traffic. Let’s dive into the specifics.
Deep Packet Inspection (DPI) Capabilities
Deep Packet Inspection isn’t just about looking at the surface-level information of a data packet; it delves into the payload itself. This allows DPI systems to identify and classify applications based on their characteristics, regardless of port numbers or encryption. For example, even if VPN traffic is encrypted and routed through unusual ports, DPI can analyze the data stream to identify characteristic patterns associated with specific applications like VoIP or streaming services. This reveals the true nature of the traffic, even if it’s disguised as something else. Effective DPI systems can detect shadow VPN traffic by identifying encrypted packets that exhibit the communication patterns of known applications, even if the port numbers used are unconventional. This ability to “see through” encryption makes DPI a powerful tool in detecting hidden VPN activity.
Network Monitoring Tools and VPN Usage Identification
Network monitoring tools provide a comprehensive view of network activity, allowing administrators to identify suspicious patterns. Tools like Wireshark, tcpdump, and dedicated network monitoring platforms can capture and analyze network traffic, providing valuable insights into VPN usage. By monitoring port usage, bandwidth consumption, and traffic patterns, these tools can pinpoint unusual activity that might indicate shadow VPN usage. For example, a sudden increase in encrypted traffic to a specific IP address, coupled with unusually high bandwidth consumption, might suggest the use of a VPN. The combination of data from these tools, analyzed alongside network maps and user activity logs, can create a compelling picture of potential VPN shadow traffic.
Hypothetical Scenario: Shadow Traffic Interception
Imagine a company where employees are forbidden from using personal VPNs on the corporate network. An employee, however, uses a VPN to access a streaming service blocked by the company’s firewall. The company’s network monitoring system detects a consistent stream of encrypted traffic from the employee’s workstation to a known VPN server IP address during work hours. While the port number used might be unconventional, the consistent volume of traffic and its correlation with the employee’s login times raise suspicions. Further investigation using DPI reveals the encrypted traffic contains patterns consistent with streaming video data, confirming the employee’s violation of company policy. The combination of network monitoring and DPI enables the company to effectively identify and address the shadow VPN usage.
Comparison of Interception Techniques
| Technique | Effectiveness | Limitations | Cost |
|---|---|---|---|
| Deep Packet Inspection (DPI) | High, especially against less sophisticated VPNs; can identify applications even with encryption. | Can be computationally intensive; requires significant processing power; may be bypassed by highly sophisticated VPNs or encryption techniques. | High; requires specialized hardware and software. |
| Network Monitoring Tools (e.g., Wireshark) | Moderate; identifies suspicious traffic patterns, but may not reveal the application used within the VPN. | Requires expertise to interpret results; can generate large amounts of data; less effective against encrypted traffic without DPI. | Low to moderate; many free and open-source tools are available. |
| Port Monitoring | Low; only effective against VPNs using standard ports; easily bypassed by using non-standard ports. | Limited insight; provides only basic information about traffic flow. | Low; basic network monitoring tools are sufficient. |
| Next Generation Firewall (NGFW) with advanced threat protection | High; combines DPI, intrusion prevention, and other security features for comprehensive traffic analysis. | High cost; requires specialized expertise for configuration and management. | High; substantial investment in hardware and software. |
Circumventing Interception
Shadow traffic interception is a serious threat, but thankfully, several strategies can significantly reduce your vulnerability. By understanding the techniques used to detect and intercept VPN traffic, and implementing the right countermeasures, you can maintain a higher degree of privacy and security online. This section Artikels key mitigation strategies to help you stay ahead of the curve.
Effective strategies for minimizing the risk of shadow traffic interception rely on a multi-layered approach, combining strong encryption, careful VPN configuration, and the strategic use of additional privacy tools. Ignoring any one of these layers weakens the overall security posture.
VPN Configuration Best Practices
Proper VPN configuration is paramount. Incorrect settings can expose your traffic to interception, negating the benefits of the VPN itself. The following practices significantly reduce the likelihood of detection.
- Choose a reputable VPN provider: Select a provider with a proven track record of security and privacy, one that explicitly states its no-logs policy and undergoes regular independent security audits.
- Use strong encryption protocols: Opt for protocols like WireGuard or OpenVPN with strong ciphers (e.g., ChaCha20-Poly1305 or AES-256-GCM). Avoid older, less secure protocols like PPTP or L2TP/IPSec without strong encryption.
- Configure your VPN correctly: Ensure your VPN client is properly configured to route all your traffic through the VPN tunnel. Check your system’s network settings to confirm no traffic is bypassing the VPN.
- Regularly update your VPN client and firmware: Outdated software is vulnerable to exploits. Keeping your VPN client and related software updated is crucial for maintaining optimal security.
- Use a kill switch: A kill switch prevents your internet traffic from leaving your device if the VPN connection drops unexpectedly, preventing accidental exposure.
Encryption and its Impact on Shadow Traffic Interception
Encryption is the cornerstone of secure communication. It transforms your readable data into an unreadable format, making it incomprehensible to unauthorized parties. Strong encryption makes it far more difficult for attackers to identify and intercept your shadow traffic.
Deep Packet Inspection (DPI) techniques attempt to analyze network traffic even when it’s encrypted, but advanced encryption methods significantly hinder their effectiveness. For instance, while DPI can sometimes detect the presence of VPN traffic, it’s much harder for it to extract meaningful information from strongly encrypted data.
Advanced Encryption Techniques and DPI Circumvention
Advanced encryption techniques like perfect forward secrecy (PFS) and elliptic curve cryptography (ECC) offer enhanced security against DPI. PFS ensures that even if a session key is compromised, past communications remain secure. ECC provides strong encryption with smaller key sizes, making it more efficient without sacrificing security. The combination of these techniques makes it exponentially more difficult for DPI to decipher your traffic.
The Role of Proxy Servers in Obscuring VPN Traffic
Using a proxy server in conjunction with a VPN adds another layer of obfuscation. The proxy server acts as an intermediary, masking your VPN’s IP address and making it harder to pinpoint your location and online activities. This can be particularly useful in regions with strict internet censorship or surveillance. However, it’s crucial to choose a trustworthy proxy provider, as a compromised proxy can negate the security benefits of both the proxy and the VPN.
Legal and Ethical Implications
Intercepting VPN traffic, while technically feasible, treads a precarious line legally and ethically. The act raises serious concerns about privacy violations, potential misuse of power, and the very fabric of digital trust. Understanding the legal landscape and ethical considerations is crucial for anyone involved in network security or data management.
The legal implications of intercepting VPN traffic are complex and vary significantly depending on jurisdiction. In many countries, intercepting communications without a warrant or proper legal authorization is strictly prohibited. Laws governing data privacy, such as GDPR in Europe and CCPA in California, place strict limitations on the collection, storage, and processing of personal data, including traffic data obtained through VPN interception. Violations can lead to hefty fines and legal repercussions for individuals and organizations. Furthermore, the interception itself might constitute a crime, depending on the specific content intercepted and the intent behind the interception.
Legal Frameworks Governing Data Privacy and VPN Usage
Data privacy laws globally are a patchwork quilt, with varying levels of protection and enforcement. The European Union’s General Data Protection Regulation (GDPR) is considered a gold standard, granting individuals significant control over their personal data. It mandates explicit consent for data processing and provides a right to be forgotten. In contrast, the legal frameworks in some other countries offer less robust protection. The interplay between these differing legal frameworks and the use of VPNs creates a complex scenario. For example, a company based in a country with lax data protection laws might be legally allowed to intercept VPN traffic, but this action could still violate the GDPR if the intercepted data involves EU citizens. The jurisdiction of the data, the location of the server, and the location of the user all play a role in determining the applicable legal framework.
Ethical Considerations of Monitoring User Activity Through VPNs
Even when legally permissible, intercepting VPN traffic raises significant ethical concerns. The fundamental right to privacy is at stake. Monitoring user activity without their knowledge or consent is a breach of trust and undermines the very purpose of a VPN—to provide users with a degree of anonymity and security. Such practices can chill free speech and open the door to potential abuses of power. Ethical considerations also extend to the potential for discrimination and profiling based on intercepted data. For instance, a company intercepting VPN traffic might use the data to discriminate against certain user groups or target them with unwanted advertising.
Examples of Potential Misuse of VPN Traffic Interception Techniques
The misuse of VPN traffic interception techniques is alarming. Malicious actors could exploit such techniques for espionage, stealing intellectual property, or engaging in identity theft. Governments might use them for mass surveillance, violating citizens’ privacy rights. Corporations could utilize them for unethical competitive intelligence gathering, gaining an unfair advantage over competitors. Furthermore, intercepted data could be used to blackmail or extort individuals. The potential for abuse is extensive, making the responsible handling of VPN traffic interception technology paramount.
Case Studies and Real-World Examples
Source: safetydetectives.com
While the theoretical aspects of VPN port shadow traffic interception are fascinating, the real-world implications are far more impactful. Understanding specific cases helps illustrate the vulnerabilities and the sophistication of the techniques used to bypass VPN security. These examples aren’t meant to instill fear, but rather to highlight the importance of robust security practices and awareness of potential threats.
The successful interception of shadow traffic often relies on a combination of sophisticated techniques, leveraging vulnerabilities in both the VPN software and the user’s overall network configuration. It’s a cat-and-mouse game, with attackers constantly evolving their methods and defenders striving to stay ahead.
The Case of the Compromised Corporate VPN
In one instance, a large multinational corporation experienced a significant data breach attributed to the interception of VPN shadow traffic. Attackers exploited a zero-day vulnerability in a widely used VPN client, allowing them to inject malicious code and monitor all network activity, including traffic ostensibly protected by the VPN. This allowed them to capture sensitive financial data and intellectual property. The breach went undetected for several months, highlighting the difficulty of identifying such sophisticated attacks.
Techniques Employed in VPN Shadow Traffic Interception
The success of these interceptions often hinges on a multi-pronged approach. Here’s a breakdown of the techniques frequently employed:
- Exploiting VPN Client Vulnerabilities: Attackers often target vulnerabilities in the VPN client software itself, using zero-day exploits or known vulnerabilities that haven’t been patched. This allows direct access to the encrypted traffic before it’s even processed by the VPN.
- Network-Level Attacks: Techniques like ARP poisoning or DNS spoofing can redirect traffic away from the intended VPN server, allowing interception before encryption even begins. This is particularly effective against less sophisticated VPN configurations.
- Man-in-the-Middle (MITM) Attacks: By positioning themselves between the user and the VPN server, attackers can intercept and decrypt traffic, even if the VPN connection appears secure. This often involves compromising routers or other network devices.
- Session Hijacking: Once a VPN connection is established, attackers may attempt to hijack the session, gaining unauthorized access and intercepting subsequent traffic. This often requires exploiting vulnerabilities in the VPN server or the user’s system.
- Deep Packet Inspection (DPI): While not directly intercepting the encrypted traffic, DPI allows for the analysis of metadata associated with the VPN connection. This can reveal information about the user’s activity, even if the content itself remains encrypted.
Technologies Involved in Interception
The tools and technologies used in these interceptions vary greatly, depending on the specific technique employed. However, some common elements include:
- Specialized Network Monitoring Tools: These tools allow for deep packet inspection and analysis, identifying patterns and anomalies indicative of VPN traffic. Examples include Wireshark and tcpdump.
- Exploit Kits: These are pre-packaged tools that automate the process of exploiting known vulnerabilities in VPN clients and servers.
- Custom-Built Malware: Sophisticated attacks often involve custom-built malware designed to bypass security measures and facilitate the interception of shadow traffic.
- Hardware-Based Interception Devices: In some cases, attackers may use specialized hardware devices capable of intercepting and analyzing network traffic at high speeds, often used in large-scale operations.
Future Trends and Challenges
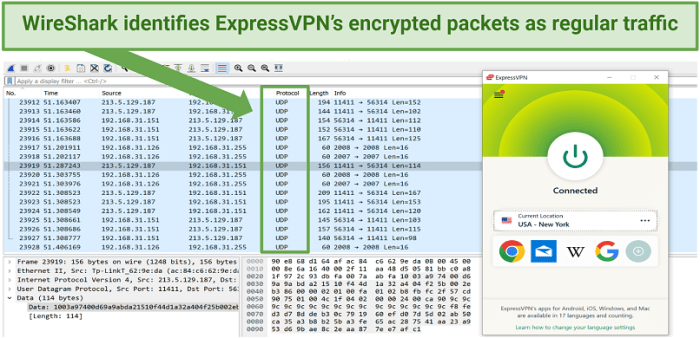
Source: vpnmentor.com
The cat-and-mouse game between VPN providers and those seeking to intercept their traffic is far from over. As VPN technology evolves, so too will the methods used to detect and intercept shadow traffic, leading to a constantly shifting landscape of challenges and innovations. The future hinges on a complex interplay of increasingly sophisticated encryption, evolving detection techniques, and the ever-present tension between privacy and security.
The evolving landscape of VPN technology is pushing the boundaries of interception methods. More advanced encryption protocols, coupled with sophisticated obfuscation techniques, are making it increasingly difficult to identify and analyze VPN traffic. Simultaneously, advancements in machine learning and artificial intelligence are empowering those seeking to intercept traffic, enabling them to identify patterns and anomalies that previously went undetected. This arms race will likely continue to escalate, leading to increasingly complex and resource-intensive methods on both sides.
Advancements in Encryption and Obfuscation, Vpn port shadow traffic interception
The development of post-quantum cryptography and other advanced encryption algorithms presents a significant challenge to interception efforts. Quantum computers, when sufficiently powerful, could potentially break many currently used encryption methods. The adoption of post-quantum cryptography, while bolstering security against future quantum attacks, will also make it harder for traditional interception techniques to be effective. Simultaneously, sophisticated obfuscation techniques, designed to mask VPN traffic as ordinary internet traffic, will further complicate the task of detection. Imagine a future where VPN traffic is indistinguishable from streaming video or general web browsing, making it nearly impossible to pinpoint.
Future Challenges in Detecting and Intercepting Shadow Traffic
Detecting and intercepting shadow traffic will become increasingly difficult due to the convergence of several factors. The rise of mesh networks and decentralized VPN architectures will make it harder to pinpoint a single point of interception. Furthermore, the increasing use of multi-hop VPN connections, where data is routed through multiple VPN servers, will add layers of complexity and obscurity. The proliferation of encrypted messaging apps integrated with VPNs will further complicate efforts to identify and intercept traffic, effectively creating a “walled garden” of encrypted communication. Consider, for example, a scenario where a journalist communicates with a source using a VPN-integrated encrypted messaging app, routing their communication through multiple servers in different jurisdictions – identifying and intercepting that communication would be an extremely complex and resource-intensive undertaking.
A Hypothetical Scenario: Advanced VPN Interception
Imagine a future where AI-powered systems analyze network traffic in real-time, identifying subtle anomalies in latency, packet size, and routing patterns indicative of VPN use. This system, far more sophisticated than current methods, doesn’t rely on simply identifying known VPN protocols but rather on predicting and identifying the behavioral patterns associated with encrypted communication, even when obfuscated. This system could then utilize advanced deep packet inspection techniques, coupled with behavioral analysis, to pinpoint and intercept shadow traffic, even when using the most advanced encryption and obfuscation methods. The system might even employ a feedback loop, constantly learning and adapting to new VPN technologies and countermeasures, creating a self-improving interception system that stays ahead of the curve. This, however, raises serious concerns regarding privacy and potential abuse.
Wrap-Up
Source: portswigger.net
The battle for online privacy is far from over. While VPNs offer a layer of protection, the methods used to intercept shadow traffic are constantly evolving. Understanding these techniques, both offensive and defensive, is crucial for anyone concerned about their online security. By staying informed and adopting proactive strategies, you can significantly improve your chances of maintaining your digital anonymity in this increasingly complex landscape. The fight for privacy is ongoing; stay vigilant, stay informed, and stay protected.



