Fin7 bypass EDR solutions represent a critical challenge in cybersecurity. This notorious threat actor continuously adapts, leveraging sophisticated techniques to evade even the most advanced endpoint detection and response (EDR) systems. Understanding Fin7’s tactics, the limitations of current EDR technology, and the emerging strategies for mitigation is crucial for organizations seeking to protect themselves against this persistent threat. We’ll explore how Fin7 exploits vulnerabilities, their advanced evasion methods, and the best practices for bolstering your defenses.
This deep dive will examine Fin7’s arsenal, from living-off-the-land binaries (LOLBins) to process injection and DLL hijacking, illustrating how they manipulate system processes and memory to achieve stealth. We’ll also analyze effective countermeasures, including enhanced logging, advanced threat hunting, and the integration of threat intelligence feeds to improve detection capabilities. The evolving landscape of AI and machine learning in cybersecurity will also be discussed, predicting the future of this cat-and-mouse game.
Understanding Fin7 Tactics and Techniques
Fin7, a prolific and sophisticated cybercrime group, has terrorized businesses globally for years, stealing sensitive financial data through highly targeted attacks. Their success stems from a combination of advanced techniques, meticulous planning, and a relentless focus on evading detection. Understanding their methods is crucial for building robust defenses.
Fin7’s arsenal is constantly evolving, but certain patterns and tactics consistently emerge. Their operations rely on a blend of social engineering, malware deployment, and exploitation of vulnerabilities to gain initial access and maintain persistence within victim networks.
Attack Vectors
Fin7 employs a multi-pronged approach to compromise targets. Spear phishing emails, often highly personalized and convincingly crafted to mimic legitimate communications, remain a cornerstone of their campaigns. These emails frequently contain malicious attachments or links leading to malware downloads. They also leverage compromised credentials obtained through various means, including brute-force attacks and exploiting vulnerabilities in network infrastructure. Finally, they’ve been known to utilize compromised third-party vendors or service providers to gain access to target networks. This approach highlights their strategic focus on exploiting weaknesses in the entire ecosystem surrounding their targets.
Evading Security Measures
Fin7 consistently demonstrates an ability to bypass traditional security measures. They utilize sophisticated malware that employs techniques like code obfuscation and polymorphism to evade signature-based detection systems. Their malware often incorporates rootkit capabilities to maintain persistence and hinder analysis. Furthermore, they leverage legitimate tools and processes, making their actions difficult to distinguish from benign activity. This “living off the land” technique makes detection significantly more challenging. For example, they might use PowerShell scripts for malicious purposes, blending their actions within the noise of legitimate system administration tasks.
Leveraging Legitimate Tools
A key element of Fin7’s success is their ability to weaponize legitimate tools and techniques. This “living off the land” approach allows them to blend in with normal system activity, making their malicious actions difficult to detect. They often use publicly available tools for reconnaissance, lateral movement, and data exfiltration. This minimizes the need for custom-built malware, reducing the chances of detection based on unique signatures. The skillful use of these tools highlights their technical expertise and adaptability.
Obfuscation Techniques
Fin7 employs a range of obfuscation techniques to hinder analysis of their malware and infrastructure. These techniques include code packing, encryption, and polymorphism. Code packing compresses and encodes the malware, making it harder to reverse engineer. Encryption protects sensitive data and commands within the malware. Polymorphism allows the malware to change its form, making it difficult for signature-based detection systems to identify it consistently. For example, they might use multiple layers of encryption to protect their command-and-control infrastructure, making it incredibly difficult to trace their activities. Their expertise in obfuscation ensures that even if a sample of their malware is detected, the underlying functionality remains obscured.
EDR Capabilities and Limitations
Endpoint Detection and Response (EDR) solutions are the modern cybersecurity knight in shining armor, promising to protect against the ever-evolving threatscape. But are they truly up to the task, especially against sophisticated adversaries like the infamous Fin7 group? Let’s delve into their capabilities and limitations.
EDR systems boast a robust arsenal of features designed to detect and respond to malicious activity on endpoints. Core functionalities include real-time monitoring of system processes and events, advanced threat hunting capabilities, behavioral analysis, and incident response tools. They essentially act as a digital detective, constantly scrutinizing the system for suspicious behavior. However, their effectiveness against advanced persistent threats (APTs) like Fin7 is a complex issue, far from a simple yes or no answer.
EDR Core Functionalities
Modern EDR solutions offer a comprehensive suite of features, including continuous monitoring of system processes and file activity, allowing them to identify deviations from normal behavior. They employ advanced analytics, such as machine learning, to spot subtle anomalies that might indicate a compromise. Furthermore, many EDRs offer threat intelligence integration, enabling them to cross-reference observed events with known malicious indicators, greatly speeding up threat identification. Finally, the ability to perform in-depth investigations, including memory forensics and detailed event reconstruction, provides crucial context for incident response.
Limitations of EDR Against Advanced Threats
Despite their impressive capabilities, EDRs have limitations, particularly when facing highly sophisticated threats like Fin7. Fin7’s techniques often involve living off the land (LOL) attacks, leveraging legitimate system tools to evade detection. These attacks are inherently difficult to detect using signature-based approaches. Furthermore, Fin7 employs techniques like code obfuscation and process injection, making it challenging for EDRs to accurately identify malicious activity. The group’s focus on data exfiltration, often through carefully crafted and stealthy channels, further complicates detection. Finally, the sheer volume of data processed by EDRs can lead to alert fatigue, making it difficult for security teams to prioritize and respond effectively to genuine threats.
EDR Solution Comparison: Effectiveness Against Fin7
Different EDR solutions vary in their effectiveness against Fin7’s tactics. Some excel in behavioral analysis, identifying suspicious patterns of activity, while others might be stronger in memory forensics, uncovering malicious code hidden in memory. The integration of threat intelligence also plays a crucial role, providing crucial context for assessing the risk posed by observed events. A robust solution would ideally combine all these features to offer a comprehensive defense.
Hypothetical EDR Configuration for Fin7 Mitigation
An optimal EDR configuration for mitigating Fin7 attacks should prioritize behavioral analysis and threat intelligence integration. This configuration needs a system that can detect anomalies in process behavior, file access patterns, and network communication, even if the malicious code itself is not known. Memory forensics capabilities are also crucial for uncovering sophisticated techniques like process injection and code obfuscation. Regular updates and tuning of the EDR’s threat detection rules are essential to stay ahead of the evolving tactics of Fin7. Finally, proactive threat hunting should be integrated to proactively search for signs of compromise.
EDR Feature Comparison Across Leading Vendors
| Feature | Vendor A | Vendor B | Vendor C |
|---|---|---|---|
| Behavioral Analysis | Excellent; utilizes machine learning and heuristic analysis | Good; provides basic behavioral monitoring | Fair; primarily relies on signature-based detection |
| Memory Forensics | Good; offers in-depth memory analysis capabilities | Fair; limited memory analysis functionality | Poor; lacks robust memory forensics capabilities |
| Threat Intelligence Integration | Excellent; integrates with multiple threat intelligence feeds | Good; integrates with some threat intelligence platforms | Fair; limited threat intelligence integration |
| Endpoint Visibility | Excellent; provides comprehensive visibility across all endpoints | Good; provides good visibility, but may miss some endpoints | Fair; visibility may be limited depending on the endpoint configuration |
Bypass Techniques Used by Fin7
Source: infinavate.com
Fin7, a notorious cybercrime group, employs sophisticated techniques to bypass endpoint detection and response (EDR) systems. Their methods are constantly evolving, making them a persistent threat. Understanding their tactics is crucial for organizations seeking to enhance their security posture. This section delves into the specific techniques Fin7 uses to evade detection and maintain persistence on compromised systems.
Fin7’s success hinges on its ability to blend into the legitimate system activity, making its malicious actions difficult to distinguish from normal processes. This is achieved through a combination of techniques that exploit vulnerabilities in software and operating systems, combined with the use of readily available tools and utilities.
Evading Signature-Based Detection
Fin7 frequently uses polymorphism and code obfuscation to avoid detection by signature-based anti-malware solutions. Polymorphic malware changes its code structure while maintaining its functionality, rendering traditional signature-based detection ineffective. Obfuscation techniques, on the other hand, make the code difficult to understand and analyze, hindering reverse engineering efforts. For instance, Fin7 might encrypt parts of its malicious code, decrypting it only during runtime, making it challenging for static analysis tools to identify malicious patterns. Furthermore, they often use packers and protectors to compress and encrypt the malicious code, making it harder to analyze and detect.
Exploitation of Living-off-the-Land Binaries (LOLBins)
Fin7 leverages Living-off-the-Land Binaries (LOLBins) extensively. These are legitimate system utilities and tools that are already present on a victim’s system. By abusing the functionality of these legitimate binaries, Fin7 can execute malicious commands without raising immediate suspicion. For example, they might use `PowerShell` to download and execute malicious payloads, or `certutil` to decode and execute encoded malware. The use of LOLBins allows Fin7 to avoid detection by traditional security solutions that focus primarily on identifying malicious files downloaded from external sources. The malicious activity appears as if it’s originating from a trusted source, making detection significantly harder.
Manipulation of System Processes and Memory
Fin7 excels at manipulating system processes and memory to remain undetected. They employ techniques such as process hollowing, where they create a legitimate process, replace its memory with malicious code, and then launch the process, effectively masking the malicious activity. Similarly, they use process injection to inject malicious code into running processes, enabling them to execute their payload within the context of a legitimate process. This makes it challenging for EDR solutions to identify the malicious code as it blends seamlessly within the legitimate process’s memory space. The use of advanced techniques such as API hooking further allows Fin7 to intercept and manipulate system calls, further obscuring their actions.
Process Injection and DLL Hijacking
Process injection is a common technique employed by Fin7. This involves injecting malicious code into the memory space of a running process. This allows the malware to execute within the context of the legitimate process, making it harder to detect. Similarly, DLL hijacking involves replacing a legitimate DLL file with a malicious one. When the legitimate application loads, it unknowingly loads the malicious DLL, executing the malicious code within the application’s context. This technique leverages the trust relationship between the operating system and the legitimate application to execute malicious code without raising immediate suspicion. For example, a legitimate application might expect a specific DLL, and Fin7 could replace that DLL with a malicious one, leading to the execution of their payload.
Effective Mitigation Strategies
Fin7’s sophisticated attacks necessitate a multi-layered defense strategy that goes beyond relying solely on EDR. Strengthening your existing security posture with proactive measures and advanced threat hunting techniques is crucial to effectively neutralize their tactics. This section Artikels key strategies to enhance your defenses and minimize the impact of a Fin7 intrusion.
By implementing robust security controls, enhancing logging and monitoring, and adopting best practices for endpoint security, organizations can significantly improve their resilience against Fin7’s advanced persistent threats (APTs).
Security Controls Enhancing EDR Effectiveness
Several security controls can significantly bolster the effectiveness of your EDR solution against Fin7’s advanced techniques. These controls act as additional layers of defense, creating a more resilient security architecture.
- Network Segmentation: Isolating sensitive systems and data from the rest of the network limits the lateral movement capabilities of attackers, hindering their ability to spread malware and exfiltrate data. Imagine a scenario where the finance department’s servers are isolated from the marketing department’s network. If Fin7 compromises a marketing machine, they’ll have significantly more difficulty accessing the sensitive financial data.
- Application Whitelisting: Only allowing approved applications to run on endpoints prevents unauthorized software execution, a common Fin7 tactic. This effectively blocks malicious tools and scripts before they can execute their payload.
- Data Loss Prevention (DLP): DLP tools monitor and prevent sensitive data from leaving the network, thwarting Fin7’s data exfiltration efforts. This includes monitoring outbound network traffic for suspicious patterns and blocking attempts to transfer sensitive information to unauthorized destinations.
- Privilege Access Management (PAM): Limiting user privileges to only what’s necessary reduces the potential damage from compromised accounts. This makes it harder for attackers to escalate privileges and gain control of critical systems.
Implementing Enhanced Logging and Monitoring
Comprehensive logging and real-time monitoring are critical for early detection of Fin7’s activities. A multi-stage approach is recommended to maximize visibility and detection capabilities.
- Centralized Log Management: Aggregate logs from all endpoints, servers, and network devices into a centralized security information and event management (SIEM) system. This provides a single pane of glass for monitoring security events across the entire infrastructure.
- Real-time Monitoring of Suspicious Activities: Configure alerts for suspicious processes, file creations, registry modifications, and network connections. Focus on unusual activities like connections to known command-and-control (C&C) servers or attempts to access sensitive data outside normal business hours.
- Regular Log Review and Analysis: Establish a regular process for reviewing and analyzing security logs to identify potential threats that may have evaded real-time alerts. This involves using security analytics tools to correlate events and identify patterns indicative of malicious activity.
- Security Information and Event Management (SIEM) Correlation: Utilize the SIEM system’s capabilities to correlate events from different sources to identify patterns indicative of attacks. For example, correlating login attempts from unusual geographic locations with unusual file accesses can pinpoint suspicious activity.
Endpoint Security Best Practices
Implementing these best practices creates a stronger foundation for endpoint security, making it significantly harder for Fin7 to gain a foothold.
- Regular Patching: Keep operating systems, applications, and firmware up-to-date with the latest security patches to mitigate known vulnerabilities.
- Strong Password Policies: Enforce strong, unique passwords and multi-factor authentication (MFA) to protect accounts from brute-force attacks and credential theft.
- Endpoint Detection and Response (EDR) Deployment: Deploy a robust EDR solution that provides comprehensive visibility into endpoint activity and allows for proactive threat hunting.
- User Education and Awareness Training: Educate users about phishing scams, social engineering tactics, and other common attack vectors used by Fin7. Regular training helps employees identify and report suspicious activities.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in the security posture.
Advanced Threat Hunting Techniques within EDR
Proactive threat hunting is crucial for detecting and responding to advanced threats like those employed by Fin7. Leveraging the capabilities of your EDR solution is key.
- Suspicious Process Analysis: Use EDR’s capabilities to investigate suspicious processes, examining their behavior, origins, and network connections. This allows for the identification of malicious processes that may have evaded initial detection.
- Memory Forensics: Analyze memory dumps to detect malicious code that may be residing in memory and not readily visible on the disk. This is particularly useful for detecting malware that utilizes advanced evasion techniques.
- Behavioral Analysis: Use EDR’s behavioral analysis capabilities to identify deviations from normal user and system behavior. This helps detect unusual activities that may indicate malicious activity.
- Threat Intelligence Integration: Integrate threat intelligence feeds into your EDR solution to identify known malicious indicators of compromise (IOCs) and proactively detect and respond to threats.
Advanced Threat Hunting and Response: Fin7 Bypass Edr Solutions
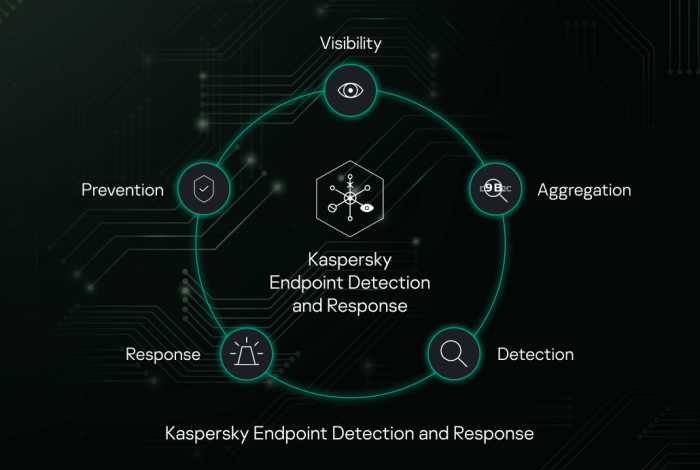
Source: kaspersky-labs.com
Fin7’s sophisticated attacks require a proactive and highly skilled approach to security. A robust threat hunting program, coupled with effective threat intelligence, is crucial for identifying and neutralizing their activity before significant damage occurs. This goes beyond simply reacting to alerts; it’s about actively seeking out malicious behavior within your systems.
A successful Fin7 hunt requires a multi-layered strategy, incorporating advanced analytics, behavioral analysis, and a deep understanding of the group’s tactics, techniques, and procedures (TTPs).
Characteristics of a Robust Threat Hunting Program
A robust threat hunting program dedicated to proactively identifying Fin7 activity should possess several key characteristics. It needs to be data-driven, leveraging logs from various sources like endpoint detection and response (EDR), security information and event management (SIEM), and network devices. This data should be analyzed using both signature-based and anomaly detection techniques. Furthermore, the program needs a dedicated team of skilled security analysts who possess a deep understanding of Fin7’s TTPs and are capable of interpreting complex data sets. Regular training and updates are essential to keep pace with Fin7’s evolving techniques. Finally, the program should incorporate a feedback loop to continuously improve its effectiveness based on past hunts and incident responses. This iterative process is vital for staying ahead of Fin7’s ever-changing methods.
Utilizing Threat Intelligence Feeds for Enhanced Detection
Threat intelligence feeds play a critical role in enhancing threat detection capabilities against Fin7. These feeds provide valuable information about known Fin7 infrastructure, malware samples, command-and-control (C2) servers, and attack techniques. By integrating these feeds into your security tools, you can significantly improve your ability to detect malicious activity. For example, if a threat intelligence feed identifies a new Fin7 C2 server, your security tools can be configured to alert you if any communication attempts are made to that server from within your network. Similarly, knowledge of known Fin7 malware hashes allows for faster identification and isolation of infected systems. Regularly updating and validating these feeds is crucial to ensure they remain relevant and effective. The use of threat intelligence platforms that correlate various data sources, including threat feeds, security logs, and vulnerability data, can significantly enhance detection capabilities.
Investigating and Responding to a Suspected Fin7 Compromise
Investigating a suspected Fin7 compromise requires a methodical and systematic approach. The process begins with identifying potential indicators of compromise (IOCs), such as unusual network traffic, suspicious file activity, or unexpected access attempts. Once potential IOCs are identified, the next step involves collecting evidence, including network logs, system logs, memory dumps, and potentially affected files. This evidence is then analyzed to determine the extent of the compromise, identify the attacker’s actions, and understand the impact of the intrusion. Remediation steps may include isolating affected systems, removing malware, restoring systems from backups, and patching vulnerabilities. Throughout the investigation, maintaining a chain of custody for collected evidence is crucial for legal and forensic purposes. Finally, a post-incident review should be conducted to identify weaknesses in security controls and implement necessary improvements to prevent future compromises.
Incident Response Plan for a Fin7 Intrusion
The following table Artikels a detailed incident response plan specifically addressing a Fin7 intrusion:
| Phase | Actions | Responsible Parties | Timeline |
|---|---|---|---|
| Preparation | Develop and test the incident response plan; establish communication protocols; identify key personnel and their roles; create a secure evidence storage location. | Security Team, IT Management | Ongoing |
| Detection & Analysis | Monitor security systems for suspicious activity; analyze alerts and logs; identify potential IOCs; triage alerts to determine severity. | Security Operations Center (SOC) | Within 24 hours of detection |
| Containment | Isolate affected systems; prevent further spread of malware; block malicious network connections; disable compromised accounts. | SOC, Network Team, System Administrators | Within 4 hours of confirmation |
| Eradication | Remove malware from affected systems; restore systems from backups; patch vulnerabilities; review and update security configurations. | SOC, System Administrators, Forensics Team | Within 72 hours of containment |
| Recovery | Restore data and functionality; test systems; ensure business continuity. | IT Department, Business Units | Within 7 days of eradication |
| Post-Incident Activity | Conduct a post-incident review; document findings; implement corrective actions; update security policies and procedures; improve threat hunting capabilities. | Security Team, IT Management | Within 30 days of incident resolution |
Future Trends and Predictions
The evolution of cyberattacks is a relentless arms race, and Fin7, with its history of sophisticated techniques, will undoubtedly adapt and innovate. Predicting their future actions requires analyzing current trends, understanding the capabilities of emerging technologies, and considering the likely responses from the cybersecurity community. The next few years will likely see Fin7, and similar advanced persistent threat (APT) groups, leverage increasingly sophisticated methods to bypass even the most robust security measures.
Predicting the future actions of a group like Fin7 requires a multi-faceted approach. We need to consider technological advancements, evolving attack vectors, and the ever-changing cybersecurity landscape. This analysis will focus on the convergence of these factors to paint a picture of likely future threats.
Emerging Threats and Techniques
Fin7’s future operations will likely involve a deeper integration of various attack vectors. We can expect to see more sophisticated use of living-off-the-land binaries (LOLBins), leveraging legitimate system tools to avoid detection. Furthermore, the exploitation of zero-day vulnerabilities, combined with advanced social engineering techniques targeting high-value individuals, will become increasingly prevalent. The use of polymorphic malware, which constantly changes its code to evade signature-based detection, will also be a significant factor. Expect to see a rise in attacks that combine multiple techniques, creating a complex attack chain that’s difficult to trace and analyze. For example, initial access might be gained through spear-phishing, followed by lateral movement using compromised credentials and finally data exfiltration via a newly discovered zero-day vulnerability in a widely used application.
Impact of AI and Machine Learning, Fin7 bypass edr solutions
The advancements in AI and machine learning (ML) will impact both sides of the cybersecurity battle. EDR solutions are increasingly leveraging AI for improved threat detection and response. However, Fin7 will likely use AI to enhance their attack techniques, such as developing more sophisticated evasion tactics and generating highly personalized phishing campaigns. This will lead to a continuous arms race, where both attackers and defenders utilize AI to improve their capabilities. For example, Fin7 might use AI to analyze the efficacy of different evasion techniques against various EDR solutions, optimizing their attacks for maximum success. Conversely, EDR vendors will use AI to identify patterns and anomalies indicative of Fin7’s tactics, proactively blocking attacks.
Evolution of the Cybersecurity Landscape
The ongoing threat posed by Fin7 and similar groups will drive significant changes in the cybersecurity landscape. We’ll see a greater emphasis on proactive threat hunting, utilizing advanced analytics and threat intelligence to identify and neutralize threats before they can cause damage. There will also be a greater focus on improving the security posture of organizations, including robust security awareness training for employees, improved vulnerability management processes, and the adoption of more sophisticated security technologies. The collaboration between cybersecurity researchers, security vendors, and government agencies will also become more critical in sharing threat intelligence and developing effective mitigation strategies. We might even see the emergence of specialized AI-powered threat hunting platforms tailored to specific APT groups like Fin7, proactively identifying and responding to their tactics.
Predicted Evolution of Fin7 Tactics (3-Year Projection)
Imagine a visual representation: a three-layered pyramid. The base layer (Year 1) depicts Fin7 primarily relying on established techniques like spear-phishing and LOLBins, but with increased sophistication in evasion techniques. The middle layer (Year 2) shows a shift towards a greater reliance on AI-powered tools for attack planning and execution, alongside the exploitation of zero-day vulnerabilities. The top layer (Year 3) illustrates a fully integrated, AI-driven attack model, utilizing polymorphic malware, advanced anti-forensic techniques, and highly targeted attacks focusing on critical infrastructure. This pyramid visually represents the increasing complexity and sophistication of Fin7’s tactics over the next three years, driven by technological advancements and the ongoing cybersecurity arms race.
Conclusive Thoughts

Source: emsisoft.com
The fight against sophisticated threat actors like Fin7 is an ongoing battle requiring constant vigilance and adaptation. While EDR solutions offer a crucial layer of defense, their limitations necessitate a multi-layered approach encompassing robust security controls, proactive threat hunting, and a well-defined incident response plan. By understanding Fin7’s tactics, leveraging advanced EDR capabilities, and staying ahead of emerging threats, organizations can significantly improve their resilience against these highly skilled attackers. The key takeaway? Proactive defense and a commitment to continuous improvement are paramount in the face of such persistent adversaries.



