Li fi protocol hack – LiFi protocol hack: It sounds like something out of a sci-fi thriller, right? But the reality is, the lightning-fast data transfer potential of LiFi—using light waves instead of radio waves—also introduces unique security vulnerabilities. This isn’t just about slow internet; we’re talking potential data breaches, eavesdropping, and denial-of-service attacks that could cripple entire networks. Understanding these risks is crucial as LiFi technology gains traction.
From the fundamental principles of LiFi and its communication protocols to the various attack vectors and mitigation strategies, we’ll delve into the security landscape of this promising yet precarious technology. We’ll explore different types of LiFi protocol hacks, examining real-world examples and hypothetical scenarios to illustrate the potential consequences. Get ready to shed light on the dark side of LiFi.
LiFi Protocol Overview: Li Fi Protocol Hack
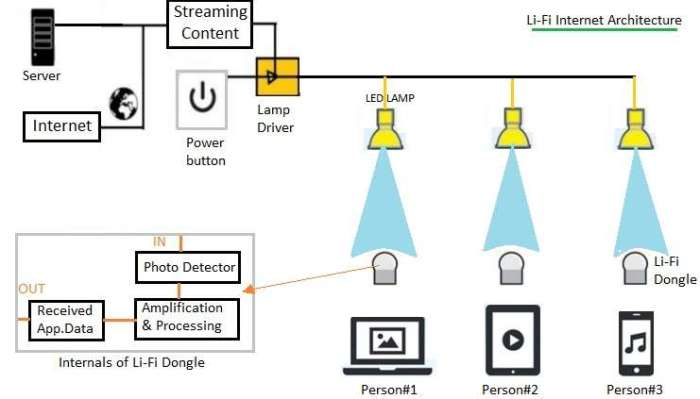
LiFi, short for Light Fidelity, is a wireless communication technology that uses light waves to transmit data. Unlike Wi-Fi, which relies on radio frequencies, LiFi leverages the visible light spectrum, offering a potentially faster, more secure, and more energy-efficient alternative. This technology harnesses the already existing infrastructure of LED lighting systems, transforming them into high-speed data transmitters.
LiFi’s fundamental principle involves modulating the intensity or color of light emitted from LED lights to encode data. This modulated light is then detected by a receiver, typically a photodiode, which converts the light signals back into electrical signals for processing. The communication protocols used in LiFi are based on various modulation schemes, enabling high data rates and robust performance. The underlying technology involves sophisticated signal processing and error correction techniques to ensure reliable data transmission even in challenging environments.
LiFi Advantages and Disadvantages Compared to Wi-Fi
LiFi boasts several advantages over its radio frequency counterpart, Wi-Fi. Its significantly higher bandwidth potential allows for much faster data transfer speeds, making it ideal for applications demanding high data throughput. Furthermore, LiFi offers enhanced security due to the limited range of light and the inability of signals to penetrate walls, mitigating the risk of unauthorized access. The inherent energy efficiency of LEDs also contributes to lower power consumption compared to Wi-Fi routers. However, LiFi suffers from a crucial limitation: its line-of-sight requirement. Unlike Wi-Fi signals that can penetrate walls and obstacles, LiFi requires a direct path between the transmitter and receiver. This restricts its range and necessitates a more deliberate deployment strategy. Additionally, the current lack of widespread adoption and standardization limits its interoperability and accessibility.
LiFi Modulation Techniques
Several modulation techniques are employed in LiFi to encode data onto light signals. On-Off Keying (OOK) is a simple technique where the presence or absence of light represents a binary ‘1’ or ‘0’. However, more sophisticated techniques like Pulse Position Modulation (PPM) and Pulse Amplitude Modulation (PAM) offer improved data rates and robustness against noise. These advanced techniques allow for more efficient encoding of data, maximizing the information carried by each light pulse. For instance, PPM varies the timing of light pulses, while PAM varies the intensity of light pulses to represent different data bits. The choice of modulation technique depends on factors such as the desired data rate, power consumption, and the specific application requirements.
Comparison of LiFi Standards
The standardization of LiFi is still an ongoing process, with various organizations developing different standards. The following table compares some key features of different LiFi standards (note that this is not an exhaustive list and specific details may vary depending on the implementation).
| Standard | Data Rate (Gbps) | Modulation Technique | Range (m) |
|---|---|---|---|
| IEEE 802.15.7 | Up to 1 Gbps (theoretical) | OOK, PPM, PAM | Varies depending on implementation |
| LiFi Consortium Standards | Varies depending on implementation | OOK, PPM, PAM, others | Varies depending on implementation |
| Proprietary Standards | Highly Variable | Highly Variable | Highly Variable |
Vulnerabilities in LiFi Systems
LiFi, while promising faster speeds and enhanced security compared to Wi-Fi, isn’t invulnerable. Several inherent weaknesses and external factors can compromise its security, making it crucial to understand these vulnerabilities to mitigate potential risks. The speed and efficiency of LiFi are counterbalanced by its reliance on visible light, which introduces unique security challenges.
LiFi’s reliance on line-of-sight communication presents a significant vulnerability. Unlike radio waves, light signals cannot penetrate walls or other obstructions. This physical limitation directly impacts security because it creates easily exploitable weaknesses.
Physical Obstructions and Security
The line-of-sight requirement of LiFi makes it susceptible to simple physical attacks. Blocking the light path, even partially, can disrupt communication or even create a denial-of-service (DoS) condition. An attacker could simply place an opaque object, like a book or a strategically placed piece of furniture, between the LiFi transmitter and receiver to interrupt data transmission. This simple act could effectively disable a LiFi network in a targeted area or against a specific device. The ease of this type of attack underscores the importance of careful network planning and robust physical security measures in LiFi deployments.
Susceptibility to Attack Vectors
Several attack vectors can exploit LiFi’s vulnerabilities. Eavesdropping, while more challenging than with radio waves due to the directional nature of light, is still possible using sophisticated optical receivers. Malicious actors could potentially use specialized equipment to intercept the light signals carrying data, compromising the confidentiality of transmitted information. Moreover, man-in-the-middle attacks, where an attacker intercepts and manipulates communication between two parties, are a concern. This could involve intercepting the light signal, altering the data, and then retransmitting it. Finally, jamming attacks, which involve disrupting the light signal with a powerful light source, can effectively render the LiFi network unusable.
Examples of Real-World Vulnerabilities
While widespread, publicly documented large-scale LiFi hacks are currently limited, vulnerabilities have been demonstrated in research settings. For example, studies have shown the susceptibility of certain LiFi systems to eavesdropping attacks using readily available optical sensors and signal processing techniques. Furthermore, the potential for DoS attacks through simple obstruction has been repeatedly highlighted. These research findings emphasize the need for continued development of robust security protocols and countermeasures to address these inherent weaknesses. The lack of widespread, large-scale LiFi deployments also limits the amount of publicly available data on real-world vulnerabilities. However, the identified vulnerabilities in research settings provide a strong indication of potential risks in real-world scenarios.
Types of LiFi Protocol Hacks
LiFi, while offering impressive speeds and security advantages over Wi-Fi, isn’t immune to attack. Understanding the vulnerabilities allows for the development of more robust security measures. This section details various methods malicious actors might exploit to compromise LiFi networks.
LiFi protocol hacks can be broadly categorized into attacks targeting the physical layer, the data link layer, and the network layer, mirroring the vulnerabilities present in traditional networking protocols. These attacks leverage the unique characteristics of LiFi, such as its reliance on light and its susceptibility to interference.
Denial-of-Service Attacks on LiFi Systems
Denial-of-service (DoS) attacks aim to disrupt the availability of a network by overwhelming it with traffic or interfering with its operation. In the context of LiFi, this can manifest in several ways. For example, a powerful light source directed at a LiFi receiver could saturate the sensor, rendering it unusable. Similarly, a carefully crafted signal could jam the communication channel, effectively blocking legitimate transmissions. Imagine a scenario where a rival business floods a competitor’s LiFi network with intense, rapidly fluctuating light signals, preventing employees from accessing crucial data or communication systems. This is analogous to a traditional DoS attack but using light instead of packets. Another approach might involve exploiting the limited bandwidth of a LiFi system. A sustained attack sending a large volume of data could exhaust the system’s capacity, causing a denial of service.
Eavesdropping on LiFi Communications
Eavesdropping, or unauthorized interception of data, is a significant concern for any communication system. In LiFi, this could involve using specialized equipment to capture the light signals transmitted between devices. High-sensitivity photodetectors coupled with signal processing techniques could potentially decode the data stream, revealing sensitive information. The effectiveness of such eavesdropping depends on factors like the distance between the eavesdropper and the communication link, the power of the transmitted signal, and the sophistication of the eavesdropping equipment. Consider a situation where a malicious actor positions a sensitive photodetector near a LiFi-enabled device in a poorly secured office. With the right equipment, they could potentially intercept confidential communications. The complexity of this attack, however, would be significantly higher than simply intercepting radio waves in Wi-Fi networks.
Man-in-the-Middle Attacks on LiFi Networks
A man-in-the-middle (MITM) attack involves intercepting and potentially manipulating communication between two parties without their knowledge. In a LiFi network, this could be achieved by strategically positioning a malicious device between the transmitter and receiver. This device could intercept the light signals, potentially decrypting the data, modifying it, and then forwarding it to the intended recipient. The recipient would be unaware of the interception and manipulation. Imagine a scenario involving a smart home controlled via LiFi. A malicious actor could place a device that intercepts the light signals between the home automation hub and the controlled devices (like lights or appliances). This would allow them to monitor the commands sent and potentially inject their own commands, granting them unauthorized control over the smart home system. The success of such an attack hinges on the ability to intercept and retransmit the light signals without introducing significant distortion or delay, highlighting the importance of robust encryption and authentication protocols in LiFi systems.
Mitigation Strategies and Security Enhancements
Source: medium.com
LiFi, while offering impressive speeds and bandwidth, isn’t immune to the vulnerabilities inherent in any wireless communication system. Robust security measures are crucial to protect LiFi networks from unauthorized access and data breaches. Implementing a multi-layered security approach is key to maximizing the effectiveness of these safeguards. This involves a combination of hardware, software, and procedural enhancements.
Encryption Techniques for LiFi Security
Encryption is the cornerstone of LiFi security, transforming readable data into an unreadable format, rendering it useless to unauthorized parties. Advanced Encryption Standard (AES) with a key length of at least 128 bits is a widely recommended standard for LiFi systems. This ensures that even if an attacker intercepts the data, they cannot decipher it without the correct decryption key. Furthermore, the use of robust key management protocols is paramount to prevent key compromise, which would render the encryption ineffective. For example, implementing a secure key exchange mechanism like Diffie-Hellman can significantly enhance the security of the encryption process.
LiFi Authentication Methods
Authentication verifies the identity of users or devices attempting to access the LiFi network. Several methods exist, each with its strengths and weaknesses. Password-based authentication, while simple, is vulnerable to brute-force attacks and phishing scams. More secure alternatives include multi-factor authentication (MFA), which combines something the user knows (password) with something the user possesses (a physical token or a biometric scan). Public Key Infrastructure (PKI) offers a more robust solution, utilizing digital certificates to authenticate devices and users, providing a higher level of trust and security. The choice of authentication method depends on the specific security requirements and the sensitivity of the data being transmitted.
Best Practices for Securing LiFi Infrastructure
A comprehensive approach to LiFi security necessitates implementing several best practices. Regular software updates are vital to patch known vulnerabilities and address emerging threats. This includes updating firmware on LiFi access points and devices. Strong password policies, mandating complex passwords with regular changes, are crucial in preventing unauthorized access. Network segmentation isolates sensitive data from less critical areas, limiting the impact of a potential breach. Finally, implementing intrusion detection and prevention systems (IDPS) provides real-time monitoring and alerts for suspicious activities, allowing for prompt response and mitigation. Regular security audits and penetration testing are also essential to identify and address vulnerabilities before they can be exploited.
Impact of LiFi Protocol Hacks
A successful LiFi protocol hack can have far-reaching consequences, impacting everything from individual privacy to national security. The potential for disruption and damage is significant, especially considering the increasing reliance on LiFi technology in various sectors. Understanding these potential impacts is crucial for developing robust security measures and mitigating risks.
The consequences of a compromised LiFi network extend beyond simple data breaches. Successful attacks can lead to a cascade of negative effects, impacting individuals, businesses, and even governments. The severity of the impact depends on the nature of the compromised data and the scale of the breach.
Data Breaches and Their Impact
A successful LiFi hack can result in the unauthorized access and theft of sensitive data. This could include personal information like names, addresses, and financial details, as well as confidential business information, intellectual property, and government secrets. Imagine a hospital network compromised: patient records, including medical histories and sensitive diagnoses, could fall into the wrong hands, leading to identity theft, blackmail, or even endangerment of patient lives. Similarly, a breach in a financial institution using LiFi could result in massive financial losses and erode public trust. The impact extends beyond the immediate victims; the reputation of the organization and public confidence in LiFi technology itself could be severely damaged.
Privacy and Data Security Implications
LiFi systems, while offering advantages in terms of speed and security compared to Wi-Fi, are not immune to attacks. A breach compromises the privacy of individuals and organizations relying on these systems. The unauthorized access to private communications, personal data, and sensitive information can have severe repercussions, leading to identity theft, financial fraud, and reputational damage. For example, eavesdropping on confidential business meetings transmitted via a compromised LiFi network could result in the loss of competitive advantage and significant financial losses. The psychological impact on individuals whose privacy has been violated should also not be underestimated.
Economic and Social Consequences
The economic impact of a large-scale LiFi protocol hack can be devastating. Businesses could face significant financial losses due to data breaches, legal repercussions, and reputational damage. The cost of remediation, including investigating the breach, notifying affected individuals, and implementing enhanced security measures, can be substantial. Furthermore, the disruption of essential services relying on LiFi networks could have widespread social consequences, impacting critical infrastructure, healthcare, and emergency response systems. For instance, a successful cyberattack targeting a smart city’s LiFi-based traffic management system could cause significant traffic congestion and economic disruption. The resulting loss of public trust in LiFi technology could also hinder its adoption and widespread implementation.
Future Research Directions
Source: rfwireless-world.com
LiFi, while promising, faces significant security hurdles. Current research focuses primarily on known vulnerabilities, but the rapid evolution of both LiFi technology and attack methods necessitates a proactive, forward-looking approach. Future research must anticipate emerging threats and develop robust, adaptable security solutions to ensure LiFi’s widespread adoption. This requires a multi-faceted strategy involving both theoretical advancements and practical implementations.
The development of more secure and resilient LiFi systems requires a concerted effort from researchers, developers, and standardization bodies. Addressing the identified open research challenges is crucial for realizing the full potential of LiFi technology while mitigating the risks associated with its deployment in various applications, from smart homes to critical infrastructure.
Advanced Encryption Techniques for LiFi
Current encryption methods, while effective against many attacks, may not be sufficient to withstand the sophistication of future threats. Research into post-quantum cryptography, lightweight cryptography suitable for resource-constrained LiFi devices, and advanced key management techniques is essential. For example, exploring the integration of lattice-based cryptography, known for its resistance to attacks from quantum computers, could significantly enhance LiFi security. This would ensure that LiFi systems remain secure even as quantum computing technology advances. Another area of focus should be on developing efficient key exchange protocols that minimize the overhead on the already bandwidth-constrained LiFi systems.
AI-Driven Security Solutions for LiFi
Artificial intelligence (AI) and machine learning (ML) offer powerful tools for detecting and mitigating LiFi-specific attacks. Research should focus on developing AI-powered intrusion detection systems that can learn to identify anomalous behavior in LiFi networks, such as unusual data patterns or access attempts. For instance, an AI system could be trained on a large dataset of normal LiFi traffic patterns, allowing it to identify deviations that might indicate a malicious attack. Real-time anomaly detection, coupled with automated response mechanisms, could significantly improve the resilience of LiFi systems.
Secure LiFi Network Architectures
The architecture of LiFi networks plays a crucial role in their overall security. Research into novel network topologies, protocols, and security mechanisms is needed. This includes exploring secure routing protocols specifically designed for LiFi networks, as well as investigating the use of blockchain technology for secure data management and access control. The integration of blockchain could provide an immutable record of transactions and access permissions, enhancing the transparency and accountability of LiFi networks. Further investigation into the implementation of secure multi-party computation within the LiFi network architecture would also contribute to enhancing privacy and security.
Research Topics for Enhancing LiFi Security and Robustness, Li fi protocol hack
The following research topics are crucial for enhancing the security and robustness of LiFi technology:
- Development of lightweight and efficient cryptographic algorithms tailored for the resource constraints of LiFi devices.
- Design and implementation of secure key management protocols for LiFi networks.
- Development of advanced intrusion detection and prevention systems using AI and machine learning.
- Investigation of secure network architectures and protocols optimized for LiFi.
- Research into the application of blockchain technology for secure data management in LiFi.
- Analysis of the security implications of LiFi integration with other communication technologies (e.g., Wi-Fi, 5G).
- Development of standardized security protocols and frameworks for LiFi.
- Investigation of the use of physical layer security techniques to enhance LiFi security.
Ultimate Conclusion
Source: wustl.edu
LiFi’s potential is undeniable, offering speeds far exceeding Wi-Fi. However, its inherent security vulnerabilities can’t be ignored. While the technology is still relatively new, proactive security measures are vital. By understanding the potential threats and implementing robust security protocols, we can harness LiFi’s speed and efficiency while mitigating the risks. The future of LiFi depends on a strong commitment to security—failing to address these vulnerabilities could dim the bright future of this technology.



