Encryption algorithms used in malware: It’s a digital cat-and-mouse game, a constant arms race between cybercriminals and security experts. Malware developers constantly seek new ways to encrypt their malicious code, making it harder to detect and analyze. This deep dive explores the most common encryption methods used in malware, their evolution, and the strategies employed to combat them. We’ll unravel the mysteries behind algorithms like AES and RSA, examining their strengths, weaknesses, and how they’re deployed in real-world attacks – from ransomware to botnets.
We’ll trace the history of encryption in malware, showcasing how attackers adapt their techniques to stay ahead of the curve. Think of it as a thrilling tech thriller, where the stakes are high, the technology is cutting-edge, and the consequences of failure are severe. Get ready to uncover the secrets behind the code that threatens our digital world.
Prevalence of Encryption Algorithms in Malware: Encryption Algorithms Used In Malware
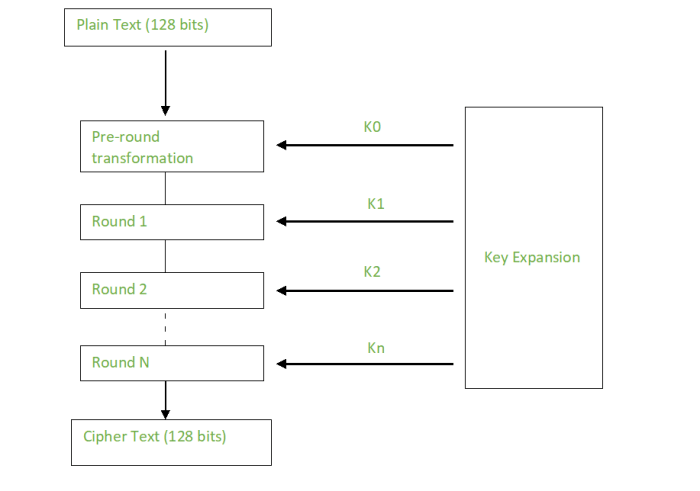
Source: appsealing.com
Malware authors rely heavily on encryption to hide their malicious activities and evade detection. The choice of encryption algorithm is a crucial factor in determining the effectiveness and longevity of a malware campaign. Understanding the prevalent algorithms helps security researchers anticipate and counter emerging threats.
The selection of an encryption algorithm by malware developers is a complex interplay of factors including the algorithm’s strength, speed, availability of libraries, and the perceived difficulty in decryption. Stronger algorithms offer better protection, but they might be slower, demanding more processing power and potentially raising suspicion. Conversely, weaker algorithms are faster but easier to crack, making them a less desirable choice for long-term operations.
Top Five Encryption Algorithms in Malware
Identifying the precise frequency of algorithm use across all malware families is a challenging task due to the constantly evolving malware landscape and the secretive nature of its development. However, based on observations from various cybersecurity reports and threat intelligence feeds over the past five years, we can highlight some of the most commonly encountered algorithms.
| Algorithm Name | Year | Malware Family (Examples) | Frequency (Relative) |
|---|---|---|---|
| AES (Advanced Encryption Standard) | 2019-2024 | Emotet, Trickbot, Ryuk | High |
| RSA (Rivest-Shamir-Adleman) | 2019-2024 | Various banking trojans, ransomware | High |
| RC4 (Rivest Cipher 4) | 2019-2024 | Older malware variants, some botnets | Medium (declining) |
| ChaCha20 | 2021-2024 | Some ransomware, file encryptors | Medium (increasing) |
| Salsa20 | 2021-2024 | Similar to ChaCha20 | Medium (increasing) |
Note: “Frequency (Relative)” is a qualitative assessment based on observed prevalence in threat intelligence reports and not a precise quantitative measure.
Reasons for Algorithm Popularity, Encryption algorithms used in malware
The popularity of these algorithms stems from a combination of factors. AES, for instance, is widely adopted due to its robust security, widespread availability of efficient implementations, and acceptance as a standard by various governmental and industrial bodies. RSA’s use is often tied to its role in public-key cryptography, enabling secure communication and key exchange. The prevalence of RC4, despite its known weaknesses, highlights the persistent presence of older, less secure malware.
The increasing adoption of ChaCha20 and Salsa20 reflects a shift towards algorithms known for their speed and performance on resource-constrained devices, a factor that might be relevant for malware operating on low-powered IoT devices or older systems.
Strengths and Weaknesses of Algorithms in Malware
AES offers strong encryption, making it difficult to crack without significant computational resources. However, its implementation can be computationally intensive, potentially slowing down malware operations. RSA, while secure for key exchange and digital signatures, is computationally expensive for encrypting large amounts of data, often limiting its use in bulk encryption tasks within malware. RC4’s known vulnerabilities make it a risky choice, although its simplicity and speed once made it attractive to malware authors.
ChaCha20 and Salsa20 offer a balance between security and speed, making them suitable for scenarios where performance is critical. However, their relative novelty means their long-term security is still under scrutiny, and extensive cryptanalysis is ongoing.
Evolution of Encryption Techniques in Malware
Malware’s use of encryption has dramatically evolved, mirroring advancements in both cryptography and decryption techniques. Early malware relied on simple, easily broken ciphers, while modern iterations utilize sophisticated methods designed to withstand even advanced analysis. This arms race between malware authors and security researchers has driven innovation on both sides.
The historical progression of encryption in malware shows a clear trend towards stronger, more resilient techniques. Initially, simple substitution ciphers or basic XOR encryption were common. These were relatively easy to crack with frequency analysis or brute-force attacks. However, as decryption tools improved, malware authors began incorporating more robust algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman). The shift reflects a constant effort to stay ahead of security measures.
Adaptation to Decryption Advancements
Malware authors continuously adapt their encryption strategies in response to the development of more powerful decryption tools and techniques. The use of longer keys, multiple layers of encryption, and the incorporation of dynamic key generation are all examples of this evolution. For instance, early versions of ransomware might have used a static encryption key, making decryption relatively straightforward if the key was discovered. Modern ransomware, however, often employs techniques like key derivation functions (KDFs) to generate unique keys for each victim, significantly increasing the difficulty of decryption. Furthermore, the integration of self-modifying code allows the malware to alter its encryption routines during execution, making static analysis and reverse engineering significantly more challenging. This constant adaptation ensures that the malware remains resilient against commonly used decryption methods.
Obfuscation and Encryption Synergies
Obfuscation techniques, which aim to make the malware’s code harder to understand, are frequently combined with encryption to create a formidable defense against analysis. This combination creates a layered security approach. Encryption protects the malware’s core functionality, while obfuscation hinders the process of even reaching the encrypted parts. For example, a malware sample might use code packing to compress and encrypt its payload, making it difficult to extract and analyze the underlying code. Further obfuscation might involve using polymorphism – the ability to change its own code while maintaining functionality – to evade signature-based detection. The combined effect of these techniques makes it significantly more difficult to understand the malware’s behavior and decrypt its payload. Imagine a scenario where the malware first uses a packer to shrink and encrypt its core code. This packed code is then further obfuscated by inserting meaningless instructions and altering control flow, making it extremely challenging to reverse engineer the original functionality. This layered approach greatly increases the resilience of the malware.
Specific Algorithm Analysis
AES, or the Advanced Encryption Standard, is a workhorse in the world of cryptography, and unsurprisingly, it’s a favorite among malware authors. Its robust security and relatively fast performance make it a tempting target for those looking to encrypt sensitive data for nefarious purposes. However, understanding how malware implements and sometimes modifies AES is crucial for effective detection and mitigation.
AES implementation in malware varies depending on the malware’s goals and the sophistication of its creators. Simpler malware might use readily available AES libraries, while more advanced threats might incorporate custom implementations or modifications to evade detection by antivirus software. This range in implementation reflects the ever-evolving arms race between malware developers and security researchers.
AES Implementation Variations in Malware
Malware authors often employ several tactics to integrate AES into their malicious code. A common approach involves using readily available, open-source AES libraries. This offers a convenient and efficient way to implement strong encryption without the need for extensive coding. However, this approach also makes the malware easier to identify and analyze, as the use of standard libraries leaves a distinct digital fingerprint. More sophisticated malware may utilize custom-coded AES implementations, which are designed to obfuscate the encryption process and hinder reverse engineering efforts. These custom implementations might involve alterations to the standard AES algorithm or the incorporation of additional layers of encryption or obfuscation. Furthermore, some malware might integrate AES with other cryptographic techniques, creating a layered approach to data protection that makes decryption significantly more challenging.
AES Modifications for Evasion
To bypass security software, malware authors frequently tweak the standard AES implementation. One common tactic is to modify the key schedule, the algorithm that generates the round keys used in the encryption process. Altering the key schedule can make it much harder for security tools to decrypt the data, even if they can identify the underlying AES algorithm. Another method is to combine AES with other encryption algorithms or hashing functions to create a more complex encryption scheme. This layered approach increases the difficulty of decryption and makes it more time-consuming for analysts to crack. Furthermore, some malware incorporates code obfuscation techniques alongside the AES implementation, making the code itself harder to understand and analyze. This can be achieved through techniques like packing, encryption of code sections, or the use of control flow obfuscation.
Hypothetical Ransomware Attack Using AES
Imagine a ransomware attack targeting a small business. The malware, upon execution, first identifies sensitive files, such as financial records, customer databases, and design documents. It then uses a robust AES implementation, possibly a custom one with a modified key schedule, to encrypt these files. The encryption process might involve splitting the files into smaller chunks and encrypting each chunk independently using a unique key derived from a master key. This master key is then encrypted using a public key obtained from a command-and-control server controlled by the attackers. The encrypted files are marked with a unique extension, indicating their encrypted state, and a ransom note is displayed, demanding a payment in cryptocurrency for the decryption key. The attackers hold the private key needed to decrypt the master key, effectively controlling access to the victim’s data. The victim, facing potential financial and reputational damage, is forced to consider paying the ransom to regain access to their crucial data. The complexity of the AES implementation, coupled with the layered encryption approach, significantly increases the difficulty of decryption without the attacker’s assistance, thereby maximizing the effectiveness of the attack.
Specific Algorithm Analysis
RSA, a cornerstone of modern cryptography, finds its way into the murky world of malware, often playing a crucial role in establishing secure, albeit malicious, communication channels. Its strength lies in its mathematical complexity, making it a seemingly impenetrable fortress for sensitive data. However, the implementation and key management within malware contexts often introduce vulnerabilities that can be exploited.
RSA’s application in malware primarily revolves around command-and-control (C&C) communication. Encrypted communication prevents casual observation of malicious instructions, updates, and exfiltrated data. This obfuscation makes it harder for security researchers and analysts to understand the malware’s activities and hinders effective response. The use of RSA encryption allows the malware to maintain a persistent connection to its C&C server, receiving commands and sending stolen information discreetly. The strength of the encryption directly impacts the difficulty of disrupting these communication channels.
RSA Encryption in Malware C&C Communication
Malware authors leverage RSA’s asymmetric nature to establish secure communication channels with their C&C servers. The server holds the public key, which is readily available to the malware, enabling encryption of data sent from the infected machine. The server then uses its corresponding private key to decrypt this data, retrieving the information sent by the malware. This setup ensures that only the intended recipient can decrypt the communication, even if it’s intercepted. This process allows for the secure transfer of sensitive data, including stolen credentials, configuration settings, and commands for further malicious actions. The effectiveness of this method hinges on the strength of the RSA key pair and the security of the private key.
Challenges in Breaking RSA Encryption in Malware
Breaking RSA encryption deployed in malware is a complex task, influenced significantly by the key size and the implementation details. Larger key sizes (e.g., 2048 bits or higher) drastically increase the computational power needed to crack the encryption. However, malware often utilizes smaller key sizes due to performance considerations, making them potentially vulnerable to brute-force attacks or advanced factoring algorithms. Furthermore, poor implementation practices within the malware itself can create weaknesses that can be exploited, even with larger keys. For instance, weak random number generators used in key generation can introduce predictable patterns, making the process easier to reverse. Additionally, vulnerabilities in the underlying cryptographic libraries used by the malware can provide entry points for attackers. For example, a known vulnerability in the library might allow bypassing the encryption process altogether. Real-world examples of this include instances where older, less secure versions of OpenSSL were used in malware, enabling researchers to reverse-engineer the encryption.
RSA Key Generation and Usage in Malware
The process of RSA key generation and usage within a malware context involves several steps, each contributing to the overall security (or lack thereof) of the communication channel.
The steps are crucial to understand the malware’s operation and its potential vulnerabilities. A weak implementation at any stage can compromise the entire security mechanism.
- Key Generation: The malware generates a pair of RSA keys – a public key and a private key – using a suitable algorithm. The strength of the key depends on the bit size; larger key sizes are more resistant to attacks, but also slower.
- Public Key Distribution: The malware’s public key is typically embedded within the malware code or obtained from a C&C server. This key is used to encrypt communication sent from the infected machine.
- Encryption: Before sending data to the C&C server, the malware encrypts the data using the server’s public key. This ensures only the server, possessing the corresponding private key, can decrypt it.
- Transmission: The encrypted data is transmitted to the C&C server over a network connection.
- Decryption: The C&C server uses its private key to decrypt the received data and process the information.
- Response: The server may generate a response, encrypt it using the malware’s public key, and send it back to the infected machine. This enables a two-way encrypted communication channel.
Detection and Mitigation Strategies
Unmasking encrypted malware requires a multi-layered approach, combining network monitoring with advanced analysis techniques. Effective detection hinges on identifying suspicious patterns and behaviors, even when the underlying data is obscured by encryption. Successful mitigation, on the other hand, relies on a combination of prevention, detection, and response strategies to minimize the impact of a successful infection.
Identifying encrypted malware traffic within a network environment often involves analyzing network flows for anomalies. This includes looking for unusual volumes of encrypted traffic, unexpected communication patterns with known malicious IP addresses or domains, and the use of unusual ports. Advanced techniques such as deep packet inspection can also be employed, although these methods are computationally expensive and may require specialized hardware.
Network Traffic Analysis for Encrypted Malware Detection
Network traffic analysis plays a crucial role in identifying malicious activity. Analyzing encrypted traffic requires looking beyond the encryption itself. This involves examining metadata such as the source and destination IP addresses, ports used, packet sizes, and timestamps. Deviations from established baselines can indicate malicious activity. For example, a sudden surge in encrypted traffic to a previously unknown server might warrant investigation. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can be configured to alert on such anomalies. Furthermore, employing machine learning algorithms trained on known malicious traffic patterns can significantly improve the accuracy of detection. These algorithms can identify subtle patterns that might be missed by traditional rule-based systems.
Malware Decryption Techniques
Decrypting malware samples is a complex process with varying degrees of success. Methods range from exploiting known vulnerabilities in the encryption algorithms used by the malware to brute-forcing encryption keys. The effectiveness of each approach depends on factors such as the strength of the encryption algorithm, the length of the encryption key, and the availability of resources for decryption. For example, attempting to decrypt malware using a weak cipher like RC4 is significantly easier than tackling AES-256 with a strong key. Specialized decryption tools and techniques, such as those developed by security researchers, can provide some assistance, but success is not guaranteed.
Sandboxing for Encrypted Malware Analysis
Sandboxing provides a safe and isolated environment for analyzing malware behavior without risking infection of the host system. When dealing with encrypted malware, sandboxing allows researchers to observe the malware’s actions and network communications in a controlled setting. By monitoring the sandboxed environment’s network traffic, file system access, and registry modifications, analysts can gain insights into the malware’s functionality, even if the data itself remains encrypted. This can help to identify the malware’s command-and-control servers, its infection vectors, and its overall objectives. Advanced sandboxing techniques can even employ dynamic instrumentation to intercept and analyze encrypted communications in real-time, providing valuable information about the malware’s behavior and communication patterns. For example, a sandbox might reveal that the malware establishes connections to specific domains known for hosting malicious infrastructure, even if the content of those communications remains encrypted.
Future Trends in Malware Encryption
Source: cisco.com
The landscape of malware encryption is constantly evolving, driven by advancements in both cryptography and the sophistication of cybercriminals. Understanding these future trends is crucial for developing effective countermeasures and safeguarding digital assets. The increasing power of computing, particularly the rise of quantum computing, presents both challenges and opportunities in the realm of malware encryption. This section explores the potential impact of these technological shifts on the security of existing and future malware encryption techniques.
The advent of quantum computing poses a significant threat to many widely used encryption algorithms. Current public-key cryptography, which relies on the computational difficulty of factoring large numbers or solving discrete logarithm problems, is vulnerable to attacks from sufficiently powerful quantum computers. Algorithms like RSA and ECC, commonly used in malware for encrypting communication channels or payloads, could become easily breakable. This necessitates a shift towards quantum-resistant cryptography, which is already underway.
Quantum Computing’s Impact on Malware Encryption
Quantum computers, with their ability to perform calculations far exceeding the capabilities of classical computers, threaten to render many current encryption algorithms obsolete. For instance, Shor’s algorithm, a quantum algorithm, can efficiently factor large numbers, directly undermining the security of RSA encryption, a mainstay in many malware operations. This potential vulnerability necessitates a proactive approach to developing and deploying quantum-resistant cryptographic algorithms to prevent widespread decryption of malware’s encrypted components. The timeline for the widespread availability of quantum computers capable of breaking current encryption remains a subject of debate, but the potential threat is undeniable and necessitates immediate attention. This could lead to a surge in the use of more robust, quantum-resistant algorithms in future malware, potentially creating a new arms race between malware developers and security researchers.
Emerging Encryption Techniques in Malware
Beyond the quantum threat, the evolution of malware encryption also involves the exploration and adoption of new cryptographic techniques. Homomorphic encryption, for example, allows computations to be performed on encrypted data without decryption, potentially enabling more sophisticated and stealthy malware operations. This could allow malware to execute commands on encrypted data, making it harder to detect malicious activity. Post-quantum cryptography (PQC) algorithms, designed to withstand attacks from quantum computers, are also likely to see increased adoption in malware, offering a longer-term solution to the quantum threat. The integration of these techniques could significantly increase the difficulty of malware analysis and detection.
Comparative Security of Encryption Algorithms Against Future Threats
| Algorithm | Current Security | Vulnerability to Quantum Computing | Post-Quantum Alternatives |
|---|---|---|---|
| RSA | Widely used, but security depends on key size | Highly vulnerable to Shor’s algorithm | CRYSTALS-Kyber, NTRU |
| ECC (Elliptic Curve Cryptography) | Generally considered strong, more efficient than RSA for same security level | Vulnerable to Shor’s algorithm (discrete logarithm problem) | SIKE, Classic McEliece |
| AES (Advanced Encryption Standard) | Widely used symmetric encryption algorithm, considered secure for now | Relatively unaffected by quantum computing (requires brute force attacks, which can be sped up by quantum computers, but not fundamentally broken) | Continued use with increased key sizes, or combined with PQC for key exchange |
| Homomorphic Encryption | Emerging technology, security depends on specific scheme | Security properties depend on underlying cryptographic primitives; some schemes are vulnerable, some are not | Research into quantum-resistant homomorphic encryption schemes is ongoing. |
Ultimate Conclusion
Source: okta.com
The battle against encrypted malware is far from over. As technology evolves, so too will the methods used to conceal malicious code. Understanding the algorithms, their vulnerabilities, and the latest detection techniques is crucial for staying ahead of the curve. The future of cybersecurity hinges on our ability to adapt and innovate, outsmarting the ever-evolving tactics of malware developers. So, buckle up, the fight continues.



