PHP vulnerability exploited – that’s the chilling reality facing many websites. From sneaky SQL injections to devastating cross-site scripting attacks, insecure PHP code opens the digital floodgates to malicious actors. This isn’t just about tech jargon; it’s about real-world consequences: data breaches, financial losses, and reputational damage. We’ll dissect the most common vulnerabilities, explore the attack methods, and arm you with the knowledge to defend your digital fortress.
This deep dive will cover the various types of PHP vulnerabilities, detailing how they’re exploited and the devastating impact they can have. We’ll examine real-world examples, explore prevention strategies, and equip you with the tools to identify and mitigate these threats. Think of this as your ultimate survival guide in the wild west of web security.
Types of PHP Vulnerabilities Exploited
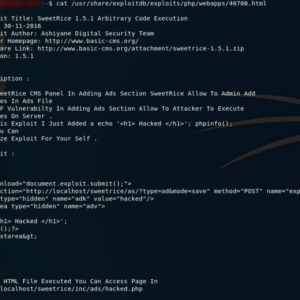
Source: phpscriptsonline.com
PHP, despite its maturity and widespread use, remains susceptible to various vulnerabilities that attackers actively exploit. Understanding these vulnerabilities is crucial for developers to build secure applications and for security professionals to effectively defend against attacks. This section delves into some of the most common PHP vulnerabilities and their exploitation mechanisms.
SQL Injection
SQL injection is a classic web vulnerability that allows attackers to inject malicious SQL code into database queries, potentially leading to data breaches, data manipulation, or even complete server compromise. It occurs when user-supplied data is directly incorporated into SQL queries without proper sanitization or parameterization. Attackers craft malicious input to alter the intended query’s logic, gaining unauthorized access to sensitive information. For example, an attacker might inject a statement like `’ OR ‘1’=’1` into a login form field, bypassing authentication checks.
| Vulnerability Type | Description | Exploitation Method | Impact |
|---|---|---|---|
| SQL Injection | Malicious SQL code injected into database queries. | Crafting malicious input to manipulate database queries; often targeting login forms or search functionalities. | Data breaches, data modification, denial of service, complete server compromise. |
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) vulnerabilities allow attackers to inject client-side scripts into web pages viewed by other users. These scripts can steal cookies, session IDs, or other sensitive information, potentially leading to account hijacking or phishing attacks. There are three main types: reflected, stored, and DOM-based XSS. Reflected XSS occurs when malicious script is reflected back to the user from the server, stored XSS involves injecting scripts into a database that are then served to other users, and DOM-based XSS targets the Document Object Model directly within the user’s browser. Imagine a scenario where a website doesn’t sanitize user input in a comment field; an attacker could inject a JavaScript code that redirects users to a malicious website.
| Vulnerability Type | Description | Exploitation Method | Impact |
|---|---|---|---|
| Cross-Site Scripting (XSS) | Injection of client-side scripts into web pages. | Injecting malicious scripts into input fields (reflected, stored), manipulating the DOM (DOM-based). | Session hijacking, cookie theft, phishing attacks, malware distribution. |
Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) exploits the trust a website has in a user’s browser. Attackers trick users into performing unwanted actions on a trusted site. This is often achieved by embedding malicious links or forms within legitimate-looking websites. For example, an attacker could create a hidden form that submits a request to change a user’s password on a banking website. If the user visits the attacker’s website without realizing the embedded form, the password change could be executed without their knowledge or consent. Effective CSRF protection usually involves using tokens and verifying the origin of requests.
| Vulnerability Type | Description | Exploitation Method | Impact |
|---|---|---|---|
| Cross-Site Request Forgery (CSRF) | Tricking users into performing unwanted actions on a trusted site. | Embedding malicious links or forms within other websites; exploiting the browser’s trust in the target website. | Unauthorized actions, account compromise, data manipulation. |
File Inclusion Vulnerabilities
File inclusion vulnerabilities allow attackers to include arbitrary files on the server, potentially executing malicious code or accessing sensitive data. This often arises from poorly implemented file inclusion functionalities, where user input is used to determine which file to include without proper validation. For instance, if a script includes a file based on a user-supplied parameter, an attacker might be able to include a file containing malicious PHP code, effectively executing it on the server.
| Vulnerability Type | Description | Exploitation Method | Impact |
|---|---|---|---|
| File Inclusion | Including arbitrary files on the server, potentially executing malicious code. | Manipulating input parameters to include malicious files; often targeting file inclusion functionalities. | Code execution, data access, server compromise. |
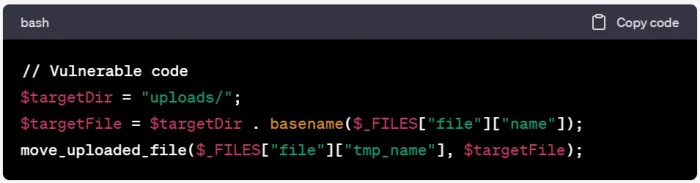
Exploitation Techniques and Vectors

Source: slideplayer.com
PHP vulnerabilities, while seemingly technical, offer attackers surprisingly straightforward pathways into your systems. Understanding these attack vectors is crucial for building robust security measures. This section details common methods used to exploit weaknesses and how attackers leverage them for malicious purposes. We’ll explore the initial access techniques, privilege escalation methods, and provide illustrative examples of malicious code.
Exploiting PHP vulnerabilities often hinges on leveraging existing functionalities for nefarious purposes. Attackers don’t typically reinvent the wheel; instead, they exploit pre-existing features, misconfigurations, or coding flaws to gain access and wreak havoc. The techniques used are often a combination of various methods, chaining vulnerabilities to achieve maximum impact.
SQL Injection
SQL injection remains a prevalent threat. Attackers inject malicious SQL code into input fields, manipulating database queries to gain unauthorized access to data or alter database structures. This can range from simple data exfiltration to complete server compromise.
- Example 1: A vulnerable login form might allow an attacker to inject SQL like
' OR '1'='1. This bypasses authentication checks, granting access without a valid username and password. - Example 2: More sophisticated attacks might involve using UNION queries to retrieve data from other tables or even execute arbitrary system commands if the database server has insufficient permissions.
Cross-Site Scripting (XSS)
XSS vulnerabilities allow attackers to inject client-side scripts into web pages viewed by other users. These scripts can steal cookies, redirect users to malicious websites, or even deface the website itself. The severity depends on the context where the vulnerability exists.
- Example 1: A vulnerable comment section might allow an attacker to inject JavaScript code that steals user cookies. This code, embedded within a seemingly harmless comment, could be executed when another user views the page.
- Example 2: Reflected XSS attacks occur when the attacker’s malicious script is immediately reflected back to the user’s browser, often through a search query parameter.
Remote File Inclusion (RFI)
RFI vulnerabilities allow attackers to include arbitrary files from remote servers. This can lead to the execution of malicious code, often through a cleverly crafted URL. This is particularly dangerous if the included file contains PHP code.
- Example: An application with a poorly sanitized include statement, like
include($_GET['page']);, allows an attacker to specify a remote URL containing malicious PHP code. This code will then be executed on the server.
Hypothetical Attack Scenario: Exploiting a SQL Injection Vulnerability
Imagine a poorly secured e-commerce website with a vulnerable search functionality. The search query is directly incorporated into an SQL query without proper sanitization. An attacker could craft a search query like ' UNION SELECT password FROM users --. This query, instead of searching for products, retrieves all user passwords from the ‘users’ table. The attacker successfully bypasses security mechanisms and gains access to sensitive user information, potentially leading to further compromises and identity theft. This scenario mirrors real-world attacks against poorly secured databases, where attackers use simple SQL injection techniques to extract valuable data. The impact can range from financial loss to reputational damage for the affected business.
Impact and Consequences of Exploits
Exploiting PHP vulnerabilities can have far-reaching and devastating consequences, impacting individuals, organizations, and even entire industries. The severity of the impact depends on the type of vulnerability exploited, the sensitivity of the compromised data, and the effectiveness of the organization’s security measures. Ignoring these risks can lead to significant financial losses, reputational damage, and legal repercussions.
The potential damage caused by successful exploits is multifaceted and can severely disrupt operations. We’ll explore the various ramifications, categorized for clarity and understanding.
Financial Consequences
Successful exploitation of PHP vulnerabilities can lead to substantial financial losses. Data breaches, for example, can result in hefty fines for non-compliance with regulations like GDPR. The costs associated with investigating the breach, notifying affected individuals, and implementing remediation measures can also be significant. Furthermore, loss of customer trust and subsequent decline in sales can inflict long-term financial damage. Consider the case of a major e-commerce site experiencing a credit card data breach; the financial penalties, legal fees, and loss of customer confidence could easily run into millions of dollars. The cost of restoring data and systems after a successful ransomware attack, often involving a significant ransom payment, is another major financial burden.
Reputational Damage
A security breach, regardless of its scale, can severely tarnish an organization’s reputation. News of a data breach or website defacement spreads rapidly, impacting public perception and eroding customer trust. This loss of trust can lead to decreased sales, difficulty attracting investors, and damage to the brand’s overall image. For instance, a social media platform suffering a data leak exposing user information would likely face significant reputational damage, potentially losing millions of users and incurring long-term damage to its brand image. The impact extends beyond the immediate crisis; recovering trust and rebuilding a positive reputation requires substantial investment and time.
Legal Consequences
Organizations failing to adequately protect user data can face severe legal consequences. Data protection laws, such as GDPR and CCPA, impose strict regulations on data handling and security. Non-compliance can result in hefty fines and legal actions. Furthermore, class-action lawsuits from affected individuals can add to the legal and financial burdens. Consider the scenario of a healthcare provider experiencing a data breach exposing patient medical records; the legal ramifications could involve significant fines, lawsuits from affected patients, and reputational damage that would severely impact the organization’s future.
Impact on Stakeholders
The consequences of PHP vulnerability exploits affect various stakeholders. Users might experience identity theft, financial loss, or privacy violations. Developers bear the responsibility for creating secure code and mitigating vulnerabilities. Organizations face financial losses, reputational damage, and legal liabilities. The impact ripples outwards, affecting investors, partners, and the broader public. For example, a compromised online banking system could lead to financial losses for users, reputational damage for the bank, and potential legal repercussions for the developers and the organization. This highlights the interconnectedness of the consequences and the importance of robust security practices.
Mitigation and Prevention Strategies
Securing your PHP applications against vulnerabilities isn’t just about patching after an attack; it’s about building security into the very foundation of your code. Proactive measures are crucial, significantly reducing the risk of exploitation and minimizing the impact of any successful breaches. A robust security strategy is a continuous process, demanding vigilance and a commitment to best practices.
Secure PHP Coding Best Practices
Implementing secure coding practices is paramount. These practices go beyond simply writing functional code; they involve a mindset of anticipating potential vulnerabilities and designing defenses against them. This proactive approach is far more effective than reactive patching.
- Use Prepared Statements: Prepared statements are a crucial defense against SQL injection. They separate the SQL query structure from user-supplied data, preventing malicious code from being injected and executed.
- Parameterize Queries: Always parameterize database queries to prevent SQL injection vulnerabilities. This ensures that user inputs are treated as data, not as executable code.
- Escape User Input: Even with prepared statements, escaping user input is a critical step. This prevents unexpected behavior or vulnerabilities arising from special characters in user-provided data.
- Validate and Sanitize Input: Thoroughly validate and sanitize all user inputs. This includes checking data types, lengths, and formats, and removing or escaping potentially harmful characters.
- Use the Least Privilege Principle: Grant database users and application processes only the necessary permissions. Restricting access minimizes the damage if a breach occurs.
- Avoid Using eval(): The
eval()function is inherently dangerous and should be avoided whenever possible. It allows arbitrary code execution, opening a significant security vulnerability. - Regularly Update Dependencies: Keep all libraries and frameworks up-to-date to benefit from the latest security patches.
- Enable Error Reporting in Development, Disable in Production: Detailed error reporting is valuable during development for debugging, but should be disabled in production environments to prevent exposing sensitive information to attackers.
Input Validation and Sanitization, Php vulnerability exploited
Input validation and sanitization are fundamental security measures. They act as the first line of defense against many common attacks, preventing malicious data from entering your application. Failing to validate and sanitize input is a recipe for disaster.
Validation ensures that the data conforms to expected types, formats, and ranges. Sanitization cleanses the data, removing or escaping potentially harmful characters. Consider this example: a form field expecting a numerical ID. Validation checks if the input is indeed a number, and sanitization removes any non-numeric characters.
Regular Security Updates and Patching
Staying current with security updates and patches is non-negotiable. Vulnerabilities are constantly being discovered in PHP itself and in its associated libraries and frameworks. Regular patching ensures your application is protected against known exploits. Failing to update leaves your system vulnerable to attacks that could have been prevented.
Establish a routine for applying updates promptly, ideally using a version control system to track changes and easily revert if necessary. Prioritize critical security patches immediately.
Secure Development Lifecycle (SDLC)
Incorporating security throughout the entire software development lifecycle is crucial. A secure SDLC ensures that security is not an afterthought, but an integral part of every stage of development.
This includes security requirements gathering, threat modeling, secure coding practices, code reviews, penetration testing, and regular security audits. Each stage should include specific security checkpoints and measures to identify and mitigate vulnerabilities before they reach production.
Case Studies of Exploited Vulnerabilities
Analyzing real-world incidents helps us understand the practical implications of PHP vulnerabilities. These case studies highlight the severity of these flaws and the importance of proactive security measures. Let’s delve into specific examples to illustrate these points.
The 2013 Drupalgeddon Vulnerability (CVE-2018-7600)
This high-profile vulnerability affected Drupal, a popular content management system (CMS) often implemented using PHP. The flaw resided in the Drupal core’s form API, allowing remote attackers to execute arbitrary code without authentication. Exploitation involved sending a specially crafted HTTP request to a vulnerable Drupal site. Successful exploitation granted attackers complete control over the compromised server, enabling them to steal data, install malware, or use the server for further malicious activities. The impact was widespread, with numerous websites globally affected. Remediation involved patching Drupal installations to update the vulnerable form API component. This vulnerability highlighted the dangers of outdated software and the importance of promptly applying security patches.
Comparison with the 2019 WordPress Plugin Vulnerability (Example)
While the Drupalgeddon case involved a core component vulnerability, many significant incidents stem from vulnerabilities in third-party plugins or extensions. For example, imagine a hypothetical scenario involving a widely used WordPress plugin for e-commerce. Suppose this plugin contained a SQL injection vulnerability allowing attackers to manipulate database queries. This could lead to data breaches, account takeovers, or even complete site defacement. Similar to the Drupalgeddon incident, remediation would involve updating the vulnerable plugin or, if an update isn’t available, removing the plugin entirely. The key difference lies in the source of the vulnerability; Drupalgeddon was a core vulnerability, while the WordPress example involves a third-party extension. Both scenarios, however, demonstrate the critical need for rigorous security practices across all software components, including carefully vetting and updating third-party extensions. The impact of both vulnerabilities is severe, potentially resulting in data loss, financial damage, and reputational harm.
Tools and Techniques for Vulnerability Detection: Php Vulnerability Exploited
Hunting down vulnerabilities in PHP applications isn’t about wielding a magic wand; it’s about employing the right tools and techniques. A proactive approach to security means regularly scanning your code and applications for weaknesses before malicious actors do. This involves both automated tools and the keen eye of a skilled security auditor.
Static and Dynamic Analysis Tools
Static analysis tools examine your code without actually running it. They scrutinize the code’s structure, looking for common vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure file handling. These tools are excellent for catching errors early in the development process. Dynamic analysis, on the other hand, involves running the application and observing its behavior under various conditions. This approach helps uncover vulnerabilities that only appear during runtime. Tools like RIPS and SonarQube are examples of static analysis tools that can identify potential security issues. For dynamic analysis, tools such as OWASP ZAP (Zed Attack Proxy) are widely used, allowing security testers to simulate attacks and assess the application’s resilience.
Conducting a Security Audit
A comprehensive security audit is more than just running a scan; it’s a systematic process. It begins with identifying the scope of the audit, determining which parts of the application need to be examined. Next, a vulnerability scan is performed using automated tools, which helps create an initial inventory of potential weaknesses. Manual code review is then essential; this involves meticulously examining the codebase for vulnerabilities that automated tools might miss. Finally, penetration testing, simulating real-world attacks, helps validate the findings and assess the effectiveness of existing security measures. The entire process requires expertise in both PHP development and security best practices.
Using a Vulnerability Scanning Tool
Let’s imagine we’re using OWASP ZAP to scan a sample PHP application that handles user logins. First, we launch ZAP and configure it to point to the application’s URL. ZAP then crawls the application, mapping out its functionalities and identifying potential entry points for attacks. During the active scan, ZAP sends various requests to the application, simulating attacks like SQL injection and XSS. The results show vulnerabilities categorized by severity and location within the code. For example, ZAP might flag a vulnerable login form susceptible to SQL injection because it doesn’t properly sanitize user input. Based on these findings, developers can then patch the vulnerabilities. Remember, even the most sophisticated tool requires careful interpretation of results.
Open-Source Security Testing Tools and Their Capabilities
Choosing the right tool depends on your needs and resources. Here’s a list of open-source tools and their strengths:
- OWASP ZAP: A comprehensive web application security scanner, covering a wide range of vulnerabilities.
- RIPS: A static analysis tool specializing in detecting vulnerabilities in PHP applications.
- SonarQube: A platform for continuous inspection of code quality and security, supporting various programming languages including PHP.
- Brakeman: A static analysis tool specifically designed for Ruby on Rails applications, but can be adapted to other environments with modifications.
- PHP CodeSniffer: While not strictly a security scanner, it helps enforce coding standards which indirectly improve security by reducing vulnerabilities associated with poor coding practices.
These tools provide different approaches to vulnerability detection and often complement each other in a robust security testing strategy. Remember that no single tool is a silver bullet; a combination of tools and manual review is usually necessary for effective vulnerability detection.
Ending Remarks
Source: thehackernews.com
In the ever-evolving landscape of web security, understanding and mitigating PHP vulnerabilities is paramount. While the potential damage from exploited vulnerabilities can be severe, proactive measures like secure coding practices, regular updates, and robust security audits can significantly reduce your risk. Remember, staying vigilant and informed is your best defense against the digital bad guys. So, brush up on your security game, and keep your websites safe.