Blast radius man in the middle attack – Blast radius man-in-the-middle attack: Ever wondered how far the damage from a successful MITM attack can spread? It’s not just about stolen passwords; it’s about the ripple effect across your entire network. This article dives deep into understanding the blast radius – the extent of the damage – caused by different types of MITM attacks, exploring factors like network architecture, security protocols, and the specific vulnerabilities exploited. We’ll examine real-world examples to illustrate just how devastating, or surprisingly contained, the consequences can be.
From ARP poisoning to DNS spoofing and SSL stripping, we’ll dissect various MITM attack vectors, analyzing their potential impact on servers, clients, and routers. We’ll also delve into practical strategies for minimizing the blast radius, including network segmentation, access controls, and robust security tools. Get ready to bolster your network’s defenses and limit the potential fallout from a successful attack.
Defining “Blast Radius” in Man-in-the-Middle Attacks
Source: threatcop.com
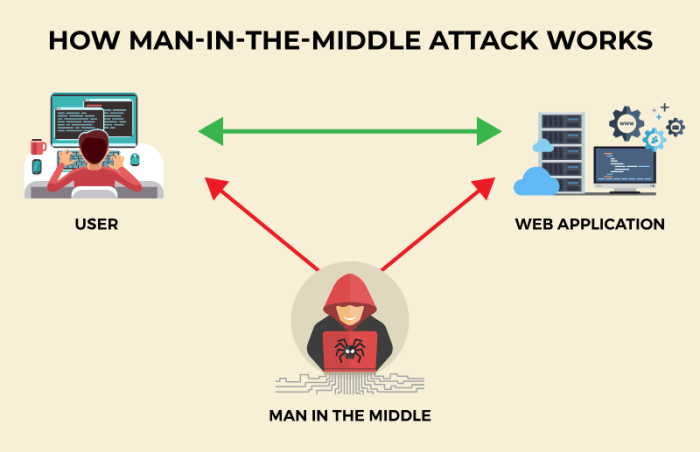
In the thrilling world of cybersecurity, a successful man-in-the-middle (MITM) attack isn’t just about intercepting a single conversation; it’s about the potential ripple effect, the damage it can cause across a network. This ripple effect is what we call the “blast radius.” Understanding its scope is crucial for effective security planning and mitigation.
The blast radius in a MITM attack refers to the extent of the compromise resulting from the successful interception and manipulation of communication between two or more parties. It’s the area of impact, encompassing all the systems, data, and users affected by the attacker’s actions. Think of it like an explosion – the closer you are to the epicenter (the compromised system), the greater the damage.
Factors Influencing Blast Radius
Several factors determine the size of the blast radius. Network architecture plays a significant role; a poorly segmented network allows the attacker to easily move laterally, expanding the impact. Robust security measures, like strong authentication and encryption, can significantly limit the blast radius by containing the attack. The number and type of compromised systems also matter – a compromised server will have a far larger impact than a compromised workstation.
Examples of Small and Large Blast Radii
Consider a scenario where an attacker compromises a single, isolated user’s laptop through a phishing email. The blast radius is relatively small, limited primarily to that user’s data and accounts. However, if the attacker compromises a domain controller in a company’s network, the blast radius becomes enormous. The attacker gains access to all user credentials, sensitive data, and potentially the entire network infrastructure. The consequences are far-reaching and potentially devastating.
Hypothetical Network Diagram Illustrating MITM Attack and Blast Radius
Imagine a network with four segments: the Internet, a Demilitarized Zone (DMZ), an internal network, and a database server.
| Segment | Description | Vulnerability | Blast Radius Impact |
|---|---|---|---|
| Internet | Publicly accessible network | High (potential entry point for attackers) | Indirect; initial attack vector |
| DMZ | Contains publicly accessible servers (e.g., web server) | Medium (requires stronger security than internal network) | Moderate; compromise can lead to data breaches or further network penetration |
| Internal Network | Contains internal servers and workstations | Low (ideally protected by firewall and other security measures) | High if compromised; attacker can access sensitive data and internal systems |
| Database Server | Contains sensitive company data | High (critical asset requiring robust security) | Catastrophic; compromise leads to significant data loss and potential regulatory fines |
In this example, a successful MITM attack on the DMZ web server could potentially expand the blast radius to the internal network and even the database server if security measures are inadequate. The attacker might exploit vulnerabilities to move laterally, gaining access to more sensitive data and systems. Conversely, if strong security measures are in place, the blast radius might remain contained within the DMZ.
Types of Man-in-the-Middle Attacks and Their Blast Radius
Man-in-the-middle (MITM) attacks represent a significant threat in modern networking, compromising data integrity and confidentiality. Understanding the various types of MITM attacks and their potential impact is crucial for effective security measures. The “blast radius,” or the extent of the attack’s influence, varies considerably depending on the specific technique employed and the vulnerabilities exploited.
Different MITM attacks leverage distinct network vulnerabilities, leading to varying levels of impact. The attacker’s ability to intercept and manipulate communication depends on their position within the network and the specific protocols they target. This section will explore several common MITM attack types, analyzing their mechanisms, vulnerabilities exploited, and their resulting blast radius.
ARP Poisoning
ARP poisoning targets the Address Resolution Protocol (ARP), which maps IP addresses to MAC addresses on local area networks (LANs). By sending falsified ARP replies, an attacker can redirect network traffic intended for a specific device to their own machine. This grants the attacker complete control over communication between the targeted device and other network nodes within the same LAN segment. The blast radius is limited to the local network segment, but the impact can be devastating for all devices within that segment.
The vulnerabilities exploited are the reliance on unverified ARP responses and the lack of robust authentication mechanisms in the ARP protocol itself. The attacker doesn’t need privileged access; they just need to be on the same LAN segment. The impact on network components includes compromised communication between clients and servers, allowing the attacker to eavesdrop on traffic, inject malicious code, or perform denial-of-service attacks. Routers are indirectly affected as traffic is misdirected, but they are not directly compromised.
Steps involved in a successful ARP poisoning attack and its potential impact:
- The attacker sends forged ARP replies to the target device, claiming to be the default gateway (router).
- The attacker simultaneously sends forged ARP replies to the default gateway, claiming to be the target device.
- All traffic intended for the target device is now routed through the attacker’s machine.
- All traffic from the target device is also routed through the attacker’s machine.
- Impact: Data theft, session hijacking, man-in-the-browser attacks, denial-of-service attacks, and the potential compromise of sensitive information within the LAN segment.
DNS Spoofing, Blast radius man in the middle attack
DNS spoofing involves manipulating Domain Name System (DNS) responses to redirect users to malicious websites. The attacker intercepts DNS queries and provides fraudulent responses, directing users to a controlled server instead of the legitimate one. This attack’s blast radius can be significantly larger than ARP poisoning, potentially affecting numerous users across different networks if the compromised DNS server is widely used.
The vulnerabilities exploited are weaknesses in DNS server security, such as lack of proper authentication or vulnerabilities in the DNS server software itself. The impact on network components includes compromised client-server communication, phishing attacks, malware distribution, and data breaches. Servers can be indirectly impacted if they are the target of the malicious redirection.
SSL Stripping
SSL stripping targets HTTPS connections by downgrading them to insecure HTTP. This is typically achieved by manipulating the communication between the client and the server during the initial connection handshake. The attacker intercepts the communication, removing the SSL/TLS encryption, and then forwards the traffic between the client and server. The blast radius depends on the attacker’s ability to intercept traffic, which could range from a single user to a larger network segment depending on the attack method.
The vulnerabilities exploited often lie in the client’s lack of awareness or misconfiguration, allowing the attacker to intercept and manipulate the connection establishment. The impact on network components involves data theft, session hijacking, and the compromise of sensitive information transmitted in plain text. Servers are not directly compromised, but the attacker can intercept sensitive data exchanged with the clients.
Mitigating the Blast Radius of Man-in-the-Middle Attacks
So, you’ve learned about the devastating potential of a man-in-the-middle (MITM) attack – the digital equivalent of a highway robbery. But fear not, digital highway patrol is on the case! Minimizing the impact of a successful MITM attack isn’t about preventing every single attempt (that’s practically impossible), but about significantly reducing the damage if one does slip through. Think of it like building a robust fortress – you might not stop every siege, but you can make it incredibly difficult for attackers to breach your defenses and conquer your digital kingdom.
Implementing robust security measures is crucial for minimizing the damage caused by a successful MITM attack. A multi-layered approach, combining preventative measures with proactive detection and response strategies, is the most effective way to shrink that blast radius. Think of it as a layered defense system, each layer adding to the overall protection.
Network Segmentation and Access Control Limit the Impact
Network segmentation divides your network into smaller, isolated segments. This limits the impact of a compromise. If an attacker gains access to one segment, they won’t automatically have access to the entire network. Think of it like separating your valuable jewels from your everyday silverware – even if a thief gets into the silverware drawer, your precious jewels remain safe. Access control mechanisms, such as role-based access control (RBAC), further restrict access to sensitive data and systems, even within segmented networks. This ensures that only authorized personnel can access specific resources, even if an attacker manages to compromise a user account. This granular control limits the attacker’s ability to move laterally within your network and wreak havoc.
Security Tools and Technologies for MITM Detection and Prevention
A robust security posture necessitates a proactive approach. Here’s a selection of tools and technologies that can help you detect and prevent MITM attacks:
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, including patterns indicative of MITM attacks. They can alert you to potential threats and even block malicious traffic.
- Firewall: A firewall acts as a gatekeeper, controlling network traffic based on predefined rules. By carefully configuring your firewall, you can block unauthorized connections and prevent attackers from intercepting communications.
- VPN (Virtual Private Network): VPNs encrypt your internet traffic, making it much harder for attackers to intercept and decrypt your data. Think of it as a secure tunnel protecting your data from prying eyes.
- HTTPS Everywhere: This browser extension enforces HTTPS connections whenever possible, ensuring that your communications are encrypted even when the website doesn’t automatically use HTTPS.
- Network Monitoring Tools: These tools provide visibility into your network traffic, allowing you to identify unusual patterns or anomalies that might indicate a MITM attack.
These tools, used in conjunction, provide a comprehensive defense against MITM attacks, significantly reducing the likelihood of a successful compromise and limiting the damage if one occurs.
Strong Encryption Protocols Reduce Potential Damage
Strong encryption is your best friend in the fight against MITM attacks. Protocols like TLS 1.3 and its successor, TLS 1.4, provide robust encryption that makes it incredibly difficult for attackers to decrypt intercepted data. Even if an attacker manages to intercept your communications, they won’t be able to understand the content without the decryption key. This is analogous to writing a message in a code that only you and the recipient can decipher; the attacker intercepts the message, but it remains meaningless to them. The implementation of strong encryption protocols significantly reduces the potential damage from a successful MITM compromise, protecting sensitive data from unauthorized access. Think of it as a highly secure vault protecting your most valuable assets. The stronger the encryption, the more difficult it is for even the most skilled thieves to crack the code and access your valuable data.
Case Studies
Real-world examples illuminate the devastating consequences of Man-in-the-Middle (MITM) attacks and the varying degrees of their “blast radius.” Analyzing these incidents helps us understand the vulnerabilities exploited, the scale of the impact, and the crucial steps needed for effective prevention and mitigation. We’ll examine two distinct cases, highlighting their similarities and differences to provide a comprehensive picture.
The DigiNotar Certificate Authority Breach
This 2011 attack targeted DigiNotar, a Dutch Certificate Authority (CA). The attackers compromised DigiNotar’s systems, gaining the ability to issue fraudulent SSL certificates. These certificates, when used by websites, allowed the attackers to intercept communications between users and those websites, effectively establishing a MITM position. The impact extended far beyond DigiNotar’s immediate clients. The compromised certificates could be used to impersonate virtually any website, leading to widespread data breaches and financial fraud.
| Timeline | Consequences |
|---|---|
| Attackers gain unauthorized access to DigiNotar’s systems. | Initial compromise, undetected for a period of time. |
| Attackers issue fraudulent SSL certificates for various domains. | Users connecting to legitimate websites are unknowingly redirected to attacker-controlled servers. |
| Users’ sensitive information, including login credentials and financial data, is intercepted. | Widespread data breaches, impacting potentially millions of users. Significant financial losses for individuals and businesses. |
| The breach is discovered and publicly disclosed. | Loss of trust in DigiNotar and its services. Significant reputational damage and financial losses for DigiNotar. Legal repercussions for DigiNotar. |
The Iranian Nuclear Program Stuxnet Attack
Unlike the DigiNotar incident which targeted a CA for widespread compromise, the Stuxnet worm, discovered in 2010, represented a highly targeted MITM attack against the Iranian nuclear program. Stuxnet infected industrial control systems (ICS) managing uranium enrichment centrifuges, manipulating their operation without detection. This was achieved by intercepting communication between the centrifuges and their control systems, subtly altering the instructions to cause damage and slow down the enrichment process. The blast radius in this case was geographically limited, impacting only the targeted centrifuges within the Iranian nuclear facilities. However, the geopolitical consequences were significant.
Comparison of Case Studies
Both attacks leveraged the MITM technique, but their targets, methods, and blast radius differed significantly. DigiNotar involved a broad, indiscriminate attack aiming to compromise numerous users and websites, resulting in a wide blast radius. Stuxnet, conversely, was a highly targeted, sophisticated attack with a limited geographic blast radius but far-reaching geopolitical consequences. The scale of the DigiNotar breach was amplified by the nature of CAs; a single compromise affects the trust of a vast network. Stuxnet’s impact was magnified by the critical infrastructure it targeted and the geopolitical context.
Lessons Learned
These case studies underscore the critical need for robust security measures across all levels. For CAs, stringent security practices, regular audits, and multi-factor authentication are essential. For organizations managing critical infrastructure, advanced threat detection and response systems, along with air-gapped networks and strict access controls, are vital. Furthermore, strong user education regarding phishing and other social engineering tactics is crucial to prevent initial compromises. The varying blast radii highlight the importance of considering the potential impact of security breaches and tailoring mitigation strategies accordingly.
Visualizing the Blast Radius

Source: makinrajin.com
Understanding the impact of a man-in-the-middle (MITM) attack isn’t just about the immediate victim; it’s about the ripple effect across a network. The “blast radius” describes this impact, and visualizing it helps understand the potential consequences. This section explores scenarios highlighting how network configurations and security measures dramatically affect the size of this radius.
MITM Attack on a Single Device with Extensive Network Impact
Imagine a small office network, where all devices share a single, unsecured Wi-Fi network. No firewalls or VLANs segment the network. An employee’s laptop becomes the victim of a MITM attack. The attacker, positioned between the laptop and the Wi-Fi router, intercepts all traffic. Because the network lacks segmentation, the attacker now has access to all devices connected to that Wi-Fi. They can potentially access sensitive data from shared network drives, intercept communications between other employees, and even install malware on other machines, effectively expanding the attack’s reach far beyond the initially compromised laptop. The network resembles a single, interconnected web, and the attack spreads like wildfire through its unsecured threads. The compromised laptop acts as a gateway, granting access to the entire office network. This is a classic example of a small attack with a significantly large blast radius.
MITM Attack on a Critical Server with Limited Impact
Now, picture a large corporation with a highly secure network infrastructure. A critical server, handling sensitive customer data, falls victim to a MITM attack. However, this server is meticulously protected. It resides within a tightly controlled virtual private cloud (VPC), separated from other network segments by robust firewalls and intrusion detection systems. Multi-factor authentication protects access, and data encryption ensures that even if intercepted, the data remains unreadable. The attacker, despite gaining initial access to the server, finds their ability to move laterally severely restricted. Their blast radius remains confined to the compromised server itself, preventing widespread damage. The server, though compromised, remains a contained island within a vast and well-defended network.
Factors Influencing Blast Radius
The size of the blast radius in a MITM attack is significantly influenced by several key factors:
- Network Segmentation: The presence of firewalls, VLANs, and other security measures that segment the network into isolated zones. Strong segmentation limits the spread of an attack.
- Security Protocols: The use of encryption (HTTPS, VPNs), multi-factor authentication, and robust access controls. Strong security protocols make it harder for attackers to exploit vulnerabilities and expand their reach.
- Network Topology: The physical and logical layout of the network. A centralized, less segmented network is more vulnerable than a distributed, well-segmented one.
- Vulnerability Management: Regular patching and updates of software and systems. Outdated software creates opportunities for attackers to exploit vulnerabilities.
- Monitoring and Detection: The use of intrusion detection and prevention systems (IDPS) and security information and event management (SIEM) tools. These systems can detect and respond to suspicious activity, limiting the impact of an attack.
Last Word: Blast Radius Man In The Middle Attack

Source: pcdn.co
Understanding the blast radius of a man-in-the-middle attack is crucial for effective cybersecurity. While completely eliminating the risk is impossible, by implementing strong security practices, leveraging robust tools, and understanding the vulnerabilities of different attack vectors, you can significantly minimize the damage and protect your valuable data and systems. Remember, proactive security is your best defense against the unpredictable consequences of a compromised network.