Kimsuky hackers exe docx attacks: Think North Korean state-sponsored hacking, sophisticated social engineering, and some seriously nasty malware. We’re diving deep into the world of Kimsuky, exploring their history, tactics, and the devastating impact of their EXE and DOCX-based attacks. Get ready to unravel the intricate web of deception and destruction they weave.
From meticulously crafted phishing emails to expertly disguised malicious documents, Kimsuky’s operations showcase a chilling level of expertise. We’ll dissect their methods, analyze their malware, and uncover the strategies they employ to bypass security measures. This isn’t just another cybersecurity story; it’s a look inside the mind of a relentless adversary.
Kimsuky Group
Source: bleepstatic.com
The Kimsuky group is a sophisticated North Korean state-sponsored hacking group known for its persistent and targeted cyber espionage campaigns. Operating for over a decade, they’ve consistently refined their techniques, making them a significant threat in the global cybersecurity landscape. Their operations are characterized by meticulous planning, the exploitation of zero-day vulnerabilities, and a heavy reliance on social engineering to achieve their objectives.
Kimsuky’s targets and motivations are primarily focused on stealing sensitive information for the benefit of the North Korean government. Their victims often include think tanks, government agencies, and defense contractors involved in geopolitical issues relevant to North Korea, particularly those relating to its nuclear program and international relations. This data acquisition allows the North Korean regime to inform its strategic decisions, counter international pressure, and advance its national interests.
Operational Methods and Tactics
Kimsuky employs a multi-stage attack process. Initial compromise often involves spear-phishing emails containing malicious attachments or links. These lures are meticulously crafted to appear legitimate and relevant to the target’s interests, often exploiting current events or known professional contacts. Once initial access is gained, the group leverages various techniques to maintain persistence, escalate privileges, and exfiltrate data. This can include the use of custom malware, backdoors, and other advanced techniques to evade detection and maintain control over compromised systems. They are known for their patience and persistence, often spending months or even years maintaining access to a target’s network before exfiltrating data.
Social Engineering Techniques
Social engineering forms a cornerstone of Kimsuky’s attack methodology. They invest considerable time and effort in researching their targets, identifying key individuals, and crafting highly personalized phishing campaigns. This often involves creating fake online identities, posing as legitimate contacts, and leveraging social media to build trust and gather intelligence. The sophistication of their social engineering is evident in their ability to bypass even the most vigilant security measures, emphasizing the human element’s vulnerability in cybersecurity. For example, they might impersonate a researcher from a respected institution to gain access to a target’s email account.
Timeline of Significant Attacks
Tracking Kimsuky’s activities precisely is challenging due to the clandestine nature of their operations. However, several significant attacks have been attributed to them, revealing an evolution in their tactics and targets over time. Early campaigns focused on smaller, more localized targets. Over time, their operations became more ambitious, targeting larger organizations and utilizing more sophisticated techniques. A noticeable shift occurred towards leveraging zero-day vulnerabilities and employing more advanced malware, indicating a continuous investment in enhancing their capabilities. While specific dates and details are often kept confidential for security reasons, reports consistently show a pattern of escalating sophistication and expanding target range over the years. Attribution to Kimsuky is often based on technical analysis of malware samples, infrastructure overlaps, and operational similarities across various campaigns.
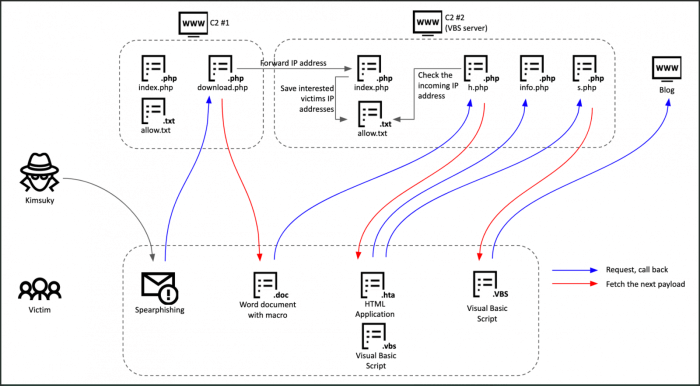
EXE and DOCX Malware Delivery
Source: thehackernews.com
Kimsuky, a notorious North Korean state-sponsored hacking group, employs sophisticated techniques to deliver malicious EXE and DOCX files, often leveraging social engineering and advanced evasion tactics to bypass security measures. Their operations demonstrate a high level of technical expertise and a deep understanding of human psychology. Understanding their methods is crucial for organizations aiming to bolster their cybersecurity defenses.
Kimsuky’s malware delivery methods are multifaceted, combining spear-phishing emails with carefully crafted lures to trick unsuspecting victims into executing malicious code. These attacks often target specific individuals or organizations, demonstrating meticulous pre-attack reconnaissance and a tailored approach. The group leverages both established and novel techniques to maximize their chances of success.
Spear-Phishing Email Tactics
Kimsuky’s phishing campaigns are known for their precision and realism. Emails often mimic legitimate communications, using forged sender addresses, authentic-looking logos, and subject lines designed to pique the recipient’s interest. For example, they might impersonate a colleague, a business partner, or even a government agency, sending emails containing malicious attachments or links. The content is tailored to the target’s industry and interests, increasing the likelihood of engagement. A common tactic is to embed malicious links within seemingly innocuous documents, such as job descriptions or press releases.
Malicious Document Engineering
Malicious DOCX files often contain embedded macros that execute malicious code upon opening. These macros can download and install further malware, such as keyloggers or remote access trojans (RATs). Kimsuky frequently uses techniques to obfuscate the malicious code, making it difficult for antivirus software to detect. They might use techniques like polymorphism, where the code changes its structure to evade signature-based detection, or employ packing techniques to compress and encrypt the malicious code. In some instances, the DOCX file might appear benign initially, but additional malicious content is downloaded and executed after the user interacts with the document.
EXE File Delivery and Execution
Malicious EXE files are often delivered through spear-phishing emails, disguised as legitimate software updates or attachments related to the target’s work. These EXEs can contain various types of malware, including backdoors that allow attackers to remotely control the compromised system. Kimsuky may leverage techniques like code signing certificates (potentially stolen or forged) to increase the trust level of the malicious EXE. This adds a layer of legitimacy, deceiving security software and users alike.
Bypassing Security Software
Kimsuky consistently adapts its techniques to bypass security software. This includes using advanced evasion techniques such as code obfuscation, polymorphism, and packing to hinder static and dynamic analysis. They might also exploit zero-day vulnerabilities in software to gain initial access. Furthermore, they employ techniques to disable or circumvent security features on the victim’s system, ensuring persistence and stealthy operation.
Hypothetical Kimsuky Attack Chain
Imagine a researcher working on a sensitive project related to North Korea. A seemingly innocuous email arrives, purportedly from a known colleague, containing a DOCX file titled “Project Update.docx”. The document appears benign, containing a summary of the project’s progress. However, an embedded macro silently downloads a malicious EXE file, which then establishes a persistent backdoor on the researcher’s system. This backdoor allows Kimsuky to exfiltrate sensitive data, potentially including research documents, communication logs, and personal information, without triggering immediate detection. The attacker maintains persistent access, potentially using the compromised system as a springboard for further attacks.
Analysis of Kimsuky’s Malware
Source: itechtics.com
Kimsuky, a notorious North Korean state-sponsored Advanced Persistent Threat (APT) group, has demonstrated a sophisticated and evolving arsenal of malware. Their operations leverage a combination of social engineering, spear-phishing, and meticulously crafted malicious documents and executables to infiltrate their targets. Understanding the characteristics of their malware is crucial for effective defense.
Kimsuky’s malware toolkit isn’t static; it adapts to evade detection and exploit emerging vulnerabilities. This analysis focuses on the key features and functionalities of their EXE and DOCX malware, comparing and contrasting their use across different campaigns and examining their impact on victims.
Key Features and Functionalities of Kimsuky’s EXE and DOCX Malware
Kimsuky’s malware exhibits several consistent characteristics. Their DOCX files often employ macro-based exploits, leveraging vulnerabilities in Microsoft Office applications to execute malicious code. Once executed, these macros typically download and install further malicious payloads, often in the form of EXEs. These EXEs frequently include functionalities for data exfiltration, system reconnaissance, and persistence. They often employ techniques like process injection and DLL hijacking to evade detection by security software. The malware is designed for stealth, aiming to remain undetected for extended periods, allowing for the sustained compromise of the victim’s systems. For example, one campaign involved a malicious DOCX document disguised as a job application, tricking the victim into enabling macros. This triggered the download and execution of a sophisticated backdoor.
Comparison of Malware Across Different Kimsuky Campaigns
While Kimsuky maintains a core set of capabilities, variations exist in their malware across different campaigns. Earlier campaigns might rely on simpler techniques, while more recent operations demonstrate more advanced evasion and persistence mechanisms. For instance, some campaigns utilized custom-developed backdoors with unique functionalities, tailored to specific targets and their networks. Other campaigns involved the repurposing of publicly available tools, modified to evade detection. This adaptability highlights the group’s continuous refinement of their techniques. This evolution necessitates a dynamic approach to threat detection and mitigation.
Payloads and Impact on Victims
The payloads delivered by Kimsuky’s malware vary depending on the campaign’s objectives. However, common themes include data exfiltration, system reconnaissance, and the establishment of a persistent presence on the victim’s system. Data exfiltration can range from stealing sensitive documents and emails to capturing credentials and network configurations. System reconnaissance involves gathering information about the victim’s network, software, and hardware. This information is invaluable for planning subsequent attacks or identifying valuable targets within the network. The ultimate impact on victims includes data breaches, financial losses, intellectual property theft, and reputational damage. A high-profile case involved the theft of sensitive military documents, illustrating the potential severity of their attacks.
Persistence Mechanisms
Kimsuky employs various techniques to achieve persistence on compromised systems. These include the creation of scheduled tasks, registry modifications, and the installation of services. Scheduled tasks allow the malware to automatically execute at regular intervals, ensuring its continued operation. Registry modifications alter system settings to maintain persistence even after a reboot. The installation of services ensures the malware runs as a background process, making it more difficult to detect and remove. The specific persistence mechanisms employed can vary depending on the malware variant and the target operating system. The use of these robust techniques underlines the group’s dedication to maintaining long-term access to compromised systems.
Impact and Consequences of Attacks
Kimsuky’s sophisticated cyberattacks, leveraging malicious EXE and DOCX files, inflict significant damage on individuals and organizations. The consequences extend far beyond simple data breaches, impacting national security, economic stability, and individual privacy. Understanding the full scope of these repercussions is crucial for effective prevention and mitigation strategies.
The potential consequences of successful Kimsuky attacks are wide-ranging and severe. Stolen data can be used for various malicious purposes, leading to significant financial losses, reputational damage, and legal repercussions. The long-term impact on victims can be substantial, hindering their operations and eroding public trust.
Types of Data Stolen and Their Misuse
Kimsuky’s targets often include government agencies, think tanks, and defense contractors. The types of data they seek are highly sensitive and valuable, including intellectual property, military secrets, diplomatic communications, and personal information. This data is then misused in various ways: for espionage, to gain a competitive advantage, to blackmail individuals, or to launch further attacks. For example, stolen intellectual property could be sold to competitors, giving them an unfair advantage in the market. Military secrets could be leaked to adversarial nations, compromising national security. Personal data could be used for identity theft or targeted phishing campaigns.
Real-World Impacts of Kimsuky’s Activities
While specific details of Kimsuky’s operations are often kept confidential for national security reasons, publicly available information reveals the real-world impact of their activities. Reports indicate successful breaches leading to the theft of sensitive government documents and intellectual property related to defense technologies. These breaches have resulted in significant investigations and damage control efforts by affected organizations, consuming substantial resources and time. The long-term effects on national security and international relations are difficult to fully quantify but are undoubtedly substantial.
Financial and Reputational Damage
| Damage Type | Example | Cost | Impact |
|---|---|---|---|
| Financial Loss | Loss of intellectual property leading to decreased market share and lost revenue. | Millions of dollars (depending on the value of the IP) | Significant financial strain, potential bankruptcy. |
| Reputational Damage | Public disclosure of a data breach, leading to loss of customer trust and investor confidence. | Difficult to quantify, but can lead to decreased sales, difficulty attracting investors. | Long-term damage to brand image, difficulty in attracting and retaining customers. |
| Legal Costs | Lawsuits from affected individuals and regulatory fines. | Hundreds of thousands to millions of dollars, depending on the severity of the breach and legal jurisdiction. | Financial burden, potential legal liabilities, and reputational damage. |
| Operational Disruption | System downtime and recovery efforts following a successful attack. | Varies depending on the size and complexity of the organization and the extent of the disruption. | Loss of productivity, potential delays in projects, and decreased efficiency. |
Defense Strategies and Mitigation Techniques
Kimsuky’s sophisticated attacks highlight the urgent need for robust cybersecurity strategies. Their use of spear-phishing emails containing malicious EXE and DOCX files underscores the importance of proactive defense mechanisms, extending beyond basic antivirus solutions. A multi-layered approach is crucial to effectively mitigate the risk of compromise.
Preventing Kimsuky-style attacks requires a comprehensive strategy that combines technological safeguards with employee training and awareness. Simply relying on software is insufficient; a human element is always involved, either as the target or as a weak link in the chain. Therefore, a combination of technical and human-centric approaches is necessary for effective defense.
Email Security Best Practices
Implementing strong email security measures is paramount. This involves utilizing advanced threat protection solutions that go beyond simple spam filters. These solutions should actively scan attachments for malicious code, employing sandboxing techniques to analyze suspicious files in a controlled environment before they reach user inboxes. Furthermore, implementing email authentication protocols like DMARC, SPF, and DKIM helps to verify the authenticity of emails and prevent spoofing, a common tactic employed by Kimsuky. Regularly updating email security settings and policies is crucial to adapt to evolving threat landscapes.
Secure Handling of EXE and DOCX Files
Protecting against malicious EXE and DOCX files requires a multi-pronged approach. Firstly, users should be trained to identify suspicious emails and attachments. This includes being wary of unexpected emails, unusual attachments, and generic greetings. Secondly, organizations should enforce strict policies regarding the opening of attachments from unknown or untrusted sources. Thirdly, deploying application whitelisting technologies can significantly reduce the risk of malware execution by only allowing trusted applications to run. Finally, robust endpoint detection and response (EDR) solutions can monitor system activity for malicious behavior, even if a file initially evades detection.
Employee Training and Awareness
Effective employee training is crucial in preventing successful Kimsuky-style attacks. Regular security awareness training should educate employees about phishing techniques, social engineering tactics, and the dangers of opening malicious attachments. Simulated phishing campaigns can help assess employee vulnerability and reinforce training effectiveness. Training should cover specific examples of Kimsuky’s tactics, including the use of spear-phishing emails and the types of malicious documents they deploy. Employees should be empowered to report suspicious emails and attachments promptly.
Security Tools and Technologies
A combination of security tools and technologies is essential for detecting and mitigating Kimsuky-style attacks.
- Advanced Threat Protection (ATP): These solutions go beyond traditional antivirus, analyzing emails and attachments for malicious behavior using advanced techniques like sandboxing and machine learning.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoint devices for malicious activity, providing visibility into system processes and enabling rapid response to threats.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, enabling detection of suspicious activity and security breaches.
- Application Whitelisting: This technology only allows pre-approved applications to run, significantly reducing the risk of malware execution.
- Data Loss Prevention (DLP): DLP solutions help prevent sensitive data from leaving the organization’s network, mitigating the impact of successful attacks.
- Email Authentication Protocols (DMARC, SPF, DKIM): These protocols help to verify the authenticity of emails and prevent spoofing.
Attribution and Identification of Kimsuky Attacks
Pinpointing the perpetrators behind sophisticated cyberattacks like those launched by Kimsuky requires meticulous investigation and a deep understanding of their tactics. Attribution isn’t a simple process; it’s a complex puzzle requiring the piecing together of various pieces of digital evidence. This involves analyzing malware samples, network traffic, and other digital fingerprints to link them back to a specific threat actor.
Techniques Used for Attribution, Kimsuky hackers exe docx attacks
Attribution to Kimsuky relies on a multi-faceted approach leveraging several key techniques. Researchers analyze the malware’s code for unique characteristics, such as coding styles, embedded comments, and the use of specific tools and libraries. These “digital fingerprints” can be compared against a known database of Kimsuky’s past operations. Furthermore, the infrastructure used to deliver and control the malware, including command-and-control (C2) servers and domains, provides crucial clues. Analysis of these servers’ geographical location, registration details, and associated infrastructure can further solidify attribution. Finally, the targets themselves play a significant role. Kimsuky’s consistent targeting of specific sectors and organizations over time contributes to a clearer picture of their motives and operational patterns. For example, the consistent targeting of South Korean government entities and defense contractors strongly supports the existing attribution to Kimsuky.
Indicators of Compromise (IOCs) Associated with Kimsuky Malware
Kimsuky’s malware arsenal leaves behind a trail of digital breadcrumbs. These Indicators of Compromise (IOCs) are crucial for identifying and responding to their attacks. Common IOCs include specific file hashes (unique digital fingerprints of malware files), domain names used for command and control (C2), IP addresses associated with malicious infrastructure, and specific code signatures found within the malware itself. For instance, the use of specific encryption algorithms or unique obfuscation techniques within their malware samples can act as strong indicators. Moreover, the specific techniques used to deliver the malware, such as spear-phishing emails with malicious attachments or exploiting software vulnerabilities, can also serve as identifying characteristics. The persistence mechanisms employed by Kimsuky’s malware, such as registry entries or scheduled tasks, are further indicators.
The Role of Threat Intelligence in Identifying and Responding to Kimsuky Attacks
Threat intelligence plays a vital role in both proactively identifying and reactively responding to Kimsuky attacks. By collecting and analyzing information from various sources – including open-source intelligence (OSINT), private sector threat feeds, and government agencies – security researchers build a comprehensive picture of Kimsuky’s tactics, techniques, and procedures (TTPs). This intelligence helps organizations anticipate potential attacks, develop targeted defenses, and quickly identify compromised systems. Real-time threat feeds can provide immediate alerts about newly discovered IOCs associated with Kimsuky’s malware, enabling organizations to take swift action to mitigate the impact of an attack. Furthermore, sharing threat intelligence within the cybersecurity community is crucial for collective defense against sophisticated adversaries like Kimsuky.
Stages of Attribution Analysis
A visual representation of the attribution analysis would depict a flowchart. The first stage would be Malware Analysis, encompassing reverse engineering, code analysis, and identification of IOCs. This would feed into the Infrastructure Analysis stage, focusing on identifying C2 servers, domains, and associated infrastructure. Simultaneously, Target Analysis would identify the victims and their affiliations, revealing patterns in the selection of targets. These three streams converge in the Correlation and Analysis stage, where similarities in code, infrastructure, and targets are compared against known Kimsuky activity. The final stage, Attribution, confirms the link between the observed activity and the Kimsuky group based on the accumulated evidence. This flowchart would visually demonstrate the iterative and collaborative nature of attribution analysis, highlighting the interconnectedness of different investigative avenues.
Final Wrap-Up: Kimsuky Hackers Exe Docx Attacks
So, Kimsuky’s attacks aren’t just about stealing data; they’re about crippling organizations and undermining geopolitical stability. Understanding their methods is crucial for building robust defenses. By staying informed about their evolving tactics and investing in proactive security measures, we can better protect ourselves and our data from these highly skilled threat actors. The fight against Kimsuky is far from over, but by arming ourselves with knowledge, we can level the playing field.



