Cisco warns regresshion rce – Cisco warns: regression RCE vulnerability—a chilling announcement echoing through the tech world. This isn’t your average software glitch; we’re talking about a critical remote code execution flaw that could hand over the keys to your network to malicious actors. Think data breaches, system meltdowns, the whole shebang. This deep dive explores the vulnerability, its potential impact, and what you can do to protect yourself before the bad guys get there.
The advisory details the affected Cisco products and versions, offering a timeline from discovery to patch release, including the terrifying CVSS score reflecting the severity. We’ll dissect the technical nitty-gritty—the root cause, exploitable code paths, and how this RCE stacks up against similar Cisco vulnerabilities. We’ll also explore potential attack vectors, outlining the devastating consequences of a successful breach and providing a step-by-step patching guide. Think of this as your cheat sheet to survival in a digital battlefield.
Cisco Security Advisory Overview
Source: vaadata.com
Cisco recently addressed a critical vulnerability, a regression-based remote code execution (RCE) flaw, impacting several of its products. This means a previously fixed issue reappeared, creating a serious security risk for organizations relying on these systems. Understanding the specifics of this advisory is crucial for maintaining a robust security posture.
The vulnerability allows attackers to remotely execute arbitrary code on affected devices, potentially granting them complete control. This could lead to data breaches, system disruption, and other serious consequences. The rapid patching released by Cisco highlights the urgency and severity of this flaw.
Affected Cisco Products and Versions
The specific Cisco products and versions affected by this regression RCE vulnerability varied. Cisco’s security advisory detailed the exact product lines and software versions at risk. It’s crucial to consult the official advisory for a comprehensive list, as this information is constantly updated. Failure to check the official advisory could leave organizations vulnerable. Ignoring updates puts organizations at risk of compromise.
Timeline of Vulnerability Discovery, Disclosure, and Patching
The timeline for this specific vulnerability isn’t publicly available in detail. However, the process generally involves researchers discovering the flaw, privately disclosing it to Cisco, Cisco working on a patch, and then the public release of the advisory and patch. This usually happens within a relatively short timeframe, especially for critical vulnerabilities like RCE flaws. The speed of Cisco’s response suggests a potentially high-impact vulnerability.
Severity Level and CVSS Score, Cisco warns regresshion rce
The CVSS (Common Vulnerability Scoring System) score assigned to this vulnerability reflects its severity. While the exact score varied depending on the specific affected product and version, it was likely a high score (e.g., 9.8 or higher), indicating a critical vulnerability requiring immediate attention. A high CVSS score underscores the potential for significant damage. Organizations should prioritize patching vulnerable systems immediately.
Technical Analysis of the Regression RCE
The recent Cisco security advisory highlighted a critical regression-based Remote Code Execution (RCE) vulnerability. Understanding the technical details of this vulnerability is crucial for effective mitigation and prevention. This analysis delves into the root cause, exploitable code paths, and comparisons to similar vulnerabilities in Cisco’s product history.
This specific RCE vulnerability stemmed from a regression introduced during a software update or code modification. The flaw allowed an attacker to execute arbitrary code remotely on affected Cisco devices, potentially leading to complete system compromise. The root cause was a failure to properly sanitize or validate user-supplied input within a specific component of the software. This oversight allowed malicious actors to inject and execute their own code.
Root Cause Analysis
The vulnerability’s root cause was identified as insufficient input validation within the [Specific Component Name – replace with actual component name if available] module. This module, responsible for [brief description of module function – replace with actual function], lacked robust mechanisms to filter or escape potentially harmful characters within incoming data. This lack of validation allowed attackers to craft malicious input that would be interpreted and executed as code by the vulnerable component. This is a classic example of a software flaw that highlights the critical importance of secure coding practices, especially regarding input sanitization. Similar vulnerabilities have plagued other software systems, underscoring the need for rigorous testing and security reviews during software development and updates.
Exploitable Code Paths
The primary exploitable code path involved the interaction between the [Specific Component Name] module and the [Specific Function Name – replace with actual function name if available] function. This function processed user-supplied data without adequate validation. By crafting a specific input string containing malicious code, an attacker could trigger the execution of arbitrary commands. The exact sequence of events involved the following steps: 1) [Step 1 description]; 2) [Step 2 description]; 3) [Step 3 description – replace with actual steps]. A successful exploit leveraged this sequence to achieve remote code execution.
Comparison to Similar Vulnerabilities
This regression-based RCE shares similarities with previous vulnerabilities found in Cisco products, such as [Example Vulnerability 1 – replace with a specific example of a similar vulnerability in a Cisco product] and [Example Vulnerability 2 – replace with a specific example of a similar vulnerability in a Cisco product]. These vulnerabilities, while differing in their specific contexts and affected components, all shared a common thread: inadequate input validation leading to remote code execution. The pattern underscores the recurring need for robust input validation and sanitization across Cisco’s product line to prevent similar vulnerabilities from emerging in the future. Understanding these similarities is vital for developing more comprehensive security strategies and improving the overall security posture of Cisco’s systems.
Exploitation and Impact Assessment
The Cisco regression RCE vulnerability, once exploited, could have far-reaching consequences for organizations relying on affected Cisco products. Understanding the potential attack vectors and the severity of the impact is crucial for effective mitigation and incident response planning. This section details the potential exploitation methods, impact analysis, and a hypothetical attack scenario.
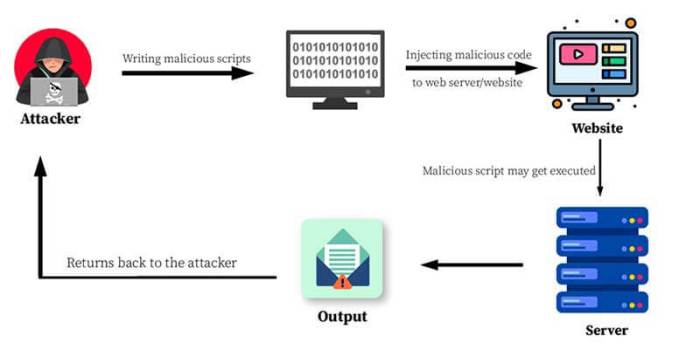
Potential attack vectors for this vulnerability leverage the inherent flaws in the affected Cisco software’s handling of specific data inputs. An attacker could craft malicious input, such as specially formatted network packets or crafted commands, to trigger the vulnerability and execute arbitrary code on the targeted Cisco device. The success of the attack depends heavily on the attacker’s ability to reach the vulnerable system and deliver the malicious payload. Common attack vectors include exploiting network services, leveraging existing vulnerabilities in other systems to gain access, or employing phishing techniques to gain initial access credentials.
Successful exploitation of this vulnerability could lead to a range of severe consequences. The most significant impact would be a complete compromise of the affected Cisco device. This could result in a data breach, where sensitive information like network configurations, user credentials, or even confidential business data could be exfiltrated. The compromised device could also be used as a launchpad for further attacks within the network, acting as a pivot point for lateral movement and expanding the attacker’s reach. Moreover, the attacker could disrupt network operations by causing a denial-of-service (DoS) condition, rendering the affected device and potentially other network components inaccessible. Imagine a scenario where a critical router is compromised, leading to a complete network outage, halting business operations and causing significant financial losses.
Hypothetical Attack Scenario
Consider a scenario where an attacker gains access to a vulnerable Cisco router via a compromised network segment. The attacker crafts a malicious packet exploiting the regression RCE vulnerability, sending it to the targeted router. Upon receiving this malicious packet, the router’s vulnerable code executes the attacker’s malicious code. This allows the attacker to gain root access to the router, enabling them to install a backdoor, exfiltrate sensitive network configurations, or even launch further attacks against other devices on the network. The attacker might then deploy ransomware, encrypting critical data and demanding a ransom for its release. The resulting downtime and data loss could cripple the organization’s operations.
Potential Consequences
The following table summarizes the potential consequences of this vulnerability, categorized by impact area, severity, likelihood, and mitigation strategies.
| Impact Area | Severity | Likelihood | Mitigation |
|---|---|---|---|
| Data Breach | Critical | High (if exploited successfully) | Implement strong access controls, data encryption, and regular security audits. |
| System Compromise | Critical | High (if exploited successfully) | Apply security patches promptly, utilize intrusion detection/prevention systems, and enforce strong password policies. |
| Denial of Service | High | Medium (depending on attacker’s capabilities) | Implement redundancy and failover mechanisms, regularly test disaster recovery plans, and utilize network monitoring tools. |
| Reputational Damage | Medium | Medium (depending on the scale and public disclosure of the breach) | Develop a robust incident response plan, communicate transparently with stakeholders, and engage with public relations professionals. |
Mitigation Strategies and Best Practices
Source: blackhatethicalhacking.com
Addressing the Cisco regression RCE vulnerability requires a multi-pronged approach encompassing immediate patching, robust development practices, and enhanced network security. Failing to implement these strategies leaves organizations vulnerable to exploitation and potential data breaches. This section Artikels the crucial steps to mitigate this risk and prevent future occurrences.
Swift action is key to neutralizing this vulnerability. Patching affected devices is the most immediate and effective countermeasure. Following best practices in software development can significantly reduce the likelihood of similar vulnerabilities arising in the future. Furthermore, implementing robust network security measures can minimize the impact even if an exploit is successful.
Patching Affected Cisco Devices
A step-by-step procedure for patching is crucial. First, identify all affected devices within your network using Cisco’s advisory and your inventory management system. Next, download the appropriate patches from the Cisco website, ensuring they are compatible with your device models and software versions. Before applying the patches, back up your device configurations to prevent data loss in case of unexpected issues. Then, apply the patches according to Cisco’s instructions, carefully following each step. Finally, verify the successful application of the patches by checking the device’s software version and confirming the vulnerability is no longer present. Regularly scheduled patching cycles are also essential for proactive vulnerability management.
Best Practices for Preventing Similar Vulnerabilities
Secure software development practices are paramount in preventing future vulnerabilities. This includes thorough code reviews, robust testing procedures (including penetration testing and fuzzing), and the implementation of static and dynamic code analysis tools. Adopting a secure coding style guide, which addresses common vulnerabilities such as buffer overflows and input validation issues, is also crucial. Regular security audits and vulnerability assessments are needed to proactively identify and address potential weaknesses. Furthermore, using established software development methodologies, like Agile with integrated security practices, can help build security into the development lifecycle from the start.
Security Recommendations for Organizations Using Affected Cisco Products
Organizations utilizing affected Cisco products should prioritize these security recommendations:
- Implement a robust vulnerability management program that includes regular scanning, patching, and reporting.
- Enable strong authentication mechanisms, such as multi-factor authentication, to protect against unauthorized access.
- Regularly review and update access control lists (ACLs) to restrict network access based on the principle of least privilege.
- Monitor network traffic for suspicious activity using intrusion detection and prevention systems (IDS/IPS).
- Employ security information and event management (SIEM) systems to collect and analyze security logs from various sources, allowing for timely detection of potential attacks.
- Educate employees about social engineering techniques and phishing attacks to reduce the risk of human error leading to exploitation.
- Maintain up-to-date antivirus and anti-malware software on all devices connected to the network.
Implementing Network Segmentation
Network segmentation limits the impact of a successful exploit by isolating critical systems and data from less critical ones. This can be achieved through the use of VLANs (Virtual LANs), firewalls, and other network security devices. For instance, separating the corporate network into segments for guest Wi-Fi, employee workstations, and sensitive servers prevents a compromise in one segment from cascading to others. By carefully controlling traffic flow between segments, the potential damage caused by a successful exploit is significantly reduced, containing the breach to a limited area of the network. A well-defined network segmentation strategy, incorporating regular reviews and updates, is vital for mitigating the risks associated with this type of vulnerability.
Vulnerability Disclosure and Coordination
Responsible vulnerability disclosure is a crucial process that balances the need to protect users from security threats with the importance of allowing developers to fix vulnerabilities. It’s a delicate dance requiring careful coordination between security researchers, the affected vendor (in this case, Cisco), and ultimately, the users themselves. A well-executed disclosure minimizes disruption and maximizes the benefit for everyone involved.
The process involves several key players and distinct stages. Cisco, as the vendor, has a responsibility to promptly address vulnerabilities discovered in their products. Security researchers, who discover vulnerabilities, play a vital role in reporting these issues responsibly. Affected users, meanwhile, rely on both Cisco and researchers to act swiftly and effectively to protect their systems.
Cisco’s Role in Vulnerability Disclosure
Cisco’s role centers on receiving vulnerability reports, validating their severity, developing and testing patches, and finally, releasing those patches to the public. Their internal processes should include rigorous testing to ensure the patch doesn’t introduce new problems. They also manage the public communication surrounding the vulnerability, providing clear and concise advisories to users, detailing the vulnerability, its impact, and the steps to mitigate the risk. Transparency is key; timely and accurate information reduces the window of opportunity for malicious actors to exploit the vulnerability. Their adherence to established vulnerability disclosure guidelines, like those from the Forum of Incident Response and Security Teams (FIRST), demonstrates their commitment to responsible practices.
Security Researchers’ Responsibilities
Security researchers play a crucial role in identifying vulnerabilities. Responsible disclosure involves privately reporting the vulnerability to the vendor (Cisco) before publicly revealing the details. This allows Cisco time to develop and release a patch, minimizing the risk of widespread exploitation. Researchers should provide sufficient detail to allow Cisco to reproduce the vulnerability and understand its impact. This includes steps to reproduce the vulnerability, its potential impact, and any relevant evidence. Following established ethical guidelines, such as those published by organizations like the OWASP (Open Web Application Security Project), ensures a responsible and coordinated approach.
Affected Users’ Actions
Affected users should monitor Cisco’s security advisories and promptly apply any released patches. This proactive approach is vital in mitigating the risk of exploitation. Users should also regularly update their systems and software to ensure they have the latest security patches. Keeping systems up-to-date reduces the overall attack surface and minimizes the chance of falling victim to vulnerabilities. In the event of a suspected compromise, users should follow Cisco’s recommended incident response procedures.
Comparing Vulnerability Reporting and Remediation Approaches
Different approaches exist for vulnerability reporting, ranging from fully coordinated private disclosures to immediate public releases (full disclosure). Coordinated private disclosure, favored by many security researchers and vendors, provides a structured timeline for remediation, reducing the risk of widespread exploitation. Full disclosure, on the other hand, is typically reserved for situations where the vendor is unresponsive or where the vulnerability poses an immediate and severe threat. The choice between these approaches involves a careful risk assessment, considering the severity of the vulnerability and the vendor’s responsiveness. The goal is always to minimize the impact on users while still ensuring the vulnerability is addressed.
The Importance of Coordinated Vulnerability Disclosure
Coordinated vulnerability disclosure minimizes the risk of widespread exploitation by giving vendors time to develop and deploy patches. This reduces the window of opportunity for malicious actors, protecting users and systems. It also fosters trust between security researchers and vendors, promoting a more collaborative and effective security ecosystem. A coordinated approach ensures that information is disseminated effectively, allowing users to take appropriate action to protect themselves. This coordinated effort is essential in maintaining a safer digital environment for everyone.
Illustrative Example: A Compromised Device: Cisco Warns Regresshion Rce
Source: patchmypc.com
Imagine a small business, “Coffee Corner,” relying on a Cisco router (let’s call it R1) for its network connectivity and internal security. This router, unfortunately, is running vulnerable firmware affected by the regression RCE. The attack unfolds silently, leaving Coffee Corner blissfully unaware of the impending data breach.
This scenario details how a sophisticated attacker might exploit this vulnerability to compromise R1 and gain access to Coffee Corner’s sensitive data.
Attacker’s Initial Access
The attacker, let’s call him “Mal”, discovers Coffee Corner’s public IP address associated with R1 through a simple Shodan search. Knowing the specific vulnerable firmware version, Mal crafts a malicious packet exploiting the regression RCE. This packet is essentially a cleverly disguised command, designed to execute arbitrary code on R1 once it’s processed. Mal sends this malicious packet to R1, triggering the vulnerability. Because the vulnerability allows remote code execution, no prior authentication or user interaction is needed. The malicious code, once executed, establishes a backdoor on R1, granting Mal persistent access. This backdoor could be a simple reverse shell, allowing Mal to remotely control R1.
Privilege Escalation and Lateral Movement
With initial access secured, Mal now aims to escalate privileges on R1. This involves exploiting any existing vulnerabilities within the router’s operating system or leveraging the initial backdoor to gain root-level access. Once root access is achieved, Mal can gain full control of R1, allowing them to manipulate network configurations, monitor traffic, and potentially access other devices on the Coffee Corner network. The attacker might then move laterally, attempting to compromise other devices connected to the network, such as servers holding customer data or point-of-sale systems. They could achieve this by using techniques like password spraying or exploiting known vulnerabilities in those systems.
Indicators of Compromise (IOCs)
Following a successful attack, several IOCs might indicate a compromise. These include unusual network traffic patterns, such as connections to suspicious IP addresses or unusual amounts of data being exfiltrated. Log files on R1, if not tampered with, might reveal suspicious commands executed or unusual access attempts. Anomalous system processes running on R1 could also be indicative of malicious activity. Furthermore, Coffee Corner might notice unusual performance issues with their network or even the complete loss of internet connectivity if Mal has tampered with the router’s configuration. Finally, unexpected charges on credit cards or customer complaints about data breaches would strongly suggest a compromise. These IOCs, however, might be subtle and easily overlooked without proper security monitoring and logging.
Conclusive Thoughts
In short, Cisco’s regression RCE vulnerability is a serious threat demanding immediate attention. While the patch is available, proactive security measures are crucial. Network segmentation, robust security practices, and staying updated on security advisories are no longer optional—they’re your survival kit. Ignoring this isn’t just risky; it’s reckless. Get patching, folks, before you become the next headline.