Logsign Unified SECOps RCE vulnerabilities: Think your security is airtight? Think again. This isn’t your grandpappy’s SIEM; we’re diving deep into the potential weaknesses lurking within Logsign’s powerful security platform. From identifying entry points for remote code execution attacks to crafting mitigation strategies, we’re pulling back the curtain on the vulnerabilities that could leave your systems wide open. Get ready for a no-holds-barred look at how these vulnerabilities work, their devastating impact, and how to fortify your defenses.
We’ll break down the architecture of Logsign Unified SECOps, explore its key features, and compare it to similar platforms. Then, we’ll dissect potential RCE attack vectors, detailing the steps involved in a typical exploit. This isn’t just theoretical; we’ll offer practical advice on detecting, remediating, and ultimately preventing these vulnerabilities. Think of this as your cheat sheet to securing your Logsign environment.
Logsign Unified SECOps Overview
Source: baeldung.com
Logsign Unified SECOps is a comprehensive security platform designed to streamline and enhance an organization’s security operations. It consolidates various security tools and processes into a single, unified platform, offering a centralized view of an organization’s security posture. This approach aims to improve efficiency, reduce response times to threats, and minimize the complexity often associated with managing disparate security systems.
Logsign Unified SECOps Architecture
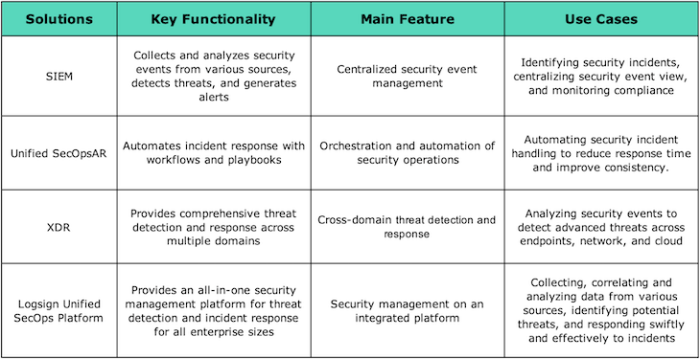
Logsign Unified SECOps employs a modular architecture, allowing organizations to tailor the platform to their specific needs and scale it as their security requirements evolve. The core components typically include a central management console, various security information and event management (SIEM) capabilities, threat intelligence integration, and automated response functionalities. Data from diverse sources, such as firewalls, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions, are ingested, correlated, and analyzed within the platform. This architecture allows for real-time threat detection, incident response, and proactive security measures.
Key Features and Functionalities
Logsign Unified SECOps offers a wide array of features designed to address the multifaceted challenges of modern cybersecurity. These features typically include real-time threat detection and alerting, automated incident response workflows, comprehensive security information and event management (SIEM) capabilities, security orchestration, automation, and response (SOAR) functionalities, and robust reporting and analytics. The platform also often incorporates threat intelligence feeds to proactively identify and mitigate emerging threats. This combination of features aims to provide a holistic and proactive approach to security management.
SIEM Handling in Logsign Unified SECOps, Logsign unified secops rce vulnerabilities
Logsign Unified SECOps’s SIEM capabilities are central to its functionality. The platform collects, normalizes, and correlates security logs from various sources, enabling security analysts to identify patterns and anomalies indicative of malicious activity. Advanced analytics, including machine learning algorithms, are often employed to enhance threat detection accuracy and reduce false positives. The SIEM component facilitates the creation of custom dashboards and reports, providing valuable insights into the organization’s security posture and enabling proactive risk mitigation. Real-time alerts and notifications are crucial elements, ensuring prompt responses to critical security events.
Comparison with Other Similar Platforms
Compared to other similar platforms, Logsign Unified SECOps often distinguishes itself through its focus on ease of use and integration. While other platforms might offer comparable features, Logsign aims to provide a more intuitive user experience and seamless integration with existing security infrastructure. The specific advantages and disadvantages relative to competitors will depend on factors such as the organization’s size, existing infrastructure, and specific security needs. A detailed comparison would require a comprehensive evaluation of individual platform features, performance benchmarks, and customer reviews, which is beyond the scope of this overview. However, Logsign often emphasizes its commitment to providing a user-friendly interface and strong integration capabilities as key differentiators.
Remote Code Execution (RCE) Vulnerabilities in Logsign Unified SECOps
Logsign Unified SECOps, while a powerful security platform, is not immune to the ever-present threat of remote code execution (RCE) vulnerabilities. These vulnerabilities, if exploited, can grant attackers complete control over the system, potentially compromising sensitive data and disrupting operations. Understanding the potential entry points and impact of such attacks is crucial for effective security posture management.
RCE vulnerabilities arise from flaws in the software’s design or implementation, allowing malicious actors to inject and execute arbitrary code on the Logsign Unified SECOps server. This could range from subtle flaws in input validation to more serious vulnerabilities in underlying libraries or components. The consequences of a successful RCE attack can be severe, potentially leading to data breaches, system outages, and complete compromise of the organization’s security infrastructure.
Potential Entry Points for RCE Attacks
RCE attacks against Logsign Unified SECOps could leverage several potential entry points. These might include vulnerabilities in web interfaces, APIs, or even misconfigured integrations with third-party systems. Insufficient input sanitization in any of these areas could allow attackers to inject malicious code. For example, a vulnerable API endpoint accepting user-supplied data without proper validation could be exploited to execute arbitrary commands on the server. Similarly, a flaw in the web interface’s authentication or authorization mechanisms could enable attackers to bypass security controls and gain unauthorized access, potentially leading to RCE. Exploiting a vulnerability in a third-party integration could also provide an indirect path to RCE.
Impact of Successful RCE Exploits
A successful RCE exploit against Logsign Unified SECOps could have devastating consequences. Attackers could gain complete control over the system, allowing them to: steal sensitive data such as logs, security configurations, and user credentials; modify security settings to disable alerts or compromise other security systems; install backdoors for persistent access; and launch further attacks against the organization’s network and systems. The impact could range from minor data breaches to complete disruption of the organization’s security operations, potentially resulting in significant financial losses and reputational damage. Consider a scenario where an attacker gains RCE and disables all security alerts, effectively blinding the organization’s security team.
Examples of Common RCE Vulnerabilities in Similar Security Platforms
Many security platforms, similar to Logsign Unified SECOps, have historically suffered from RCE vulnerabilities. These often stem from insecure coding practices, such as improper input validation, buffer overflows, and use of outdated or vulnerable libraries. For example, vulnerabilities in web application frameworks like Apache Struts or Spring have historically led to widespread RCE exploits in various applications. Another example could be insufficiently secured API endpoints that lack proper authentication and authorization mechanisms. These vulnerabilities often expose the system to attacks like command injection, where malicious code is injected into legitimate commands.
Steps Involved in a Typical RCE Attack
Understanding the typical steps involved in an RCE attack is crucial for implementing effective mitigation strategies.
| Step | Description | Potential Impact | Mitigation |
|---|---|---|---|
| Vulnerability Discovery | Attackers identify a vulnerability (e.g., insecure API endpoint, flawed input validation) in Logsign Unified SECOps. | Potential for unauthorized access and code execution. | Regular security assessments, penetration testing, and code reviews. |
| Exploit Development | Attackers develop an exploit to leverage the identified vulnerability. | Successful exploitation could lead to RCE. | Secure coding practices, input validation, and use of up-to-date libraries. |
| Exploit Execution | Attackers execute the exploit, gaining remote code execution capabilities on the Logsign Unified SECOps server. | Complete system compromise, data breaches, and service disruption. | Strong access controls, network segmentation, and intrusion detection systems. |
| Post-Exploitation Activities | Attackers perform malicious activities, such as data exfiltration, lateral movement, and persistent backdoor installation. | Significant data loss, operational disruption, and long-term security compromise. | Regular security monitoring, log analysis, and incident response planning. |
Vulnerability Detection and Remediation Strategies: Logsign Unified Secops Rce Vulnerabilities
Source: logsign.com
Finding and fixing Remote Code Execution (RCE) vulnerabilities in Logsign Unified SECOps is crucial for maintaining a secure environment. Proactive vulnerability management is key to preventing breaches and data loss. This section details strategies for detection, scanning, prevention, and remediation.
Effective RCE vulnerability detection requires a multi-layered approach combining automated tools with manual code reviews and security best practices. Ignoring even seemingly minor vulnerabilities can have severe consequences. Regular and rigorous testing is paramount.
Vulnerability Detection Methods
Detecting RCE vulnerabilities in Logsign Unified SECOps necessitates a combination of techniques. Static and dynamic application security testing (SAST and DAST) tools can automatically scan for known vulnerabilities. Penetration testing, performed by security experts, simulates real-world attacks to identify exploitable weaknesses. Regular security audits, both internal and external, provide an independent assessment of the system’s security posture. Finally, careful code reviews by experienced developers are essential for identifying subtle vulnerabilities that automated tools might miss. A layered approach significantly increases the likelihood of finding and addressing all vulnerabilities.
Vulnerability Scanning Procedure
A robust vulnerability scanning procedure for Logsign Unified SECOps should be implemented regularly. This procedure should include the following steps:
- Initial Assessment: Conduct a thorough inventory of all Logsign Unified SECOps components and their configurations.
- Automated Scanning: Utilize SAST and DAST tools to scan for known vulnerabilities, paying close attention to any identified RCE risks. Tools like Nessus, OpenVAS, or specialized Logsign-compatible scanners should be used. Regular updates to the vulnerability databases of these tools are crucial for effectiveness.
- Manual Review: Manually review the codebase, focusing on areas identified by automated scans and high-risk functions. This step is vital to identify vulnerabilities that automated tools may miss.
- Penetration Testing: Periodically conduct penetration tests to simulate real-world attacks and identify exploitable vulnerabilities that might be missed by automated scans.
- Reporting and Remediation: Document all identified vulnerabilities and prioritize them based on their severity and likelihood of exploitation. Develop and implement remediation plans for all critical and high-severity vulnerabilities.
Best Practices for Preventing RCE Vulnerabilities
Proactive measures significantly reduce the risk of RCE vulnerabilities. Implementing these best practices is crucial for a robust security posture.
- Input Validation: Strictly validate all user inputs to prevent malicious code injection. Sanitize and escape all data before using it in the application.
- Secure Coding Practices: Follow secure coding guidelines and use parameterized queries to prevent SQL injection vulnerabilities, a common pathway to RCE.
- Least Privilege Principle: Grant only the necessary permissions to users and processes. This limits the impact of a successful attack.
- Regular Updates: Keep all software components, including Logsign Unified SECOps and its dependencies, up-to-date with the latest security patches.
- Regular Security Audits: Conduct regular internal and external security audits to identify and address vulnerabilities before attackers can exploit them. This proactive approach minimizes risk.
- Firewall Configuration: Implement and maintain robust firewall rules to restrict network access to only authorized users and applications.
Remediating an RCE Vulnerability
Remediating an RCE vulnerability requires a systematic approach to ensure the vulnerability is completely eliminated. A quick fix without proper verification can leave the system vulnerable.
- Isolate the affected system: Immediately isolate the affected system from the network to prevent further exploitation.
- Analyze the vulnerability: Thoroughly analyze the vulnerability to understand its root cause and potential impact.
- Develop a remediation plan: Create a detailed remediation plan that addresses the root cause of the vulnerability. This may involve patching, code changes, or configuration updates.
- Implement the fix: Implement the remediation plan carefully, testing thoroughly to ensure it effectively addresses the vulnerability without introducing new issues.
- Verify the fix: After implementing the fix, rigorously test the system to ensure the vulnerability is completely eliminated. Retest using the same methods used to identify the vulnerability.
- Monitor for recurrence: Continuously monitor the system for any signs of recurrence or similar vulnerabilities.
Security Hardening and Best Practices
Proactive security measures are crucial for mitigating the risks associated with Logsign Unified SECOps vulnerabilities, particularly those leading to Remote Code Execution (RCE). A robust security posture involves regular audits, stringent access controls, and the implementation of best practices for user account management. Ignoring these aspects can leave your system vulnerable to exploitation, leading to data breaches and operational disruptions.
Regular security audits are vital for identifying and addressing potential weaknesses before they can be exploited. These audits should encompass a comprehensive review of system configurations, user permissions, and security logs, looking for anomalies and misconfigurations that could compromise the system’s integrity. The frequency of these audits depends on the sensitivity of the data processed and the criticality of the system. For instance, high-security environments might require monthly audits, while others might suffice with quarterly or biannual reviews.
Security Hardening Techniques
Effective security hardening involves implementing a series of protective measures to minimize the attack surface and enhance the system’s resilience against malicious actors. This includes regularly updating the Logsign Unified SECOps software to patch known vulnerabilities, enabling strong password policies, and configuring network firewalls to restrict unauthorized access. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they manage to obtain credentials. Regular vulnerability scanning and penetration testing can also reveal hidden weaknesses that could be exploited.
Access Control and Authentication in Mitigating RCE Vulnerabilities
Robust access control and authentication mechanisms are fundamental to preventing RCE vulnerabilities. By implementing the principle of least privilege, users are granted only the necessary permissions to perform their tasks, limiting the potential damage from a compromised account. Strong password policies, including password complexity requirements and regular password changes, are essential. Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile device. This makes it significantly harder for attackers to gain unauthorized access, even if they manage to obtain a user’s password. Regularly reviewing and updating access control lists (ACLs) ensures that only authorized users and systems have access to sensitive resources.
User Account Management Best Practices
Effective user account management is crucial for maintaining a secure environment. This includes establishing a clear process for creating, modifying, and disabling user accounts. Regularly reviewing and disabling inactive accounts minimizes the potential for compromised accounts to remain active. Implementing strong password policies, enforcing regular password changes, and using MFA significantly enhances security. Additionally, adhering to the principle of least privilege, ensuring users only have access to the resources necessary for their roles, limits the potential impact of a compromised account. Regularly auditing user activity can help detect suspicious behavior and potential security breaches. Proper account management contributes significantly to a more resilient security posture, reducing the risk of unauthorized access and RCE attacks.
Impact Analysis and Mitigation Planning
Source: patchmypc.com
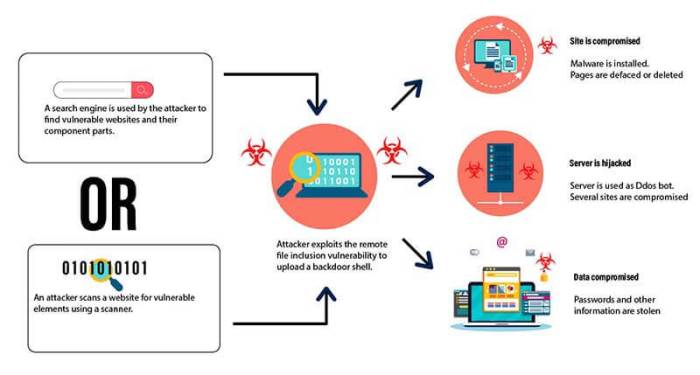
A successful Remote Code Execution (RCE) exploit against Logsign Unified SECOps could have devastating consequences, potentially leading to significant data breaches, service disruptions, and reputational damage. Understanding the potential impact and developing a robust mitigation plan is crucial for minimizing the risk and ensuring business continuity. This section details the potential consequences of an RCE attack, Artikels a mitigation plan, presents a hypothetical attack scenario, and emphasizes the importance of incident response planning.
Potential Consequences of an RCE Exploit
An RCE vulnerability in Logsign Unified SECOps allows attackers to execute arbitrary code on the system. This grants them complete control, enabling them to steal sensitive data like customer information, credentials, and security logs; modify or delete critical system files; install malware; launch further attacks against internal networks; and disrupt the organization’s security monitoring capabilities. The severity depends on the attacker’s skills and objectives. A sophisticated attacker could completely compromise the organization’s security posture, leading to extensive financial losses and legal repercussions. Consider the hypothetical scenario of a financial institution: an RCE exploit could result in the theft of customer banking details, leading to significant financial losses and severe reputational damage.
Mitigation Plan for RCE Attacks
A comprehensive mitigation plan should incorporate several key strategies. Firstly, proactive vulnerability management is essential; regularly update Logsign Unified SECOps to the latest version containing security patches. Secondly, implement strong access control measures, restricting access to the system based on the principle of least privilege. Thirdly, employ robust intrusion detection and prevention systems (IDPS) to monitor for suspicious activities and block malicious traffic. Fourthly, regularly back up critical data to an offline, secure location to enable quick recovery in case of a successful attack. Finally, invest in security awareness training for all personnel to mitigate the risk of social engineering attacks that could lead to RCE exploits.
Hypothetical RCE Attack Scenario and Response
Imagine a scenario where an attacker exploits a known RCE vulnerability in Logsign Unified SECOps via a phishing email containing a malicious attachment. The attacker gains access and installs a backdoor. The immediate response involves isolating the affected system from the network to prevent further lateral movement. Next, a forensic investigation is launched to determine the extent of the compromise and identify the attacker’s actions. All compromised credentials are changed, and the system is thoroughly sanitized and restored from a clean backup. Finally, the vulnerability is patched, and security controls are reviewed and strengthened. The entire incident is documented and lessons learned are incorporated into future security practices.
Importance of Incident Response Planning
A well-defined incident response plan is paramount for effectively handling RCE attacks against Logsign Unified SECOps. Without a plan, reacting to an attack becomes chaotic and inefficient, potentially exacerbating the damage.
A robust incident response plan should include clearly defined roles and responsibilities, communication protocols, escalation procedures, containment strategies, eradication techniques, recovery processes, and post-incident activity review. It must be regularly tested and updated to reflect changes in the organization’s infrastructure and threat landscape.
Logsign Unified SECOps Security Updates and Patches
Staying on top of security updates is crucial for any organization, especially when dealing with a sophisticated system like Logsign Unified SECOps. Ignoring patches leaves your security posture vulnerable, potentially exposing your entire operation to significant risks. Understanding the patching process and its importance is paramount for maintaining a robust and secure environment.
Applying security updates and patches to Logsign Unified SECOps typically involves downloading the latest patch from the official Logsign vendor portal. This portal usually provides detailed release notes, including a description of the fixed vulnerabilities, installation instructions, and potential downtime. The installation process itself can vary depending on the specific update and your deployment environment; some updates may require a simple restart, while others might necessitate a more complex procedure. Always consult the official documentation for your specific version of Logsign Unified SECOps. Thorough testing in a staging environment before applying patches to your production system is highly recommended.
Patching Process Details
The Logsign Unified SECOps patching process usually begins with checking for available updates through the system’s interface or the vendor’s portal. Once updates are identified, a download initiates, followed by an installation process. This process may require a system restart, resulting in temporary downtime. Post-installation, a verification step ensures the patch has been successfully applied and the system is functioning correctly. Regular backups before applying any updates are essential to ensure data recovery in case of unforeseen issues. Logsign may provide detailed step-by-step guides and videos to aid in the process.
Importance of Staying Updated
Staying current with security advisories and patches is paramount to mitigating the risk of exploitation by malicious actors. Outdated software often contains known vulnerabilities that attackers actively exploit. These vulnerabilities can range from minor issues to critical flaws that allow for complete system compromise, including data breaches, service disruptions, and financial losses. Regular updates ensure that these known vulnerabilities are patched, reducing the attack surface and improving the overall security posture. Ignoring updates is akin to leaving your front door unlocked – it’s an open invitation for trouble. For example, the infamous Heartbleed vulnerability (CVE-2014-0160) exposed sensitive data for countless organizations that failed to apply timely patches.
Effectiveness of Patching Strategies
Several patching strategies exist, each with varying degrees of effectiveness. A proactive approach, involving regularly scheduled updates and immediate application of critical patches, offers the best protection. Reactive patching, where updates are applied only after a vulnerability is exploited, is far less effective, leaving the system vulnerable for a potentially extended period. Automated patching systems can significantly improve efficiency and reduce the risk of human error. However, rigorous testing remains crucial, regardless of the chosen strategy, to ensure compatibility and avoid unintended consequences. The optimal strategy often depends on the organization’s risk tolerance, available resources, and the criticality of the system.
Risks of Delaying Security Updates
Delaying security updates exposes your organization to a multitude of risks. The longer a vulnerability remains unpatched, the greater the chance of exploitation. This can lead to data breaches, financial losses, reputational damage, and regulatory fines. Moreover, delayed patching can significantly complicate remediation efforts, making the process more time-consuming and costly. In some cases, delayed patches may even render the system irreparable, necessitating a complete system rebuild. For instance, a delay in patching a critical vulnerability could result in a ransomware attack, leading to significant data loss and operational downtime. The cost of inaction often far outweighs the cost of proactive patching.
Final Review
So, you’ve just journeyed through the wild west of Logsign Unified SECOps RCE vulnerabilities. The good news? Awareness is the first step to a stronger security posture. By understanding the potential risks and implementing the strategies Artikeld here—regular security audits, robust access controls, and a proactive patching regime—you can significantly reduce your attack surface. Remember, staying ahead of the curve is crucial in the ever-evolving landscape of cybersecurity. Don’t just react; proactively protect your systems. Your data (and sanity) will thank you.



