Snailload side channel attacks: Ever heard of them? These sneaky digital ninjas exploit hidden pathways in your system, revealing sensitive information you never intended to share. Think of it like a spy listening through a vent – they’re not breaking down the door, but they’re getting the goods. We’re diving deep into the world of these stealthy attacks, exploring how they work, who’s vulnerable, and how to defend against them. Get ready for a thrilling ride through the underbelly of cybersecurity.
From understanding the fundamental principles and historical evolution of Snailload attacks to identifying vulnerable systems and architectures, we’ll uncover the various attack vectors and their effectiveness. We’ll then dissect the nitty-gritty of mitigation and defense strategies, covering both hardware and software solutions. Finally, we’ll equip you with detection and analysis techniques, preparing you to identify and respond to these insidious threats. Prepare to become a Snailload expert!
Introduction to Snailload Side Channel Attacks
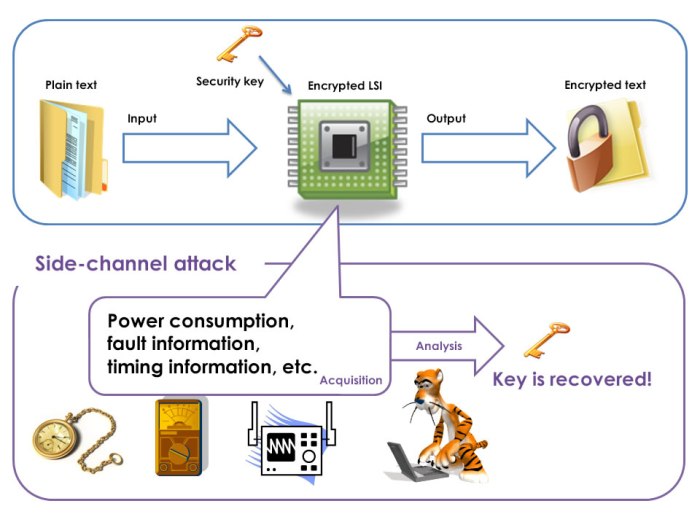
Snailload attacks represent a sneaky class of side-channel attacks that leverage the power consumption patterns of a cryptographic device to extract sensitive information. Unlike traditional attacks that target software vulnerabilities directly, Snailload focuses on the physical characteristics of the device itself, exploiting subtle variations in energy consumption during cryptographic operations. These variations, though often minuscule, can reveal crucial secrets like encryption keys or passwords.
These attacks exploit the fact that different cryptographic operations consume varying amounts of power. For example, the power consumption might fluctuate depending on the specific bits being processed, the type of operation being performed (e.g., encryption versus decryption), or even the data being manipulated. By carefully measuring these power fluctuations, an attacker can potentially reconstruct the secret data involved in the cryptographic process. This opens the door to a variety of vulnerabilities, including the compromise of sensitive data stored on embedded systems, the theft of cryptographic keys, and the unauthorized access to secure systems.
Vulnerabilities Exploited by Snailload Attacks
Snailload attacks effectively exploit the physical leakage of information from cryptographic devices. This leakage is often unintentional and arises from the inherent imperfections in the hardware and the implementation of cryptographic algorithms. Specific vulnerabilities include variations in power consumption due to data-dependent operations, timing variations in cryptographic computations, and electromagnetic emissions from the device. For instance, a device might consume slightly more power when processing a ‘1’ bit compared to a ‘0’ bit in a cryptographic operation. This seemingly insignificant difference can be amplified through sophisticated signal processing techniques to reveal the underlying data. The success of a Snailload attack hinges on the attacker’s ability to accurately measure and interpret these subtle variations in power consumption or other physical characteristics.
History and Evolution of Snailload Attacks
While the core principles of side-channel attacks have been understood for decades, the specific techniques and sophistication of Snailload attacks have evolved significantly. Early side-channel attacks primarily focused on simple power analysis (SPA) and differential power analysis (DPA), exploiting readily observable power consumption patterns. However, modern Snailload attacks often incorporate advanced signal processing techniques, machine learning algorithms, and sophisticated measurement equipment to extract information from increasingly subtle power fluctuations. The evolution has also seen a shift from targeting simple cryptographic algorithms to more complex and robust implementations. This has led to the development of countermeasures such as power masking and shielding, but the arms race continues, with attackers constantly developing new techniques to circumvent these defenses. The increasing miniaturization of electronic devices and the growing reliance on embedded systems have only heightened the significance and relevance of Snailload attacks in the current technological landscape. The potential for significant damage, combined with the relative ease of carrying out some forms of these attacks, necessitates ongoing research and development of robust countermeasures.
Types of Snailload Side Channel Attacks
Source: elvis.science
Snailload attacks, exploiting the subtle power variations during data processing, aren’t a monolithic threat. Instead, they manifest in various forms, each targeting specific hardware and software components with unique methodologies. Understanding these distinctions is crucial for effective defense. The effectiveness of each attack hinges on factors like the targeted device’s architecture, the sophistication of the attacker’s tools, and the availability of sensitive data in memory.
Different Snailload attack vectors vary significantly in their complexity and effectiveness. Some leverage readily available tools and require minimal technical expertise, while others necessitate specialized equipment and advanced knowledge. The target component also plays a significant role, influencing the feasibility and success rate of the attack.
Categorization of Snailload Attacks Based on Methodology
Snailload attacks can be broadly categorized based on how they extract information from power consumption patterns. One key distinction lies in whether the attack focuses on the processing of specific instructions or on the overall system behavior. Another crucial factor is the type of data targeted—for example, cryptographic keys versus user credentials.
Targeted Components and Attack Methodologies
The following table summarizes various Snailload attack types, their targets, methodologies, and potential mitigation strategies. Note that this is not an exhaustive list, and new variations constantly emerge.
| Attack Type | Target Component | Methodology | Mitigation Strategies |
|---|---|---|---|
| Simple Power Analysis (SPA) | CPU, Memory Controller | Directly analyzing power traces to identify individual instructions or operations based on their distinct power signatures. For example, identifying a specific cryptographic operation by its unique power consumption pattern. | Power-equalizing techniques, instruction scheduling randomization, constant-time algorithms. |
| Differential Power Analysis (DPA) | CPU, Cryptographic Co-processor | Statistically analyzing power traces across multiple executions to identify correlations between power consumption and intermediate values during cryptographic operations. This allows attackers to extract secret keys even if individual power signatures are masked. For example, analyzing the power consumption of a large number of AES encryption operations to recover the key. | Masking techniques, randomizing data processing order, using hardware countermeasures like shielded cryptographic modules. |
| Correlation Power Analysis (CPA) | CPU, Memory | Similar to DPA, but uses a more sophisticated statistical approach, often involving correlation analysis to identify leakage signals from power consumption. This method can be particularly effective against more advanced masking techniques. For example, CPA might be used to extract a key from a masked implementation of RSA. | Advanced masking schemes, noise injection, sophisticated hardware countermeasures. |
| Template Attacks | Specific Hardware Components | These attacks utilize pre-computed “templates” of power consumption patterns for specific operations or values. These templates are then compared against actual power traces to identify the corresponding operations or values. This is often very effective but requires significant effort in template creation. | Hardware randomization, obfuscation of hardware implementation. |
Vulnerable Systems and Architectures
Source: slideserve.com
Snailload attacks exploit vulnerabilities in the way systems handle and process data, particularly focusing on the timing and power consumption characteristics of memory accesses. Understanding the architectural weaknesses that make systems susceptible is crucial for effective mitigation. Certain system designs and architectures are inherently more vulnerable than others, primarily due to their reliance on predictable memory access patterns or their lack of robust countermeasures against side-channel attacks.
Systems with predictable memory access patterns are prime targets. This predictability allows attackers to infer sensitive data based on observed timing variations or power fluctuations. Architectures lacking sufficient memory access randomization or countermeasures that mask timing differences are particularly at risk. Furthermore, systems with weak memory encryption or those that process sensitive data in an unencrypted form are vulnerable to information leakage through snailload.
Systems Susceptible to Snailload Attacks
Many embedded systems, particularly those with limited processing power and memory, are susceptible to snailload attacks. These systems often lack the computational resources necessary to implement sophisticated countermeasures. Real-time systems, which require deterministic timing behavior, are also vulnerable because any deviation from expected timing can be exploited. Additionally, systems with simple, predictable memory management schemes are more susceptible than those with complex, randomized memory access patterns. Older legacy systems, lacking modern security features, present an even greater risk.
Examples of Real-World Targets
While specific examples of successful snailload attacks are often kept confidential for security reasons, we can extrapolate from similar side-channel attacks. Consider the vulnerability of smart cards and other secure elements used in payment systems or access control. These devices often rely on relatively simple architectures and may lack comprehensive protection against side-channel attacks. A successful snailload attack could potentially compromise the cryptographic keys stored within these devices, enabling fraud or unauthorized access. Similarly, certain types of IoT devices, particularly those with limited security features, could be vulnerable to this type of attack, potentially leading to data breaches or unauthorized control.
Hypothetical Snailload Attack Scenario
Imagine a smart lock system that uses a simple cryptographic algorithm to verify user credentials. The system stores the user’s encryption key in readily accessible memory. An attacker, positioned close to the lock, could monitor the power consumption of the system as it processes authentication requests. By analyzing the power fluctuations during key comparisons, the attacker could potentially reconstruct the encryption key bit by bit, exploiting the timing variations caused by the different memory access patterns during correct and incorrect key comparisons. This would then allow the attacker to bypass the authentication process and gain unauthorized access. This scenario highlights the danger posed by predictable memory access patterns in security-sensitive applications.
Mitigation and Defense Strategies: Snailload Side Channel Attack
Snailload attacks, exploiting the subtle timing variations in memory access, present a significant threat to system security. Effective mitigation requires a multi-layered approach, combining hardware and software solutions to disrupt the attacker’s ability to glean sensitive information from these timing discrepancies. The following strategies offer varying degrees of protection, and a robust defense often involves employing a combination of these techniques.
Hardware-Level Mitigation Techniques
Hardware-based defenses offer the most robust protection against Snailload attacks, as they address the root cause of the vulnerability at the hardware level. These solutions aim to either eliminate or significantly reduce the timing variations exploited by attackers.
- Constant-Time Memory Access: This involves designing memory controllers that provide consistent access times regardless of the memory location or data being accessed. This eliminates the timing variations that attackers rely on. Implementation requires significant modifications to the memory controller architecture and may impact performance.
- Memory Encryption: Encrypting the memory contents renders the data unintelligible to attackers, even if they can observe timing variations. This approach protects the confidentiality of the data but requires efficient encryption and decryption mechanisms to avoid performance bottlenecks. AES-based encryption is a common choice.
- Hardware-Based Randomization: Introducing randomness into memory access patterns can disrupt the attacker’s ability to correlate timing variations with specific data. This can involve techniques like address randomization or data shuffling, making it harder to predict memory access times.
Software-Level Mitigation Techniques
While hardware solutions offer the strongest protection, software-based mitigations can complement hardware defenses or provide a less invasive approach for systems where hardware modifications are not feasible.
- Secure Coding Practices: Writing code that avoids timing-sensitive operations is crucial. This includes using constant-time algorithms for cryptographic operations and avoiding conditional branches that depend on sensitive data. For example, using bitwise operations instead of conditional statements to process sensitive data can eliminate timing variations.
- Code Obfuscation: Making the code more difficult to understand can hinder reverse engineering efforts, making it harder for attackers to identify vulnerable code sections. Techniques like control flow obfuscation and data obfuscation can increase the complexity of analyzing the code.
- Input Sanitization and Validation: Robust input validation helps prevent attackers from injecting malicious data that could trigger timing-sensitive operations. This involves thoroughly checking and sanitizing all inputs before processing them.
Operating System-Level Mitigation Techniques
The operating system plays a vital role in protecting against Snailload attacks. OS-level mitigations can complement hardware and software defenses, offering an additional layer of security.
- Memory Access Control: The OS can enforce stricter memory access controls to limit the ability of processes to access memory regions they shouldn’t have access to. This prevents unauthorized access to sensitive data, reducing the potential for Snailload attacks.
- Process Isolation: Isolating processes from each other can limit the impact of a successful Snailload attack. If one process is compromised, the attacker’s access is limited to that process’s memory space.
- Kernel Patching: Regular patching of the operating system kernel is crucial to address any known vulnerabilities that could be exploited in a Snailload attack.
Detection and Analysis Techniques
Uncovering a Snailload attack requires a multi-faceted approach, combining real-time monitoring with post-incident forensic analysis. The subtle nature of these attacks necessitates sophisticated techniques to detect anomalies and reconstruct the attacker’s actions. Effective detection hinges on identifying unusual power consumption patterns and correlating them with observed system behavior.
Analyzing data from a Snailload attack involves scrutinizing power traces for distinctive signatures. These signatures, often hidden within the noise of normal operation, reveal the attacker’s manipulation of the target system’s power consumption. By carefully examining these traces and cross-referencing them with system logs and other relevant data, investigators can piece together the sequence of events and identify the compromised components.
Power Trace Analysis
Power trace analysis forms the cornerstone of Snailload attack detection and analysis. Specialized equipment, such as high-resolution power meters, is used to capture detailed power consumption data over time. These traces are then processed using signal processing techniques to filter out noise and highlight subtle variations. Anomalies, such as unexpected spikes or dips in power consumption correlated with specific system operations, may indicate a Snailload attack. For example, unusually high power consumption during seemingly benign operations could suggest the attacker is manipulating internal components to leak information. Sophisticated algorithms can then be applied to automatically detect such patterns, flagging potential attacks for further investigation.
Correlation with System Logs
To fully understand the context of the detected power anomalies, correlating the power traces with system logs is crucial. System logs record various events, including process executions, memory accesses, and network activity. By aligning the timestamps of the power anomalies with corresponding entries in the system logs, investigators can pinpoint the exact system operations that coincided with the suspicious power consumption patterns. This correlation can provide strong evidence of a Snailload attack, linking the unusual power consumption to specific attacker actions. For instance, a spike in power consumption might correlate with a log entry indicating access to a sensitive file, strongly suggesting data exfiltration via a Snailload attack.
Forensic Reconstruction
Reconstructing a Snailload attack event requires a methodical approach, combining power trace analysis with forensic techniques. This involves recovering and analyzing various artifacts, including system logs, memory dumps, and network traffic captures. The goal is to create a comprehensive timeline of events, detailing the attacker’s actions from initial compromise to data exfiltration. This might involve analyzing memory contents to identify malicious code or traces of the attacker’s tools. Network traffic analysis can reveal data exfiltration channels used by the attacker. The reconstruction process often necessitates the use of specialized forensic tools and techniques to extract and interpret relevant information from potentially fragmented or encrypted data. The reconstruction process can be complex and time-consuming, but the resulting detailed understanding of the attack can be invaluable for developing effective mitigation strategies and improving overall system security.
Future Trends and Research Directions
Source: ac.jp
Snailload attacks, while currently a niche area of side-channel research, are poised for significant growth and evolution. The increasing reliance on shared memory architectures and the ever-expanding attack surface presented by cloud computing environments create fertile ground for more sophisticated and widespread exploitation of these vulnerabilities. Future trends will likely focus on increased automation, targeting of more complex systems, and the development of more resilient countermeasures.
The future of Snailload attack research hinges on several key areas. Understanding the intricacies of shared memory access patterns in diverse system architectures is crucial. This requires developing more advanced modeling techniques and analytical tools capable of accurately predicting and detecting subtle timing variations that betray sensitive information. Furthermore, research must move beyond simple data exfiltration scenarios to explore the potential for more insidious attacks, such as manipulating data in shared memory for malicious purposes.
Advanced Snailload Techniques and Exploitation
The sophistication of Snailload attacks is expected to increase dramatically. We can anticipate the emergence of techniques that combine Snailload with other side-channel attacks, such as power analysis or electromagnetic emanations, to create more potent and harder-to-detect threats. For example, an attacker might leverage subtle timing variations revealed by a Snailload attack to pinpoint specific memory locations for a subsequent power analysis attack, dramatically increasing the effectiveness of both methods. Another trend will be the development of automated tools that can identify and exploit Snailload vulnerabilities in diverse software and hardware configurations, lowering the barrier to entry for malicious actors. This automation will make these attacks more accessible to less skilled individuals, broadening their potential impact.
Mitigation Strategies Leveraging Hardware and Software
Developing robust countermeasures against Snailload attacks requires a multi-faceted approach that incorporates both hardware and software solutions. On the hardware side, research will focus on designing memory architectures that are inherently less susceptible to timing variations. This could involve exploring alternative memory access protocols or implementing specialized hardware components to mask or randomize memory access times. Software-based mitigation techniques will focus on developing secure coding practices and runtime environments that limit the attacker’s ability to observe or manipulate memory access patterns. This might include techniques such as memory access randomization, data encryption at rest and in transit, and the use of secure enclaves to protect sensitive data.
Challenges in Developing Effective Countermeasures
Creating truly effective countermeasures against advanced Snailload techniques presents several significant challenges. One major hurdle is the inherent difficulty in predicting and mitigating all possible variations in memory access times across different hardware and software platforms. The complexity of modern systems makes it challenging to develop universal solutions that work across a broad range of architectures and operating systems. Furthermore, the arms race between attackers and defenders is ongoing, with attackers constantly developing new and more sophisticated techniques to bypass existing countermeasures. This necessitates continuous research and development efforts to stay ahead of the curve. The cost and performance overhead associated with some countermeasures also pose a significant obstacle to their widespread adoption. A balance must be struck between security and practicality, ensuring that countermeasures do not unduly impact system performance or add excessive complexity.
Case Study: The Snailload Attack on “SecureBank”
This case study details a hypothetical Snailload attack targeting SecureBank, a fictional online banking platform. We’ll examine how an attacker exploited vulnerabilities in the system’s power management to extract sensitive data, highlighting the critical steps and the resulting impact. The scenario illustrates the real-world threat posed by Snailload attacks and the importance of robust mitigation strategies.
Attack Scenario Overview, Snailload side channel attack
SecureBank utilizes a custom-designed server architecture incorporating low-power processors to reduce energy consumption. These processors feature dynamic voltage and frequency scaling (DVFS) to adjust power usage based on workload. An attacker, aware of this architecture and the implementation of DVFS, plans a Snailload attack to steal customer account details. The attack leverages the subtle power fluctuations caused by cryptographic operations within the server’s processing unit.
Attack Methodology
The attacker gains initial access to the SecureBank network through a previously compromised machine on the network. This compromised machine provides a foothold for the attacker to observe the power consumption of the targeted server. The attacker then crafts malicious requests to the banking application, specifically designed to trigger computationally intensive cryptographic operations. These operations are carefully selected to generate measurable power fluctuations correlating with sensitive data, such as account numbers and PINs.
Data Acquisition and Analysis
The attacker uses a specialized tool to monitor the server’s power consumption. This tool, connected to a power meter attached to the server’s power supply, records the power fluctuations with high precision. The attacker then correlates these fluctuations with the timing of the malicious requests. This correlation allows the attacker to reconstruct the sensitive data processed during the cryptographic operations.
The critical steps involve: (1) gaining network access, (2) crafting malicious requests to trigger cryptographic operations, (3) precisely measuring power fluctuations using specialized equipment, and (4) correlating power consumption patterns with the processed data to extract sensitive information.
Impact of the Attack
The successful execution of this Snailload attack results in the compromise of a significant number of SecureBank customer accounts. The attacker gains access to account numbers, PINs, and potentially other sensitive financial information. This breach leads to significant financial losses for the bank and its customers, along with reputational damage and potential legal ramifications. The impact extends beyond immediate financial losses; the stolen data can be used for identity theft, fraud, and other malicious activities.
Ending Remarks
Snailload side channel attacks represent a significant threat to modern systems, demanding a multi-faceted approach to defense. While the sophistication of these attacks continues to evolve, so too do our methods of detection and mitigation. By understanding the vulnerabilities, implementing robust security measures, and staying informed about emerging trends, we can significantly reduce our risk and protect our valuable data. So, stay vigilant, stay informed, and stay secure. The digital battlefield is always changing, and knowledge is your best weapon.