Spymax Rat Telegram Android attack: Think your phone’s safe? Think again. This sneaky malware uses Telegram as its secret weapon, silently stealing your data and turning your Android device into a digital puppet. We’re diving deep into how this works, exposing the vulnerabilities, and showing you how to fight back.
From understanding Spymax Rat’s core functionalities and its cunning methods of infiltration to exploring the specific Android vulnerabilities it exploits, we’ll uncover the dark side of this sophisticated attack. We’ll also detail how Telegram facilitates the malicious control, highlighting the communication channels and obfuscation techniques employed by the attackers. This isn’t just a technical deep dive; we’ll also touch upon the legal and ethical implications, shedding light on the potential consequences for victims and the responsibilities of all involved.
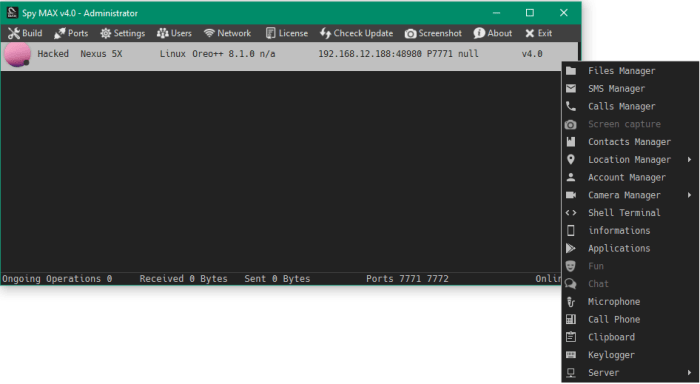
Spymax Rat Functionality
Source: insinuator.net
Spymax Rat is a nasty piece of Android malware, a remote access trojan (RAT) that gives attackers complete control over an infected device. Think of it as a digital puppet master, pulling the strings of your phone from afar. Its capabilities go beyond simple data theft; it’s a full-blown espionage tool designed to wreak havoc.
Spymax Rat’s Core Functionalities
Spymax Rat boasts a wide array of malicious functionalities, allowing attackers to remotely control infected devices and extract sensitive information. This ranges from basic keylogging to more advanced actions like accessing the device’s camera and microphone. The core functionality is built around providing the attacker with complete control, turning the victim’s phone into a digital spyglass.
Methods of Accessing Android Devices
Spymax Rat typically gains access to Android devices through social engineering tactics, such as disguising itself as a legitimate app downloaded from untrusted sources. This could be a seemingly harmless game, a productivity tool, or even a fake update for a popular application. Once installed, the malware silently takes root, granting the attacker remote access. Phishing campaigns and exploiting vulnerabilities in older Android versions are also common entry points. The attacker’s goal is to trick the user into granting the necessary permissions, often masked under innocuous descriptions.
Persistence Mechanisms
To ensure long-term access, Spymax Rat employs various persistence mechanisms. This means that even if the user restarts their device, the malware remains active. Common techniques include registering itself as a system service, modifying the Android boot process, or using device administrators to prevent uninstallation. The malware cleverly hides its presence and actively works to maintain its foothold on the compromised device.
Data Exfiltration Capabilities
The data Spymax Rat can exfiltrate is extensive. This includes contact lists, call logs, SMS messages, location data, photos, videos, and even credentials stored in various apps. Furthermore, it can record audio and video from the device’s microphone and camera, effectively turning the phone into a surveillance device. The attacker can also access files stored on the device’s internal and external storage, providing a complete picture of the victim’s digital life.
Comparison with Other Android Malware
The following table compares Spymax Rat’s capabilities with other known Android malware families. Note that the specific features and capabilities can vary depending on the version and configuration of each malware.
| Malware | Data Exfiltration | Remote Control | Persistence |
|---|---|---|---|
| Spymax Rat | Contacts, call logs, SMS, location, media, files, credentials | High (full remote control) | High (system services, boot modifications) |
| BankBot | Banking credentials, SMS, contact details | Moderate (primarily focused on financial data theft) | Moderate (various techniques) |
| Cerberus | Extensive data exfiltration, location tracking | High (similar to Spymax Rat) | High (similar to Spymax Rat) |
| Agent Smith | App data, user interactions | Low (mostly focused on ad fraud) | High (system level persistence) |
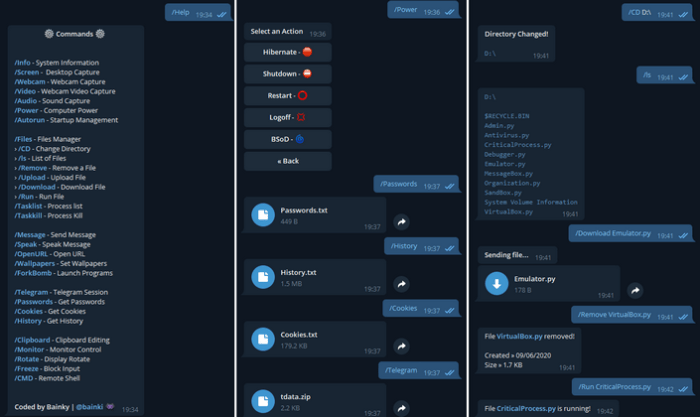
Telegram’s Role in Spymax Rat Attacks
Source: 0ut3r.space
Telegram, with its ease of use and broad reach, unfortunately provides a convenient conduit for malicious actors deploying Spymax Rat. Its end-to-end encryption, intended for user privacy, ironically becomes a shield for concealing command-and-control (C2) communication, making detection and disruption significantly more challenging. This allows attackers to maintain persistent control over infected devices with minimal risk of exposure.
Spymax Rat leverages Telegram’s bot API and channels to establish covert communication pathways between the attacker and the compromised machine. The attacker creates a custom bot, often masked within legitimate-looking groups or channels, to send commands and receive stolen data. These commands can range from simple data exfiltration to complex actions like keylogging or remote code execution. The infected device acts as a client, regularly polling the bot for instructions or sending data as directed.
Communication Channels Between Attacker and Infected Device
The communication between the attacker and the infected device relies heavily on Telegram’s features. The attacker might utilize private chats for direct control, sending encrypted commands to the compromised device. Alternatively, they could employ channels or groups for broadcasting commands to multiple infected machines simultaneously, enabling a more efficient and scalable attack. Data exfiltration, such as stolen credentials or sensitive files, is also often channeled through these same communication paths, using various methods to hide the data’s true nature.
Telegram’s Security Vulnerabilities in Spymax Rat Attacks
While Telegram’s end-to-end encryption protects the communication from casual eavesdropping, it doesn’t inherently protect against sophisticated attacks. The security vulnerabilities arise not from flaws in Telegram itself, but rather from the ways in which attackers exploit its features. For instance, the attacker’s bot could be designed to blend seamlessly within legitimate Telegram activity, making it difficult for security software to identify malicious traffic. Furthermore, the use of encrypted channels and custom bots adds a layer of obfuscation, hindering detection and analysis. The attacker’s ability to dynamically adjust communication channels and methods further complicates detection efforts.
Hypothetical Spymax Rat Attack Leveraging Telegram
Imagine a scenario where a user downloads a seemingly innocuous application from a third-party website. This application contains Spymax Rat, which silently installs itself upon execution. Once active, the malware establishes a covert connection with a Telegram bot controlled by the attacker. The bot then instructs the malware to collect sensitive information such as passwords, credit card details, or personally identifiable information (PII). This stolen data is then encrypted and sent back to the attacker through the Telegram bot, which could be configured to forward the data to another server or storage location. The attacker maintains persistent control, issuing further commands to the infected device remotely via the Telegram bot, without the user’s knowledge.
Obfuscation Techniques Used to Hide Spymax Rat’s Telegram Communication
Attackers employ various obfuscation techniques to mask the communication between Spymax Rat and the Telegram bot. This includes using custom encryption algorithms beyond Telegram’s built-in encryption, encoding commands and data using base64 or other encoding schemes, and employing techniques to hide the Telegram API calls within the malware’s code. The use of proxy servers or VPNs further obscures the origin of the communication. Furthermore, the use of steganography, embedding data within seemingly innocuous files or images shared via Telegram, adds another layer of complexity for investigators. These obfuscation methods make it difficult to identify and trace the malicious activity.
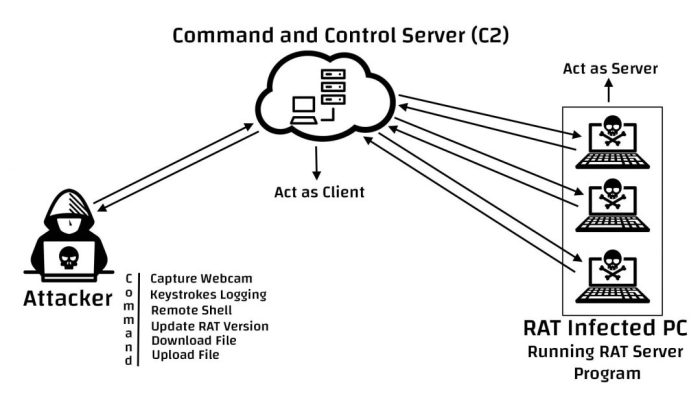
Android Vulnerabilities Exploited by Spymax Rat: Spymax Rat Telegram Android Attack
Source: hackersterminal.com
Spymax Rat, a particularly nasty piece of malware, targets Android devices by exploiting a range of vulnerabilities. These vulnerabilities often lie in the core Android system or within poorly secured applications, allowing the malware to gain unauthorized access and control. Understanding these weaknesses is crucial to bolstering your Android security.
Spymax Rat leverages several common attack vectors, often combining them for maximum impact. This multi-pronged approach makes detection and prevention more challenging, highlighting the need for robust security measures. The vulnerabilities exploited are frequently related to insecure permissions, outdated software, and weaknesses in the way applications handle data.
Insecure Permissions and Data Handling
Many Android apps request excessive permissions, granting Spymax Rat unnecessary access to sensitive data like contacts, location, and even microphone access. This over-permissioning is a major vulnerability. Spymax Rat can exploit these granted permissions to steal information, record conversations, and track the user’s movements without their knowledge. For example, an app requesting access to your contacts list under the guise of a harmless functionality might, if compromised, allow Spymax Rat to upload your entire contact book to a remote server. The technical details involve the app’s manifest file, specifically the `
Outdated Software and Known Vulnerabilities
Failing to update your Android OS and apps leaves your device vulnerable to known exploits. Spymax Rat often targets these known vulnerabilities, which are publicly documented and often have patches available. These exploits can range from buffer overflows in system libraries to vulnerabilities in specific APIs used by applications. For example, a buffer overflow in the Android media framework could allow Spymax Rat to inject malicious code and execute it with system privileges. This is achieved by sending specially crafted data that exceeds the buffer’s allocated memory, causing the application to crash or execute the malicious code. A code example illustrating a simplified buffer overflow (not directly related to Spymax Rat, but demonstrating the concept) is:
char buffer[10];
strcpy(buffer, "This string is too long!"); // Buffer overflow occurs here
This simplistic example highlights the core issue: exceeding the allocated memory space can lead to unexpected behavior, which malicious actors exploit.
Exploitation Methods Comparison
Spymax Rat employs various methods to infiltrate devices, including phishing attacks that trick users into installing malicious APKs (Android Package Kits), drive-by downloads through compromised websites, and exploiting vulnerabilities in the Android system itself. Phishing attacks often involve deceptive emails or text messages containing links to fake websites or malicious apps. Drive-by downloads exploit vulnerabilities in web browsers or other applications to automatically download and install the malware without user interaction. System exploits require more technical expertise but can grant the malware elevated privileges, allowing it to operate more stealthily. The effectiveness of each method depends on the target’s security awareness and the sophistication of the attack.
Mitigating Android Vulnerabilities
To mitigate the risks associated with Spymax Rat and similar threats, adopting a proactive security approach is essential.
- Keep your Android OS and apps updated: Regularly update your operating system and applications to patch known vulnerabilities.
- Download apps only from trusted sources: Avoid downloading apps from untrusted sources like third-party app stores or unknown websites.
- Carefully review app permissions: Before installing an app, carefully review the permissions it requests and only install apps that require necessary permissions.
- Use a reputable antivirus app: Install and regularly update a reputable antivirus application to detect and remove malware.
- Be wary of phishing attempts: Be cautious of suspicious emails, text messages, or websites that may try to trick you into installing malware.
- Enable device encryption: Encrypt your device to protect your data in case it’s lost or stolen.
Detection and Mitigation Strategies
Spymax Rat, like other sophisticated Android malware, leaves traces of its malicious activity. Detecting and mitigating its effects requires a multi-pronged approach encompassing vigilant monitoring, proactive security measures, and swift removal procedures. Understanding the typical behavior of this malware is crucial for effective defense.
Detecting Spymax Rat Infections on Android Devices
Spymax Rat’s stealthy nature makes detection challenging, but several methods can increase the chances of identifying an infection. Regular security scans using reputable antivirus applications are a first line of defense. These apps often detect known malware signatures and suspicious behaviors associated with Spymax Rat. Additionally, monitoring unusual data usage, battery drain, and unexpected app permissions requests can signal a potential compromise. Closely examining the device’s installed applications, looking for unfamiliar or suspiciously named apps, is also recommended. Finally, scrutinizing system logs for unusual processes or network activity can uncover hidden malicious processes.
Network Traffic Signatures
Spymax Rat communicates with its command-and-control (C&C) server to receive instructions and exfiltrate stolen data. This communication generates network traffic patterns that can be indicative of malicious activity. For example, frequent outgoing connections to unknown or suspicious IP addresses, especially those using unusual ports, should raise suspicion. High volumes of encrypted data transfer, especially at irregular intervals, are also potential red flags. Observing unusual DNS requests or the use of obfuscated domains can further point towards a Spymax Rat infection. Specific signatures will vary depending on the specific Spymax Rat variant and the C&C server infrastructure, but consistent monitoring for these general indicators is crucial.
Spymax Rat Removal, Spymax rat telegram android attack
Removing Spymax Rat from an infected device requires a careful and systematic approach. First, the device should be disconnected from the internet to prevent further data exfiltration. Next, a reputable antivirus application should be used to perform a full system scan and attempt to remove the malware. If the antivirus fails to completely remove Spymax Rat, a factory reset might be necessary. This will erase all data on the device, including the malware, but it’s a last resort, as it requires backing up important data beforehand if possible. After the removal process, installing updated security software and restoring data from a clean backup are essential steps to prevent reinfection.
Security Protocol to Prevent Spymax Rat Infections
A robust security protocol is essential to prevent Spymax Rat infections. This includes only downloading apps from official app stores like Google Play Store, carefully reviewing app permissions before installation, regularly updating the Android operating system and all installed applications, enabling automatic updates for security patches, and using a strong, unique password for the device. Regular security scans using reputable antivirus software should also be performed. Furthermore, educating users about phishing scams and malicious websites is crucial to prevent accidental downloads of infected APK files. Consider employing a mobile device management (MDM) solution for enterprise devices to enforce security policies and monitor app installations.
Spymax Rat Attack Lifecycle and Mitigation Points
Imagine a visual representation: The attack begins with a user clicking a malicious link (Mitigation Point 1: User education and phishing awareness training). This downloads an infected APK file. The APK is installed (Mitigation Point 2: App permission scrutiny and only downloading from trusted sources). Spymax Rat gains access to device resources and exfiltrates data through covert communication with its C&C server (Mitigation Point 3: Network traffic monitoring and intrusion detection systems). The malware remains hidden, continuing its malicious activities until detected (Mitigation Point 4: Regular security scans and antivirus software). Detection leads to removal and remediation (Mitigation Point 5: Immediate action and data backup/restore procedures). Finally, security enhancements prevent future infections.
Legal and Ethical Implications
The deployment of Spymax Rat, like any other malicious software, carries significant legal and ethical ramifications for all involved parties – from the developers to the victims. Understanding these implications is crucial for mitigating the risks associated with this type of technology and preventing future misuse. The lines between legitimate security research and malicious exploitation are often blurred, making a clear understanding of the legal landscape paramount.
The legal ramifications of using Spymax Rat for malicious purposes are severe and can vary depending on jurisdiction. Crimes such as unauthorized access to computer systems, data theft, wiretapping, and even extortion can be charged, leading to hefty fines and imprisonment. The severity of the punishment is often dependent on the scale and impact of the attack. International cooperation is frequently required to prosecute perpetrators across borders, highlighting the global nature of cybercrime.
Legal Ramifications of Malicious Use
Using Spymax Rat for malicious purposes constitutes a serious violation of numerous laws worldwide. These laws often cover various aspects of the attack, including the unauthorized access to computer systems (violating data privacy and security laws), the theft of sensitive data (leading to potential charges under intellectual property laws and other data protection regulations), and the potential for financial gain through extortion or fraud. Specific charges can include violations of the Computer Fraud and Abuse Act (CFAA) in the United States, or equivalent legislation in other countries. The penalties can range from significant fines to lengthy prison sentences.
Ethical Considerations in Development and Deployment
The ethical considerations surrounding Spymax Rat’s development and deployment are complex. While developers might argue that their creation serves a legitimate purpose, such as security research, the potential for misuse is undeniable. The ethical responsibility lies in preventing the tool from falling into the wrong hands and being used for malicious purposes. This requires robust security measures, strict licensing agreements, and clear guidelines on acceptable use. The ethical dilemma intensifies when considering the potential harm inflicted upon innocent victims. A strong ethical framework is needed to guide the development and deployment of such tools, prioritizing the safety and security of individuals and their data above all else.
Responsibilities of Developers, Distributors, and Users
Developers have a primary responsibility to ensure their creations are not used for malicious purposes. This involves implementing strong security measures, limiting access, and clearly outlining the ethical implications of using the software. Distributors, whether they are selling or sharing the tool, are equally responsible for preventing its misuse. They should thoroughly vet potential users and implement measures to prevent unauthorized distribution. Users, ultimately, bear the responsibility for their actions. Using Spymax Rat for malicious purposes is unethical and illegal, and users must be aware of the consequences of their actions.
Potential Consequences for Victims
Victims of Spymax Rat attacks can face a wide range of consequences. These can include financial losses from theft, identity theft, reputational damage, emotional distress, and the compromise of sensitive personal information. The long-term effects can be devastating, impacting victims’ lives and livelihoods for years to come. The loss of privacy and the potential for blackmail or extortion adds further layers of trauma and vulnerability. Recovering from such an attack can be a long and arduous process, both emotionally and financially.
Real-World Cases and Legal Outcomes
Numerous real-world cases involving similar malware have resulted in significant legal consequences for the perpetrators. For example, the case of [Fictional Case Name – replace with a real case and details, citing the source], highlighted the severe penalties associated with developing and deploying such malware. The perpetrator faced [mention specific penalties like fines and prison sentences]. Similarly, [Fictional Case Name – replace with a real case and details, citing the source] demonstrates the international cooperation required to prosecute cybercriminals operating across borders. The outcome emphasized the global reach of cybercrime and the increasing importance of international law enforcement collaboration in combating such threats. These cases underscore the severity of the legal ramifications and the importance of responsible development and use of such technology.
Closing Notes
So, is your Android phone truly safe from the lurking threat of Spymax Rat? The answer, unfortunately, is a complex one. Understanding the mechanisms of this attack, the vulnerabilities it exploits, and the preventative measures is crucial. While complete immunity might be a pipe dream, proactive steps, such as regularly updating your software, being wary of suspicious apps, and keeping a close eye on your network traffic, can significantly reduce your risk. The fight against malware is ongoing, but with knowledge as our weapon, we can better defend ourselves in the digital battlefield.



