Indirector side channel attacks are the sneaky ninjas of the cybersecurity world, silently extracting sensitive data through indirect means. Unlike their direct counterparts that directly target cryptographic algorithms, these attacks exploit unintended information leakage from seemingly innocuous system characteristics like power consumption, electromagnetic emissions, or even the sound of your computer. Think of it as eavesdropping on a conversation not by listening directly, but by observing the subtle vibrations in the windowpane – clever, right? This exploration dives into the fascinating world of these attacks, revealing their mechanisms, potential impact, and the strategies to combat them.
We’ll uncover how variations in power consumption, electromagnetic emanations, and acoustic signals can betray confidential information. We’ll also delve into the insidious world of cache-based attacks, where the timing of memory access becomes a vulnerability. Prepare to be amazed (and slightly terrified) by the ingenuity of these attacks and the equally ingenious countermeasures designed to thwart them. The journey through this hidden world of data breaches will equip you with a deeper understanding of the ever-evolving landscape of cybersecurity threats.
Introduction to Indirect Side Channel Attacks

Source: informationsecurityasia.com
Think of it like this: you’re trying to crack a safe. A direct attack involves picking the lock or blowing it up. An indirect attack, however, might involve observing the vibrations in the floor when someone’s trying to open it, or noticing the flickering of nearby lights due to the power draw. That’s the essence of indirect side-channel attacks – exploiting unintended information leaks, not directly from the target system’s core functionality, but from its side effects.
Indirect side-channel attacks differ from direct attacks in their approach. Direct attacks target the cryptographic algorithm or system directly, attempting to manipulate inputs or break encryption. Indirect attacks, conversely, focus on observable side effects—power consumption, timing variations, electromagnetic emissions, or even acoustic noise—that indirectly reveal sensitive information about the computation being performed. They exploit the system’s physical characteristics and environment, rather than its logical vulnerabilities.
Examples of Real-World Indirect Side-Channel Attacks
Several real-world examples illustrate the potency of indirect side-channel attacks. The infamous “TEMPEST” attacks, for instance, leveraged electromagnetic emissions from computer monitors and other equipment to intercept data. Another example is the exploitation of power consumption variations in cryptographic devices to recover encryption keys. Variations in timing, caused by conditional branching within algorithms, have also been successfully used to extract sensitive data. These attacks demonstrate that seemingly insignificant side effects can compromise even the most secure systems if not properly addressed.
Comparison of Indirect Side-Channel Attack Types
The table below categorizes different types of indirect side-channel attacks based on the exploited resource. Understanding these categories is crucial for developing effective countermeasures.
| Attack Type | Exploited Resource | Description | Example |
|---|---|---|---|
| Power Analysis | Power Consumption | Analyzing variations in power consumption during cryptographic operations to infer secret information. | Simple Power Analysis (SPA) and Differential Power Analysis (DPA) |
| Electromagnetic Analysis | Electromagnetic Emissions | Capturing and analyzing electromagnetic emissions from a device to extract sensitive data. | Similar techniques to power analysis, but focusing on electromagnetic signals. |
| Acoustic Cryptanalysis | Acoustic Signals | Analyzing sounds emitted by a device during computation to infer secret information. This can include sounds from hard drives, fans, or even keystrokes. | Analyzing the sounds of a keyboard to recover keystrokes, or the sounds from a hard drive to infer data access patterns. |
| Timing Attacks | Execution Time | Exploiting variations in the execution time of cryptographic operations to recover secret information. | Observing differences in processing time based on conditional branches within an algorithm. |
Exploiting Power Consumption as an Indirect Channel: Indirector Side Channel Attack
Power consumption, seemingly a mundane aspect of computing, can inadvertently reveal sensitive information. Variations in a device’s power draw, even minuscule ones, can betray the operations being performed, acting as a sneaky side channel for attackers. This is because different cryptographic operations, for instance, require varying amounts of power depending on the data being processed. These variations, when carefully measured and analyzed, can expose secrets.
Variations in power consumption leak sensitive data because the underlying hardware’s energy use is directly tied to its activity. For example, a processor performing a complex calculation will draw more power than one sitting idle. Similarly, accessing different memory locations can lead to detectable power fluctuations. By meticulously monitoring these fluctuations, an attacker can infer the data being processed, effectively bypassing traditional security measures. This is particularly true in cryptographic contexts where the algorithm’s behavior is influenced by the secret key.
A Hypothetical Scenario: Stealing a Cryptographic Key
Imagine a smart card used for secure authentication. This card employs a cryptographic algorithm to verify user identity. An attacker, equipped with specialized equipment capable of measuring the card’s power consumption with high precision, might initiate a series of authentication attempts. Each attempt will involve the card performing cryptographic computations using the secret key. The attacker, by analyzing the subtle power fluctuations during these computations, can correlate specific power signatures with different parts of the key. Through sophisticated statistical analysis, they can reconstruct the entire key, compromising the security of the system. This is a simplified example, but it illustrates the core principle: even seemingly insignificant power variations can leak significant information.
Mitigating Power-Based Indirect Side-Channel Attacks
Several techniques exist to reduce the vulnerability of systems to power analysis attacks. These methods focus on either masking the power variations or making the analysis significantly more difficult.
Countermeasures Against Power Analysis Attacks, Indirector side channel attack
The effectiveness of power analysis attacks can be significantly reduced through a combination of hardware and software techniques. Here are some crucial countermeasures:
- Power Shielding: Physically shielding the device to reduce the signal strength of power fluctuations.
- Regular Power Consumption: Designing circuits to consume a consistent amount of power regardless of the data being processed.
- Power Balancing: Designing cryptographic algorithms to ensure that the power consumption is relatively uniform for all possible inputs.
- Clock Glitching: Introducing intentional clock variations to disrupt the timing correlations exploited by power analysis attacks.
- Hardware Randomization: Introducing randomness into the circuit’s operation to break the correlation between power consumption and data.
- Software Countermeasures: Employing software techniques such as blinding or masking to randomize the data processed, thereby obfuscating its impact on power consumption.
Electromagnetic Emanations as Indirect Channels
Electromagnetic emanations, those invisible waves of energy radiating from electronic devices, represent another potent avenue for side-channel attacks. Unlike power consumption analysis, which focuses on the device’s energy usage, electromagnetic emanations reveal information through the subtle electromagnetic fields generated during computation. These fields, though often weak, can contain traces of the data being processed, providing attackers with a window into the device’s inner workings. This technique is particularly effective because electromagnetic signals propagate through air and other materials, offering attackers a degree of physical distance from their target.
Electromagnetic emanations are a byproduct of the electrical currents and switching activities within a device. Every time a transistor switches states, a tiny electromagnetic pulse is emitted. These pulses, while individually weak, can be aggregated and analyzed to reveal sensitive information. The principle behind electromagnetic emanation attacks relies on the fact that these emanations are directly correlated with the internal processes of the device. By carefully measuring and interpreting these emanations, an attacker can potentially extract cryptographic keys, passwords, or other sensitive data.
Vulnerabilities Exploited Through Electromagnetic Emanations
Several vulnerabilities can be exploited through electromagnetic emanations. These include vulnerabilities in cryptographic implementations where intermediate values leak through electromagnetic emissions, flaws in memory access patterns revealing data locations, and timing-related information exposed through variations in electromagnetic signals. For example, a specific electromagnetic signature might correspond to a particular instruction being executed, revealing details about the algorithm used and potentially the secret key itself. The level of detail revealed depends on the sophistication of the attack and the sensitivity of the target device’s design.
A Hypothetical Electromagnetic Side-Channel Attack
Imagine a scenario where an attacker targets a smart card used for secure transactions. The attacker uses a specialized antenna, positioned close to the card, to capture its electromagnetic emissions during a transaction. The captured signals are then processed using sophisticated signal processing techniques, including filtering, amplification, and correlation analysis. By correlating the measured electromagnetic emissions with the known timing of the smart card’s operations, the attacker might be able to isolate specific signals related to the decryption of the transaction data. Through careful analysis of these signals, the attacker could potentially reconstruct parts of the decryption key, allowing them to subsequently intercept and manipulate future transactions. This is not merely a hypothetical scenario; similar attacks have been successfully demonstrated against various cryptographic implementations in real-world settings.
Electromagnetic Shielding Techniques: A Comparison
Several techniques exist to mitigate electromagnetic emanation attacks. These techniques primarily focus on reducing the strength of the emitted electromagnetic fields. Common approaches include the use of conductive shielding materials, such as metal enclosures or conductive coatings. The effectiveness of these materials depends on factors such as the frequency of the emitted signals and the material’s conductivity. Another approach involves careful circuit design techniques, such as minimizing the loop area of circuits and using shielded cables. These techniques aim to reduce the intensity of the electromagnetic fields generated by the device. Furthermore, sophisticated countermeasures involve incorporating random delays or noise into the device’s operation to make the emanations less predictable and more difficult to analyze. The choice of shielding technique depends on the specific security requirements, the cost constraints, and the complexity of the device. A comprehensive approach often combines multiple techniques for optimal protection.
Acoustic Side Channels as Indirect Channels
The world of side-channel attacks isn’t limited to power consumption or electromagnetic emissions. The sounds a computer makes, seemingly innocuous, can also leak sensitive data. These acoustic side channels offer attackers a surprisingly effective way to glean information, often overlooked in standard security assessments. Understanding these vulnerabilities is crucial for building robust security systems.
Acoustic signals generated by computing devices, from the subtle whir of fans to the clicks of hard drives, can subtly vary based on the operations being performed. These variations, often imperceptible to the human ear, can be captured and analyzed to reveal sensitive information such as cryptographic keys or passwords. The intensity, frequency, and timing of these sounds all provide potential avenues for attack.
Acoustic Attack Vectors and Data Leakage
The process of extracting data through acoustic side-channels often involves sophisticated signal processing techniques. For instance, the timing of keystrokes on a mechanical keyboard can be captured and analyzed to reconstruct the typed text. Similarly, the varying speeds of hard disk drives, reflecting the intensity of data access, can be correlated with specific operations, revealing patterns in data processing. Even the subtle variations in fan noise, related to CPU temperature fluctuations during cryptographic operations, can offer clues about the data being processed. This demonstrates that even seemingly minor acoustic variations can expose sensitive information.
Mitigating Acoustic Emanations
Reducing acoustic emanations requires a multi-pronged approach. The first step involves physical shielding, such as sound-dampening enclosures or strategically placed acoustic barriers, to reduce the transmission of sound waves. Modifying hardware components to reduce noise production, such as using quieter fans or solid-state drives (SSDs) instead of traditional hard disk drives (HDDs), can significantly minimize acoustic leakage. Software-based solutions include implementing algorithms that randomize or mask acoustic patterns generated during sensitive operations. This might involve introducing artificial noise or strategically varying processing times to obscure patterns.
Acoustic Attack Countermeasures
| Attack Vector | Countermeasure | Effectiveness | Implementation Cost |
|---|---|---|---|
| Keyboard Acoustic Analysis (Keystroke Timing) | Use of silent keyboards, software keystroke randomization | High (for silent keyboards), Moderate (for software randomization) | High (for hardware), Low (for software) |
| Hard Drive Acoustic Analysis (Seek Time) | Use of SSDs, data encryption | High (for SSDs), High (for encryption) | Moderate (for SSDs), Low (for encryption) |
| Fan Noise Analysis (CPU Temperature Fluctuations) | Improved thermal management, use of quieter fans | Moderate | Low to Moderate |
| Power Supply Acoustic Analysis (Switching Frequency) | Use of quieter power supplies, sound dampening enclosure | Moderate to High | Low to Moderate |
Cache-Based Indirect Side Channel Attacks
Cache-based attacks represent a sneaky way to glean sensitive information from a computer system without directly accessing the data itself. They exploit the inherent timing variations in how a computer’s cache memory operates, revealing patterns that indirectly betray the secrets held within. This is a classic example of an indirect side-channel attack, where the attacker doesn’t directly breach security but instead observes subtle side effects of the system’s behavior.
Cache timing attacks are categorized as indirect side-channel attacks because they don’t involve directly accessing memory or manipulating system files. Instead, they leverage the observable side effect of cache access times to infer information about the data being processed. The attacker observes the timing differences in memory access, which vary depending on whether the requested data is already present in the cache (fast access) or needs to be fetched from slower main memory (slow access). These subtle timing variations, usually measured in nanoseconds, can reveal a surprising amount of sensitive data.
Cache Timing Attack Mechanisms
The core mechanism behind cache-based attacks hinges on the principle of locality of reference. Programs tend to access data in clusters. If a program accesses a particular data element, it’s likely to access related data elements shortly afterward. This leads to those related data elements being loaded into the cache. An attacker can then strategically craft requests that probe the cache, measuring the access times. Faster access times indicate the data was already in the cache, implying a relationship with previously accessed data, thereby revealing information about the target data. For example, if an attacker observes a consistently faster access time for specific memory addresses when a particular cryptographic key is processed, they can infer the value of that key.
Hypothetical Cache Timing Attack: Exfiltrating a Password
Let’s imagine a scenario where a user’s password is stored in memory. A malicious program could be designed to repeatedly access memory locations near the suspected password location. By meticulously timing each access, the attacker can identify which memory locations are cached more quickly, thereby pinpointing the location of the password. This is because the act of accessing the password would likely bring neighboring memory locations into the cache as well.
Step-by-Step Procedure for a Hypothetical Cache-Based Attack
- Target Identification: The attacker first identifies the target process (e.g., a web browser handling user logins) suspected of storing sensitive data in memory.
- Memory Address Prediction: The attacker attempts to predict the likely memory address range where the sensitive data (password in this case) is stored. This might involve reverse engineering the target application or exploiting known memory layout patterns.
- Cache Probe Design: The attacker crafts a program that repeatedly accesses memory locations within the predicted address range. The program precisely measures the time taken for each access.
- Data Analysis: The measured access times are analyzed. Significantly faster access times for specific memory locations indicate that those locations were already in the cache, revealing the probable location of the sensitive data.
- Data Extraction: Finally, once the location is identified, the attacker can attempt to extract the sensitive data. This might involve directly reading the memory location (if permissions allow) or using other techniques to infer the data based on its surrounding context.
Mitigating Indirect Side-Channel Attacks
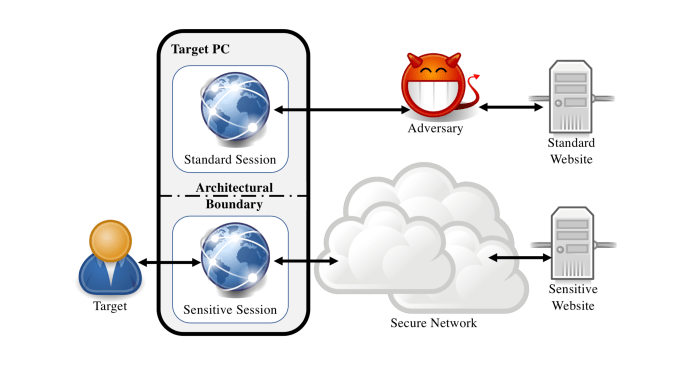
Source: ac.il
Protecting against indirect side-channel attacks requires a multi-layered defense strategy, acknowledging that a single solution rarely provides complete immunity. The goal is to make the extraction of sensitive information prohibitively difficult and costly for attackers. This involves both hardware and software modifications, each with its own set of trade-offs.
General Mitigation Strategies
Effective mitigation hinges on minimizing the information leakage pathways. This involves reducing the correlation between the processed data and the observable side channel. Techniques range from masking sensitive data to introducing noise into the system, thereby obscuring any patterns that an attacker might exploit. The choice of strategy often depends on the specific side channel being targeted and the sensitivity of the data being processed.
Hardware Countermeasures
Hardware-based countermeasures offer a more robust approach, directly addressing the physical mechanisms responsible for side-channel leakage. These solutions often come with higher implementation costs and potential performance penalties. Examples include specialized shielding to reduce electromagnetic emissions, power-supply filtering to minimize power fluctuations, and the use of countermeasures like constant-time execution units, which execute code in a uniform time regardless of the data processed. For instance, implementing a constant-time cryptographic library in specialized hardware can significantly reduce timing attacks.
Software Countermeasures
Software countermeasures focus on modifying the code and operating system to reduce the information leakage. These solutions are generally easier and cheaper to implement than hardware countermeasures but may not be as effective. Techniques include data obfuscation, which makes the data harder to interpret from the side channel, and the use of randomized algorithms to introduce variability in execution times and power consumption. A simple example is the use of software-based masking, where sensitive data is combined with random noise to obscure its value. However, these software solutions often require careful implementation to avoid introducing vulnerabilities elsewhere in the system.
Security and Performance Trade-offs
Implementing countermeasures inevitably impacts system performance. Hardware solutions, while often more effective, tend to increase cost and reduce speed significantly. Software-based countermeasures typically have a less dramatic impact on performance but might offer less protection. The optimal approach involves a careful balancing act. For example, using constant-time algorithms can eliminate timing attacks but might lead to a performance overhead. The choice depends on the specific application’s sensitivity to performance degradation versus the need for robust security. In high-security applications, like financial transactions, a performance hit might be acceptable if it ensures data integrity and confidentiality. For less sensitive applications, a less intensive countermeasure might be sufficient.
Implementing a Chosen Mitigation Strategy: Flowchart
The flowchart below illustrates the implementation of a software-based masking technique.
[Imagine a flowchart here. The flowchart would start with “Identify sensitive data and potential side channels.” This would branch to “Select appropriate masking technique (e.g., additive masking).” Then, “Implement masking algorithm in code.” Next, “Test for effectiveness using side-channel analysis tools.” This would branch to two options: “Adequate masking achieved – proceed to deployment” or “Insufficient masking – refine algorithm and repeat testing.” Finally, the flowchart would conclude with “Deployment and ongoing monitoring.”] This flowchart represents a simplified version; a real-world implementation would require far more detailed steps and considerations.
Future Trends and Research Directions
The field of indirect side-channel attacks is constantly evolving, driven by the increasing sophistication of both hardware and software systems. As devices become more powerful and interconnected, the potential attack surface expands, necessitating ongoing research into novel attack vectors and robust defense mechanisms. The future of this field hinges on anticipating and mitigating increasingly subtle and complex attacks.
The next generation of indirect side-channel attacks will likely leverage previously unexplored data leakage pathways and exploit vulnerabilities in emerging technologies. Researchers are exploring increasingly intricate combinations of different side channels, blurring the lines between traditional classifications and creating hybrid attacks that are far more difficult to detect and mitigate. This necessitates a shift towards holistic security approaches that consider the interconnectedness of various side channels.
Emerging Attack Vectors and Their Implications
Future attacks may exploit the unique characteristics of novel computing paradigms. For example, attacks could target the power consumption patterns of quantum computers, exploiting the unique nature of their computations to extract sensitive information. Similarly, the increasing reliance on machine learning (ML) in various applications introduces new vulnerabilities. An attacker could potentially manipulate the training data or internal workings of an ML model to induce predictable side-channel leakage, revealing sensitive information processed by the model. The implications are significant, ranging from data breaches in sensitive applications like finance and healthcare to compromised autonomous systems in critical infrastructure. Consider a scenario where an attacker manipulates the training data of a self-driving car’s object recognition system, subtly influencing its power consumption in a way that reveals the car’s location or route. This could have devastating consequences.
Challenges in Developing Effective Defenses
Developing effective defenses against advanced indirect side-channel attacks presents a significant challenge. Traditional countermeasures, such as shielding and masking techniques, may prove inadequate against sophisticated attacks that exploit multiple side channels simultaneously. The inherent complexity of modern systems, coupled with the ever-evolving nature of attack techniques, necessitates a multi-layered defense strategy. This includes developing novel hardware and software countermeasures, improving detection algorithms, and fostering a stronger emphasis on security-by-design principles. The difficulty lies in balancing the need for security with the performance requirements of the system, as many countermeasures introduce performance overhead.
A Future Attack Scenario and its Potential Impact
Imagine a future scenario involving a sophisticated attack targeting a secure enclave within a high-performance computing system. The attacker, leveraging a combination of power analysis, electromagnetic emanations, and cache timing attacks, exploits subtle variations in the system’s behavior to extract cryptographic keys used to protect sensitive data. This attack could bypass traditional software-based security mechanisms and extract information directly from the hardware. The potential impact is enormous, potentially leading to the compromise of sensitive government data, financial transactions, or intellectual property. The success of such an attack underscores the need for proactive research and development of robust, multi-faceted defense strategies to secure future computing systems against increasingly sophisticated threats.
Last Word
Source: slideserve.com
The world of indirector side channel attacks is a thrilling game of cat and mouse, where attackers constantly seek new ways to exploit subtle vulnerabilities, and defenders race to develop innovative countermeasures. While the sophistication of these attacks continues to evolve, so too does our ability to mitigate their threat. Understanding the underlying principles and adopting robust security practices are crucial steps in safeguarding sensitive data in this increasingly complex digital landscape. The fight is far from over, but armed with knowledge, we can stay one step ahead.



