CocoaPods vulnerability iOS macOS: The seemingly innocuous act of managing dependencies in your iOS and macOS projects through CocoaPods can harbor serious security risks. Think of it like this: you’re building a house, and CocoaPods is your supplier. If your supplier gives you faulty bricks, your entire house is compromised. This article dives deep into the potential vulnerabilities lurking within CocoaPods, offering practical strategies to safeguard your applications.
We’ll explore common attack vectors, methods for identifying vulnerable pods, and crucial mitigation strategies. From dependency pinning and secure coding practices to vulnerability scanning tools and best practices for dependency management, we’ll equip you with the knowledge to build secure and robust iOS and macOS applications. We’ll even walk through a hypothetical scenario to illustrate the real-world impact of a vulnerable pod.
CocoaPods Security Overview
CocoaPods, the ubiquitous dependency manager for iOS and macOS projects, simplifies development by streamlining the inclusion of third-party libraries. However, this convenience introduces security considerations that developers must understand and proactively address. A compromised dependency can expose your application and its users to significant risks.
CocoaPods’ architecture relies on a central repository, where developers publish their libraries (pods). Developers integrate these pods into their projects using a Podfile, a specification file that lists the required dependencies and their versions. CocoaPods then downloads and manages these dependencies, integrating them seamlessly into the project’s build process. This centralized nature, while efficient, presents potential vulnerabilities. A compromised pod, even a seemingly innocuous one, could introduce malware or backdoors into numerous applications. Furthermore, the reliance on specific versions of pods creates potential attack surfaces if vulnerabilities in older versions remain unpatched.
CocoaPods Attack Vectors
Several attack vectors can exploit vulnerabilities within the CocoaPods ecosystem. One primary concern is the potential for malicious actors to compromise the central repository or individual pods. This could involve injecting malicious code into a legitimate pod, creating a counterfeit pod with a similar name to a popular library, or even compromising the CocoaPods infrastructure itself. Another significant risk is the use of outdated or insecure dependencies. Failing to regularly update pods exposes applications to known vulnerabilities that have already been patched in newer versions. Supply chain attacks, where a malicious actor targets a specific dependency used by many applications, are also a considerable threat. A single compromised pod can cascade vulnerabilities throughout a vast ecosystem of apps.
Dependency Management and iOS/macOS Security
Effective dependency management is crucial for maintaining the security of iOS and macOS applications. Regularly auditing dependencies, ensuring that only trusted sources are used, and promptly updating to the latest versions are essential security practices. Employing robust code signing and verification mechanisms helps to detect and prevent the installation of tampered or malicious pods. Furthermore, incorporating security testing into the development lifecycle, including static and dynamic analysis, can help identify potential vulnerabilities before they reach production. Utilizing tools that scan dependencies for known vulnerabilities, like those provided by various security platforms, adds another layer of protection. A proactive approach to dependency management is paramount in mitigating the security risks associated with CocoaPods.
Identifying Vulnerable Pods: Cocoapods Vulnerability Ios Macos
Navigating the world of CocoaPods can feel like venturing into a bustling marketplace – exciting, but potentially risky. While CocoaPods offers a fantastic way to manage dependencies, it’s crucial to understand how to identify and mitigate vulnerabilities within the packages you integrate into your iOS and macOS applications. Ignoring this can lead to security breaches, app crashes, and a whole lot of developer headaches.
CocoaPods packages, like any software, are susceptible to various vulnerabilities. Understanding these common weaknesses and how to detect them is key to building secure and robust applications.
Common CocoaPod Vulnerabilities
A range of vulnerabilities can plague CocoaPods packages, impacting everything from data integrity to application stability. These vulnerabilities often stem from insecure coding practices, outdated libraries, or insufficient testing.
- Dependency Confusion: This occurs when an attacker creates a malicious package with the same name as a legitimate dependency, potentially tricking your project into using the harmful version.
- Remote Code Execution (RCE): A particularly dangerous vulnerability, RCE allows an attacker to execute arbitrary code on a user’s device, potentially leading to data theft or system compromise.
- Cross-Site Scripting (XSS): This vulnerability allows attackers to inject malicious scripts into your application, potentially stealing user credentials or manipulating user data.
- SQL Injection: If a pod interacts with a database, vulnerabilities could allow attackers to manipulate database queries, potentially leading to data breaches or application crashes.
- Denial of Service (DoS): Certain vulnerabilities might make your app unresponsive or crash, effectively denying service to legitimate users.
Real-World Examples of CocoaPod Vulnerabilities, Cocoapods vulnerability ios macos
While specific vulnerability details are often kept private for security reasons, it’s important to understand that real-world incidents involving compromised CocoaPods have occurred. For example, imagine a scenario where a popular networking library, widely used across many apps, is discovered to contain a hidden backdoor allowing an attacker to monitor network traffic. The impact on applications utilizing this library could be significant, potentially exposing sensitive user data. Another example could involve a seemingly innocuous image processing pod containing a vulnerability allowing arbitrary code execution upon image loading.
Identifying Outdated or Insecure Pods
Regularly auditing your dependencies is crucial for maintaining the security of your applications. Several methods can help you identify outdated or insecure pods.
- CocoaPods outdated command: Running
pod outdatedin your terminal within your project directory provides a clear list of pods requiring updates. This highlights versions that are behind the latest release, which may contain critical security patches. - Manual dependency review: Regularly checking the GitHub repositories or official websites of your pods can reveal security advisories or release notes mentioning fixes for known vulnerabilities.
- Security scanning tools: Several third-party security scanning tools can analyze your Podfile and identify potential vulnerabilities based on known exploits and publicly available vulnerability databases. These tools can automate the process and offer a comprehensive overview of your project’s security posture.
Mitigation Strategies
So, you’ve identified potential vulnerabilities in your CocoaPods dependencies. Now what? Panic is not the answer. A proactive approach, focusing on prevention and swift action, is key to keeping your iOS and macOS apps secure. Let’s dive into the strategies that will help you sleep soundly at night, knowing your apps are protected.
Implementing robust mitigation strategies is crucial for minimizing the risk of vulnerabilities stemming from CocoaPods. This involves a multi-pronged approach encompassing proactive security measures, regular updates, and the use of appropriate scanning tools. By adopting these strategies, developers can significantly reduce the likelihood of security breaches and maintain the integrity of their applications.
CocoaPods Security Checklist
A comprehensive checklist helps ensure you’re covering all bases when integrating CocoaPods. Think of it as your pre-flight checklist before launching your app into the wild. Regularly reviewing this checklist helps maintain a high level of security throughout your development lifecycle.
This checklist should be integrated into your development workflow. It’s not a one-time task, but a continuous process of review and improvement.
- Regularly update CocoaPods: Keep your CocoaPods version current to benefit from the latest security patches and improvements.
- Employ dependency pinning: Pin your Pod versions to specific releases to prevent unintended updates that might introduce vulnerabilities.
- Utilize a vulnerability scanner: Regularly scan your dependencies for known vulnerabilities using tools like Bundler-audit or Snyk.
- Implement a secure coding practice: Follow secure coding guidelines to minimize vulnerabilities in your own codebase.
- Conduct regular security audits: Periodically review your Podfile and Podfile.lock for any suspicious or outdated dependencies.
- Use a dedicated security repository: Consider using a private repository to manage your dependencies, improving control and security.
Updating Pods to Secure Versions
Updating your Pods is not just about getting new features; it’s about patching security holes. A step-by-step process ensures a smooth and secure update.
- Check for updates: Run
pod outdatedto see which Pods need updating. - Review changelog: Before updating, check the changelog of each Pod to ensure the update doesn’t introduce regressions or other issues.
- Update the Podfile: Update the versions in your Podfile to the latest secure versions. For example, change
pod 'AFNetworking', '~> 3.0'topod 'AFNetworking', '3.2.1'(replace with actual version numbers). - Run
pod update: This command will fetch and install the updated Pods. - Thorough testing: After updating, perform comprehensive testing to ensure everything works as expected and no new vulnerabilities or bugs have been introduced.
Dependency Pinning Implementation
Dependency pinning is like locking down your dependencies to prevent unexpected changes. It ensures that your app always uses the specific versions of Pods you’ve tested and verified. This helps avoid introducing vulnerabilities through unintentional updates.
By specifying exact versions, you avoid the potential for automatic updates to introduce security risks. This is especially critical for production applications.
Instead of using version ranges (e.g., ~> 1.0), specify exact versions (e.g., 1.0.1) in your Podfile. This will be reflected in your Podfile.lock file, providing a consistent build across different environments.
Vulnerability Scanning Tools Comparison
Several tools can help you identify vulnerabilities in your CocoaPods dependencies. Choosing the right one depends on your needs and budget.
| Tool | Features | Pricing | Ease of Use |
|---|---|---|---|
| Snyk | Automated vulnerability detection, integration with CI/CD pipelines, detailed reports | Free and paid plans | Easy to integrate and use |
| Bundler-audit | Open-source, command-line tool for Ruby dependency checking, identifies vulnerabilities | Free | Requires command-line familiarity |
| Dependabot (GitHub) | Automated dependency updates and vulnerability alerts, integrated with GitHub | Free for public repositories, paid for private repositories | Easy to set up for GitHub users |
| CocoaPods-core (with manual checks) | Requires manual review of Pod versions and changelogs, less automated | Free | Requires more manual effort |
Secure Coding Practices
Even with the most meticulously vetted CocoaPods, vulnerabilities can still slip through. Secure coding practices are your last line of defense, minimizing the impact of any potential breaches and safeguarding your app’s integrity. This involves proactively addressing how your code interacts with potentially compromised dependencies and handling sensitive data responsibly.
Building secure iOS and macOS apps using CocoaPods requires a multi-faceted approach. It’s not just about choosing secure pods; it’s about writing code that’s resilient to attacks, even if a dependency is compromised. This means implementing robust security measures throughout your application’s architecture.
Data Handling and Encryption
Protecting sensitive data is paramount. Never store credentials, API keys, or personally identifiable information (PII) directly in your code. Instead, utilize the Keychain for storing sensitive data securely. The Keychain provides a hardware-backed security mechanism that protects data even if the device is compromised. For data transmitted over a network, always use HTTPS and consider implementing end-to-end encryption using established cryptographic libraries. This ensures that data remains confidential even if intercepted. Remember to properly handle encryption keys, storing them securely within the Keychain or using a dedicated key management system.
Input Validation and Sanitization
User inputs are a frequent entry point for attacks. Never trust user-provided data. Always validate and sanitize all inputs before using them in your application. This involves checking for data type, length, and format, and removing or escaping any potentially harmful characters. For example, if expecting an email address, check that it conforms to a valid email pattern before processing it. Similarly, if processing user-supplied text for display, sanitize it to prevent cross-site scripting (XSS) attacks by escaping special characters like `<`, `>`, and `&`. Regular expressions can be valuable tools for this process, but be mindful of their potential performance impact for large datasets. A well-structured validation process is crucial for preventing data injection attacks.
Least Privilege Principle
Implement the principle of least privilege. Grant only the necessary permissions to your code and the pods it uses. Avoid using excessive entitlements, and carefully review the permissions requested by each pod. This limits the potential damage from a compromised pod, as it won’t have unnecessary access to system resources. This is particularly important when dealing with sensitive data or system-level operations. For example, if a pod only needs access to the camera, don’t grant it access to the user’s contacts or location data.
Secure Coding Practices within CocoaPods
When integrating third-party libraries through CocoaPods, it’s vital to audit their codebase for potential vulnerabilities. This involves checking for insecure coding patterns, such as hardcoded credentials or inadequate input validation. Prioritize libraries with a strong track record of security updates and active maintenance. Regularly update your pods to benefit from security patches and bug fixes. This proactive approach significantly reduces your app’s exposure to known vulnerabilities. Additionally, use static and dynamic code analysis tools to identify potential security weaknesses in your code and your dependencies.
Impact Assessment and Remediation
Discovering a vulnerability in a CocoaPod used across your iOS and macOS applications can be a serious situation. The impact depends heavily on the nature of the vulnerability, the pod’s role in your app, and the extent of its use. A thorough impact assessment is crucial before jumping into remediation.
Understanding the potential consequences is the first step in effectively mitigating risks. Failing to do so could lead to compromised user data, application crashes, or even complete system compromise. This section Artikels a structured approach to evaluating these risks and implementing effective fixes.
Potential Impacts of CocoaPods Vulnerabilities
The impact of a vulnerable CocoaPod can range from minor inconveniences to significant security breaches. For example, a vulnerability allowing unauthorized access to local files could lead to data leaks, while a crash vulnerability might only cause temporary app disruption. More critically, a remote code execution vulnerability could grant an attacker complete control over the affected device. The severity is directly tied to the type of vulnerability and the pod’s functionality within the application. A pod handling sensitive user data presents a much higher risk than one responsible for simple UI elements. Consider the potential for data breaches, application crashes, performance degradation, and even denial-of-service attacks.
Remediation Strategies for Common Vulnerabilities
Different vulnerabilities require different remediation strategies. For instance, if a dependency has a known cross-site scripting (XSS) vulnerability, updating the pod to the latest version that addresses this issue is the primary solution. This usually involves updating the Podfile and running `pod update`. However, if the vulnerability is in a pod that’s no longer maintained, a more complex approach is needed. This could involve forking the pod, patching the vulnerability yourself, and then using your forked version in your project.
Another example is a denial-of-service (DoS) vulnerability. Here, mitigating the risk may involve implementing robust input validation and sanitization within your application, even if the underlying pod isn’t directly patched. This prevents malicious input from triggering the DoS condition. For vulnerabilities related to insecure data handling, implementing encryption and secure storage mechanisms is crucial, even if the underlying pod is updated. This adds an extra layer of protection, minimizing the impact even if the pod still has minor weaknesses.
Structured Approach to Risk Assessment and Mitigation
A structured approach is essential for effectively managing the risks associated with CocoaPods vulnerabilities. This involves several key steps:
- Identify Vulnerable Pods: Regularly scan your dependencies for known vulnerabilities using tools like Bundler-audit or Snyk.
- Assess the Impact: Evaluate the severity of each vulnerability and its potential impact on your application and users. Consider the sensitivity of the data handled by the vulnerable pod and the potential consequences of exploitation.
- Prioritize Remediation: Focus on addressing the most critical vulnerabilities first. Those with high severity and significant impact should be prioritized.
- Implement Remediation Strategies: Update vulnerable pods, apply patches, or implement compensating controls as needed. Thoroughly test the changes after implementation.
- Monitor and Reassess: Regularly monitor for new vulnerabilities and reassess the risk profile of your application’s dependencies. Continuous monitoring is key to maintaining a secure application.
Following this structured approach allows for a proactive and efficient response to CocoaPods vulnerabilities, minimizing potential damage and ensuring the security of your applications.
Best Practices for Dependency Management
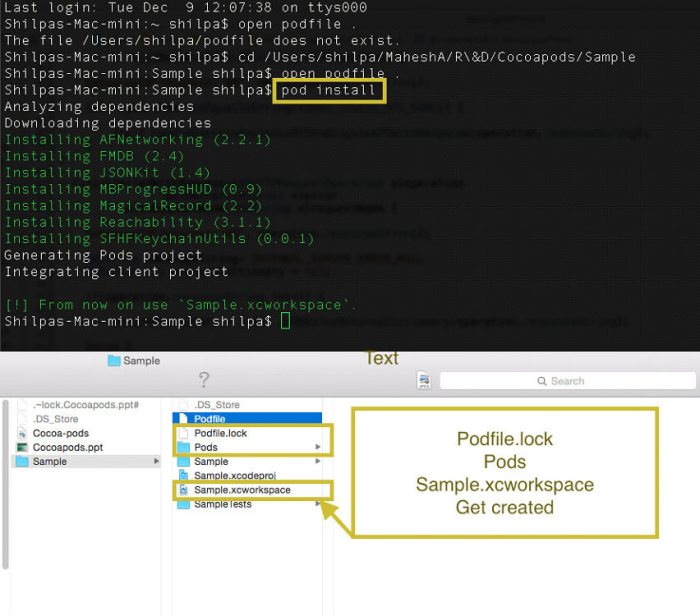
Source: mobisoftinfotech.com
Navigating the world of CocoaPods and its dependencies can feel like traversing a jungle – thrilling, but potentially fraught with danger. A robust dependency management strategy is crucial for building secure and maintainable iOS and macOS applications. This section Artikels key practices to help you tame the wild west of project dependencies.
Effective dependency management isn’t just about avoiding vulnerabilities; it’s about streamlining your workflow, improving collaboration, and ensuring the long-term health of your project. By following these best practices, you can significantly reduce the risk of security breaches and improve the overall quality of your codebase.
Version Specifiers and Dependency Resolution
Precise version specification is paramount. Avoid using overly broad version ranges like `~> 1.0` unless absolutely necessary. Instead, specify precise versions (e.g., `1.2.3`) whenever possible to eliminate unexpected behavior from updates. This allows for better control and reproducibility of your build environment. Using `>= 1.2.3` allows for future updates while still providing a minimum version requirement. Careful consideration of the semantic versioning (SemVer) system helps ensure compatibility and minimizes surprises. For instance, if a library jumps from version 1.0 to 2.0, a breaking change might be introduced that breaks your application.
Dependency Updates and Version Pinning
Regularly check for updates to your dependencies. CocoaPods provides tools to help you identify outdated pods. However, blindly updating everything is risky. Before updating, carefully review the release notes and changelog of each pod to understand potential changes and ensure compatibility with your application. Consider version pinning for critical dependencies to prevent accidental upgrades that might introduce regressions or vulnerabilities. This practice locks down specific versions of key libraries, creating a more stable and predictable development environment. For example, if a library has a critical security patch, you can update to the patched version while pinning other dependencies.
Private CocoaPods Repositories
Utilizing a private CocoaPods repository offers several significant advantages. It allows for secure management of internal libraries and dependencies, preventing accidental exposure of proprietary code or sensitive information. A private repository also simplifies collaboration within a team, allowing for consistent access to shared components and facilitating better version control. This reduces the risk of using outdated or insecure third-party libraries. Companies often use private repositories to manage internal frameworks, ensuring consistent quality and security across their applications.
Automating Security Checks
Integrating automated security checks into your Continuous Integration/Continuous Deployment (CI/CD) pipeline is essential. Tools can automatically scan your dependencies for known vulnerabilities and flag potential issues before they reach production. This proactive approach helps identify and address vulnerabilities early in the development lifecycle, minimizing the impact of any security flaws. A common approach is to integrate dependency scanners like `bundler-audit` (for RubyGems, which underlies CocoaPods) or dedicated security analysis tools into your CI/CD process. This allows for automated checks at each build, providing a real-time overview of potential security risks.
Illustrative Example: Vulnerable Pod Analysis
Let’s imagine a scenario where your iOS app uses a popular CocoaPod called “AwesomeImagePicker,” a library designed to simplify image selection from the device’s photo library. This pod, however, contains a critical vulnerability: a flaw in its handling of user permissions that allows unauthorized access to the device’s entire photo library, even if the user only granted permission for the app to access specific images. This isn’t just a theoretical risk; similar vulnerabilities have plagued real-world image picker libraries in the past, highlighting the importance of proactive security measures.
This vulnerability poses a significant threat to user privacy and data security. A malicious actor could exploit this flaw to gain access to sensitive personal photos without the user’s knowledge or consent. The impact extends beyond simple privacy concerns; the compromised photos could be used for identity theft, blackmail, or other malicious purposes.
Vulnerability Identification and Assessment
Discovering this vulnerability would likely involve a combination of methods. Regularly checking the CocoaPods security advisories is crucial. Additionally, automated security scanning tools, which analyze the code of your dependencies, can identify potential vulnerabilities. Manual code review, while time-consuming, is another effective approach, particularly for critical dependencies. Once identified, the severity of the vulnerability needs careful assessment. In our example, unauthorized access to a user’s entire photo library is a high-severity issue, warranting immediate action. This assessment should consider the sensitivity of the data at risk, the likelihood of exploitation, and the potential impact of a successful attack.
Remediation Strategy
The most effective remediation strategy is to update the “AwesomeImagePicker” pod to a version that addresses the vulnerability. CocoaPods makes this relatively straightforward; updating involves modifying the Podfile to specify the patched version and then running `pod update`. If a patched version isn’t available, consider alternative image picker libraries that are well-maintained and have a strong security track record. In extreme cases, if no suitable alternative exists, you might need to fork the vulnerable pod, fix the vulnerability yourself, and incorporate your patched version into your project. This, however, is generally more complex and requires careful consideration of long-term maintainability.
Impact on Application Security
The impact of the vulnerability is multi-faceted. Firstly, it directly compromises user privacy by granting unauthorized access to sensitive personal data. This breach of trust can severely damage the app’s reputation and lead to a loss of user confidence. Secondly, it exposes the application to legal and regulatory repercussions, particularly concerning data protection laws like GDPR and CCPA. Thirdly, a successful exploitation could open the door to further attacks, potentially compromising other aspects of the application’s security. Finally, the reputational damage and potential legal consequences could result in significant financial losses for the app developer. A real-world example would be the consequences faced by an app that suffered a data breach due to a vulnerable third-party library; this could involve hefty fines, legal battles, and a significant drop in user base.
Future Trends in CocoaPods Security
Source: code-gorilla.com
CocoaPods, while a vital tool for iOS and macOS development, faces an ever-evolving landscape of security threats. As dependency management becomes more complex, so too do the potential vulnerabilities. Understanding these emerging threats and anticipating future developments is crucial for maintaining secure and robust applications.
The increasing sophistication of supply chain attacks presents a significant challenge. Malicious actors are constantly seeking new ways to compromise open-source libraries, potentially introducing backdoors or malware into seemingly innocuous pods. This necessitates a proactive approach to security, moving beyond reactive patching to encompass preventative measures.
Evolving Supply Chain Attacks
The complexity of modern software projects, relying on numerous interconnected dependencies, creates a vast attack surface. Sophisticated attacks might involve compromising a seemingly unrelated pod, subtly introducing malicious code that remains undetected until exploited. For example, a seemingly harmless image processing library could contain a hidden component that exfiltrates sensitive user data. Future threats might involve more targeted attacks, focusing on specific high-value applications or industries. This necessitates the development of more robust verification and validation mechanisms for CocoaPods dependencies.
Advanced Threat Detection Mechanisms
The future of CocoaPods security hinges on the development of advanced threat detection mechanisms. This includes leveraging machine learning and AI to identify anomalous behavior within pods, such as unexpected network requests or unusual code patterns. Static and dynamic analysis techniques will play a crucial role in proactively identifying potential vulnerabilities before they are exploited. Real-time monitoring of pod activity, coupled with automated alerts, will be essential in responding quickly to emerging threats. Think of this as a sophisticated antivirus for your project’s dependencies.
Improved Dependency Verification
Strengthening the verification process for CocoaPods is paramount. This could involve incorporating cryptographic signatures for pods, ensuring the authenticity and integrity of each dependency. Enhanced provenance tracking, providing a clear lineage for each pod, would help in identifying compromised components. A system for automated vulnerability scanning, integrated directly into CocoaPods, would significantly reduce the burden on developers. This could be similar to how many package managers now offer built-in security checks.
Enhanced Security Auditing
Regular security audits of the CocoaPods ecosystem are crucial. This involves a comprehensive review of the security practices employed by pod maintainers, identifying potential weaknesses and areas for improvement. Incentivizing secure coding practices through community engagement and recognition would foster a more secure development environment. This could involve providing best-practice guidelines and training resources for pod maintainers, coupled with regular security audits of popular pods.
Conclusive Thoughts
Source: scalablepath.com
Securing your iOS and macOS applications against CocoaPods vulnerabilities isn’t just about following best practices; it’s about proactively mitigating risks and building a robust security posture. By understanding the potential threats, implementing effective mitigation strategies, and staying updated on emerging security trends, you can significantly reduce your exposure to vulnerabilities and protect your users’ data and privacy. Remember, vigilance and proactive security measures are key to safeguarding your applications in the ever-evolving landscape of mobile development.
