Csharp streamer malware attack windows – C# Streamer Malware Attack: Windows Vulnerabilities – sounds scary, right? Imagine this: you’re live-streaming your epic gaming session, suddenly, BAM! Your system’s compromised. Malware, lurking in the shadows of your C# application, is stealing your data, disrupting your stream, or worse. This isn’t some far-fetched sci-fi plot; it’s a real threat to C# streamers on Windows. We’ll dive deep into the common vulnerabilities, sneaky delivery methods, and effective mitigation strategies to keep your stream safe and secure.
From insecure coding practices and memory management issues to the dangers of phishing attacks and vulnerable streaming software, we’ll uncover the dark side of online streaming. We’ll equip you with the knowledge and tools to identify and prevent malware attacks, analyze suspicious code, and build a robust incident response plan. Get ready to level up your cybersecurity game!
C# Streamer Malware Vulnerabilities
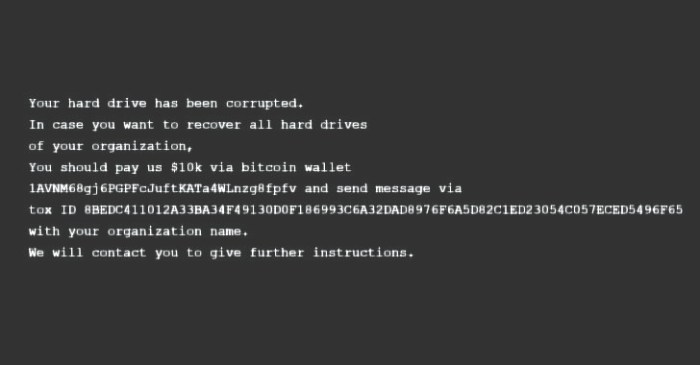
Source: thehackernews.com
C# applications, while powerful and versatile, are not immune to malware attacks. Streamers, often utilizing custom applications for interaction with their audience, are particularly vulnerable due to the potential for direct interaction with untrusted sources. Understanding the common vulnerabilities and implementing secure coding practices is crucial for protecting both the streamer and their viewers.
Insecure Deserialization
Deserialization, the process of reconstructing an object from its serialized representation, is a frequent attack vector. If a C# application deserializes data from an untrusted source without proper validation, an attacker could inject malicious code disguised as serialized data. This malicious code could then execute within the application’s context, potentially granting the attacker complete control. For example, an application accepting configuration files from viewers could be exploited if it doesn’t thoroughly validate the contents of those files before deserialization. Failing to properly sanitize and validate user inputs before deserialization is a critical oversight.
SQL Injection Vulnerabilities
Many streaming applications interact with databases to store and retrieve information. If these interactions are not properly parameterized, SQL injection vulnerabilities can arise. An attacker could craft malicious SQL queries embedded within user inputs, potentially allowing them to read, modify, or delete sensitive data. For instance, imagine a streamer’s application allowing users to search for other streamers by name. If the search query is directly concatenated into the SQL query without proper parameterization, an attacker could inject malicious SQL code, potentially gaining access to the streamer’s database.
Improper Input Validation
Insufficient input validation is a fundamental weakness. Failing to thoroughly check and sanitize user inputs before processing them can lead to various attacks, including buffer overflows, cross-site scripting (XSS), and command injection. Consider a scenario where a streamer’s chat application allows users to enter arbitrary text. If this text is not properly validated and sanitized before being displayed, an attacker could inject malicious JavaScript code (XSS) that executes in the viewers’ browsers, potentially stealing their session cookies or performing other malicious actions.
Memory Management Issues
While C# boasts automatic garbage collection, memory management issues can still be exploited. Unhandled exceptions or memory leaks can lead to instability and vulnerabilities. A denial-of-service (DoS) attack could be launched by forcing the application to consume excessive memory, resulting in crashes or slowdowns. Furthermore, if the application fails to properly release resources, it could leave sensitive data exposed in memory, potentially accessible by attackers. Efficient error handling and proper resource management are essential to prevent such issues.
Secure Coding Guideline for C# Streamers, Csharp streamer malware attack windows
To mitigate these vulnerabilities, streamers should adhere to a strict secure coding guideline:
- Always validate and sanitize all user inputs before processing them.
- Use parameterized queries to prevent SQL injection vulnerabilities.
- Implement robust input validation to prevent buffer overflows and other injection attacks.
- Utilize secure deserialization techniques, validating data thoroughly before reconstructing objects.
- Implement comprehensive error handling and resource management to prevent memory leaks and crashes.
- Regularly update all libraries and dependencies to patch known vulnerabilities.
- Conduct thorough code reviews and security testing before deploying any application.
Malware Delivery Methods Targeting C# Streamers
C# streamers, like any software developers utilizing the .NET framework, face unique vulnerabilities when it comes to malware attacks. Their reliance on various tools, libraries, and online resources creates avenues for malicious actors to infiltrate their systems and potentially disrupt their streams or steal sensitive information. Understanding the common methods used to deliver malware is crucial for implementing effective security measures.
Malware delivery to C# streamers often leverages techniques common across the broader software development community, but with specific targeting towards the unique environment of live streaming. The impact can range from minor inconvenience to significant financial and reputational damage.
Phishing Attacks
Phishing remains a highly effective method for delivering malware. Attackers craft deceptive emails or messages pretending to be legitimate entities—software vendors, streaming platforms, or even fellow streamers—luring victims into clicking malicious links or opening infected attachments. These attachments often contain trojans or other malware designed to steal credentials, install keyloggers, or remotely control the victim’s system. A successful phishing attack against a streamer could lead to account compromise, theft of sensitive financial data, or even the disruption of their live stream. The effectiveness hinges on the sophistication of the phishing campaign and the vigilance of the target.
Drive-by Downloads
Drive-by downloads exploit vulnerabilities in web browsers or other software used by C# streamers. Visiting a compromised website or clicking a seemingly innocuous link can automatically download and install malware without the user’s explicit consent. This method is particularly insidious because it doesn’t require active user participation beyond browsing the internet. The impact can range from system instability to complete data loss, depending on the type of malware delivered. The effectiveness relies on the prevalence of unpatched vulnerabilities in the streamer’s software ecosystem.
Software Vulnerabilities
Outdated or vulnerable software packages, libraries, and frameworks used in the streamer’s C# projects present another significant attack vector. Malicious actors actively scan for known vulnerabilities, exploiting them to gain unauthorized access to the system. This could involve exploiting a flaw in a specific library used for streaming or a vulnerability in the operating system itself. The impact is directly tied to the severity of the exploited vulnerability. A successful exploit could allow attackers complete control over the system, leading to data theft, ransomware attacks, or the complete compromise of the streaming setup.
Exploiting Third-Party Tools and Plugins
Many C# streamers rely on third-party tools and plugins to enhance their streaming experience. These tools, if not properly vetted and maintained, can contain vulnerabilities that malicious actors can exploit. An attacker might inject malicious code into a seemingly legitimate plugin, gaining access to the streamer’s system through this indirect route. The impact can be significant, as these plugins often have broad access to system resources.
| Method | Target | Impact | Mitigation |
|---|---|---|---|
| Phishing | Streamer’s email account, credentials | Account compromise, data theft, malware installation | Security awareness training, strong passwords, multi-factor authentication, email filtering |
| Drive-by Downloads | Web browser, system vulnerabilities | Malware installation, system instability, data loss | Up-to-date antivirus software, regular software updates, cautious web browsing habits |
| Software Vulnerabilities | C# applications, libraries, frameworks, OS | System compromise, data theft, ransomware, stream disruption | Regular software updates, security audits, penetration testing, robust input validation |
| Exploiting Third-Party Tools | Streaming plugins, add-ons | Malware installation, data theft, system compromise | Careful selection of plugins, review of plugin permissions, regular updates, source code review (where possible) |
Windows Security Implications for C# Streamers
Securing your Windows environment is paramount for C# streamers, as a compromised system can lead to data breaches, account hijacking, and reputational damage. Malicious actors actively target streamers, leveraging vulnerabilities in both their applications and operating systems. Understanding and implementing robust security measures is crucial for maintaining a safe and productive streaming environment.
Protecting your Windows system from malware attacks aimed at C# applications requires a multi-layered approach. This goes beyond simply installing antivirus software; it involves proactively securing your system and regularly updating its defenses. Ignoring these steps significantly increases your vulnerability to attacks that could disrupt your stream, compromise your personal information, or even lead to legal repercussions.
Best Practices for Securing a Windows Environment for C# Streaming
Implementing strong security practices is essential to minimize the risk of malware infections. This includes using strong, unique passwords for all accounts, enabling two-factor authentication wherever possible, and regularly backing up your important data to an external drive or cloud service. Furthermore, avoiding suspicious links, downloads, and email attachments significantly reduces the chance of malware entering your system. Keeping your operating system and all software up-to-date is crucial for patching known vulnerabilities. Finally, consider using a virtual machine (VM) for streaming, isolating your main operating system from potential threats. In a VM scenario, if the VM is compromised, your main system remains untouched.
Windows Security Features and Malware Protection for C# Applications
Windows offers several built-in security features that can significantly enhance the protection of C# applications. Windows Defender, the built-in antivirus, provides real-time protection against malware. Windows Firewall controls network traffic, preventing unauthorized access to your system. User Account Control (UAC) prompts you before making significant system changes, preventing unauthorized modifications. AppLocker, a feature available in some Windows editions, allows you to control which applications can run on your system, limiting the potential impact of malware. Enabling these features and configuring them appropriately significantly reduces the attack surface for malicious actors.
The Importance of Regular Windows Updates and Security Patches
Regular updates and security patches are critical for protecting against malware. Microsoft regularly releases updates that address vulnerabilities in Windows and its components. These updates often include patches for security flaws that malware authors exploit. Failing to install these updates leaves your system vulnerable to known attacks. Setting up automatic updates ensures that your system is always protected against the latest threats. This simple yet effective practice is often overlooked, leaving many systems vulnerable to exploitation. Scheduling regular reboots to allow updates to install completely is also crucial.
Essential Security Software and Tools for C# Streamers on Windows
A robust security posture requires a combination of tools. Beyond Windows Defender, consider a reputable third-party antivirus program for an additional layer of protection. A strong password manager can help you create and manage complex, unique passwords for all your accounts. A firewall, either the built-in Windows Firewall or a third-party option, is essential for controlling network traffic. Regularly scanning your system with malware scanners and employing anti-malware software can help identify and remove threats. Finally, using a reputable VPN can provide an extra layer of security, especially when using public Wi-Fi networks. This comprehensive approach provides a robust defense against various malware threats.
Analyzing C# Malware Targeting Streamers
C#’s popularity in game development and streaming applications makes it a prime target for malware authors. Understanding the characteristics of this malware is crucial for streamers to protect their systems and data. This analysis focuses on the common traits, techniques, and detection methods related to C# malware specifically designed to exploit vulnerabilities within the streaming ecosystem.
Malware targeting C# streamers on Windows often shares common characteristics, primarily leveraging vulnerabilities within the streaming application itself or exploiting weaknesses in the broader Windows environment. These malicious programs frequently employ techniques designed to remain undetected, steal sensitive information like login credentials and API keys, or disrupt live streams for malicious purposes. The methods used are often sophisticated, requiring a deep understanding of both C# programming and Windows security to effectively mitigate.
Common Characteristics of C# Streamer Malware
Several recurring characteristics are observed in C# malware targeting streamers. These include obfuscation techniques to hide the malware’s true purpose, use of legitimate libraries for camouflage, and the exploitation of known vulnerabilities in streaming software or associated plugins. Furthermore, many samples exhibit persistence mechanisms, ensuring their continued presence on the infected system, and often include self-propagation capabilities to spread to other systems.
Examples of Malicious Code Snippets
While providing complete malicious code snippets is irresponsible and could be misused, we can illustrate typical malicious patterns. For example, a keylogger might utilize a `System.Windows.Forms.SendKeys` method to capture keystrokes, sending the captured data to a remote server. Another example might involve a hidden process that monitors network traffic for API keys or authentication tokens, using libraries like `System.Net.Sockets` to achieve this. These snippets often leverage techniques like string encryption and code obfuscation to hinder reverse engineering.
Example (Conceptual – DO NOT USE): A simplified illustration of data exfiltration could involve:
string apikey = GetApiKey(); SendDataToServer(apikey);This illustrates the fundamental concept of retrieving sensitive information and sending it to a remote location. The actual implementation would be far more complex and obfuscated.
Data Theft and System Compromise Techniques
C# streamer malware frequently employs various techniques to steal data and compromise systems. These include keylogging (as mentioned above), process injection (injecting malicious code into legitimate processes), and the exploitation of vulnerabilities in streaming software or plugins to gain elevated privileges. Additionally, some malware uses techniques to disable security software or manipulate system settings to hinder detection and removal.
Identifying Suspicious Activities in C# Streaming Application Code
Identifying suspicious activities requires careful examination of the application’s codebase. Look for unusual network connections, particularly those to unknown or suspicious domains. Analyze the use of external libraries and ensure their legitimacy. The presence of unexpected functions related to data encryption, keylogging, or system manipulation should raise concerns. Obfuscation or code complexity that seems unnecessary should also trigger investigation. Regular code reviews and the use of static analysis tools can significantly aid in detecting malicious code.
Mitigation and Response Strategies
Source: fortinet.com
So, your C# streaming setup has been hit by malware. Panic isn’t productive; a swift, organized response is key. This section Artikels strategies to minimize damage and get back online. Think of it as your emergency streaming survival guide.
A comprehensive incident response plan is crucial for minimizing downtime and data loss. It’s not just about reacting to an attack; it’s about proactively preparing for one. A well-defined plan ensures a coordinated and efficient response, reducing the impact of a malware infection.
Incident Response Plan for C# Streaming Malware Attacks
An effective incident response plan involves several key stages. First, detection: This involves setting up monitoring tools to identify unusual activity on your system. Next, containment: Isolate the infected system from your network to prevent the malware from spreading. Eradication: Thoroughly remove the malware using appropriate tools and techniques. Recovery: Restore your system to a clean state from a backup. Post-incident activity: Analyze the attack to identify vulnerabilities and implement preventative measures. Regular testing of the plan is essential to ensure its effectiveness. Consider involving cybersecurity professionals for complex situations.
Step-by-Step Malware Recovery Guide for C# Streamers
Imagine this: Your stream is down, and you suspect malware. Here’s your recovery roadmap. First, disconnect from the internet immediately to prevent further damage. Second, boot into safe mode. This limits the processes running, hindering the malware’s activity. Third, run a full system scan with a reputable antivirus program. Fourth, remove any identified malware files. Fifth, restore your system from a recent backup. Sixth, change all your passwords. Finally, update your software and security patches.
Best Practices for Data Backup and Recovery in C# Streaming Environments
Data loss is a streamer’s nightmare. Regular backups are non-negotiable. Implement a robust backup strategy involving multiple backups stored in different locations – ideally, both on-site and off-site. Consider cloud-based solutions for off-site backups. Regularly test your backups to ensure they’re functional. Use version control for your C# code, allowing you to revert to previous versions if necessary. Implement a clear backup schedule and document your procedures meticulously.
Immediate Actions Following a Suspected Malware Infection
Time is of the essence. Your immediate actions can significantly impact the extent of the damage. First, disconnect from the internet immediately. Second, document everything – take screenshots of error messages, note any unusual behavior. Third, run a malware scan with updated antivirus software. Fourth, identify any compromised accounts and change the passwords. Fifth, contact your IT support or a cybersecurity professional for assistance. Sixth, consider reporting the incident to relevant authorities, depending on the severity and nature of the attack. This swift response can prevent a minor incident from becoming a major catastrophe.
The Role of Streaming Software in Malware Attacks: Csharp Streamer Malware Attack Windows
Source: slideplayer.com
Streaming software, while offering incredible entertainment and connection opportunities, presents a significant attack vector for malware. Its popularity and the often-complex interactions with operating systems and other software create vulnerabilities that malicious actors can exploit to gain unauthorized access to a user’s system. This can range from simple data theft to full-system compromise, resulting in significant financial and personal losses.
Streaming software vulnerabilities are frequently exploited because they often require extensive system privileges to function correctly, giving malware a high degree of access. Furthermore, the constant updates and diverse plugins used in streaming frequently introduce new attack surfaces. A poorly secured plugin, for instance, could allow malware to infiltrate the system undetected.
Vulnerabilities in Popular Streaming Software and Their Exploitation
Many popular streaming platforms rely on third-party plugins and extensions to enhance functionality. These add-ons, while offering convenience, often introduce security risks. A vulnerability in a single plugin can compromise the entire streaming application and potentially the entire operating system. Malicious actors can craft plugins containing malicious code that executes when the plugin is installed or activated. This code can then steal login credentials, install keyloggers, or even deploy ransomware. For example, a seemingly harmless streaming enhancement plugin might secretly upload user data to a remote server or install a crypto-miner, degrading system performance without the user’s knowledge. This highlights the importance of carefully vetting all plugins and extensions before installation.
Security Risks Associated with Third-Party Plugins and Extensions
Using third-party plugins and extensions for streaming software introduces several security risks. These risks include, but are not limited to: malware injection, data theft, unauthorized access, and system instability. Malicious plugins might be disguised as legitimate tools, making it difficult for users to distinguish between safe and unsafe extensions. Furthermore, outdated plugins can contain known vulnerabilities that attackers actively exploit. Regularly updating streaming software and its plugins is crucial but often overlooked, creating a persistent security risk. A lack of proper security measures in the development process of these plugins can also lead to vulnerabilities that are easily exploited.
Choosing Secure and Reputable Streaming Software and Plugins
Selecting secure and reputable streaming software and plugins requires careful consideration. Users should prioritize well-known and established brands with a proven track record of security updates and responsiveness to vulnerability reports. Checking online reviews and security ratings from independent sources can provide valuable insights into the software’s safety and reliability. Always download software from the official website or trusted app stores to avoid malicious imitations. Prioritizing plugins from reputable developers with a history of secure coding practices is also essential. Regularly checking the plugin’s permissions and uninstalling unused plugins can further reduce the attack surface.
Recommendations for Safely Using Streaming Software
To minimize malware risks when using streaming software, consider the following recommendations:
- Always download streaming software and plugins from official sources.
- Keep your streaming software and operating system updated with the latest security patches.
- Regularly review and update the permissions granted to plugins and extensions.
- Uninstall any unused or suspicious plugins immediately.
- Use a reputable antivirus and anti-malware solution and keep it updated.
- Be cautious when clicking on links or downloading files from unknown sources, especially those associated with streaming.
- Enable two-factor authentication whenever possible on your streaming accounts.
- Regularly back up your important data to protect against data loss from malware attacks.
Last Point
So, you’ve learned about the real dangers lurking in the digital world for C# streamers. Remember, a proactive approach to security is key. By understanding the common vulnerabilities, implementing secure coding practices, and staying updated on the latest threats, you can significantly reduce your risk. Don’t let malware ruin your stream – empower yourself with knowledge and secure your digital castle. Keep streaming, but stream smart!



