HC3 unveils Qilin ransomware—a new, nasty piece of malware shaking up the cybersecurity world. This isn’t your grandpappy’s ransomware; Qilin boasts sophisticated encryption and a cunning infrastructure, leaving victims scrambling for answers. We’re diving deep into the technical details, exploring the group’s history, and outlining strategies to dodge this digital bullet.
From its technical intricacies to the geopolitical implications, we’ll unpack everything you need to know about this emerging threat. Get ready to understand how Qilin works, who’s behind it, and what you can do to protect yourself and your data. The stakes are high, and understanding the enemy is the first step to victory.
HC3 Group and its Activities
The HC3 Group, a shadowy player in the cybercrime underworld, has made a name for itself through sophisticated ransomware attacks. While maintaining a low profile, their operations reveal a well-organized and adaptable group capable of significant damage. Their recent deployment of the Qilin ransomware underscores their continued threat and warrants a closer examination of their history and modus operandi.
HC3’s activities are characterized by a focus on high-value targets, suggesting a financially driven motivation. Their operations are meticulously planned, demonstrating a high level of technical expertise and an understanding of their victims’ security infrastructure. This allows them to maximize their impact and minimize the chances of detection and apprehension. The group’s adaptability is also noteworthy, as they’ve demonstrated the ability to switch ransomware strains and refine their techniques over time, making them a persistent and evolving threat.
HC3’s Previous Ransomware Campaigns
HC3’s history includes several significant ransomware campaigns, each demonstrating a pattern of targeting specific industries and utilizing varying techniques to achieve their objectives. While precise details about their earlier campaigns remain scarce due to the group’s clandestine nature, information gathered from security researchers and incident reports suggests a preference for organizations with sensitive data and a willingness to pay ransoms. The impact of these campaigns has included data breaches, operational disruptions, and substantial financial losses for victims. One notable example, although details are limited due to non-disclosure agreements, involved a major manufacturing company experiencing significant downtime and paying a substantial ransom to regain access to their systems. The incident resulted in a loss of productivity and damaged reputation for the victim.
Comparison of Qilin Ransomware with Other HC3 Strains
While the exact details of all ransomware strains used by HC3 remain incomplete, comparing Qilin to publicly known examples reveals certain similarities and differences. For instance, some researchers speculate that Qilin shares some code similarities with previous HC3 ransomware variants, suggesting a possible evolution rather than a complete shift in their toolkit. However, Qilin’s encryption methods and exfiltration techniques might be more sophisticated, potentially making recovery more difficult for victims. The key difference often lies in the specific encryption algorithms employed, the level of data exfiltration, and the ransom demands. The sophistication of the ransomware may also increase over time, reflecting the group’s continuous refinement of its tactics.
HC3’s Typical Targets and Motivations
HC3 predominantly targets organizations in sectors with valuable data and a high tolerance for paying ransoms. This includes, but is not limited to, manufacturing, healthcare, and financial services. Their motivations are primarily financial, aiming to maximize profits from ransom payments. The group likely conducts extensive reconnaissance before selecting targets, ensuring that the potential payoff outweighs the risks involved. This targeted approach suggests a high level of professionalism and planning within the group’s operations. Their actions indicate a strong understanding of the vulnerabilities within targeted industries and the potential impact of their attacks.
Timeline of Significant HC3 Events
Creating a precise timeline for HC3’s activities is challenging due to the limited publicly available information. However, based on available data from security researchers and news reports, a partial timeline can be constructed:
While specific dates are difficult to confirm, a pattern emerges: initial attacks may have been less sophisticated, focusing on simpler encryption techniques and smaller ransom demands. Over time, the attacks have become more targeted, using more advanced encryption and incorporating data exfiltration to increase pressure on victims. The emergence of Qilin represents the latest chapter in this evolution, showcasing HC3’s continued adaptation and refinement of its methods.
Qilin Ransomware Technical Analysis

Source: cloudfront.net
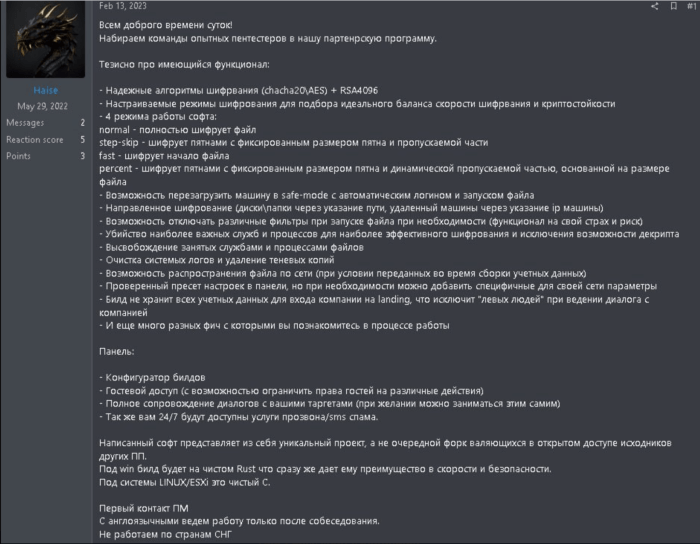
Qilin ransomware, a sophisticated piece of malware attributed to the HC3 Group, presents a significant threat due to its robust encryption, resilient infrastructure, and evasive techniques. Understanding its technical intricacies is crucial for developing effective countermeasures. This analysis delves into the core functionalities and architecture of Qilin, providing insights into its operation and potential mitigation strategies.
Encryption Methods
Qilin employs a hybrid encryption approach, combining symmetric and asymmetric encryption algorithms for enhanced security. The specific algorithms used haven’t been publicly disclosed in detail, but analysis suggests the use of a strong symmetric algorithm like AES (Advanced Encryption Standard) for encrypting files, providing speed and efficiency. The asymmetric component, likely RSA or ECC (Elliptic Curve Cryptography), is then used to encrypt the symmetric key, ensuring only the attackers with the private key can decrypt the files. This two-pronged approach makes brute-forcing the encryption key significantly harder than relying solely on symmetric encryption. The strength of the encryption relies heavily on the key length used for both AES and the asymmetric algorithm. Longer key lengths exponentially increase the difficulty of decryption without the proper key.
Command-and-Control Infrastructure and Communication Protocols
Qilin’s command-and-control (C2) infrastructure is designed for resilience and anonymity. The attackers likely utilize a distributed network of servers, potentially employing techniques like domain generation algorithms (DGAs) to generate dynamic domain names, making them harder to track and block. Communication protocols used are likely to be encrypted and obfuscated, possibly leveraging HTTPS or custom protocols to evade detection. The use of multiple layers of proxies and VPNs further complicates tracing the communication channels back to the attackers. This decentralized approach makes it difficult to take down the C2 infrastructure with a single takedown action, requiring a multi-pronged approach involving sinkholing domains, disrupting network infrastructure, and working with internet service providers to take down malicious servers.
Malware Code Structure and Components
The Qilin ransomware code likely comprises several modules, each responsible for a specific task. A core module handles the encryption process, another manages the communication with the C2 server, and additional modules may handle tasks such as file searching, ransom note creation, and self-propagation. The code is likely written in a compiled language like C++ or Go, chosen for their performance and cross-platform compatibility. The use of anti-analysis techniques, such as code obfuscation, packing, and polymorphism, would further hinder reverse engineering efforts. These techniques make it difficult for security researchers to fully understand the ransomware’s inner workings and create effective countermeasures. Analyzing samples requires advanced techniques, including unpacking, deobfuscation, and dynamic analysis.
Mitigation Strategy
A comprehensive mitigation strategy against Qilin ransomware necessitates a multi-layered approach. Regular backups are paramount, preferably using the 3-2-1 rule (3 copies of data, on 2 different media, with 1 offsite copy). Robust endpoint detection and response (EDR) solutions, coupled with advanced threat protection, are vital for detecting and blocking malicious activity. Keeping software updated and patching vulnerabilities promptly minimizes the attack surface. Security awareness training for employees is crucial to prevent phishing attacks and other social engineering attempts, as these are often the initial vectors for ransomware infections. Network segmentation can limit the impact of a successful infection, preventing the ransomware from spreading laterally. Finally, implementing a strong incident response plan allows for swift containment and recovery in case of an infection. Regular security audits and penetration testing further help identify and address vulnerabilities.
Impact and Response to Qilin Attacks
Source: group-ib.com
The Qilin ransomware, despite its relatively recent emergence, has already left a trail of disruption across various sectors. Understanding the impact of these attacks and the responses implemented is crucial for developing effective preventative measures and mitigation strategies. This section details the consequences of Qilin attacks, the responses from affected organizations and law enforcement, and the challenges encountered during incident response.
While precise figures on the number of Qilin attacks remain elusive due to the often-unreported nature of ransomware incidents, available information paints a concerning picture. The attacks have targeted a range of organizations, leading to significant financial losses, operational downtime, and reputational damage. The decentralized nature of the threat actors behind Qilin further complicates the situation, making attribution and effective countermeasures challenging.
Reported Qilin Ransomware Attacks and Their Consequences
The following table summarizes some reported Qilin ransomware attacks, highlighting the industries affected, geographical locations, and the ransom demands. Note that due to the sensitive nature of these incidents, complete details are often unavailable publicly. The information presented below represents a compilation of publicly available reports and news articles.
| Industry | Location | Ransom Demand (USD) | Consequences |
|---|---|---|---|
| Manufacturing | United States | $500,000 | Significant production downtime, data loss, potential supply chain disruptions. Negotiations with the attackers resulted in a partial data recovery. |
| Healthcare | Germany | $250,000 | Disruption of patient care, delays in medical procedures, potential compromise of sensitive patient data. The organization chose not to pay the ransom and instead focused on data recovery and system restoration. |
| Financial Services | United Kingdom | $1,000,000 | Operational disruption, potential financial losses due to system downtime and data breaches. Law enforcement was involved in the investigation. |
| Education | Canada | $100,000 | Disruption of academic activities, potential loss of student and faculty data. The institution opted to rebuild systems from backups and reported the incident to authorities. |
Responses of Affected Organizations and Law Enforcement Agencies
Affected organizations have employed a variety of responses to Qilin ransomware attacks, ranging from paying the ransom (a decision often discouraged by law enforcement) to restoring systems from backups and engaging cybersecurity experts for incident response and remediation. Law enforcement agencies have played a crucial role in investigating these attacks, working to identify and apprehend the perpetrators, and providing guidance and support to victims. International cooperation has also been vital in tracking down the threat actors operating across borders.
Impact on Victims’ Operations
The impact of Qilin ransomware attacks extends far beyond simple data encryption. Victims often experience significant operational disruptions, including:
* Data Loss: Irrecoverable data loss, leading to potential financial losses and business disruption.
* System Downtime: Extended periods of system unavailability, impacting productivity and revenue.
* Reputational Damage: Negative publicity and loss of customer trust.
* Financial Losses: Costs associated with ransom payments (if paid), data recovery, system restoration, legal fees, and business interruption.
* Legal and Regulatory Compliance Issues: Potential breaches of data protection regulations and subsequent penalties.
Challenges in Responding to Qilin Ransomware Attacks
Responding to Qilin ransomware attacks presents several significant challenges:
* Rapid Encryption: The speed at which Qilin encrypts data often leaves little time for intervention.
* Data Recovery Complexity: Recovering encrypted data can be extremely difficult and time-consuming, even with backups.
* Attribution Difficulty: Identifying and tracking the threat actors behind Qilin is challenging due to their decentralized nature and use of sophisticated techniques.
* Lack of Public Information: Limited public information on Qilin’s tactics, techniques, and procedures (TTPs) hinders the development of effective countermeasures.
* Sophisticated Evasion Techniques: Qilin employs advanced techniques to evade detection and hinder incident response efforts.
Prevention and Mitigation Strategies
Source: dailysecurityreview.com
Protecting your organization from ransomware like Qilin requires a multi-layered approach. A robust cybersecurity strategy isn’t just about reacting to attacks; it’s about proactively minimizing the risk of infection and ensuring swift recovery if an incident does occur. This involves a combination of technical safeguards, employee training, and a well-defined incident response plan.
The following best practices offer a strong foundation for preventing Qilin ransomware and similar threats.
Best Practices for Preventing Qilin Ransomware Infections
Implementing these practices significantly reduces the likelihood of a successful ransomware attack. A layered approach, combining multiple strategies, is key to robust protection.
- Maintain Updated Software: Regularly update all software, including operating systems, applications, and firmware. Outdated software often contains vulnerabilities that ransomware can exploit. Enable automatic updates whenever possible.
- Employ Strong Passwords and Multi-Factor Authentication (MFA): Use strong, unique passwords for all accounts and enable MFA wherever available. MFA adds an extra layer of security, making it much harder for attackers to gain unauthorized access.
- Restrict Administrative Privileges: Limit the number of users with administrative privileges. Malicious software often requires administrative rights to install and operate effectively.
- Regularly Patch Systems: Patching systems promptly addresses known vulnerabilities, preventing attackers from exploiting them. This includes both operating systems and applications.
- Use a Reputable Antivirus and Endpoint Detection and Response (EDR) Solution: A robust antivirus solution, combined with an EDR system, provides real-time protection and threat detection capabilities.
- Implement Network Segmentation: Segmenting your network limits the impact of a breach. If one segment is compromised, the rest of the network is less likely to be affected.
- Regularly Back Up Data: Regular backups are crucial for data recovery in the event of a ransomware attack. Employ the 3-2-1 backup rule: three copies of your data, on two different media types, with one copy offsite.
- Control Access to Sensitive Data: Implement strict access control measures to limit who can access sensitive data. This reduces the risk of data exfiltration even if a system is compromised.
- Educate Employees on Phishing and Social Engineering: Many ransomware attacks begin with phishing emails or social engineering tactics. Regular security awareness training is vital.
The Importance of Regular Backups and Data Recovery Plans, Hc3 unveils qilin ransomware
Data backups are not just a good idea; they’re a necessity in today’s threat landscape. A comprehensive data recovery plan, tested regularly, is critical for minimizing downtime and data loss following a ransomware attack.
Regular backups, stored offline and in a geographically separate location, are the best defense against data loss. A well-defined recovery plan Artikels the steps to restore systems and data, minimizing business disruption. This plan should include details on recovery time objectives (RTOs) and recovery point objectives (RPOs), specifying acceptable downtime and data loss thresholds.
The Role of Security Awareness Training in Mitigating Ransomware Attacks
Human error remains a significant vulnerability in cybersecurity. Employees often fall victim to phishing scams and social engineering tactics, leading to ransomware infections. Comprehensive security awareness training empowers employees to identify and avoid these threats.
Training should cover topics such as phishing email recognition, safe browsing practices, strong password creation, and the importance of reporting suspicious activity. Regular simulated phishing campaigns help assess employee awareness and reinforce training effectiveness. Remember, a well-informed employee is the first line of defense against ransomware.
Benefits of Employing Advanced Threat Detection and Response Solutions
Advanced threat detection and response (ATDR) solutions provide proactive protection against sophisticated threats like Qilin ransomware. These solutions go beyond traditional antivirus software by employing machine learning and behavioral analysis to identify and respond to threats in real time.
ATDR solutions offer several key benefits, including early threat detection, automated incident response, and reduced dwell time (the time between initial compromise and detection). They can analyze network traffic, endpoint activity, and user behavior to identify suspicious patterns and alert security teams to potential threats. This allows for faster response and mitigation of attacks, minimizing damage and downtime.
A Comprehensive Cybersecurity Strategy to Minimize Ransomware Risk
A comprehensive strategy combines multiple layers of defense to minimize the risk of ransomware attacks. It’s not a one-size-fits-all solution; it requires tailoring to your organization’s specific needs and risk profile.
This strategy should include regular security assessments, vulnerability scanning, penetration testing, incident response planning, and employee training. It’s crucial to establish clear roles and responsibilities for incident response and to regularly test and update the plan. Investing in advanced security technologies, such as EDR and SIEM solutions, further enhances the effectiveness of the strategy. Regular review and adaptation are essential to ensure the strategy remains effective in the face of evolving threats.
Attribution and Geopolitical Implications
The attribution of cyberattacks, especially sophisticated ransomware campaigns like the one orchestrated by the HC3 Group using Qilin ransomware, is a complex and often murky affair. Pinpointing the exact origin and motivations requires meticulous investigation, piecing together digital breadcrumbs scattered across the globe. While definitive attribution remains challenging, analyzing the attack vectors, infrastructure, and operational techniques can offer valuable clues about the perpetrators and their potential geopolitical agendas.
The limited publicly available information makes definitively identifying the geographic location of the HC3 group difficult. However, certain indicators, such as the language used in the ransomware notes, the time zones of observed activity, and the infrastructure’s digital fingerprints, could potentially point towards a specific region or country. Investigative efforts often focus on identifying overlaps with known threat actor groups, infrastructure used in past attacks, and the overall sophistication of the techniques employed. Such analysis, when coupled with intelligence gathering, can narrow down the field of potential suspects.
Potential Origin and Geographic Location of HC3 Group
While precise geolocation is currently unavailable due to the clandestine nature of these operations, analysts often look for patterns. For instance, the use of specific servers located in certain countries, the language used in malware code, or the targets of the attacks can all offer hints. If the HC3 group targets specific industries or governments within a particular region, it could strongly suggest a geographical connection. Further analysis of the group’s infrastructure, including IP addresses and domain registrations, could help to triangulate their location. This often requires collaboration between cybersecurity firms, governments, and intelligence agencies.
Geopolitical Implications of the Qilin Ransomware Campaign
The Qilin ransomware campaign, like many sophisticated cyberattacks, carries significant geopolitical implications. The targeting of specific sectors—be it healthcare, critical infrastructure, or government entities—can destabilize targeted nations, disrupting essential services and potentially impacting national security. The potential for escalation is high, particularly if the attacks are perceived as state-sponsored. Attribution, or the lack thereof, can strain international relations, potentially leading to diplomatic tensions or even retaliatory actions. The economic impact, considering the financial losses incurred by victims, also plays a significant role in the broader geopolitical landscape.
Comparison with Other State-Sponsored Cyberattacks
Comparing Qilin attacks to other known state-sponsored cyberattacks reveals similarities and differences in techniques, targets, and motivations. For example, some state-sponsored attacks focus on espionage, aiming to steal sensitive data, while others, like Qilin, may prioritize disruption and financial gain. The level of sophistication, the use of advanced persistent threats (APTs), and the choice of targets can also offer clues about the potential state actors involved. Analyzing the technical aspects of the attacks—the malware’s code, the command-and-control infrastructure, and the evasion techniques—allows for comparison with known tactics, techniques, and procedures (TTPs) associated with specific nation-state actors. Examples such as NotPetya and SolarWinds attacks provide useful benchmarks for comparative analysis.
Motivations Behind the Qilin Attacks
The motivations behind the Qilin attacks could be multifaceted. Financial gain is a primary driver for many ransomware campaigns, but state-sponsored actors might have additional geopolitical objectives. These could include disrupting critical infrastructure, undermining national security, conducting espionage, or spreading disinformation. The attackers’ targets and the ransom demands provide clues. For example, targeting a specific industry might suggest an attempt to destabilize that sector within a targeted nation. Similarly, the amount and method of ransom payment can also offer insights into the attackers’ motivations. Understanding these motivations requires a comprehensive analysis of the campaign’s overall strategy and the context in which the attacks occurred.
Challenges in Attributing Cyberattacks to Specific Actors
Attributing cyberattacks with certainty is notoriously difficult. Threat actors often employ advanced techniques to mask their identities and origins, using proxies, anonymizing tools, and sophisticated evasion tactics. The decentralized and global nature of the internet further complicates attribution efforts. The lack of clear evidence, the difficulty in obtaining legal cooperation across borders, and the sheer volume of cyberattacks all contribute to the challenge. The process often involves analyzing a vast amount of data, including network traffic, malware samples, and digital forensics, requiring significant resources and expertise. This complexity often leaves attribution uncertain, leading to ongoing debates and investigations.
Visual Representation of Qilin Ransomware’s Lifecycle: Hc3 Unveils Qilin Ransomware
Understanding the lifecycle of Qilin ransomware is crucial for effective prevention and mitigation. Visualizing this process helps security professionals and organizations anticipate attack vectors and develop robust defense strategies. This section provides a detailed breakdown of the various stages, from initial infection to the final ransom demand.
Qilin Ransomware Infection Process
The Qilin ransomware infection process typically begins with a malicious payload delivered through various means. This payload then executes, initiating the encryption process.
The initial infection vector might involve phishing emails containing malicious attachments, exploiting software vulnerabilities, or leveraging compromised credentials to gain unauthorized access to systems.
Once executed, the ransomware quickly scans the system for target files, employing specific file extensions as criteria. It then encrypts these files using a strong encryption algorithm, rendering them inaccessible.
Following encryption, the ransomware may delete shadow copies to prevent data recovery attempts and leave behind a ransom note detailing the attack and instructions for payment.
Qilin Ransomware Deployment and Spread
Attackers employ various methods to deploy and spread the Qilin ransomware, often targeting organizations with less robust security measures.
Phishing emails remain a primary vector, using deceptive subject lines and attachments designed to trick users into executing malicious code.
Exploiting known vulnerabilities in software applications allows attackers to gain initial access to systems without user interaction. This often involves leveraging publicly available exploits or zero-day vulnerabilities.
Compromised credentials obtained through previous breaches or social engineering tactics can provide attackers with direct access to systems, bypassing traditional security controls.
Qilin Ransomware Encryption and Decryption Challenges
Qilin ransomware utilizes sophisticated encryption techniques to ensure data inaccessibility. Recovering data without the decryption key presents significant challenges.
The ransomware likely employs a robust symmetric encryption algorithm, such as AES or ChaCha20, for encrypting files individually. This ensures that even if one file’s encryption is broken, others remain secure.
The encryption process often involves generating a unique key for each victim, making mass decryption efforts impractical. Furthermore, the encryption key is often stored on the attacker’s server, making it inaccessible to victims.
Decryption typically requires the attacker’s decryption key, which is only provided after the ransom is paid. However, there’s no guarantee that the attackers will provide the key even after payment.
Qilin Ransomware Communication and Ransom Demand
The attackers employ various methods to communicate with victims and demand payment of the ransom.
The ransom note, typically a text file left on the compromised system, details the attack, the amount of ransom demanded, and instructions on how to pay. This note often includes a unique identifier for the victim.
The attackers may also use encrypted communication channels, such as Tor hidden services, to maintain anonymity and avoid detection. This makes tracing the attackers more difficult.
The ransom is typically demanded in cryptocurrency, such as Bitcoin, to enhance anonymity and make tracing the payment more difficult. The ransom amount varies depending on factors like the size and sensitivity of the compromised data.
Wrap-Up
The unveiling of Qilin ransomware by the HC3 group highlights the ever-evolving landscape of cyber threats. Understanding its technical capabilities, the group’s modus operandi, and proactive mitigation strategies are crucial for organizations and individuals alike. Staying informed and adapting to these emerging threats is no longer optional; it’s a necessity in today’s digital world. The fight against ransomware is ongoing, but with knowledge and preparedness, we can minimize its impact.



