Windows XSS flaw: Sounds scary, right? It should. Cross-site scripting (XSS) vulnerabilities on Windows systems are a serious threat, allowing attackers to inject malicious scripts into web pages viewed by unsuspecting users. This can lead to everything from stolen credentials to complete system compromise. We’re diving deep into the nitty-gritty of these flaws, exploring how they work, how to spot them, and most importantly, how to stop them dead in their tracks.
From reflected and stored XSS attacks to the more insidious DOM-based variants, we’ll dissect the various ways these vulnerabilities can exploit weaknesses in Windows web applications. We’ll explore common sources like improper input validation, outdated software, and insufficient output encoding. Think of this as your survival guide to navigating the treacherous waters of Windows XSS.
Introduction to Windows XSS Flaws
Source: imperva.com
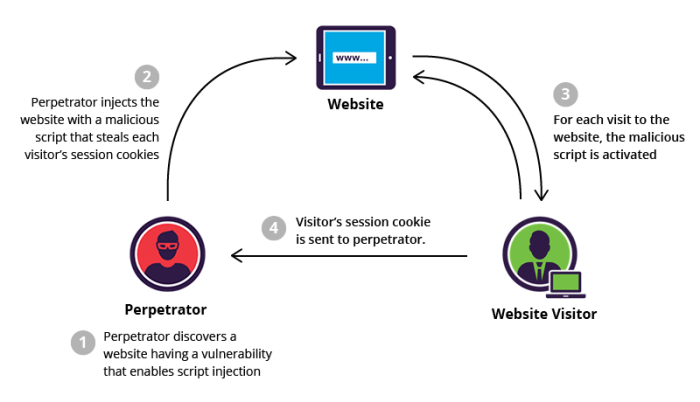
Cross-Site Scripting (XSS) vulnerabilities are a sneaky type of web attack that allows malicious actors to inject client-side scripts into otherwise benign websites. These scripts can then be executed in the victim’s browser, potentially stealing sensitive information, redirecting users to phishing sites, or even taking control of the user’s system. While often associated with web applications, XSS flaws can also manifest in Windows environments, particularly within applications that interact with web technologies or handle user-supplied data without proper sanitization. The impact can be significant, especially in enterprise settings.
XSS vulnerabilities in Windows environments often arise from applications that process user input, such as web-based administration panels, internal portals, or applications that embed web browsers. These applications might not adequately validate or sanitize data received from external sources, leaving them open to exploitation. The attack surface expands significantly when considering the diverse applications running on a Windows machine, ranging from web servers to desktop applications that utilize web components. Failing to address these vulnerabilities can lead to serious security breaches.
Types of XSS Vulnerabilities in Windows
The classification of XSS vulnerabilities remains consistent across different operating systems, including Windows. Understanding these categories is crucial for effective mitigation.
| Vulnerability Type | Description | Example Code Snippet (Illustrative) | Mitigation Strategy |
|---|---|---|---|
| Reflected XSS | The attacker’s malicious script is reflected back to the user’s browser from the server. This often happens in search queries or form submissions where user input is directly displayed without proper encoding. | http://example.com/search?q= (Imagine this query being echoed back on the page without encoding) |
Encode all user-supplied data before displaying it on the page using appropriate encoding mechanisms (e.g., HTML encoding). Validate all input rigorously to prevent unexpected characters. |
| Stored XSS (Persistent XSS) | The attacker’s malicious script is stored on the server, typically in a database. This script is then executed whenever a user accesses the affected page or content. Examples in a Windows context might include comments sections on an internal application or data entered into a database-driven application. | (Illustrative: Imagine a comment field in an internal application where a user inputs |
Sanitize all data stored in databases before displaying it to users. Implement input validation and output encoding. Regularly audit databases for suspicious content. |
| DOM-Based XSS | The malicious script is executed within the client-side browser’s Document Object Model (DOM). This doesn’t involve the server directly; the vulnerability lies in how the client-side JavaScript handles user input. A Windows application utilizing a webview component could be susceptible. | (Illustrative: A JavaScript function in a Windows application might directly use user input from a form field to update the DOM without proper encoding. The input could contain malicious JavaScript code.) | Use a robust JavaScript framework that handles input sanitization automatically. Validate and sanitize all user input before using it to manipulate the DOM. |
Common Sources of Windows XSS Flaws
Cross-site scripting (XSS) vulnerabilities in Windows web applications aren’t unique to the operating system itself; instead, they stem from insecure coding practices and configurations within the applications running on it. These flaws offer attackers a pathway to inject malicious scripts into otherwise legitimate web pages, potentially stealing user data, hijacking sessions, or defacing websites. Let’s delve into the common culprits.
Several components within Windows web applications frequently contribute to XSS vulnerabilities. These vulnerabilities aren’t inherent to Windows itself, but rather arise from how applications are built and maintained. Understanding these common sources is crucial for mitigating the risk.
Improper Input Validation
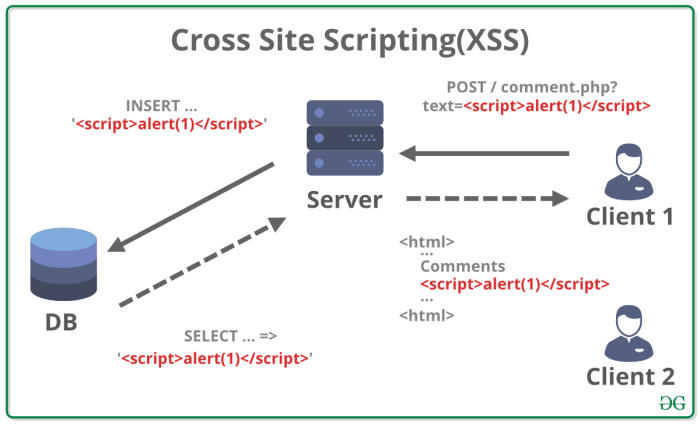
Insufficient input validation is a primary cause of XSS vulnerabilities. Web applications often accept user-supplied data—from login credentials to search queries—without properly sanitizing or validating it. If an application fails to filter or escape special characters like `<`, `>`, `’`, and `”` within user input before storing or displaying it, an attacker can inject malicious JavaScript code. For example, if a website allows users to enter their name in a profile field and then displays it directly without encoding, an attacker could enter `` as their name, causing the browser to execute the malicious script. This results in a reflected XSS attack, where the injected script is immediately reflected back to the user. Persistent XSS attacks, where the malicious script is stored on the server and executed later, are also possible if the input is not properly sanitized before storage.
Outdated Software and Libraries, Windows xss flaw
Using outdated software and libraries significantly increases the risk of XSS vulnerabilities. Older versions often contain known security flaws that have been patched in newer releases. These vulnerabilities can provide easy entry points for attackers. For instance, an outdated content management system (CMS) or a vulnerable web framework might have XSS vulnerabilities that have been addressed in later versions. Regularly updating software and libraries is a crucial step in protecting against these vulnerabilities. Failing to do so leaves your application exposed to attacks that could have been easily prevented.
Insufficient Output Encoding
Even with proper input validation, insufficient output encoding can still lead to XSS vulnerabilities. Output encoding is the process of converting special characters into their HTML entities. For example, the `<` character should be encoded as `<`, preventing it from being interpreted as the start of an HTML tag. Failure to properly encode data before displaying it on a web page allows attackers to inject malicious scripts. This is particularly critical when dealing with data that's dynamically generated and displayed on a web page, such as user comments, forum posts, or search results. The application should consistently encode all user-supplied data before displaying it, regardless of the input validation already performed.
Exploiting Windows XSS Flaws
So, you’ve identified a Cross-Site Scripting (XSS) vulnerability in a Windows-based web application. Now what? Knowing *where* the vulnerability lies is only half the battle; exploiting it effectively requires a strategic approach tailored to the specific type of XSS flaw. Let’s dive into the nitty-gritty of turning vulnerability discovery into actionable exploitation. Remember, ethical hacking and responsible disclosure are key – only test vulnerabilities on systems you have explicit permission to test.
Exploiting XSS vulnerabilities hinges on injecting malicious scripts into the application’s context, tricking the victim’s browser into executing them. The impact can range from stealing session cookies to gaining complete control over the victim’s machine. The methods for exploitation differ slightly depending on whether the vulnerability is reflected, stored, or DOM-based.
Reflected XSS Exploitation in Windows Web Applications
A reflected XSS vulnerability allows an attacker to inject malicious scripts into a web application’s URL parameters or form data. The application then reflects this malicious script back to the victim’s browser, which subsequently executes it. Exploitation typically involves crafting a malicious URL containing a JavaScript payload. For instance, if a search function is vulnerable, an attacker might craft a URL like `http://vulnerable-site.com/search?query=`. When a victim clicks this link, the browser will execute the alert, proving the vulnerability. More sophisticated attacks could steal cookies or redirect the victim to a phishing site. The key here is understanding how the application processes user input and crafting a payload that leverages this processing.
Stored XSS Exploitation for User Account Compromise
Stored XSS, also known as persistent XSS, is more dangerous. Malicious scripts are stored permanently on the server, usually within a database. Every user who views the affected content triggers the execution of the malicious script. Exploiting a stored XSS vulnerability to compromise user accounts often involves injecting a script that steals session cookies or other authentication tokens. This could be achieved by embedding a script within a comment field or a forum post. The script could then use the `document.cookie` property to access and transmit the user’s session ID to a server controlled by the attacker. Once the attacker has the session ID, they can impersonate the victim and access their account.
DOM-Based XSS Exploitation in a Windows Environment
DOM-based XSS vulnerabilities reside within the client-side Document Object Model (DOM). They don’t involve server-side interaction; the vulnerability lies in how the browser manipulates and displays data. Exploiting this requires a deeper understanding of JavaScript and how the application handles data within the browser.
The following steps illustrate the exploitation process:
- Identify the vulnerable DOM element: This usually involves inspecting the application’s source code to find areas where user input directly affects the DOM without proper sanitization.
- Craft a malicious JavaScript payload: This payload will target the identified DOM element. For example, if the application dynamically updates a user’s profile based on user input, a payload might be designed to overwrite the profile’s data with malicious code.
- Inject the payload: This usually involves manipulating the application’s input fields to introduce the crafted payload. The payload might attempt to overwrite crucial DOM elements, manipulating user actions or data displayed to the user.
- Observe the impact: The impact will depend on the nature of the payload. It could range from a simple alert box to a complete compromise of the user’s session or data.
Mitigation Techniques for Windows XSS Flaws
Preventing Cross-Site Scripting (XSS) vulnerabilities in Windows applications requires a multi-layered approach focusing on secure coding practices, robust input validation, and reliable output encoding. Ignoring these crucial steps leaves your applications wide open to attacks that can compromise user data and system integrity. Let’s delve into the specifics of effective mitigation.
Secure Coding Practices
Implementing secure coding practices is the cornerstone of preventing XSS vulnerabilities. This involves consistently following secure development principles throughout the entire software development lifecycle (SDLC). Developers should be trained to understand the risks associated with XSS and adopt defensive programming techniques. This includes minimizing the use of dynamic content where possible, and carefully considering the trustworthiness of all user inputs. Employing a secure coding standard, such as OWASP’s Secure Coding Practices, and regularly performing code reviews are essential steps in this process. Regular security audits and penetration testing further strengthen this defensive posture.
Input Validation Techniques
Thorough input validation is crucial in preventing malicious scripts from entering your application. This involves carefully scrutinizing all user-supplied data before it’s processed or stored. For example, validating the length of strings, checking for unexpected characters, and ensuring data types match expectations are all vital steps. Consider these examples: For a username field, you might limit its length and allow only alphanumeric characters and underscores. For an email field, you should validate the format using regular expressions to ensure it conforms to a standard email structure. Never trust user input; always validate it rigorously. Whitelisting, where you only accept explicitly allowed characters or data patterns, is a more secure approach than blacklisting, which attempts to block known harmful patterns, as attackers can always find ways to circumvent blacklists.
Output Encoding
Output encoding is the process of converting special characters in data to their corresponding HTML entities before displaying them on a webpage. This prevents the browser from interpreting them as executable code. For example, the less-than symbol (<) should be encoded as < and the greater-than symbol (>) as >. This simple act can prevent many XSS attacks. The specific encoding method depends on the context. For HTML output, HTML encoding is necessary; for JavaScript output, JavaScript encoding is required; and for attribute values, attribute encoding should be used. Failing to correctly encode output is a major source of XSS vulnerabilities. It’s important to consistently apply appropriate encoding techniques based on the context where data is rendered.
Web Application Firewall (WAF) Comparison
Web Application Firewalls (WAFs) provide an additional layer of security by filtering malicious traffic before it reaches the application. Different WAFs offer varying levels of protection and features. The effectiveness of a WAF depends on its configuration and the sophistication of the attack. Here’s a comparison of some popular WAFs:
| WAF Name | Key Features | Strengths | Weaknesses |
|---|---|---|---|
| ModSecurity | Rule-based filtering, customizable rules, real-time protection | Highly customizable, open-source, widely used | Requires expertise to configure effectively, can generate false positives |
| Cloudflare WAF | Cloud-based, easy to integrate, various security features | Simple to set up, good performance, integrated with other Cloudflare services | Can be expensive, relies on Cloudflare’s infrastructure |
| AWS WAF | Integrated with AWS ecosystem, scalable, managed service | Easy integration with other AWS services, high scalability | Can be expensive, requires familiarity with AWS |
| Azure Web Application Firewall | Integrated with Azure ecosystem, scalable, managed service | Easy integration with other Azure services, high scalability | Can be expensive, requires familiarity with Azure |
Case Studies of Real-World Windows XSS Flaws
Understanding real-world examples of Cross-Site Scripting (XSS) vulnerabilities in Windows applications is crucial for effective prevention and mitigation. These cases highlight the potential severity of these flaws and demonstrate how seemingly minor coding oversights can have significant consequences. Examining these examples provides valuable insights into best practices for secure development.
Let’s consider a scenario involving a widely used internal Windows-based application responsible for managing employee data. This application allowed users to update their personal profiles, including their name, contact information, and a short biographical section. The application, unfortunately, lacked proper input sanitization in the profile update functionality. A malicious actor discovered that they could inject JavaScript code into the biographical section. When a user viewed the profile of an affected user, the injected script would execute in their browser, potentially allowing the attacker to steal cookies, session IDs, or even execute arbitrary code in the context of the victim’s browser.
Vulnerability Details
The core vulnerability stemmed from the application’s failure to properly encode user-supplied input before displaying it on the page. The biographical section accepted user input without any form of escaping or encoding, making it susceptible to XSS attacks. This allowed an attacker to inject malicious JavaScript code, which would then be executed by the victim’s browser within the context of the application. The impact of this vulnerability was significant, potentially leading to account takeover, data theft, and session hijacking.
Impact and Remediation
The consequences of this vulnerability were severe. Successful exploitation could have resulted in the compromise of employee accounts, leading to unauthorized access to sensitive data within the application. The compromised accounts could also be used to launch further attacks against the organization’s network. Remediation involved implementing robust input validation and output encoding mechanisms. All user-supplied data was sanitized before being rendered on the page, effectively preventing the injection of malicious scripts. The application also underwent thorough security testing to identify and address any remaining vulnerabilities. Regular security audits and penetration testing were implemented as part of the ongoing security posture improvement.
Lessons Learned
This case study underscores the importance of secure coding practices. The failure to properly sanitize user input is a common cause of XSS vulnerabilities. Developers must always validate and sanitize all user-supplied data before displaying it on a web page. This includes encoding special characters to prevent them from being interpreted as executable code. Furthermore, regular security testing and code reviews are crucial for identifying and addressing vulnerabilities before they can be exploited. Employing a Secure Development Lifecycle (SDLC) that incorporates security testing throughout the development process is paramount. The adoption of automated security tools and the training of developers in secure coding practices are also essential components of a robust security strategy.
Advanced XSS Techniques in Windows
Source: medium.com
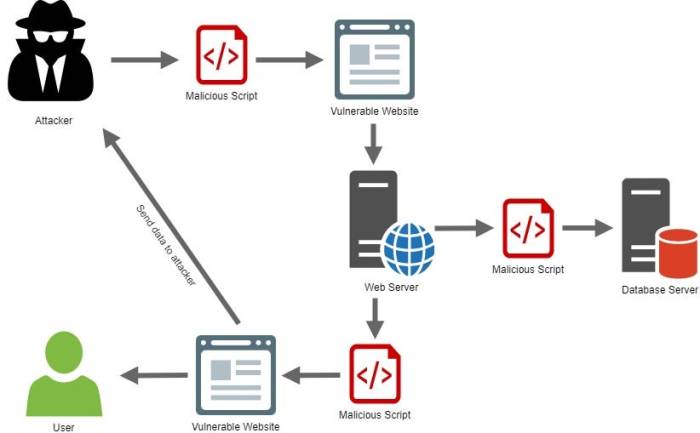
The seemingly simple Cross-Site Scripting (XSS) vulnerability takes on a far more sinister character when wielded by sophisticated actors within the Windows environment. Advanced Persistent Threats (APTs), with their resources and patience, leverage XSS to achieve objectives beyond simple data theft, often establishing long-term footholds and escalating privileges. Understanding these advanced techniques is crucial for effective defense.
Advanced XSS techniques in Windows often involve exploiting vulnerabilities beyond the basic reflected or stored XSS vectors. These attacks frequently incorporate sophisticated evasion techniques and leverage the unique characteristics of the Windows operating system and its applications to achieve their goals. The focus shifts from immediate impact to establishing persistent access and control.
Advanced Persistent Threats (APTs) and XSS
APTs are characterized by their stealthy and persistent nature. They often involve highly targeted attacks against specific organizations or individuals, aiming for long-term access to sensitive information and systems. XSS, while seemingly a relatively simple vulnerability, serves as an effective entry point for APTs. A successful XSS attack can provide initial access, allowing the attacker to subsequently deploy more sophisticated malware or establish persistent backdoors. Consider a scenario where an APT compromises a high-value employee’s machine via a carefully crafted phishing email containing a malicious link. The link triggers an XSS vulnerability on a corporate intranet website, giving the attacker a foothold. This initial access is then leveraged to escalate privileges and establish a persistent presence within the network, allowing for long-term data exfiltration and potentially even network manipulation.
Bypassing Common XSS Prevention Mechanisms
Standard XSS prevention mechanisms, such as input sanitization and output encoding, can be bypassed through various techniques. Attackers may use techniques like encoding and decoding to evade filters, employ homoglyph attacks (using visually similar characters to bypass filters), or utilize techniques like DOM-based XSS to target client-side vulnerabilities that might not be addressed by server-side protection. For example, an attacker might use JavaScript’s `unescape()` function to bypass server-side encoding, or they might exploit vulnerabilities in the way a browser renders and interprets HTML to inject malicious scripts. These techniques require a deep understanding of both web technologies and the specific security mechanisms implemented on the target system.
Privilege Escalation via XSS
Once an attacker has successfully exploited an XSS vulnerability, the next step is often privilege escalation. This involves gaining higher-level access within the Windows environment, potentially allowing the attacker to control the entire system. This can be achieved by exploiting vulnerabilities in specific applications or by leveraging existing user privileges to access sensitive data or perform unauthorized actions. For instance, an attacker might use an XSS vulnerability to inject code that exploits a known vulnerability in a specific Windows application, granting them elevated privileges. Alternatively, an attacker might use XSS to steal session cookies or other authentication tokens, allowing them to impersonate a legitimate user with higher privileges. The success of this depends heavily on the specific vulnerabilities present on the target system and the attacker’s ability to exploit them.
End of Discussion
Source: geeksforgeeks.org
So, there you have it – a whirlwind tour through the world of Windows XSS flaws. Understanding these vulnerabilities isn’t just about technical prowess; it’s about protecting your systems, your data, and ultimately, your peace of mind. By implementing secure coding practices, leveraging robust input validation, and staying up-to-date on security patches, you can significantly reduce your risk. Remember, proactive security is the best defense against these insidious attacks. Stay vigilant, stay informed, and stay safe.



