Intrusion detection prevention systems (IDPS) are the unsung heroes of cybersecurity, silently guarding our digital fortresses against a relentless barrage of threats. They’re not just about detecting intrusions; they actively prevent them, acting as a crucial layer of defense in today’s complex digital landscape. Understanding how these systems work, from their historical evolution to their cutting-edge AI-powered capabilities, is key to bolstering your organization’s security posture. This exploration will unravel the intricacies of IDPS, from deployment strategies to advanced technologies, equipping you with the knowledge to navigate the ever-evolving world of cyber threats.
We’ll delve into the core functionalities of IDPS, exploring the differences between intrusion detection systems (IDS) and intrusion prevention systems (IPS). We’ll examine various deployment models, including network-based, host-based, and cloud-based solutions, comparing their strengths and weaknesses. We’ll also dissect the architecture of a typical IDPS, from sensors and analyzers to response units, and explain how signature-based and anomaly-based detection methods work. The role of machine learning and artificial intelligence in modern IDPS will be a key focus, alongside a look at best practices for deployment, management, and optimization.
Introduction to Intrusion Detection and Prevention Systems (IDPS)
Source: spiceworks.com
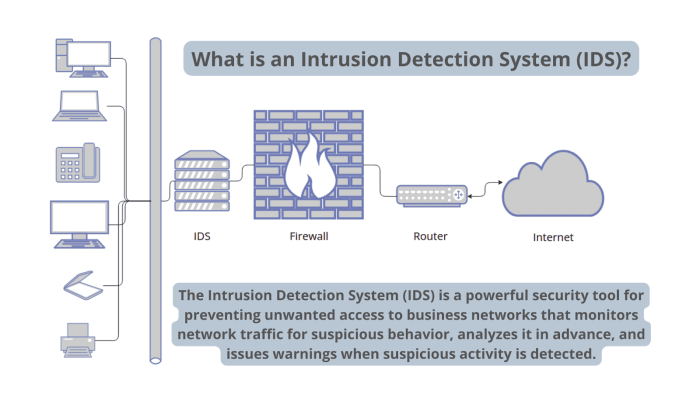
Intrusion Detection and Prevention Systems (IDPS) are the digital sentinels guarding our increasingly interconnected world. They’re the unsung heroes silently working to protect our networks and systems from cyber threats, acting as a crucial layer of security in today’s complex digital landscape. Understanding their functionality is key to comprehending the ever-evolving world of cybersecurity.
IDPS encompass two main categories: Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). While both monitor network traffic and system activity for malicious behavior, their responses differ significantly. IDS passively monitor and alert administrators to suspicious activity, essentially acting as a watchful eye. IPS, on the other hand, take a more proactive approach, actively blocking or mitigating identified threats in real-time. Think of IDS as a security guard who calls the police, and IPS as a security guard who also apprehends the intruder.
IDS vs. IPS: A Clear Distinction
The core difference lies in their response to detected threats. An IDS flags suspicious activity, providing valuable insights into potential breaches, but it doesn’t interfere with the network traffic. An IPS, however, goes further; it actively blocks or modifies malicious traffic, preventing it from reaching its target. This proactive approach significantly reduces the impact of successful attacks. While both are valuable tools, the choice between IDS and IPS, or a combined approach, depends on the specific security needs and risk tolerance of an organization. Many modern security solutions integrate both capabilities into a single system.
A Brief History of IDPS Evolution
The evolution of IDPS is intrinsically linked to the growth of computer networks and the increasing sophistication of cyberattacks. Early systems relied heavily on signature-based detection, identifying known threats based on their unique characteristics. However, as attackers developed more sophisticated techniques, including polymorphism and zero-day exploits, behavior-based detection became crucial. This shift involved analyzing network traffic and system activity for anomalies that deviate from established baselines. The advent of machine learning and artificial intelligence has further revolutionized IDPS capabilities, enabling more accurate threat detection and response. The integration of cloud-based solutions and the rise of security information and event management (SIEM) systems have also played a significant role in expanding the reach and capabilities of IDPS.
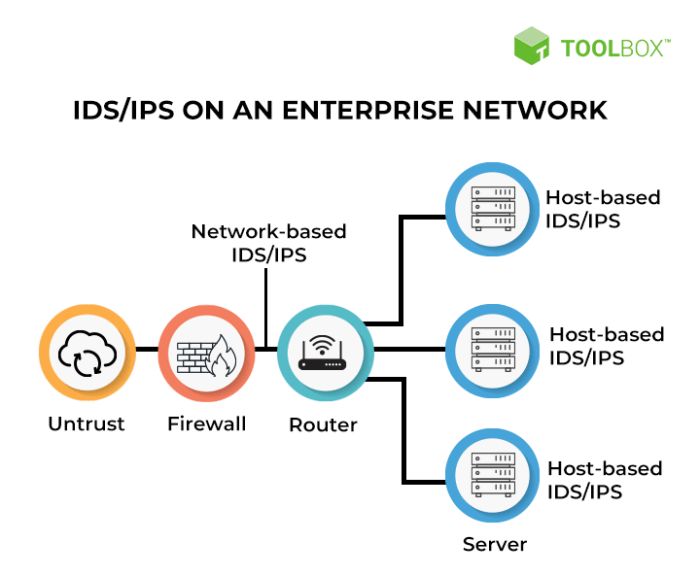
IDPS Deployment Models
Understanding the different deployment models is essential for optimizing IDPS effectiveness. The choice depends on factors like network architecture, budget, and specific security needs.
| Deployment Model | Description | Advantages | Disadvantages |
|---|---|---|---|
| Network-based | Monitors network traffic for malicious activity. Typically deployed at strategic points in the network, such as routers or firewalls. | Provides broad visibility across the network, detecting attacks targeting multiple systems. Relatively easy to deploy and manage. | Can generate high volumes of alerts, requiring robust filtering and analysis. May miss attacks targeting specific hosts. |
| Host-based | Resides on individual systems, monitoring their activity for malicious behavior. | Provides detailed insights into individual system activity. Can detect attacks that bypass network-based IDS/IPS. | Requires agent installation on each host, increasing management overhead. May not detect network-level attacks. |
| Cloud-based | Leverages cloud infrastructure to provide IDPS capabilities. Can be deployed as a service, eliminating the need for on-premise hardware and software. | Scalable and flexible, adapting to changing needs. Reduces management overhead. | Reliance on cloud provider security. Potential latency issues depending on network connectivity. |
IDPS Architectures and Components: Intrusion Detection Prevention Systems
Source: redswitches.com
Intrusion Detection and Prevention Systems (IDPS) aren’t monolithic entities; they’re complex systems composed of interconnected components working in concert to safeguard networks. Understanding their architecture is crucial to appreciating their capabilities and limitations. This section delves into the key components and methodologies underpinning effective IDPS deployment.
A typical IDPS architecture comprises three main components: sensors, analyzers, and response units. These components interact dynamically, processing network traffic and responding to detected threats. The efficiency and effectiveness of the entire system depend heavily on the seamless integration and communication between these elements.
IDPS Components
The effectiveness of an IDPS hinges on the coordinated operation of its core components. Let’s examine each in detail.
- Sensors: These are the eyes and ears of the IDPS, strategically placed throughout the network to collect data. Sensors passively monitor network traffic, capturing packets and system logs. They can be network-based (monitoring network traffic at specific points) or host-based (monitoring activity on individual systems). The type and placement of sensors are crucial for comprehensive network coverage. Effective sensor placement minimizes blind spots and ensures the IDPS captures relevant data for analysis.
- Analyzers: The analyzers are the brains of the operation, responsible for processing the data collected by the sensors. They employ various detection methods (discussed below) to identify malicious activity. Analyzers compare collected data against known threat signatures or establish baselines to detect anomalies. The analyzer’s processing power and algorithm efficiency directly impact the speed and accuracy of threat detection.
- Response Units: These are the enforcement arm of the IDPS, taking action based on the analyzer’s findings. Actions can range from logging alerts, blocking malicious traffic, resetting connections, to even quarantining infected systems. The response unit’s capabilities are crucial for mitigating the impact of detected threats. The sophistication of the response unit directly affects the effectiveness of the IDPS in preventing damage.
Signature-Based and Anomaly-Based Detection
IDPS employ two primary detection methods: signature-based and anomaly-based. Each has its strengths and weaknesses.
- Signature-Based Detection: This method relies on comparing network traffic or system events against a database of known attack signatures (patterns of malicious activity). If a match is found, the system triggers an alert. It’s effective against known threats but struggles with zero-day attacks (new attacks without known signatures).
- Anomaly-Based Detection: This method establishes a baseline of normal system behavior and flags deviations from this baseline as potential anomalies. It’s more effective against zero-day attacks and previously unknown threats, but it can generate false positives if the baseline isn’t properly established or if legitimate activities deviate significantly from the norm. This requires careful configuration and tuning to minimize false positives.
The Role of Machine Learning in Modern IDPS
Machine learning (ML) is revolutionizing IDPS capabilities. ML algorithms can analyze vast amounts of data to identify complex patterns and relationships indicative of malicious activity, improving both signature-based and anomaly-based detection. ML algorithms adapt and learn from new data, enhancing their ability to detect emerging threats and reduce false positives. For example, ML can be used to refine anomaly detection baselines dynamically, adapting to changing network behavior and reducing false alerts. Furthermore, ML can assist in prioritizing alerts, focusing security teams’ attention on the most critical threats.
Sample IDPS Architecture Diagram
Imagine a diagram showing a network with several sensors (network and host-based) strategically placed. Arrows depict the flow of network traffic and system logs from these sensors to a central analyzer. The analyzer, depicted as a central processing unit, processes this data using signature-based and anomaly-based techniques. If a threat is detected, the analyzer sends a signal to the response unit, shown as a separate module. The response unit, in turn, takes action, such as blocking traffic, generating alerts, or isolating infected systems. The communication between these components is represented by labeled arrows indicating data flow and control signals. The diagram clearly shows the data flow from sensors, through the analyzer, and finally to the response unit, highlighting the interconnectedness of the IDPS components.
IDPS Deployment Strategies and Best Practices
Deploying an Intrusion Detection and Prevention System (IDPS) effectively is crucial for maintaining network security. Getting it wrong can lead to vulnerabilities, performance bottlenecks, and a deluge of useless alerts. This section dives into the best practices and strategies for successful IDPS implementation, ensuring your network remains protected without sacrificing performance or sanity.
Choosing the right deployment strategy depends heavily on your network architecture, security goals, and tolerance for disruption. A poorly planned deployment can render your IDPS ineffective, or worse, a hindrance. Understanding the nuances of different approaches and optimizing for performance is key to a successful implementation.
Inline versus Passive Monitoring
Inline deployment places the IDPS directly in the network path, actively inspecting all traffic. This provides immediate protection, blocking malicious activity in real-time. However, this approach introduces a single point of failure and can impact network performance if the IDPS isn’t properly sized or optimized. Think of it like a security guard standing directly at the door, stopping threats before they enter the building. Conversely, passive monitoring involves placing the IDPS on a mirrored port, observing traffic without directly interfering. This approach is less disruptive but offers only detection capabilities; it can’t actively block attacks. This is more like having security cameras monitoring the building – they record activity but don’t directly intervene. The choice depends on your risk tolerance and the level of control needed. High-security environments might favor inline deployment, while organizations prioritizing minimal disruption might opt for passive monitoring.
Optimizing IDPS Performance and Minimizing False Positives
Effective IDPS management goes beyond simply installing the software. Regular tuning and maintenance are critical for optimal performance and minimizing the dreaded false positives. False positives, alerts triggered by benign activity, can overwhelm security teams and lead to alert fatigue, making genuine threats harder to identify. Strategies include:
- Regular Signature Updates: Keeping your IDPS signature database up-to-date is paramount. Outdated signatures can lead to missed threats and unnecessary alerts. Think of it as updating your antivirus software regularly.
- Fine-tuning Alert Thresholds: Adjust alert thresholds to reduce noise. Too many alerts can bury real threats. Finding the right balance requires careful monitoring and adjustment based on your network’s typical activity.
- Implementing Anomaly Detection Rules Carefully: Anomaly detection can be powerful but requires careful configuration to avoid excessive false positives. Overly sensitive rules can trigger alerts for perfectly normal network behavior.
- Regular Performance Monitoring: Monitor CPU usage, memory consumption, and network latency to ensure the IDPS doesn’t become a bottleneck. Regular checks help proactively identify and address performance issues.
Common Challenges and Mitigation Strategies
Implementing an IDPS presents several challenges. Understanding these beforehand allows for proactive mitigation.
- High False Positive Rates: As mentioned earlier, false positives can overwhelm security teams. Mitigation: Fine-tune alert thresholds, regularly update signatures, and carefully configure anomaly detection rules.
- Performance Impact: Inline deployments can impact network performance if not properly sized and optimized. Mitigation: Choose the right hardware, optimize IDPS settings, and consider passive monitoring for less critical segments of the network.
- Complexity of Management: Managing and maintaining an IDPS can be complex, requiring specialized skills. Mitigation: Invest in training for your security team, use centralized management tools, and consider managed security services.
- Integration with Existing Systems: Integrating the IDPS with existing security tools and systems can be challenging. Mitigation: Choose an IDPS that offers good integration capabilities, and plan for integration carefully during the deployment phase.
- Cost: Implementing and maintaining an IDPS can be expensive, requiring investments in hardware, software, and personnel. Mitigation: Carefully evaluate your needs and choose a solution that fits your budget, consider cloud-based solutions for cost-effectiveness.
Types of Intrusions and IDPS Countermeasures
Intrusion Detection and Prevention Systems (IDPS) are crucial for safeguarding networks from a variety of threats. Understanding the common types of intrusions and the countermeasures an IDPS employs is vital for effective cybersecurity. This section details common intrusion types, the IDPS responses, and how IDPS integrates with other security tools for a robust defense.
Network intrusions come in many forms, each requiring a specific approach to mitigation. Effective IDPS implementation relies on a multi-layered strategy that combines detection, prevention, and response capabilities.
Denial-of-Service Attacks
Denial-of-Service (DoS) attacks aim to overwhelm a system’s resources, making it unavailable to legitimate users. Distributed Denial-of-Service (DDoS) attacks amplify this by using multiple compromised systems. IDPS countermeasures include rate limiting (restricting the number of requests from a single IP address), traffic filtering (blocking suspicious traffic patterns), and anomaly detection (identifying unusual traffic spikes). Effective mitigation often requires collaboration with Internet Service Providers (ISPs) to block malicious traffic at the network’s edge. For example, a sudden surge in SYN packets targeting a specific port might trigger an alert, indicating a potential DoS attack. The IDPS can then implement rate limiting to prevent the server from being overloaded.
Malware Infections
Malware, encompassing viruses, worms, trojans, and ransomware, poses a significant threat. IDPS utilizes signature-based detection (matching known malware signatures) and anomaly-based detection (identifying unusual behavior) to detect infections. Countermeasures involve blocking malicious traffic, quarantining infected systems, and deploying automated responses like system isolation or malware removal. Imagine a situation where an IDPS detects a system attempting to connect to a known malicious command-and-control server. The IDPS can immediately block the connection and trigger an alert, preventing further damage.
Unauthorized Access
Unauthorized access attempts, often involving brute-force attacks or exploiting vulnerabilities, are common intrusions. IDPS employs authentication monitoring (checking login attempts against allowed users), intrusion prevention rules (blocking access from unauthorized sources), and anomaly detection (identifying unusual login patterns). For example, repeated failed login attempts from a single IP address might trigger an alert, suggesting a brute-force attack. The IDPS can then temporarily block the IP address or implement account lockout policies.
IDPS Integration with Other Security Tools
IDPS works effectively when integrated with other security tools. Firewalls act as the first line of defense, filtering traffic before it reaches the IDPS. Security Information and Event Management (SIEM) systems collect and analyze logs from various security tools, including the IDPS, providing a comprehensive view of security events. This integration allows for a more holistic approach to security, enhancing threat detection and response capabilities. For instance, a firewall might block a suspicious connection attempt, and the IDPS would log this event, providing additional context to the SIEM system for analysis.
Interpreting IDPS Alerts and Logs
IDPS generates alerts and logs that provide crucial information about security incidents. Analyzing these logs helps security professionals identify the nature and severity of attacks, trace their origins, and implement appropriate countermeasures. Alerts typically include information such as the type of intrusion, the affected system, the source of the attack, and the timestamp. By correlating these alerts with other security logs, a complete picture of the incident can be constructed, facilitating a timely and effective response. For example, a series of alerts related to unauthorized access attempts followed by data exfiltration attempts suggests a coordinated attack. This allows security personnel to take immediate action, such as isolating the compromised system and initiating a forensic investigation.
Advanced IDPS Technologies and Future Trends
The landscape of cybersecurity is constantly evolving, demanding increasingly sophisticated intrusion detection and prevention systems (IDPS). Traditional signature-based approaches are proving insufficient against the ever-growing sophistication of cyberattacks. This necessitates a shift towards advanced technologies leveraging artificial intelligence, behavioral analytics, and cloud-based infrastructure. This section explores these cutting-edge developments and their impact on the future of IDPS.
Behavioral Analytics and User and Entity Behavior Analytics (UEBA) in Modern IDPS
Behavioral analytics forms the cornerstone of modern IDPS, moving beyond simple signature matching to identify anomalies in system and user behavior. Instead of relying solely on known attack patterns, UEBA systems build profiles of normal activity for users, devices, and applications. Any deviation from this established baseline triggers an alert, allowing for the detection of zero-day exploits and insider threats that traditional methods often miss. For example, a UEBA system might detect unusual login times from a specific user account, or a sudden surge in data access from an unusual location, triggering an investigation. This proactive approach significantly enhances the effectiveness of IDPS in identifying and responding to threats.
Artificial Intelligence and Machine Learning in Enhancing IDPS Capabilities
AI and ML are revolutionizing IDPS capabilities. Machine learning algorithms can analyze vast amounts of data to identify subtle patterns indicative of malicious activity, significantly improving detection rates and reducing false positives. AI-powered systems can also adapt to evolving threat landscapes, learning from new attacks and automatically updating their detection models. For instance, an AI-powered IDPS could learn to recognize the subtle characteristics of a new ransomware variant by analyzing its network traffic and system behavior, even before traditional signature-based systems are updated. This adaptive learning capability is crucial in the fight against increasingly sophisticated and rapidly evolving threats.
Impact of Cloud Computing and Virtualization on IDPS Deployment and Management, Intrusion detection prevention systems
The rise of cloud computing and virtualization presents both challenges and opportunities for IDPS. The distributed nature of cloud environments requires a more dynamic and scalable approach to security. Virtualized environments also introduce complexities in identifying and isolating threats. However, cloud-based IDPS solutions offer benefits such as enhanced scalability, reduced infrastructure costs, and improved accessibility. Many cloud providers offer integrated security services, simplifying IDPS deployment and management. For example, a company migrating its infrastructure to a cloud platform can leverage the provider’s built-in IDPS capabilities, reducing the need for on-premises infrastructure and management overhead.
Emerging IDPS Technologies and Their Potential Benefits
| Technology | Description | Potential Benefits | Example Use Case |
|---|---|---|---|
| Next-Generation Firewalls (NGFWs) | Firewalls with advanced features like deep packet inspection, application control, and intrusion prevention. | Improved threat detection and prevention, enhanced application security. | Blocking malicious traffic targeting specific applications within a corporate network. |
| Security Information and Event Management (SIEM) | Systems that collect and analyze security logs from various sources to provide a comprehensive view of security events. | Improved threat detection, incident response, and security auditing. | Correlating security logs from different network devices to identify a coordinated attack. |
| Endpoint Detection and Response (EDR) | Solutions that monitor endpoints for malicious activity and provide incident response capabilities. | Improved detection of malware and other endpoint threats, faster incident response. | Identifying and isolating a compromised endpoint before it can spread malware to other systems. |
| Threat Intelligence Platforms (TIPs) | Systems that collect and analyze threat intelligence from various sources to provide actionable insights. | Improved threat awareness, proactive security measures, and enhanced incident response. | Using threat intelligence feeds to identify and block known malicious IP addresses. |
Case Studies and Real-World Examples
Source: com.au
Intrusion Detection and Prevention Systems (IDPS) aren’t just theoretical concepts; their effectiveness is demonstrably proven in real-world scenarios. Understanding both successful implementations and the consequences of neglecting IDPS is crucial for any organization prioritizing cybersecurity. The following case studies highlight the tangible impact of IDPS, illustrating its power to protect sensitive data and prevent significant financial and reputational damage.
The success or failure of an IDPS implementation hinges on several factors, including proper configuration, regular updates, and integration with other security tools. A poorly implemented or neglected IDPS can be worse than having no system at all, potentially creating false senses of security and leaving critical vulnerabilities exposed.
Successful IDPS Implementations and Their Impact
Several organizations have successfully leveraged IDPS to bolster their security posture. These examples demonstrate the positive outcomes achievable through careful planning, implementation, and ongoing management.
- Financial Institution X: This major bank implemented a comprehensive IDPS, integrating network-based and host-based solutions. The system detected and prevented numerous sophisticated phishing attacks targeting customer data, resulting in a significant reduction in successful breaches and associated financial losses. The IDPS’s ability to analyze network traffic and identify malicious patterns proved invaluable in protecting the bank’s assets and reputation.
- E-commerce Company Y: This online retailer deployed an IDPS to protect its e-commerce platform from various threats, including SQL injection attacks and denial-of-service attempts. The system’s real-time threat detection capabilities enabled immediate responses to attacks, minimizing downtime and preventing data breaches. This resulted in improved customer trust and reduced operational disruptions.
Consequences of Failing to Implement or Properly Manage an IDPS
Neglecting IDPS implementation or failing to properly manage an existing system can lead to severe consequences, impacting an organization’s security, financial stability, and reputation.
- Healthcare Provider Z: This hospital lacked a robust IDPS, resulting in a significant data breach compromising sensitive patient information. The breach led to substantial financial penalties, legal action, and a severe erosion of public trust. The lack of proactive security measures proved incredibly costly.
- Manufacturing Company A: This company experienced a ransomware attack that crippled its production lines for several days due to the absence of a functioning IDPS. The attack resulted in significant production delays, financial losses, and reputational damage. The inability to detect and respond to the attack quickly had severe repercussions.
Real-World Scenarios Illustrating IDPS Prevention and Mitigation
Several real-world examples illustrate how IDPS has played a crucial role in preventing or mitigating security breaches.
- Government Agency B: This government agency’s IDPS detected and blocked a sophisticated zero-day exploit attempt targeting its internal network. The timely detection and prevention of this attack prevented a potentially devastating data breach and protected sensitive government information.
- Educational Institution C: This university’s IDPS identified and neutralized a malware infection that was spreading rapidly across its network. The system’s rapid response contained the infection, preventing further damage and protecting valuable research data and student records. The quick response minimized disruption to academic activities.
Final Review
In the ever-escalating arms race against cybercriminals, intrusion detection and prevention systems are no longer a luxury—they’re a necessity. From understanding the nuances of different detection methods to mastering the art of interpreting IDPS alerts, this journey into the heart of IDPS has equipped you with the knowledge to make informed decisions about your organization’s security. Remember, a robust IDPS, coupled with proactive security practices, forms the bedrock of a truly resilient digital infrastructure. Staying informed about the latest advancements and emerging technologies is crucial in this ever-evolving landscape, ensuring your defenses remain ahead of the curve.



