Microsoft corporate email accounts spoof: It sounds like something out of a spy thriller, right? But the reality is far more commonplace, and potentially devastating. From subtle display name tweaks to sophisticated header manipulation, malicious actors are constantly finding new ways to impersonate legitimate Microsoft accounts, leading to phishing attacks, data breaches, and financial losses. This deep dive explores the various methods used, the red flags to watch out for, and crucially, how to protect yourself and your organization.
We’ll dissect the different types of spoofing—header, display name, and email address—showing you real-world examples of how these techniques are used to trick unsuspecting users. We’ll then equip you with the knowledge to identify these fraudulent emails, providing a practical checklist and step-by-step guide to verify sender authenticity. Finally, we’ll delve into preventative measures, exploring email authentication protocols and outlining a robust security policy to minimize your risk.
Types of Microsoft Corporate Email Spoofing
Source: prajwaldesai.com
Microsoft corporate email accounts are prime targets for sophisticated spoofing attacks. These attacks leverage various techniques to trick recipients into believing the email originates from a legitimate Microsoft source, often leading to phishing scams, malware distribution, or data breaches. Understanding the different types of spoofing is crucial for effective prevention and mitigation.
Spoofing attacks manipulate different aspects of an email to impersonate a legitimate sender. The key difference lies in *what* is being faked: the sender’s email address, their displayed name, or the email headers themselves. Each method presents unique challenges and can be used in various combinations to enhance the effectiveness of the attack.
Header Spoofing
Header spoofing involves manipulating the email headers, the behind-the-scenes metadata of an email. This allows attackers to forge information such as the “From” address, the “Reply-To” address, and other header fields. While the recipient might see a legitimate-looking “From” address, the underlying headers reveal the true sender. This is often used to bypass email authentication systems that rely on header analysis. The sophistication of header spoofing can vary greatly, from simple alterations to complex techniques involving the manipulation of multiple header fields.
Display Name Spoofing
Display name spoofing focuses on manipulating the sender’s name displayed to the recipient. This is often done by placing a legitimate-looking name (like “Microsoft Security Team”) within the email’s header, while the actual email address might be entirely different. This relies on the user’s tendency to focus on the displayed name rather than carefully scrutinizing the email address. It’s a simple but effective tactic, particularly for less tech-savvy users.
Email Address Spoofing
Email address spoofing involves forging the email address itself, making it appear as if the email originated from a legitimate Microsoft domain (e.g., @microsoft.com). This is often combined with display name spoofing to create a convincing imitation. However, sophisticated email authentication protocols like SPF, DKIM, and DMARC can often detect this type of spoofing, though not always reliably.
Examples of Spoofing in Phishing Attacks
Here are some examples of how these spoofing methods are used in phishing attacks targeting Microsoft accounts:
| Spoofing Method | Description | Example | Potential Impact |
|---|---|---|---|
| Header Spoofing | Attackers manipulate email headers to mask their true origin, even if the “From” address looks legitimate. | An email appears to be from “[email protected],” but header analysis reveals it came from a compromised server in a different country. | Malware delivery, credential theft, account takeover. |
| Display Name Spoofing | Attackers use a legitimate-looking display name (“Microsoft Account Support”) while the email address is suspicious. | An email with the display name “Microsoft Account Support” is sent from “[email protected],” urging the user to update their password. | Phishing, credential theft. |
| Email Address Spoofing | Attackers forge the email address to mimic a legitimate Microsoft address (e.g., “[email protected]”). | An email seemingly from “[email protected]” requests users to click a link to verify their account. | Malware delivery, credential theft, account takeover. |
Identifying Spoofed Emails
Spotting a fake Microsoft email might seem like a digital detective game, but with the right tools and knowledge, it’s totally doable. These sneaky spoofed emails often try to trick you into revealing sensitive information or downloading malware, so mastering identification is crucial for your online safety. This section will equip you with the skills to sniff out these digital imposters.
Spoofed emails cleverly mimic legitimate Microsoft communications, making them incredibly convincing. However, a closer look reveals telltale signs. By understanding these indicators and employing verification methods, you can significantly reduce your risk of falling victim to these sophisticated phishing attacks.
Email Header Analysis
Examining the email headers is like looking under the hood of your email. It reveals the email’s journey, revealing potential inconsistencies that point to spoofing. Headers contain technical information such as the sender’s IP address, the mail servers used, and the email’s route. Discrepancies between the displayed sender address and the information in the headers are a major red flag. For example, the “From” field might show a Microsoft address, but the header might reveal the email originated from a suspicious IP address or domain. You can usually access the headers by clicking “Show Original” or a similar option in your email client.
Email Content Examination
Beyond the technical aspects, the email’s content itself offers valuable clues. Look for grammatical errors, poor formatting, or generic greetings. Legitimate Microsoft emails typically maintain a professional tone and use personalized salutations. Suspicious links or attachments are also major warning signs. Hovering over a link before clicking reveals its true destination – if it differs from the displayed text, it’s a potential trap. Be wary of urgent requests for personal information or login credentials; Microsoft rarely requests such data via email.
Authenticity Checklist, Microsoft corporate email accounts spoof
Before engaging with any email claiming to be from Microsoft, consider this checklist:
This checklist is designed to help you quickly assess the legitimacy of emails, especially those that seem urgent or request sensitive information.
- Verify the Sender’s Address: Carefully examine the email address. Does it exactly match a known Microsoft address? Be cautious of slight variations.
- Check for Grammatical Errors and Poor Formatting: Legitimate emails are typically well-written and professionally formatted.
- Inspect Links and Attachments: Hover over links to check their destination. Avoid opening attachments from unknown senders.
- Look for Urgent or Suspicious Requests: Microsoft rarely requests personal information or login credentials via email.
- Examine the Email Headers: Compare the “From” address with the information in the headers. Discrepancies suggest spoofing.
Sender Identity Verification
Verifying the sender’s identity involves more than just looking at the “From” field. You can utilize several resources:
Don’t just rely on visual inspection; actively verify the sender’s identity using these steps.
- Check Microsoft’s Official Website: Look for contact information or support pages on Microsoft’s official website. Never rely solely on links within the suspicious email.
- Contact Microsoft Support Directly: Use the contact information found on the official website to verify the email’s legitimacy.
- Use Anti-Phishing Tools: Several online tools can help analyze emails for malicious content and identify potential phishing attempts.
Impact of Spoofing Attacks: Microsoft Corporate Email Accounts Spoof
Microsoft corporate email spoofing isn’t just a minor inconvenience; it’s a serious threat with far-reaching consequences. A successful attack can inflict significant financial losses, severely damage reputation, and cripple operational efficiency. The impact extends beyond the immediate victim, potentially affecting clients, partners, and even the broader public. Understanding the potential damage is crucial for implementing effective preventative measures.
Spoofing attacks targeting Microsoft corporate email accounts can lead to a cascade of negative effects, impacting various aspects of an organization. The severity of the consequences depends on factors such as the sophistication of the attack, the sensitivity of the compromised data, and the organization’s response capabilities. However, the potential for substantial damage is undeniable.
Financial Losses
The financial ramifications of a successful spoofing attack can be devastating. Phishing attacks leveraging spoofed emails can trick employees into revealing sensitive financial information, leading to direct monetary losses through fraudulent transactions. Moreover, the costs associated with investigating the breach, remediating the damage, and potentially facing legal action can quickly escalate. For example, a large corporation might incur millions in losses due to compromised financial data and subsequent legal battles. The disruption to business operations also represents a significant opportunity cost, with lost productivity and potential contract cancellations contributing to the overall financial impact.
Reputational Damage
Beyond the immediate financial impact, spoofing attacks can inflict significant reputational damage. A data breach resulting from a spoofing attack can erode public trust, damaging the organization’s brand image and potentially leading to a loss of customers and investors. The negative publicity surrounding a security breach, even if quickly resolved, can linger for a considerable time, impacting future business prospects. Consider the impact on a financial institution whose clients lose confidence after a successful phishing campaign targeting their email accounts. The resulting loss of trust could lead to significant financial repercussions and a long road to recovery.
Operational Disruptions
Successful spoofing attacks can disrupt core business operations. Compromised email accounts can be used to spread malware, disabling systems and interrupting workflows. The disruption caused by malware infections, data breaches, and the subsequent remediation efforts can significantly impact productivity and operational efficiency. Imagine a manufacturing company whose production line is halted due to a ransomware attack delivered via a spoofed email. The downtime, repair costs, and lost production would represent a substantial operational disruption. Furthermore, the time and resources spent on investigating and resolving the incident divert attention and resources away from other critical business activities.
Real-World Examples
Numerous real-world examples highlight the devastating consequences of successful Microsoft corporate email spoofing attacks. The 2016 Yahoo! data breach, although not solely attributed to email spoofing, involved phishing attacks that compromised user accounts and exposed sensitive personal information. The resulting legal battles and reputational damage cost Yahoo! millions and significantly impacted its market value. Similarly, numerous smaller businesses have faced crippling financial and operational consequences from less publicized but equally damaging spoofing attacks. These incidents underscore the critical need for robust security measures and proactive threat detection to mitigate the risks associated with email spoofing.
Prevention and Mitigation Strategies
Preventing Microsoft corporate email spoofing requires a multi-pronged approach combining robust technical measures, strong security policies, and comprehensive user training. Failing to implement these strategies leaves organizations vulnerable to significant financial and reputational damage. A proactive stance is crucial to minimizing the risk and ensuring business continuity.
Email Authentication Protocols: SPF, DKIM, and DMARC
Email authentication protocols are the cornerstone of any effective anti-spoofing strategy. These protocols verify the sender’s identity, helping to prevent malicious actors from forging emails that appear to originate from legitimate Microsoft accounts. SPF (Sender Policy Framework) verifies the sender’s IP address, DKIM (DomainKeys Identified Mail) uses digital signatures to authenticate the email’s origin, and DMARC (Domain-based Message Authentication, Reporting & Conformance) builds on SPF and DKIM to provide instructions on how receiving mail servers should handle emails that fail authentication checks. Implementing and properly configuring these protocols significantly reduces the success rate of spoofing attempts. For example, a properly configured DMARC policy can instruct receiving servers to reject or quarantine emails that fail authentication, effectively blocking spoofed messages from reaching users’ inboxes.
User Education and Awareness Training
User education is paramount in preventing successful spoofing attacks. Phishing emails often exploit human error, relying on users clicking malicious links or revealing sensitive information. Comprehensive training programs should cover common spoofing tactics, such as email subject lines mimicking legitimate communications, urgent calls to action, and requests for sensitive information. Regular simulated phishing campaigns can assess user vulnerability and reinforce training effectiveness. Training should emphasize careful examination of email headers, verification of sender identity through alternative means (such as a phone call), and reporting of suspicious emails. For example, a user trained to recognize a spoofed email might notice an unusual email address or inconsistencies in the sender’s name and domain.
Comprehensive Security Policy
A robust security policy should Artikel clear procedures for preventing and responding to email spoofing incidents. This policy should detail the implementation and maintenance of email authentication protocols, stipulate user responsibilities in identifying and reporting suspicious emails, and define incident response procedures. The policy should address the escalation path for security incidents, including the roles and responsibilities of different teams within the organization. Regular audits and reviews of the security policy are crucial to ensure its effectiveness and adaptability to evolving threats. For instance, the policy might mandate regular security awareness training for all employees, specify the acceptable use of corporate email accounts, and detail the consequences of non-compliance. Furthermore, a detailed incident response plan should be in place, including steps to contain the breach, investigate the cause, and remediate any vulnerabilities.
Forensic Analysis of Spoofed Emails
Unmasking the perpetrators behind sophisticated Microsoft corporate email spoofing requires a meticulous forensic investigation. This involves analyzing various aspects of the spoofed email to pinpoint the attacker’s techniques and ultimately, their identity. The process blends technical expertise with a methodical approach, utilizing readily available information within the email itself and leveraging external resources to trace the attack’s origin.
Analyzing a spoofed email isn’t just about identifying the sender’s address; it’s about unraveling the entire chain of events leading to the email’s delivery. This involves examining headers, metadata, and potentially, the email’s content for clues. By carefully piecing together this digital puzzle, investigators can build a comprehensive picture of the attack, potentially leading to the apprehension of the responsible parties.
Email Header Analysis
Email headers contain a wealth of information about an email’s journey. They reveal the various mail servers involved in the transmission, the timestamps of each step, and the original sender’s IP address (though this can be spoofed). Analyzing the “Received” headers, for instance, allows investigators to reconstruct the email’s path, identifying potential points of compromise or manipulation. Discrepancies between the displayed “From” address and the actual sender’s IP address, as revealed in the headers, are strong indicators of spoofing. A thorough examination of the “Authentication-Results” header can reveal whether authentication mechanisms like SPF, DKIM, and DMARC were bypassed or failed, providing crucial insights into the attacker’s methods. For example, a missing or failed SPF check might indicate that the attacker used a compromised server or forged DNS records.
Metadata Extraction
Beyond headers, the email itself contains metadata—hidden information about the email’s creation and modification. This metadata might include details like the creation time, the software used to compose the email, and even the operating system of the sender’s computer. While this information is not always directly related to identifying the attacker, it can provide valuable context and corroborate other findings. For example, detecting metadata indicating the email was created using a known malware-infected system could suggest a compromised account as the source of the attack. Tools specifically designed for metadata extraction can be used to unveil this hidden information.
Tracing the Origin of a Spoofed Email
Tracing the origin of a spoofed email often involves reverse-engineering the email’s path using the information gleaned from the headers. This might involve contacting the various mail servers listed in the “Received” headers to obtain additional logs and information. Investigators can also use IP address geolocation tools to determine the geographical location of the servers involved in the email’s transmission. Furthermore, analyzing the email’s content for clues like embedded links, attachments, or malicious code can provide further insights into the attacker’s intentions and infrastructure. The identification of specific malware signatures within attachments, for example, can link the attack to known malware campaigns.
Forensic Analysis Process Flowchart
Imagine a flowchart: The process begins with the acquisition of the spoofed email. This is followed by a detailed examination of the email headers, extracting information such as the “Received” headers, “From” address, and authentication results. Simultaneously, metadata extraction is performed to uncover hidden information about the email’s creation and modification. This information is then analyzed to identify discrepancies and potential points of compromise. The next step involves tracing the email’s path through the mail servers identified in the headers, potentially involving communication with those servers for additional logs. Finally, the gathered information is synthesized to create a comprehensive report outlining the attack, including the attacker’s methods and potential identity. The entire process is iterative, with findings from one stage often informing subsequent steps.
Legal and Regulatory Implications

Source: prajwaldesai.com
Email spoofing, especially targeting corporate accounts, isn’t just a tech headache; it’s a legal minefield. The potential for financial loss, reputational damage, and even legal repercussions for both the victim and, in some cases, the perpetrators, is substantial. Understanding the legal landscape is crucial for businesses to protect themselves and navigate the complexities of these attacks.
The legal implications of Microsoft corporate email spoofing attacks are multifaceted, stemming from various legal frameworks designed to protect individuals and organizations from cybercrime. These attacks can trigger liability under several different laws, depending on the specific nature of the attack and its consequences. The responsibility falls squarely on organizations to implement robust security measures and respond effectively to incidents. Failure to do so can lead to significant penalties and legal battles.
Applicable Laws and Regulations
Several laws and regulations address email spoofing and its consequences. For instance, the Computer Fraud and Abuse Act (CFAA) in the United States makes it a crime to access a protected computer without authorization, which could include accessing email accounts through spoofing. Furthermore, depending on the context, state laws concerning identity theft or fraud might also apply if the spoofing leads to financial losses or other forms of identity compromise. Internationally, similar laws exist in various jurisdictions, often mirroring the principles of the CFAA. The General Data Protection Regulation (GDPR) in Europe, for example, places strict obligations on organizations to protect personal data, and a successful spoofing attack leading to data breaches could trigger significant penalties under GDPR. Compliance with these regulations is paramount, as non-compliance can lead to hefty fines and legal action.
Organizational Responsibilities
Organizations have a legal and ethical duty to protect their email systems and the data they contain. This responsibility extends beyond simply implementing security software; it includes developing comprehensive security policies, employee training programs, and incident response plans. Regular security audits and vulnerability assessments are also crucial to identify and address weaknesses before they can be exploited by attackers. Moreover, organizations must ensure they have adequate processes in place to detect, investigate, and respond to spoofing attempts, including reporting such incidents to relevant authorities. Transparency with affected parties and regulatory bodies is also a key aspect of fulfilling these responsibilities.
Penalties for Inadequate Protection
The penalties for organizations that fail to adequately protect their email systems from spoofing attacks can be severe. These penalties can include hefty fines, legal fees, reputational damage, and loss of customer trust. Under regulations like GDPR, fines for data breaches can reach millions of euros. In the United States, the CFAA carries significant criminal penalties, including substantial fines and imprisonment for individuals involved in the attack. Civil lawsuits from affected parties seeking compensation for damages are also a possibility. The financial and legal ramifications can be crippling, underscoring the importance of proactive security measures and robust incident response planning. The potential for class-action lawsuits, further amplifying the financial burden, adds another layer of risk for organizations failing to uphold their security responsibilities.
Last Point
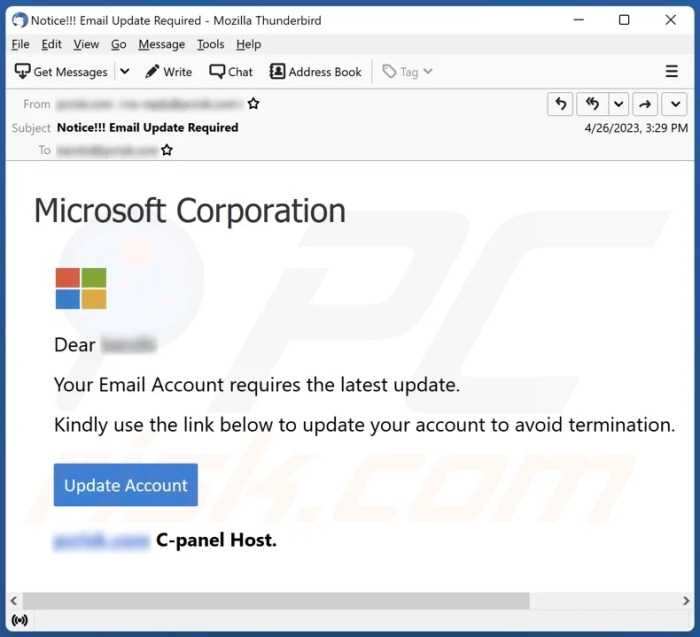
Source: pcrisk.com
In the ever-evolving landscape of cyber threats, Microsoft corporate email account spoofing remains a persistent and dangerous challenge. Understanding the tactics employed, recognizing the warning signs, and implementing proactive security measures are not just best practices—they’re essential for survival in the digital age. By arming yourself with knowledge and employing the strategies Artikeld here, you can significantly reduce your vulnerability to these attacks and protect your valuable data and reputation. Remember, vigilance is your strongest defense.



