Fortra warns of hard coded password – Fortra warns of hard-coded passwords – a seemingly small detail with massive security implications. Think of it as leaving your front door unlocked with a note saying “keys under the mat.” Hard-coded passwords are essentially digital equivalents, embedding login credentials directly into software. This opens the door (pun intended) to devastating breaches, allowing malicious actors unfettered access to sensitive data and systems. We’re diving deep into why this is a major no-no, how to spot these sneaky vulnerabilities, and most importantly, how to fix them before disaster strikes.
From understanding the vulnerabilities created by hard-coded passwords to exploring real-world attack examples, we’ll equip you with the knowledge to secure your digital fortress. We’ll cover techniques for detecting these passwords, both manually and with the help of automated tools, and provide actionable steps to remove them and prevent future occurrences. This isn’t just about technical solutions; we’ll also discuss the crucial role of security awareness training in fostering a culture of proactive security.
Fortra’s Security Warning

Source: cheggcdn.com
Fortra’s recent security warning highlighted a critical vulnerability: hard-coded passwords embedded within their software. This isn’t just a minor inconvenience; it represents a significant security risk with potentially devastating consequences for users. Understanding the implications of this practice is crucial for safeguarding sensitive data and maintaining system integrity.
Hard-coded passwords, essentially passwords directly written into the source code of a software application, create a gaping hole in security. This practice bypasses standard authentication mechanisms, leaving the system vulnerable to malicious actors. The implications are far-reaching, impacting data confidentiality, system integrity, and overall user trust.
Potential Vulnerabilities Created by Hard-Coded Passwords
The presence of hard-coded passwords introduces several critical vulnerabilities. First, anyone with access to the software’s source code—whether through a security breach, malicious insider, or even a simple code review—can easily extract these passwords. This eliminates any security provided by traditional authentication methods. Second, even compiled software isn’t completely safe. Reverse engineering techniques can sometimes reveal hard-coded credentials, especially if proper obfuscation isn’t implemented. Third, the existence of hard-coded passwords often indicates a lack of robust security practices throughout the development lifecycle, suggesting other potential vulnerabilities may exist. Finally, compromised hard-coded passwords can provide attackers with a foothold for lateral movement within a network, allowing them to access more sensitive systems and data.
Real-World Examples of Hard-Coded Password Exploits
Numerous real-world attacks demonstrate the devastating consequences of hard-coded passwords. For instance, several high-profile incidents have involved attackers gaining access to sensitive databases or internal networks simply by exploiting hard-coded credentials found within the software’s codebase. These breaches have resulted in data leaks, financial losses, and reputational damage for the affected organizations. While specific details of these incidents often remain confidential for security reasons, the common thread is always the presence of hard-coded passwords.
Hypothetical Scenario: Consequences of a Hard-Coded Password Breach
Imagine a small business using a point-of-sale (POS) system with a hard-coded password for its database. A disgruntled employee, or even a skilled attacker exploiting a software vulnerability, gains access to the source code and extracts the password. They then access the database, stealing customer credit card information and potentially sensitive personal data. The consequences could be catastrophic: significant financial losses due to fraud, legal repercussions for violating data privacy regulations, and irreparable damage to the company’s reputation. This scenario highlights the real-world risks associated with this dangerous practice.
Secure Password Management Methods
The following table compares various secure password management techniques, emphasizing their advantages and disadvantages.
| Method | Advantages | Disadvantages | Example |
|---|---|---|---|
| Environment Variables | Keeps passwords separate from the codebase, improves security. | Requires proper environment setup, still vulnerable if environment is compromised. | Storing database connection strings in environment variables. |
| Secrets Management Tools (e.g., HashiCorp Vault, AWS Secrets Manager) | Centralized, secure storage and management of sensitive information, access control, auditing capabilities. | Requires additional infrastructure and expertise, adds complexity. | Storing API keys and database passwords in a dedicated secrets management vault. |
| Configuration Files (with appropriate encryption) | Relatively easy to implement, keeps passwords separate from code. | Requires secure storage of configuration files, encryption needs to be robust. | Storing passwords in an encrypted configuration file that is only accessible to the application. |
| Key Management Systems (KMS) | Highly secure, centralized key management and control, encryption at rest and in transit. | Requires integration with a KMS provider, increased complexity. | Using a KMS to encrypt and decrypt passwords at runtime. |
Identifying Hard-Coded Passwords in Code
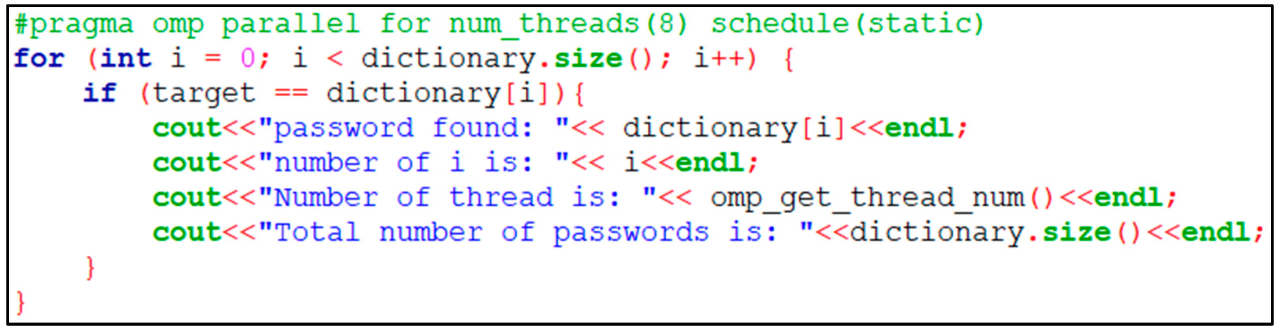
Source: mdpi-res.com
Hard-coding passwords directly into your source code is a major security vulnerability. It exposes your application to significant risks, including unauthorized access and data breaches. This section details effective methods for detecting and preventing this dangerous practice.
Manual Code Review Techniques
Experienced developers are your first line of defense. During code review, they should meticulously examine the codebase for any instances of strings resembling passwords. This includes looking for suspiciously long strings, strings containing special characters often found in passwords, or strings located near database connection details. Careful attention to areas handling authentication or authorization is crucial. Peer review offers a fresh perspective, catching what automated tools might miss.
Static and Dynamic Analysis Tools
Static analysis tools examine your code without actually executing it. These tools can scan the codebase for patterns matching known password formats or suspicious strings. Popular static analysis tools often include features specifically designed to detect hard-coded credentials. Dynamic analysis, on the other hand, involves running the application and monitoring its behavior. Tools employing dynamic analysis can identify passwords being used during runtime, even if they are obfuscated or encrypted. Combining static and dynamic analysis provides a more comprehensive approach to security.
Comparison of Code Scanning Methods
Different code scanning methods offer varying levels of accuracy and coverage. Signature-based methods look for specific patterns matching known passwords or encryption keys, while machine learning-based methods analyze code behavior and identify anomalies indicative of hard-coded credentials. Regular expression-based methods, discussed below, also fall under this umbrella. The best approach often involves a multi-layered strategy, combining several methods to improve detection rates. Consider the trade-off between the precision and recall of each method when selecting your tools. A high recall is important to avoid false negatives, even if it means accepting some false positives.
Regular Expressions for Password Detection
Regular expressions provide a powerful mechanism for identifying potential hard-coded passwords. A simple regular expression like `”[a-zA-Z0-9]8,”`, for instance, might identify strings that are at least eight characters long and contain alphanumeric characters – a common password pattern. However, more sophisticated expressions can be created to account for various password complexities, including special characters and capitalization. Remember that regular expressions are not foolproof and might generate false positives, requiring manual verification. It’s important to refine your regular expressions based on your specific context and coding standards. For example, you might need to exclude strings used as legitimate keys or identifiers.
Best Practices for Preventing Hard-Coded Passwords
Preventing hard-coded passwords starts with a strong development process.
- Employing secure configuration management tools to store and manage credentials centrally.
- Utilizing environment variables to store sensitive information outside the codebase.
- Implementing robust secret management solutions, like HashiCorp Vault or AWS Secrets Manager.
- Regularly conducting security audits and penetration testing to identify vulnerabilities.
- Educating developers on secure coding practices and the risks associated with hard-coded credentials.
Remediation Strategies for Hard-Coded Passwords
Hard-coded passwords are a major security vulnerability, leaving your systems exposed to potential breaches. Addressing this issue requires a multi-pronged approach that combines immediate remediation with long-term secure credential management practices. This isn’t just about fixing a bug; it’s about fundamentally changing how your organization handles sensitive information.
Removing Hard-Coded Passwords from Existing Code
The process of removing hard-coded passwords involves a systematic review and update of your codebase. This is often a painstaking task, especially with large or legacy systems, but it’s crucial for security. A phased approach is recommended, prioritizing the most critical applications first.
- Identify Hard-Coded Passwords: Begin by using static analysis tools to scan your code for instances of hard-coded credentials. These tools can significantly speed up the process and ensure you don’t miss any hidden passwords.
- Replace with Placeholders: Once identified, replace each hard-coded password with a placeholder, such as a variable name. This ensures the application compiles while you implement the secure alternatives.
- Implement Secure Alternatives: This involves moving the credentials to a secure location, such as environment variables or a secrets management system. We’ll discuss this in detail in the next section.
- Thorough Testing: After making the changes, thoroughly test your application to ensure that it functions correctly with the new credential management system. This includes testing various scenarios and edge cases.
- Version Control: Use a version control system (like Git) to track all changes, making it easier to revert to previous versions if necessary and providing a clear audit trail.
Secure Credential Management Approaches
Managing sensitive credentials securely requires a shift from relying on hard-coded values to employing robust, centralized systems. This approach enhances security and simplifies the management of credentials across multiple applications and environments.
- Environment Variables: Environment variables allow you to store credentials outside the application code. They are accessed at runtime, preventing them from being directly embedded in the code itself. For example, you could set a database password as an environment variable named `DB_PASSWORD`.
- Secrets Management Systems: These dedicated systems provide a centralized and secure repository for storing and managing sensitive data like passwords, API keys, and certificates. They often include features like access control, auditing, and encryption at rest and in transit. Examples include HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault.
- Configuration Management Tools: Tools like Ansible, Chef, or Puppet allow you to manage and deploy configurations securely. These tools can handle sensitive data through secure methods and ensure consistency across different environments.
Secure Configuration Management Practices
Implementing secure configuration management practices ensures that sensitive information is handled securely throughout the entire software development lifecycle. This goes beyond just storing credentials securely; it’s about establishing robust processes and controls.
Centralized configuration management systems offer several benefits: they enforce consistency across environments, simplify updates and rollbacks, and improve security by reducing the number of places where sensitive information needs to be managed.
Secure Alternatives to Hard-Coded Passwords
The most effective approach involves using environment variables or a dedicated secrets management system.
Environment Variables Example: Instead of directly embedding a password in your code like this:
database_password = "MySecretPassword123!"
You would instead access it from the environment:
database_password = os.environ.get("DB_PASSWORD")
Secrets Management System Example: A secrets management system would allow you to store the password securely, and your application would retrieve it using an API call or SDK, eliminating the need to hardcode it directly.
Challenges in Removing Hard-Coded Passwords from Legacy Systems
Removing hard-coded passwords from legacy systems presents unique challenges. These systems often lack comprehensive documentation, use outdated technologies, and may be tightly coupled, making modifications risky.
A phased approach, focusing on critical applications first, is vital. Careful planning, thorough testing, and a strong understanding of the legacy system’s architecture are essential to mitigate the risk of introducing new vulnerabilities or causing system instability during the remediation process.
Preventing Future Occurrences of Hard-Coded Passwords
Source: cheggcdn.com
So, you’ve found hard-coded passwords in your code – a major security blunder. But the good news is, you can prevent this from happening again. This isn’t just about fixing a bug; it’s about building a robust security culture within your development team. Let’s dive into how to make that happen.
This section Artikels best practices for preventing hard-coded passwords and fostering a security-conscious development environment. We’ll cover secure coding standards, the crucial role of code reviews and security testing, and how to integrate secure password management into your workflow. Think of it as building a fortress, not just patching a hole.
Secure Coding Standards and Guidelines
Following established secure coding standards is paramount. These standards provide a framework for writing code that’s inherently less vulnerable to security risks, including the insidious hard-coded password. For example, the OWASP (Open Web Application Security Project) provides comprehensive guidelines covering various aspects of secure coding, including input validation, output encoding, and error handling – all vital in preventing vulnerabilities that might lead to hard-coded credentials. Adopting a style guide that emphasizes avoiding literal values in code, instead favoring environment variables or configuration files, is crucial. This minimizes the risk of inadvertently committing sensitive information. Consider implementing static analysis tools that automatically scan your code for potential vulnerabilities, including hard-coded credentials. These tools can act as a first line of defense, catching issues early in the development process.
The Importance of Code Reviews and Security Testing
Code reviews aren’t just about catching syntax errors; they’re about catching security flaws before they reach production. Having another developer review your code provides a fresh perspective, often uncovering issues you might have missed. Specifically, focusing code reviews on identifying potential hard-coded passwords or other sensitive information is essential. Similarly, incorporating security testing into your development pipeline is non-negotiable. Penetration testing, for example, simulates real-world attacks to identify vulnerabilities, including those stemming from hard-coded passwords. Regular security audits should also be part of the process to ensure your security practices remain up-to-date and effective.
Integrating Secure Password Management into the SDLC
Secure password management shouldn’t be an afterthought; it needs to be integrated into every stage of the Software Development Lifecycle (SDLC). From the initial design phase to deployment and maintenance, the handling of passwords must be carefully considered. This means using a dedicated secrets management tool to store and manage passwords securely, preventing them from ever being directly embedded in code. These tools often provide features like access control, auditing, and rotation, significantly reducing the risk associated with password exposure. Implementing a robust CI/CD pipeline that incorporates automated security checks and utilizes secrets management tools throughout the build and deployment process is a vital step towards secure password handling. This ensures that sensitive information is never hard-coded into the application.
Security Training for Developers
Regular security training is crucial to cultivate a security-conscious development team. It’s not enough to simply provide guidelines; developers need to understand the “why” behind secure coding practices. Effective training programs should be ongoing, not a one-time event.
- Understanding common vulnerabilities and their impact.
- Secure coding practices and the importance of avoiding hard-coded credentials.
- The use of secrets management tools and other secure password handling techniques.
- The role of code reviews and security testing in identifying vulnerabilities.
- How to report and handle security incidents effectively.
The Role of Security Awareness Training: Fortra Warns Of Hard Coded Password
Let’s be real, even the most airtight security protocols are useless if your developers are walking around with passwords scribbled on sticky notes (we’ve all seen it, right?). Security awareness training isn’t just a box to tick; it’s the bedrock of a truly secure coding environment. It’s about fostering a culture where security isn’t an afterthought, but a fundamental part of the development process.
Educating developers about the risks associated with hard-coded passwords is paramount. A single hard-coded password can unravel months of meticulous coding, opening the door to data breaches, hefty fines, and reputational damage. This isn’t just about technical skills; it’s about changing mindsets and building responsible coding habits.
Comprehensive Security Awareness Training Program Aspects
A robust security awareness program needs more than just a one-off presentation. It requires a multi-faceted approach that integrates seamlessly into the developer workflow. This includes regular training sessions, interactive modules, and readily available resources. The goal is to make security awareness a continuous process, not a one-time event.
Sample Training Module: Secure Password Management
This module focuses on practical, real-world scenarios. It starts by explaining the devastating consequences of hard-coded passwords – think leaked source code leading to a major data breach, resulting in significant financial losses and legal battles. Then, it dives into best practices: using strong, unique passwords for every application, leveraging password managers, and understanding the importance of secure storage mechanisms like secret management tools. Real-world examples of companies that suffered breaches due to hard-coded passwords are presented, highlighting the devastating impact. The module concludes with a quiz to reinforce learning and identify knowledge gaps. This quiz includes scenarios where developers have to identify and suggest solutions for code snippets containing hard-coded passwords.
Benefits of Regular Security Audits and Penetration Testing, Fortra warns of hard coded password
Think of regular security audits and penetration testing as a comprehensive health check for your codebase. These aren’t just about finding vulnerabilities; they’re about proactively identifying weaknesses before they can be exploited. Regular audits uncover hidden hard-coded passwords, while penetration testing simulates real-world attacks to expose vulnerabilities in your security posture. This proactive approach significantly reduces the risk of breaches and ensures your systems are resilient against potential threats. The findings from these audits can be directly incorporated into future training sessions, reinforcing learning and adapting to emerging threats.
Impact of a Strong Security Culture
A strong security culture isn’t about imposing rules; it’s about fostering a shared sense of responsibility. When security is woven into the fabric of the development process, developers become proactive participants in protecting sensitive information. This includes open communication about security concerns, a culture of reporting vulnerabilities, and a commitment to continuous learning and improvement. A strong security culture makes hard-coded passwords not just a technical problem, but a collective ethical responsibility, reducing their occurrence significantly.
End of Discussion
In the end, Fortra’s warning about hard-coded passwords serves as a stark reminder: security is a continuous process, not a destination. While removing existing hard-coded credentials is critical, proactive measures – secure coding practices, rigorous code reviews, and comprehensive security training – are paramount. By adopting a holistic approach, you can significantly reduce your organization’s attack surface and protect yourself from the devastating consequences of a simple, yet easily avoidable, oversight.


