Malware shielded by Themida and VMProtect? Yeah, it’s a real headache for security researchers. These protectors are like Fort Knox for malicious code, making it incredibly tough to analyze and understand how these nasty programs work. We’re diving deep into the world of advanced malware protection, comparing these two heavy hitters, exploring how bad actors use them, and ultimately, figuring out how to fight back.
Think of Themida and VMProtect as the ultimate camouflage for malware. They obfuscate the code, making it nearly impossible to decipher what the malware is actually doing. This makes traditional antivirus solutions less effective and turns the analysis process into a real cat-and-mouse game. We’ll explore the strengths and weaknesses of each protector, the common malware families that utilize them, and the innovative techniques used by security researchers to strip away their defenses.
Themida and VMProtect
Themida and VMProtect are two leading software protectors used to safeguard applications from unauthorized access, reverse engineering, and cracking. Both employ advanced techniques to make it significantly more difficult for malicious actors to understand and modify the protected code. However, they differ in their approaches and strengths. Understanding these differences is crucial for developers choosing the right protection for their software.
A Feature Comparison of Themida and VMProtect
Themida and VMProtect each offer a robust suite of protection features, but their implementations and effectiveness vary. Choosing between them often depends on specific needs and priorities. The following table summarizes key differences:
| Feature | Themida | VMProtect |
|---|---|---|
| Obfuscation Techniques | Control flow obfuscation, string encryption, code virtualization | Control flow obfuscation, code virtualization, anti-debugging techniques, packing |
| Anti-Debugging Techniques | Strong anti-debugging measures, including detection of common debuggers and emulation environments | Advanced anti-debugging, anti-dumping, and anti-analysis techniques; includes detection of various debugging tools and techniques |
| Virtualization Layer | Uses virtualization to protect critical code segments | Employs a sophisticated virtualization layer to significantly hinder reverse engineering |
| Licensing Model | Typically subscription-based, with various tiers based on features and number of licenses. | Offers both node-locked and floating licenses, with pricing dependent on the chosen license type and features. |
Strengths and Weaknesses of Themida, Malware shielded by themida and vmprotect
Themida excels at obfuscating code and employing robust anti-debugging techniques. Its virtualization layer makes dynamic analysis significantly harder. However, extremely determined attackers might still find ways to bypass some protections through advanced techniques or exploiting vulnerabilities in the protector itself. The subscription-based model can be a factor for some developers.
Strengths and Weaknesses of VMProtect
VMProtect is known for its powerful virtualization capabilities, making it very challenging to analyze the protected code. Its anti-debugging and anti-dumping measures are also highly effective. A potential weakness is the complexity of its setup and configuration, which might require more technical expertise than Themida. The licensing options offer flexibility but also require careful consideration based on specific project needs.
Malware Techniques Utilizing Themida and VMProtect
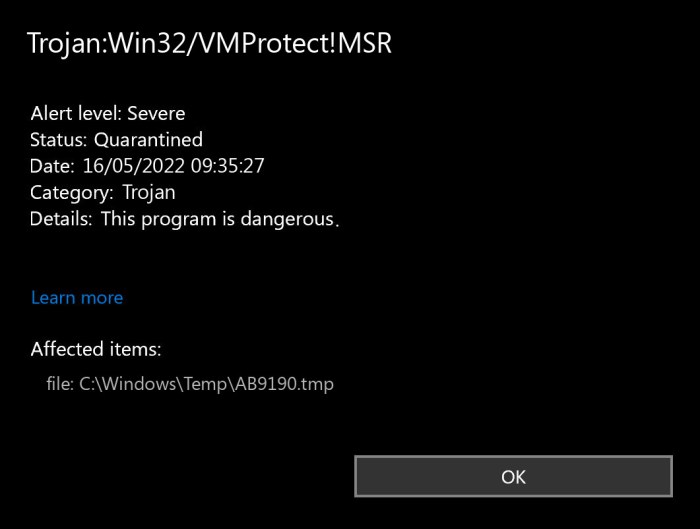
Source: howtofix.guide
Themida and VMProtect are popular commercial code protectors frequently abused by malware authors to hinder reverse engineering and analysis. These tools offer a range of obfuscation and anti-debugging techniques, making malware analysis significantly more challenging and extending the lifespan of malicious campaigns. Understanding how malware leverages these protectors is crucial for effective security measures.
Malware families employing Themida and VMProtect span a wide spectrum of threats, ranging from banking Trojans to ransomware and information stealers. The choice of protector often depends on the malware’s complexity and the author’s resources. The sophisticated techniques employed by these protectors, coupled with the creativity of malware developers, creates a constantly evolving arms race in cybersecurity.
Common Malware Families Using Themida or VMProtect
Several notorious malware families have been observed utilizing Themida or VMProtect. These protectors add layers of complexity, making static and dynamic analysis difficult. The effectiveness of these protections varies depending on the specific implementation and the skill of the malware author. For example, a poorly implemented protection scheme might be easily bypassed, while a sophisticated one can significantly hinder analysis efforts. Examples include, but are not limited to, certain strains of ransomware and banking Trojans that utilize these protectors to evade detection and analysis. Specific examples often remain undisclosed due to ongoing investigations and the need for protecting sensitive information about ongoing threats.
Evasion Techniques Employed by Malware Using Themida and VMProtect
Malware using these protectors often employs several evasion techniques to thwart analysis. These techniques can range from simple code obfuscation to advanced anti-debugging and anti-virtualization methods. For example, the malware might use code virtualization to make the code execution flow incredibly difficult to trace. Furthermore, the use of anti-debugging techniques, such as checking for the presence of debuggers or modifying system calls to detect analysis tools, can hinder dynamic analysis. The malware might also employ polymorphism or metamorphic techniques to change its code structure and behavior over time, making signature-based detection more difficult.
Impact on Static and Dynamic Analysis
Themida and VMProtect significantly hinder both static and dynamic analysis. Static analysis, which involves examining the malware’s code without executing it, is hampered by the extensive code obfuscation and encryption techniques implemented by these protectors. The code’s structure becomes highly complex, making it difficult to identify malicious functions and understand the malware’s behavior. Dynamic analysis, which involves executing the malware in a controlled environment, is challenged by anti-debugging and anti-virtualization techniques. The malware might detect the presence of a debugger or virtual machine and terminate its execution or alter its behavior to avoid detection.
Methods for Bypassing Themida and VMProtect
Malware authors often employ techniques to bypass or circumvent the security features of Themida and VMProtect. These techniques can include exploiting vulnerabilities in the protectors themselves or employing advanced reverse engineering skills to manually disassemble and analyze the protected code. This often involves using advanced debugging tools and techniques, including memory analysis, to understand the code’s behavior and identify the underlying malicious logic. The effectiveness of these bypass methods depends heavily on the sophistication of the protection implemented by the malware author and the expertise of the analyst attempting to bypass it. Successful bypasses often involve a combination of multiple techniques and require significant time and effort.
Reverse Engineering Challenges Posed by Themida and VMProtect
Delving into the depths of malware protected by Themida and VMProtect is like navigating a complex labyrinth. These protectors employ sophisticated techniques to obfuscate the malware’s true functionality, making reverse engineering a significant challenge for security researchers. The layers of protection significantly increase the time and expertise needed to understand the malware’s behavior and malicious intent.
These protectors utilize various anti-debugging and anti-analysis techniques to hinder reverse engineering efforts. They dynamically encrypt and decrypt code sections, making static analysis difficult and requiring dynamic analysis methods. Furthermore, they often employ virtualization techniques, creating a simulated environment that makes it challenging to trace the actual execution flow. This makes understanding the malware’s actions a complex and time-consuming process.
Themida and VMProtect’s Anti-Debugging and Anti-Analysis Techniques
Themida and VMProtect employ a range of techniques to thwart reverse engineering attempts. These include code virtualization, anti-debugging checks, and sophisticated packing algorithms. The combined effect makes static analysis exceptionally difficult and necessitates the use of advanced dynamic analysis tools and techniques. Understanding these techniques is crucial for successfully reverse engineering protected malware.
Overcoming Themida and VMProtect Protections
Reverse engineers utilize several strategies to overcome these protections. These methods often involve a combination of techniques, requiring patience, persistence, and a deep understanding of both the protectors and the underlying malware. The process is iterative, with each step informing the next.
Debugger and Disassembler Utilization in Analysis
Debuggers like x64dbg and IDA Pro are indispensable tools for dynamic analysis. Debuggers allow step-by-step execution of the code, providing visibility into the program’s internal state and registers. Disassemblers, such as IDA Pro, convert the machine code into assembly language, making it more human-readable and facilitating the identification of key functions and code sections. The combination of these tools enables a deeper understanding of the malware’s behavior.
Step-by-Step Procedure for Analyzing a Protected Sample
Analyzing a Themida or VMProtect-protected sample requires a methodical approach. The process is often iterative, requiring adjustments based on the specific techniques employed by the protector.
- Initial Static Analysis: Examine the sample’s metadata, file headers, and imports using tools like PEiD or FLOSS. This provides initial clues about the protector and potential entry points.
- Unpacking: Employ unpacking techniques to remove the protector’s layers. This might involve manual analysis, using automated unpacking tools, or a combination of both. This stage is often the most challenging.
- Dynamic Analysis: Utilize a debugger to run the unpacked sample in a controlled environment. Monitor the execution flow, memory accesses, and system calls to identify malicious activities. This often requires setting breakpoints and single-stepping through critical code sections.
- Disassembly and Code Analysis: Analyze the disassembled code using a disassembler like IDA Pro to understand the functionality of different code sections. Identify key functions, data structures, and algorithms used by the malware.
- Behavioral Analysis: Observe the malware’s behavior in a sandboxed environment. This helps to identify its malicious actions without risking damage to your system. Note any network connections, file modifications, or registry changes.
Detection and Mitigation Strategies

Source: medium.com
Unmasking malware shielded by sophisticated protectors like Themida and VMProtect requires a multi-layered approach. These tools are designed to hinder reverse engineering and analysis, making traditional antivirus signatures less effective. Therefore, a robust strategy needs to combine various detection methods and proactive security measures.
Detecting malware employing Themida and VMProtect necessitates a shift from relying solely on signature-based detection to a more comprehensive strategy that incorporates behavioral analysis and proactive threat hunting. The complexity of these protectors necessitates a layered approach to effectively identify and mitigate the threats they conceal.
Signature-Based Detection Limitations
Signature-based detection, while a cornerstone of many antivirus solutions, struggles against obfuscated malware. Themida and VMProtect actively transform the malware’s code, making it difficult for traditional signature matching to identify the malicious payload. Signatures are created based on known malware samples; as these protectors change the code’s structure, existing signatures become ineffective. This necessitates a complementary approach focusing on behavioral analysis.
Heuristic-Based Detection and Behavioral Analysis
Heuristic-based detection focuses on identifying suspicious behaviors rather than specific code patterns. This approach is more effective against obfuscated malware because it analyzes the actions the program performs, regardless of its altered code. For example, a heuristic system might flag a program that attempts to connect to known command-and-control servers, modifies system files without authorization, or exhibits unusual memory access patterns, even if the code itself is heavily obfuscated by Themida or VMProtect. This method is crucial for detecting zero-day malware or variants that haven’t yet been cataloged in signature databases.
Sandboxing and Emulation Techniques
Sandboxing provides a controlled environment to execute suspicious files. This isolates the program from the rest of the system, allowing analysts to observe its behavior without risking infection. Emulation takes this a step further by simulating a target system’s environment, providing a highly controlled and repeatable testing ground. Advanced sandboxes can analyze the malware’s dynamic behavior, network activity, and registry modifications, providing invaluable insights even when the malware is heavily protected. For example, a sandbox might detect a program attempting to steal sensitive data, even if the data exfiltration code is obscured by VMProtect.
Flowchart for Identifying and Mitigating Themida/VMProtect-Protected Malware
The process of identifying and mitigating malware protected by Themida and VMProtect can be represented by a flowchart. The flowchart would begin with the detection of suspicious activity, potentially triggered by a heuristic-based system or an anomaly detection engine. This would lead to the analysis of the suspicious sample in a sandboxed environment. Successful identification of malicious behavior would then trigger the appropriate mitigation actions, such as quarantine, removal, and incident response procedures. The flowchart would visually represent the sequential steps, branching paths based on analysis results, and culminating in the resolution of the security incident. This visualization helps streamline the incident response process, ensuring efficiency and minimizing potential damage.
The Arms Race
The battle between malware developers and security researchers is a constant, evolving conflict. It’s a never-ending game of cat and mouse, with each side constantly adapting and innovating to outmaneuver the other. The sophistication of malware protection techniques, like those employed by Themida and VMProtect, reflects this ongoing arms race.
Malware authors are driven by profit, espionage, or disruption, constantly seeking new ways to bypass security measures. Their techniques are often highly specialized and adapt rapidly to the latest detection methods. This necessitates a similarly agile response from the security community.
Malware Adaptation Strategies
Malware authors employ a range of techniques to evade detection. These strategies are frequently combined to create a layered defense against reverse engineering and analysis. One common approach is polymorphism, where the malware’s code is altered each time it’s executed, making static analysis difficult. Another tactic involves using obfuscation techniques to make the code extremely difficult to understand, even for experienced reverse engineers. Finally, the use of anti-debugging and anti-virtualization techniques actively hinders analysis attempts. For example, malware might check for the presence of debuggers or virtual machines and terminate execution if detected. This forces researchers to employ advanced techniques to circumvent these defenses.
Evolution of Themida and VMProtect
Themida and VMProtect, two prominent software protectors, have themselves evolved in response to the increasing sophistication of reverse engineering tools and techniques. Early versions relied heavily on basic code obfuscation and encryption. However, as reverse engineering techniques advanced, these protectors incorporated more advanced anti-debugging and anti-virtualization measures. Recent versions often include dynamic code generation, making static analysis practically impossible. They also incorporate advanced packing and encryption algorithms, making it significantly harder to unpack and analyze the protected code. This continuous arms race pushes both sides to develop increasingly complex and innovative solutions.
Future Trends in Malware Protection and Detection
Predicting the future of this arms race is challenging, but several trends are likely to shape the landscape. We can anticipate a rise in the use of artificial intelligence (AI) and machine learning (ML) on both sides. Malware authors might use AI to generate more sophisticated and polymorphic code, while security researchers could leverage AI to automate the analysis and detection of malware. Furthermore, the increased use of virtualization and cloud computing will likely influence both malware development and detection strategies. For example, malware might be designed to specifically target cloud environments, while security solutions will need to adapt to detect and mitigate threats in these dynamic settings. The ongoing development of quantum computing also presents a significant challenge and opportunity, potentially impacting both encryption algorithms used in malware protection and the development of entirely new detection techniques. The development of more sophisticated, AI-driven sandboxing environments to analyze malware behavior without triggering its anti-analysis mechanisms is also a key area of future development.
Illustrative Example
Source: ibb.co
Let’s dive into a hypothetical scenario involving a particularly nasty piece of malware, cleverly disguised and protected by both Themida and VMProtect. This dual-layered protection makes analysis significantly more challenging, highlighting the effectiveness – and the frustration – of these powerful protectors.
This hypothetical malware, which we’ll call “CrypticMiner,” is a cryptocurrency miner designed to stealthily consume system resources for illicit profit. Its functionality extends beyond simple mining, incorporating features to evade detection and hinder analysis.
CrypticMiner Functionality and Infection Vector
CrypticMiner’s primary function is to secretly mine Monero, a privacy-focused cryptocurrency. It achieves this by utilizing a sophisticated algorithm to dynamically adjust its mining intensity based on system load. If the system is under heavy load, the miner scales back its activity to avoid detection. Conversely, if the system is idle, it ramps up its mining operations to maximize profit. The infection vector is a seemingly innocuous software update delivered through a compromised website. The user, believing they are installing a legitimate program update, unwittingly executes the malware installer. This installer cleverly uses social engineering techniques, mimicking the appearance of legitimate software. Once installed, CrypticMiner establishes persistence by creating a scheduled task, ensuring it runs automatically on system startup.
CrypticMiner Evasion Techniques
CrypticMiner employs several evasion techniques to avoid detection by antivirus software and security researchers. These include:
- Themida and VMProtect Protection: The core mining functionality is heavily obfuscated and protected by both Themida and VMProtect, making static analysis extremely difficult.
- Anti-Debugging Techniques: The malware actively checks for the presence of debuggers and virtual machines, halting its execution or employing deceptive behavior if detected.
- Network Obfuscation: CrypticMiner communicates with its command-and-control (C&C) server using encrypted channels and dynamically changing IP addresses to avoid network-based intrusion detection systems.
- Rootkit Capabilities: The malware attempts to hide its processes and network activity from the operating system, making it difficult to detect its presence.
Challenges for Security Researchers
Analyzing CrypticMiner presents several significant challenges to security researchers. The dual-layered protection offered by Themida and VMProtect necessitates advanced reverse-engineering techniques. The anti-debugging mechanisms make dynamic analysis difficult, while the network obfuscation hinders network traffic analysis. The rootkit capabilities further complicate the process of identifying and removing the malware. Essentially, it’s a cat-and-mouse game requiring patience, skill, and a comprehensive toolkit.
Analysis Methodology
Analyzing CrypticMiner would require a multi-faceted approach. The process would likely involve:
- Static Analysis: Using disassemblers like IDA Pro to examine the malware’s code structure and identify potential entry points. This stage would focus on understanding the overall architecture and identifying obfuscation techniques.
- Dynamic Analysis: Utilizing debuggers like x64dbg or WinDbg to monitor the malware’s execution in a controlled environment. This involves carefully stepping through the code, bypassing anti-debugging techniques, and observing its behavior.
- Sandbox Analysis: Running the malware within a virtual machine environment to isolate it from the researcher’s system and monitor its network activity and system interactions.
- Memory Forensics: Examining the malware’s memory footprint to identify hidden processes, network connections, and other artifacts.
- Themida/VMProtect Specific Tools: Employing specialized tools designed to unpack and analyze Themida and VMProtect protected samples, though this is often a highly complex undertaking.
Outcome Summary: Malware Shielded By Themida And Vmprotect
So, the battle between malware authors and security researchers continues, a never-ending arms race fueled by innovation on both sides. Themida and VMProtect represent a significant challenge, but by understanding their mechanisms and employing advanced reverse engineering techniques, we can better equip ourselves to detect and mitigate the threats they shield. The key takeaway? Staying ahead of the curve requires constant learning and adaptation – the game is always evolving.



