Microsoft Detect Compromised Devices: It’s a digital battlefield out there, and your precious data is the prize. This isn’t some sci-fi thriller; it’s the reality of modern cybersecurity. From sneaky malware to full-blown breaches, the threats are real, but so are the defenses. This deep dive explores how Microsoft actively hunts down compromised devices, the telltale signs to watch out for, and the strategies to keep your digital fortress secure.
We’ll unpack Microsoft’s arsenal of detection methods, from the ever-vigilant Microsoft Defender for Endpoint to the proactive intelligence of Microsoft 365 Defender. We’ll also examine Indicators of Compromise (IOCs), those subtle clues that betray a compromised system. Learn how to spot them, how to respond effectively, and—crucially—how to prevent future attacks. Get ready to level up your cybersecurity game.
Microsoft’s Detection Methods
Source: hacklido.com
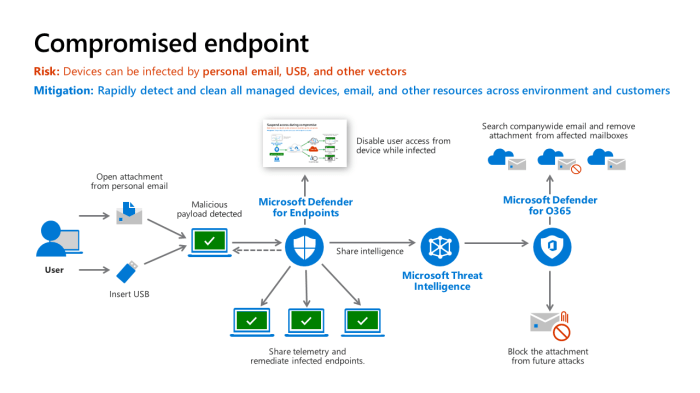
Microsoft’s vast ecosystem requires a multi-layered approach to security, and detecting compromised devices is a crucial part of that. Their strategy involves a combination of cloud-based intelligence, on-device monitoring, and proactive threat hunting to identify and respond to malicious activity swiftly and effectively. This ensures that threats are neutralized before they can cause significant damage or data breaches.
Microsoft Defender for Endpoint’s Malicious Activity Identification
Microsoft Defender for Endpoint uses a range of techniques to pinpoint malicious activity. This includes real-time behavioral analysis, identifying suspicious processes and file modifications. It leverages machine learning to detect anomalies in system activity, flagging unusual patterns that might indicate a compromise. Furthermore, it utilizes cloud-based threat intelligence to cross-reference observed behavior with known malicious signatures and indicators of compromise (IOCs), providing context and prioritization for alerts. The system also employs advanced threat hunting capabilities, enabling security professionals to proactively search for hidden threats that might have evaded initial detection. This proactive approach is crucial in catching sophisticated attacks that might otherwise go unnoticed.
Microsoft 365 Defender’s Role in Detection and Response
Microsoft 365 Defender acts as a central hub, correlating data from various Microsoft security solutions, including Defender for Endpoint, Microsoft Cloud App Security, and Azure ATP. This unified view provides a comprehensive understanding of threats across the entire Microsoft 365 environment. By integrating data from different sources, Microsoft 365 Defender can identify patterns and connections that might be missed by individual security products. It uses this integrated intelligence to not only detect compromised devices but also to orchestrate automated responses, such as isolating infected devices or blocking malicious communication channels. This coordinated response significantly reduces the impact of security incidents.
Comparing Microsoft Intune and Microsoft Defender for Endpoint, Microsoft detect compromised devices
Both Microsoft Intune and Microsoft Defender for Endpoint play vital roles in securing devices, but their approaches differ. Intune focuses primarily on device management and compliance, ensuring that devices meet specific security policies. It can enforce policies such as password complexity, software updates, and VPN usage. Defender for Endpoint, on the other hand, concentrates on threat detection and response. It actively monitors devices for malicious activity and provides tools to investigate and remediate threats. While Intune can detect some security issues through compliance checks, Defender for Endpoint offers a much more granular and proactive approach to threat detection and response. They work best in tandem; Intune ensures a baseline security posture, while Defender for Endpoint actively hunts for and neutralizes advanced threats.
Response Times of Microsoft Security Solutions
| Security Solution | Detection Time (Estimated) | Response Time (Estimated) | Notes |
|---|---|---|---|
| Microsoft Defender for Endpoint | Near real-time | Seconds to minutes (depending on automated response configuration) | Real-time monitoring and automated responses. |
| Microsoft 365 Defender | Varies depending on data source | Minutes to hours (depending on alert prioritization and human intervention) | Correlation of data from multiple sources may introduce some delay. |
| Microsoft Intune | Hours to days (depending on policy check frequency) | Varies depending on remediation method | Primarily focuses on policy compliance, not real-time threat detection. |
| Azure ATP | Near real-time | Minutes to hours (depending on alert prioritization and human intervention) | Focuses on detecting attacks targeting on-premises Active Directory. |
Indicators of Compromise (IOCs)
So, your Microsoft devices are acting a little…suspicious? Don’t panic, but let’s talk about Indicators of Compromise (IOCs). These are the digital breadcrumbs that malicious actors leave behind, hinting at a breach or infection. Understanding IOCs is crucial for quickly identifying and responding to security incidents before they escalate into full-blown disasters. Think of them as the clues in a digital detective story – the sooner you spot them, the better your chances of solving the case.
IOCs manifest in various ways, depending on the nature of the attack. Malware infections might leave traces in system logs, while data breaches could reveal unusual network activity or unauthorized access attempts. The key is to know what to look for and where to look for it. We’ll break down common IOCs, their implications, and how to effectively leverage threat intelligence to stay ahead of the game.
Malware Infection Indicators
Malware infections often leave behind telltale signs. These can range from unusual processes running in the background to changes in system configurations. For example, a sudden spike in disk activity during off-peak hours could indicate a malware infection actively encrypting files. Similarly, unexpected network connections to unfamiliar IP addresses are strong indicators of a compromised system attempting to communicate with a command-and-control server. Detecting these anomalies requires vigilant monitoring and a deep understanding of your system’s normal baseline behavior. Remember, the earlier you identify these indicators, the easier it is to contain the infection and prevent further damage.
Data Breach Indicators
Data breaches are often more subtle than malware infections, requiring a more thorough investigation. Unusual login attempts from unfamiliar locations, especially involving privileged accounts, are major red flags. Large volumes of data being transferred outside the network, or access to sensitive data by unauthorized users, are also clear indicators of a compromise. Analyzing network traffic logs and access logs for inconsistencies and anomalies is critical in detecting these breaches. Think of it like auditing your digital finances – any unexpected withdrawals should raise immediate concerns.
Unauthorized Access Indicators
Unauthorized access attempts can manifest in a variety of ways, ranging from brute-force attacks to sophisticated social engineering techniques. Failed login attempts from multiple IP addresses, especially those geographically distant from the usual login locations, should raise immediate concerns. Unexplained changes in system permissions or the creation of new user accounts without authorization are also major red flags. Regular security audits and the implementation of multi-factor authentication are vital in mitigating the risk of unauthorized access.
Utilizing Threat Intelligence Feeds
Threat intelligence feeds are invaluable resources in identifying IOCs. These feeds provide real-time updates on known malicious IP addresses, domains, and file hashes. By comparing your system’s activity against these feeds, you can quickly identify potential threats and take appropriate action. Think of threat intelligence as a preemptive strike – it allows you to anticipate and neutralize threats before they even reach your systems. Many security vendors offer these feeds, and integrating them into your security infrastructure is a proactive step towards enhanced protection.
Analyzing System and Event Logs
System and event logs are goldmines of information, providing a detailed record of system activity. Analyzing these logs for anomalies and suspicious events is crucial in detecting IOCs. Look for events such as unauthorized file access, unusual process executions, and failed login attempts. Regularly reviewing these logs and setting up alerts for suspicious activity can help you proactively identify and address potential threats. Think of it as a detailed digital audit trail – it provides the evidence you need to pinpoint the source of a compromise.
IOCs by Severity Level
The following list categorizes IOCs based on their severity level, providing descriptions and potential impact.
- Critical: Unauthorized access to sensitive data (e.g., customer PII, financial records), complete system compromise leading to ransomware encryption, significant data exfiltration. Potential Impact: Severe financial losses, reputational damage, legal repercussions.
- High: Suspicious network connections to known malicious IP addresses, significant increase in failed login attempts, unauthorized modification of system configurations. Potential Impact: Malware infection, data breach, system instability.
- Medium: Unusual user activity patterns, unexpected software installations, attempts to access restricted files. Potential Impact: Potential malware infection, compromised accounts, minor data leakage.
- Low: Minor anomalies in system logs, infrequent failed login attempts, minor configuration changes. Potential Impact: Possible reconnaissance activity, minor security vulnerabilities.
Remediation Strategies
Source: microsoft.com
So, your Microsoft device is compromised. Panic is understandable, but controlled action is key. Effective remediation involves a multi-step process, aiming to neutralize the threat, restore system integrity, and prevent future attacks. Think of it like a meticulous cleanup after a digital break-in – thoroughness is paramount.
Remediation isn’t just about fixing the immediate problem; it’s about building stronger defenses for the future. This involves not only removing malware but also patching vulnerabilities and implementing robust security practices to prevent similar incidents. Let’s dive into the specific strategies.
Isolating a Compromised Device
Isolating a compromised device is the first crucial step. This prevents the malware from spreading to other devices on your network and limits further damage. This involves physically disconnecting the device from the network (unplugging the Ethernet cable and disabling Wi-Fi) or, if managed through a network system, using network access control tools to block the device’s access. Speed is of the essence here; the longer the device remains connected, the greater the potential for damage. Imagine it like containing a fire – you need to stop the spread before tackling the flames directly.
Removing Malware and Restoring System Integrity
Once isolated, the next step is to eliminate the malware. This might involve using specialized anti-malware software, performing a system restore to a previous point before the infection, or, in severe cases, a complete reinstallation of the operating system. A clean installation ensures a fresh start, free from any lingering malicious code. Consider this akin to thoroughly scrubbing a contaminated surface – you want to eliminate all traces of the contaminant. Before reinstalling the OS, ensure you’ve backed up any crucial data from the device that hasn’t been compromised.
Patching and Software Updates
Regular patching and updating of software is crucial for preventing future compromises. Outdated software often contains vulnerabilities that attackers can exploit. Microsoft regularly releases security updates to address these vulnerabilities. Think of software updates as reinforcing your digital defenses – each update strengthens your system’s resistance to attacks. Enable automatic updates whenever possible to ensure your system is always up-to-date with the latest security patches.
Data Recovery from a Compromised Device
Recovering data from a compromised device requires a cautious approach. The process depends on the extent of the compromise and the type of malware involved. If the malware hasn’t encrypted your data, a simple backup restoration might suffice. However, if encryption is involved, specialized data recovery tools might be necessary. In some cases, professional data recovery services may be required.
- Assess the situation: Determine the type and extent of the data loss.
- Backup existing data: Copy any unaffected data to a safe external drive or cloud storage.
- Utilize data recovery software: Employ specialized tools designed to recover data from corrupted or encrypted drives.
- Seek professional help: If data recovery proves too complex, consult a data recovery specialist.
- Verify data integrity: After recovery, check the integrity of the retrieved data to ensure its usability.
Prevention and Mitigation Techniques
Proactive measures are crucial in preventing device compromise and minimizing the impact of successful attacks. A layered security approach, combining technical controls with robust security awareness, is the most effective strategy. By understanding and implementing these preventative measures, organizations can significantly reduce their vulnerability to cyber threats.
Implementing a comprehensive security strategy involves multiple layers of defense. A single point of failure can compromise the entire system, so redundancy and layered approaches are essential. This approach ensures that even if one layer is breached, others remain to protect sensitive data and systems.
Preventative Measures to Reduce Compromise Risk
A robust security posture begins with a proactive approach. These preventative measures significantly reduce the likelihood of a successful attack, minimizing the potential for data breaches and operational disruption.
- Strong Passwords and Password Management: Enforce strong, unique passwords for all accounts and encourage the use of password managers to streamline this process. Regular password changes are also crucial.
- Regular Software Updates: Promptly apply operating system, application, and firmware updates to patch known vulnerabilities. This is a fundamental aspect of reducing exposure to exploits.
- Firewall and Anti-malware Software: Deploy and maintain robust firewalls and anti-malware solutions on all devices. Regularly update these programs with the latest threat definitions.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access, even if a device is compromised.
- Principle of Least Privilege: Grant users only the necessary access rights to perform their jobs. This limits the damage a compromised account can inflict.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and address weaknesses in the security infrastructure.
Benefits of Multi-Factor Authentication (MFA)
Multi-factor authentication significantly enhances security by requiring multiple forms of verification before granting access. This layered approach makes it considerably more difficult for attackers to gain unauthorized access, even if they possess stolen credentials.
- Increased Security: MFA adds an extra layer of protection beyond just passwords, making it much harder for attackers to gain access, even if they’ve obtained usernames and passwords.
- Reduced Risk of Phishing Attacks: MFA makes phishing attacks far less effective because even if a user falls for a phishing attempt, the attacker still needs access to a second authentication factor.
- Improved Compliance: Many industry regulations require or strongly recommend the use of MFA to protect sensitive data.
Importance of Employee Security Awareness Training
Human error is a significant factor in many security breaches. Regular security awareness training empowers employees to identify and avoid common threats, acting as a crucial first line of defense.
- Phishing Awareness: Training helps employees recognize and avoid phishing scams, a common vector for malware and data breaches.
- Social Engineering Awareness: Education on social engineering tactics helps employees resist manipulative attempts to obtain sensitive information.
- Password Security Best Practices: Training reinforces the importance of strong, unique passwords and secure password management techniques.
- Reporting Suspicious Activity: Employees learn to promptly report suspicious emails, websites, or other activities to the IT security team.
Role of Network Segmentation in Mitigating Compromise Impact
Network segmentation divides a network into smaller, isolated segments. This limits the impact of a security breach by preventing an attacker from easily moving laterally across the network and accessing sensitive data or systems.
For example, separating the guest Wi-Fi network from the internal corporate network prevents a compromised guest device from accessing critical internal systems. Similarly, segmenting sensitive data servers from less critical systems limits the potential damage if one segment is compromised.
Visual Representation of Device Security Layers
Imagine a castle with multiple concentric walls. The innermost wall represents the device itself, with built-in security features like encryption and secure boot. The next wall is the operating system, with its security updates and access controls. The next wall is the network security, including firewalls and intrusion detection systems. The outermost wall represents the physical security of the device and the surrounding environment, including physical locks and security cameras. Each wall adds a layer of protection, making it progressively more difficult for attackers to breach the inner sanctum and access sensitive data.
Impact Assessment and Reporting
So, your organization’s network just got a little… uninvited. A compromised device is more than just a minor inconvenience; it’s a potential Pandora’s Box of security breaches and reputational damage. Understanding the impact and reporting it effectively is crucial for recovery and preventing future incidents. This isn’t just about ticking boxes; it’s about safeguarding your business.
Assessing the impact of a compromised device involves a methodical approach, going beyond simply identifying the infected machine. It requires a deep dive into the system’s access level, the data it held, and the potential pathways for lateral movement within the network. The speed and thoroughness of this assessment directly influences the effectiveness of the remediation and the overall recovery process.
Assessing the Impact of a Compromised Device
This involves a multi-faceted investigation. First, determine the extent of the compromise. What data was accessible to the attacker? Was it sensitive customer information, financial records, intellectual property, or something less critical? Next, identify the compromised device’s role within the network. Was it a workstation, server, or IoT device? Its position influences the potential reach of the attack. Finally, analyze the attacker’s actions. What did they do? Did they exfiltrate data, install malware, or simply gain access for reconnaissance? This information is vital in shaping the recovery and prevention strategies.
Potential Consequences of a Data Breach
The consequences of a data breach stemming from a compromised device can be far-reaching and devastating. Financial losses from fines, legal fees, and remediation efforts are a given. Reputational damage can be even more costly, leading to loss of customer trust and market share. Regulatory penalties, particularly under GDPR or CCPA, can be crippling. In extreme cases, breaches can even lead to operational disruption and business interruption. Consider the Target breach of 2013, where stolen credit card data resulted in massive financial losses and lasting reputational damage. This serves as a stark reminder of the severe consequences.
Creating a Detailed Incident Report
A comprehensive incident report is your roadmap to recovery and prevention. It should be a meticulous record of the entire event, from initial discovery to resolution. The report should be clear, concise, and easily understandable for both technical and non-technical audiences. It’s not just for internal use; it may be required for regulatory compliance or legal proceedings. Accuracy is paramount. Every detail, from timestamps to specific actions taken, needs to be documented accurately.
Key Information for a Post-Incident Report
The following information should be meticulously documented:
- Date and Time of Discovery: When was the compromise first detected?
- Affected Systems: A complete list of compromised devices and their roles within the network.
- Type of Compromise: Malware infection, phishing attack, insider threat, etc.
- Data Breached (if any): Specific types of data compromised and the estimated volume.
- Attacker Actions: Detailed description of the attacker’s activities on the compromised system.
- Remediation Steps Taken: A chronological list of actions taken to contain and remediate the breach.
- Lessons Learned: Key insights gained from the incident that can inform future security improvements.
- Financial Impact: Estimated costs associated with the breach, including remediation, legal fees, and potential fines.
Presenting Findings to Stakeholders
Presenting the findings of a compromised device investigation requires clear and concise communication. Avoid technical jargon and focus on the key impacts and remediation steps. Use visuals like charts and graphs to illustrate the scope of the breach and the effectiveness of the response. Transparency is key; stakeholders need to understand the situation, the risks, and the steps taken to mitigate them. A well-structured presentation, delivered with confidence, can help to maintain trust and prevent further damage to the organization’s reputation. Consider using a combination of verbal presentation and a written report to ensure all stakeholders have access to the information.
Closure: Microsoft Detect Compromised Devices
Source: 2-spyware.com
In the ever-evolving world of cybersecurity, staying ahead of the curve is crucial. Understanding how Microsoft detects and responds to compromised devices is no longer a luxury; it’s a necessity. By recognizing the indicators of compromise, implementing robust preventative measures, and mastering remediation strategies, you can significantly reduce your risk and protect your valuable data. Remember, a proactive approach is your best defense in this ongoing digital war.



