NHS ransomware attack leads us down a rabbit hole of cybersecurity nightmares. Imagine: vital patient data held hostage, life-saving treatments delayed, and the entire healthcare system brought to its knees. This isn’t some dystopian fiction; it’s the harsh reality facing the National Health Service, a relentless target for cybercriminals exploiting vulnerabilities for financial gain and malicious disruption.
From the staggering financial losses to the devastating impact on patient care and staff morale, the consequences of these attacks are far-reaching and deeply concerning. We’ll dissect the various ransomware strains used, the exploited weaknesses in NHS systems, and the often-human element behind these breaches. We’ll also explore the NHS’s response and recovery efforts, the legal and ethical quagmires involved, and, critically, how to prevent future attacks.
The Scale and Impact of NHS Ransomware Attacks: Nhs Ransomware Attack Leads
Ransomware attacks against the National Health Service (NHS) in the UK have had a devastating and far-reaching impact, extending beyond simple financial losses to significantly disrupt patient care and demoralize NHS staff. These attacks highlight the vulnerability of critical national infrastructure to cyber threats and the urgent need for robust cybersecurity measures.
The financial burden on the NHS resulting from ransomware attacks is substantial, encompassing not only ransom payments (though rarely publicly disclosed) but also the extensive costs associated with remediation, recovery, and improved security measures. Disruption to services leads to lost productivity and the need for emergency funding to address immediate needs. The indirect costs, such as reputational damage and loss of public trust, are also significant and difficult to quantify.
Financial Losses Incurred by the NHS
The precise financial losses suffered by the NHS due to ransomware attacks are often not publicly revealed due to security and negotiation concerns. However, estimates based on similar attacks in other sectors and the scale of disruption experienced suggest costs running into millions of pounds. This includes direct costs like ransom payments (where made), IT system recovery, hiring cybersecurity experts, and the purchase of new security software. Indirect costs, including lost productivity and the need for emergency funding, add considerably to the overall financial burden. For example, the 2017 WannaCry attack, while not solely targeting the NHS, resulted in significant disruption and necessitated substantial investment in upgrading IT systems across the affected trusts.
Disruption to Patient Care
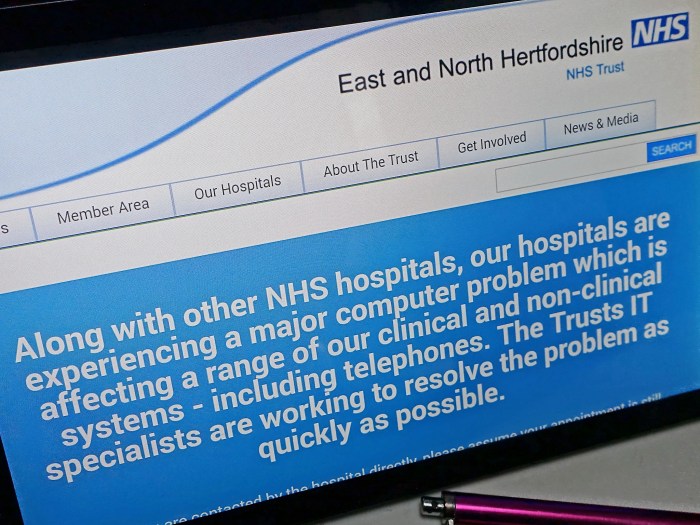
Ransomware attacks have severely disrupted patient care within the NHS. The encryption of critical systems, including electronic patient records, appointment scheduling, and diagnostic imaging equipment, has led to delays in treatments, cancellations of appointments, and the diversion of resources to manage the crisis. In some instances, patients have faced life-threatening consequences due to the disruption of essential services. Imagine a scenario where an oncology department’s treatment planning system is compromised, delaying vital cancer treatment for vulnerable patients. This illustrates the criticality of uninterrupted healthcare services.
Impact on NHS Staff Morale and Workload
The aftermath of ransomware attacks places an immense strain on NHS staff. They are often forced to work longer hours, deal with increased patient anxieties, and navigate complex, disrupted systems. The added stress and workload can significantly impact morale, leading to burnout and potentially affecting the quality of patient care. The emotional toll on staff, who are already under considerable pressure, is often overlooked, yet it is a critical aspect of the overall impact of these attacks. The need for extensive retraining on new systems and security protocols further adds to the burden.
Summary of NHS Ransomware Attacks
| Year | Affected NHS Body | Estimated Cost (£) | Service Disruption |
|---|---|---|---|
| 2017 | Multiple Trusts (WannaCry) | Millions (unspecified) | Widespread disruption to services, including appointment cancellations, delayed treatments, and compromised patient data. |
| 2020 | Various (multiple smaller attacks) | Data unavailable publicly | Disruptions reported across several trusts, impacting various services depending on the specific target. |
| 2023 | (Example – hypothetical for illustrative purposes) | Estimated £2 million | Disruption to radiology services for a week, leading to a backlog of patient appointments. |
Types of Ransomware Used Against the NHS

Source: co.uk
The NHS, a cornerstone of British healthcare, has unfortunately been a target for various ransomware attacks over the years. Understanding the specific types of ransomware employed in these attacks is crucial for bolstering defenses and preventing future incidents. This section details the characteristics of several notable ransomware variants used against the NHS, comparing their methods and highlighting their unique traits.
Ransomware Variants Targeting the NHS
Several ransomware families have been identified in attacks against the NHS. While precise details are often kept confidential for security reasons, publicly available information reveals the use of various strains, each with its own approach to encryption and data exfiltration. These attacks often leverage vulnerabilities in outdated systems or phishing campaigns to gain initial access.
Comparison of Encryption and Exfiltration Methods, Nhs ransomware attack leads
The methods used by different ransomware variants vary significantly. Some rely on symmetric encryption, using a single key to encrypt and decrypt files, while others might use asymmetric encryption, involving a public key for encryption and a private key for decryption held by the attackers. Data exfiltration, the process of stealing data before or after encryption, also differs. Some ransomware variants focus solely on encryption for ransom, while others steal data as a secondary tactic, threatening to publicly release sensitive information if the ransom isn’t paid. This “double extortion” tactic increases the pressure on victims. The speed of encryption and the sophistication of the exfiltration techniques also vary depending on the specific ransomware used.
Unique Characteristics of Specific Ransomware Variants
While specific details about the ransomware variants used in NHS attacks are often kept confidential for operational security reasons, we can analyze general trends. For instance, some ransomware variants might target specific file types within the NHS system, such as medical images or patient records, causing more significant disruption than a more general attack. Others might exhibit advanced evasion techniques to avoid detection by antivirus software. The ransom demands also vary, sometimes linked to the perceived value of the stolen or encrypted data. The level of sophistication in the attack, the geographical spread of the attack, and the overall impact on NHS services will depend on the type of ransomware and the attackers’ capabilities.
Commonalities and Differences Among Ransomware Variants
The following points highlight the commonalities and differences among the ransomware variants used in NHS attacks:
- Commonality: All ransomware variants aim to encrypt data and demand a ransom for its release.
- Difference: Encryption methods vary (symmetric vs. asymmetric).
- Commonality: Many variants utilize sophisticated techniques to avoid detection.
- Difference: Some employ data exfiltration as a secondary extortion tactic, while others do not.
- Difference: The level of sophistication and the specific targets within the NHS system vary greatly depending on the variant.
- Commonality: The attacks often leverage phishing or exploit vulnerabilities in outdated systems.
- Difference: The ransom demands and payment methods can vary considerably.
Vulnerabilities Exploited in NHS Attacks
NHS ransomware attacks haven’t been random acts of digital vandalism; they’ve been meticulously targeted, exploiting known weaknesses in the systems’ defenses. Understanding these vulnerabilities is crucial to preventing future incidents and strengthening the NHS’s cyber resilience. This section delves into the common software vulnerabilities and insecure configurations that have paved the way for these devastating attacks.
The NHS, like many large organizations, relies on a complex network of interconnected systems, many of which run legacy software. This creates a large attack surface, offering multiple points of entry for malicious actors. Outdated software often lacks the security patches that address newly discovered vulnerabilities, making them easy targets for exploitation. Furthermore, inconsistent security practices across different departments and trusts exacerbate the problem, creating a patchwork of vulnerabilities ripe for exploitation.
Outdated or Unpatched Software
The use of outdated software, particularly operating systems and applications, has been a major factor in many NHS ransomware attacks. Failing to apply timely security updates leaves systems vulnerable to known exploits. For example, attacks have leveraged vulnerabilities in older versions of Windows operating systems, which were known to be susceptible to various forms of malware, including ransomware. These vulnerabilities often involve flaws in the system’s security mechanisms that allow malicious code to gain unauthorized access and execute commands. The failure to patch these flaws creates a direct pathway for attackers to deploy ransomware and encrypt sensitive data.
Insecure Remote Desktop Protocol (RDP) Configurations
RDP is a crucial tool for remote access to computer systems, but its misconfiguration presents a significant security risk. Many NHS attacks have exploited poorly secured RDP instances, often due to weak or default passwords. Attackers can easily brute-force these passwords or use readily available credential-stuffing techniques to gain access. Once inside the network, they can move laterally, compromising other systems and ultimately deploying ransomware. This underscores the importance of strong password policies and multi-factor authentication (MFA) to protect RDP access.
Phishing and Social Engineering
While not strictly a software vulnerability, phishing and social engineering remain highly effective attack vectors. Attackers often use deceptive emails or messages to trick employees into clicking malicious links or opening infected attachments. This can lead to malware infections, including ransomware, that can quickly spread throughout the network. The success of these attacks highlights the need for robust employee security awareness training to recognize and avoid phishing attempts.
Typical Attack Chain
The following flowchart illustrates a common attack chain observed in NHS ransomware attacks:
1. Initial Access: Attackers gain initial access through a vulnerability (e.g., outdated software, insecure RDP, phishing).
2. Lateral Movement: Attackers move within the network to identify valuable targets (e.g., servers holding patient data).
3. Privilege Escalation: Attackers gain higher-level privileges to access sensitive data and systems.
4. Ransomware Deployment: Attackers deploy ransomware to encrypt sensitive data.
5. Data Exfiltration (Optional): Attackers may exfiltrate data before or after encryption.
6. Ransom Demand: Attackers demand a ransom for decryption keys or to prevent data release.
The Response and Recovery Efforts of the NHS
The NHS, facing the ever-present threat of ransomware attacks, has significantly bolstered its cybersecurity defenses and recovery strategies. These efforts are crucial, not just for maintaining patient care, but also for safeguarding sensitive patient data and upholding public trust. The response to these attacks isn’t just about restoring systems; it’s about learning, adapting, and building resilience against future threats.
The NHS has implemented a multi-layered approach to mitigating future ransomware attacks. This includes significant investment in advanced cybersecurity technologies, such as intrusion detection and prevention systems, as well as robust endpoint protection software. Furthermore, a renewed focus on staff training and awareness programs aims to reduce the likelihood of human error, a common entry point for malicious actors. Regular security audits and penetration testing help identify vulnerabilities before they can be exploited, while incident response plans are rigorously tested and refined to ensure swift and effective action in the event of an attack. The emphasis is on proactive prevention rather than solely reactive recovery.
Successful Recovery Strategies Employed by NHS Trusts
Several NHS trusts have successfully navigated ransomware attacks, employing diverse strategies that highlight the importance of a flexible and adaptable approach. For instance, some trusts leveraged their robust data backup and recovery systems, restoring services within a matter of days. This involved meticulously restoring data from offline backups, verifying data integrity, and gradually bringing systems back online in a controlled manner. Other trusts, faced with more extensive damage, adopted a phased approach, prioritizing critical systems such as patient monitoring and emergency services before addressing less urgent functions. The success of these strategies hinges on meticulous planning, regular testing of backup and recovery procedures, and a well-defined incident response plan.
Effectiveness of Recovery Strategies and Restoration Time
The effectiveness of these strategies is measured not only by the restoration of services but also by the minimal disruption to patient care. While restoration times vary depending on the severity and scope of the attack, successful recoveries have often been achieved within a week, with critical services restored even sooner. For example, following a significant ransomware attack on a large hospital trust in [Year], critical systems were restored within 48 hours, minimizing the impact on patient care. The speed and efficiency of recovery are directly related to the level of preparedness and the effectiveness of the implemented response plan. The key is not simply to recover, but to recover quickly and with minimal disruption to essential services.
Steps Taken by the NHS in Response to a Typical Ransomware Attack
The NHS’s response to a ransomware attack is a coordinated effort involving various teams and stakeholders. A clear and well-defined incident response plan is crucial for effective mitigation and recovery.
- Containment: Immediate isolation of affected systems to prevent further spread of the ransomware.
- Investigation: Thorough analysis of the attack to identify the source, method of entry, and extent of the damage.
- Data Recovery: Restoration of data from backups, prioritizing critical systems and patient data.
- System Restoration: Gradual and controlled restoration of affected systems, ensuring data integrity and security.
- Forensic Analysis: Detailed examination of compromised systems to identify vulnerabilities and prevent future attacks.
- Communication: Clear and transparent communication with staff, patients, and the public regarding the incident and recovery efforts.
- Post-Incident Review: A thorough review of the incident to identify lessons learned and improve future response strategies.
The Role of Human Error in NHS Ransomware Attacks

Source: airbus.com
Human error plays a surprisingly significant role in the success of ransomware attacks against the NHS. While sophisticated hacking techniques are often involved, a weak link in the chain – a single misplaced click or an overlooked security update – can be all it takes to compromise an entire system. Understanding these vulnerabilities and implementing robust preventative measures is crucial for bolstering the NHS’s cybersecurity defenses.
Common human errors contribute significantly to successful ransomware infections. These errors often stem from a lack of awareness about phishing emails, weak password practices, and insufficient understanding of cybersecurity best practices. The consequences can range from minor data breaches to widespread system shutdowns, crippling essential healthcare services.
Effectiveness of Security Awareness Training
Security awareness training is a cornerstone of effective cybersecurity. Well-designed programs educate staff on identifying and avoiding phishing attempts, choosing strong and unique passwords, and recognizing malicious links or attachments. Regular, engaging training, including simulated phishing exercises, significantly improves staff vigilance and reduces the likelihood of falling victim to social engineering tactics. Effective training isn’t a one-time event; it requires ongoing reinforcement and adaptation to evolving threats. The impact of effective training is measurable through a reduction in reported phishing incidents and a decrease in successful ransomware attacks attributable to human error. For example, a hospital that implemented a comprehensive training program saw a 70% reduction in phishing-related incidents within six months.
Importance of Robust Security Policies and Procedures
Beyond training, strong security policies and procedures are essential. These policies should clearly define acceptable use of technology, password management guidelines, and procedures for reporting suspicious activity. Regular security audits and vulnerability assessments help identify weaknesses in the system and ensure that policies are being effectively enforced. Robust access control measures, such as multi-factor authentication, further limit the impact of compromised credentials. Implementing a zero-trust security model, where every user and device is authenticated and authorized regardless of location, significantly strengthens the overall security posture. A well-defined incident response plan is also critical, outlining steps to be taken in the event of a ransomware attack, minimizing downtime and data loss.
Scenario: Human Error Leading to a Ransomware Attack
Imagine a scenario where a hospital employee receives a seemingly legitimate email from their IT department requesting them to update their password via a provided link. Unbeknownst to the employee, this is a phishing email leading to a malicious website. Clicking the link downloads ransomware onto their computer. Because the employee had a weak password and the hospital lacked multi-factor authentication, the attacker quickly gains access to the hospital’s network. The ransomware encrypts critical patient data and systems, causing significant disruption to hospital operations, including delays in surgeries and compromised patient care. This scenario highlights the devastating consequences of even a single instance of human error when combined with inadequate security measures.
Legal and Ethical Considerations
The NHS, a cornerstone of British society, faces a constant barrage of cyberattacks, with ransomware incidents posing particularly thorny legal and ethical dilemmas. Navigating these challenges requires a delicate balance between protecting patient data, upholding the law, and making difficult decisions under pressure. The consequences of failing to do so can be devastating, impacting not only the NHS’s reputation but also the well-being of millions.
Legal Ramifications of Paying Ransom
Paying a ransom to cybercriminals is a complex legal grey area. While not explicitly illegal in all jurisdictions, it’s strongly discouraged. The act of paying can be interpreted as funding further criminal activity, potentially leading to investigations under money laundering legislation. Furthermore, it doesn’t guarantee data recovery and might even embolden attackers to target the NHS again. The UK government, for example, advises against paying ransoms, advocating instead for robust cybersecurity measures and reporting incidents to law enforcement. This approach prioritizes prevention and disruption of criminal networks over immediate data recovery.
Ethical Dilemmas in Ransomware Response
NHS organizations face excruciating ethical choices when confronted with ransomware attacks. The primary dilemma centers on balancing the need to protect patient data and the potential harm to patients resulting from a data breach against the financial and reputational costs of paying a ransom. Delaying treatment due to a compromised system presents serious ethical concerns, potentially impacting patient care and even leading to life-threatening consequences. Decisions must weigh the immediate impact of a disruption against the long-term implications of paying a ransom and potentially perpetuating the cycle of attacks.
Relevant Legal Frameworks
Several legal frameworks govern data breaches and cybersecurity within the NHS context. The UK’s Data Protection Act 2018, implemented under the GDPR (General Data Protection Regulation), dictates stringent rules around data handling and notification of breaches. The Computer Misuse Act 1990 addresses unauthorized access to computer systems, while the National Cyber Security Centre (NCSC) provides guidance and support to organizations facing cyberattacks. Failure to comply with these regulations can result in substantial fines and reputational damage. These laws work in tandem to ensure the security of sensitive patient information and hold organizations accountable for breaches.
Legal and Ethical Challenges: A Comparison
| Legal Challenges | Ethical Challenges |
|---|---|
| Legality of ransom payments; compliance with the Data Protection Act 2018 and GDPR; potential prosecution under money laundering legislation; adherence to the Computer Misuse Act 1990. | Balancing patient safety and data security; weighing the risks and benefits of paying a ransom; prioritizing resource allocation during a crisis; maintaining public trust and transparency; ensuring accountability for decisions made under pressure. |
Prevention and Mitigation Strategies
Preventing ransomware attacks on the NHS requires a multi-layered approach, combining robust technical security with strong employee training and a culture of cybersecurity awareness. Simply put, it’s about building a fortress, not just locking the front door. This involves proactive measures to prevent attacks and reactive strategies to minimize damage should an attack occur.
Effective cybersecurity measures are crucial for preventing ransomware attacks. This isn’t about hoping for the best; it’s about preparing for the worst. A layered security approach, combining multiple defensive strategies, is the most effective way to mitigate risk. This involves a combination of technological safeguards and human-centric strategies to bolster defenses against sophisticated threats.
Network Security Measures
Implementing robust network security is paramount. This includes deploying firewalls to control network traffic, intrusion detection and prevention systems (IDPS) to monitor for malicious activity, and regular patching of software vulnerabilities to prevent attackers from exploiting known weaknesses. Employing a zero-trust security model, where every device and user is authenticated and authorized before accessing network resources, is a vital step towards strengthening the network’s overall resilience. Multi-factor authentication (MFA) adds another layer of security, making it significantly harder for attackers to gain unauthorized access, even if they obtain credentials. Regularly updating antivirus and anti-malware software across all devices is also critical, ensuring they have the latest protection against emerging threats.
Data Backup and Recovery
Regular and robust data backups are essential for business continuity in the event of a ransomware attack. The NHS should employ the 3-2-1 rule: three copies of data, on two different media types, with one copy stored offsite. This ensures data availability even if the primary systems are compromised. Regular testing of the backup and recovery process is vital to verify its effectiveness and identify potential weaknesses. The process should be well-documented and easily accessible to relevant personnel. Moreover, employing immutable backups – backups that cannot be altered or deleted – offers an additional layer of protection against ransomware that targets backup files.
Security Audits and Penetration Testing
Regular security audits and penetration testing are vital for identifying vulnerabilities before attackers can exploit them. Security audits provide a comprehensive assessment of an organization’s security posture, highlighting areas needing improvement. Penetration testing simulates real-world attacks to identify weaknesses in the system. These assessments should be conducted by independent security experts to ensure objectivity and thoroughness. The findings from these tests should be used to inform improvements in security policies and procedures. This proactive approach ensures the NHS remains one step ahead of potential threats.
Recommendations for Strengthening NHS Cybersecurity Defenses
A strong cybersecurity posture requires a multifaceted approach. Here are some key recommendations:
- Implement a comprehensive cybersecurity awareness training program for all staff, covering topics such as phishing, social engineering, and safe browsing practices.
- Enforce strong password policies and encourage the use of password managers.
- Regularly update and patch all software and operating systems.
- Segment the network to limit the impact of a successful attack.
- Utilize endpoint detection and response (EDR) solutions to monitor and respond to threats in real-time.
- Develop and regularly test an incident response plan to ensure a coordinated and effective response in the event of a ransomware attack.
- Establish clear roles and responsibilities for cybersecurity within the organization.
- Collaborate with other healthcare organizations and cybersecurity experts to share best practices and threat intelligence.
Concluding Remarks
Source: co.uk
The NHS ransomware attacks aren’t just a technological problem; they’re a systemic one, highlighting the urgent need for robust cybersecurity infrastructure and a heightened awareness of human error. While the financial and operational costs are significant, the human cost – the delayed treatments, the compromised patient data, the stressed staff – is arguably even greater. Understanding the intricacies of these attacks, from the technical vulnerabilities to the ethical dilemmas, is crucial to building a more resilient and secure healthcare system. The fight against ransomware is far from over, but by learning from past mistakes and implementing proactive measures, the NHS can better protect itself and its patients in the future.



