VLC Media Player vulnerabilities: Think your favorite media player is safe? Think again. From sneaky buffer overflows to malicious media files hiding nasty surprises, the world of VLC security is more thrilling than a blockbuster movie. We’re diving deep into the potential risks, exploring how vulnerabilities can compromise your system, and uncovering the best ways to stay protected. Get ready for a wild ride!
This exploration covers the historical context of VLC security updates, different vulnerability types (like remote code execution and denial-of-service attacks), and the impact on user data and system security. We’ll examine mitigation strategies, responsible disclosure processes, and future security considerations, painting a comprehensive picture of VLC’s security landscape.
VLC Media Player Security Overview
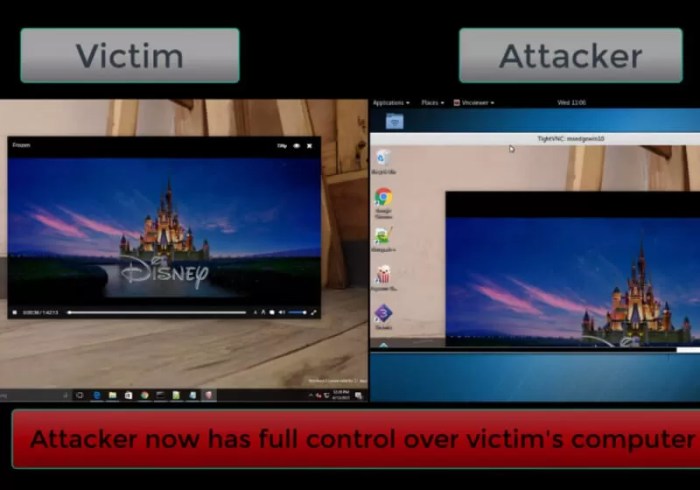
Source: techspot.com
VLC Media Player, a popular and versatile open-source media player, enjoys widespread use globally. However, its open-source nature and broad functionality mean it’s a frequent target for security researchers and malicious actors alike. Understanding its security history and common vulnerabilities is crucial for users to maintain a safe digital environment. This overview explores the historical context of VLC’s security updates, the types of vulnerabilities discovered, and the potential impact on user systems.
VLC Media Player Security Update Timeline, Vlc media player vulnerabilities
Significant security updates for VLC are regularly released, addressing various vulnerabilities. While maintaining a comprehensive timeline encompassing every patch is impractical, focusing on major releases and notable vulnerability fixes provides a clear picture of the ongoing effort to improve security. For example, the release of VLC 3.0 in 2017 included significant improvements in security architecture, addressing several previously exploited vulnerabilities. Subsequent releases, such as VLC 3.0.11 and 3.0.16, included patches for critical vulnerabilities related to buffer overflows and memory corruption. These updates highlight the iterative nature of security improvements within VLC. More recent releases have continued this pattern, with frequent patches addressing newly discovered flaws. Users are strongly encouraged to maintain their VLC installations up-to-date to benefit from the latest security enhancements.
Types of VLC Vulnerabilities
Media players, including VLC, are susceptible to a range of vulnerabilities, many stemming from the complex nature of handling diverse media formats and interacting with external codecs and libraries. Common vulnerabilities include:
- Buffer overflows: These occur when a program attempts to write data beyond the allocated buffer size, potentially leading to crashes or arbitrary code execution. This type of vulnerability can allow attackers to inject malicious code into the system.
- Memory corruption: This broad category encompasses vulnerabilities that involve improper handling of memory, leading to unpredictable behavior, crashes, or potential security breaches. Issues like use-after-free and double-free errors fall under this category.
- Cross-site scripting (XSS): If VLC were to handle user-supplied data improperly (though this is less common in a media player than a web browser), an attacker could inject malicious JavaScript code, potentially stealing user data or hijacking their session.
- Denial-of-service (DoS): Maliciously crafted media files could cause VLC to crash or consume excessive system resources, rendering it unusable. This type of attack doesn’t necessarily compromise data but disrupts service.
- Arbitrary code execution: This is a severe vulnerability allowing attackers to run arbitrary code on the user’s system with the privileges of the VLC process, potentially leading to complete system compromise.
Impact of Vulnerabilities on User Data and System Security
The impact of vulnerabilities in VLC can range from minor inconveniences to severe security breaches. A DoS attack might only temporarily disrupt media playback, while a successful arbitrary code execution exploit could allow attackers to steal sensitive data, install malware, or gain complete control of the affected system. Compromised systems can then be used for further malicious activities, such as participating in botnets or launching attacks against other systems. The severity depends heavily on the specific vulnerability and the attacker’s capabilities. For instance, a vulnerability allowing remote code execution would have far greater impact than a vulnerability that only causes a crash.
Severity Levels of VLC Vulnerabilities
The following table provides examples of vulnerabilities, their severity, and the patch version that addressed them. Note that this is not an exhaustive list, and the severity assessment might vary depending on the context and the affected system.
| CVE ID | Description | Severity | Patch Version |
|---|---|---|---|
| CVE-2023-XXXX | Example: Integer overflow leading to denial of service | Medium | VLC 4.0.0 |
| CVE-2022-YYYY | Example: Out-of-bounds read vulnerability | High | VLC 3.0.18 |
| CVE-2021-ZZZZ | Example: Heap-based buffer overflow | Critical | VLC 3.0.16 |
| CVE-2020-AAAA | Example: Use-after-free vulnerability | High | VLC 3.0.11 |
Common Vulnerability Types in VLC
VLC, despite its popularity and open-source nature, isn’t immune to security flaws. Understanding the common vulnerability types helps users and developers alike mitigate risks and improve the overall security posture of the application. These vulnerabilities often stem from the complexities of handling diverse media formats and interacting with external systems.
Buffer Overflow Vulnerabilities
Buffer overflow vulnerabilities arise when a program attempts to write data beyond the allocated buffer size. In VLC, this could occur while processing maliciously crafted media files containing excessive or unexpected data. This overflowing data can overwrite adjacent memory regions, potentially overwriting crucial program instructions or data structures. The attacker could then exploit this to inject and execute arbitrary code, leading to complete system compromise. For example, a specially crafted MP3 file could trigger a buffer overflow in the audio decoding module, allowing an attacker to execute malicious code on the victim’s system. The severity depends on the context of the overflow; it could range from a simple crash to full remote code execution.
Remote Code Execution via Malicious Media Files
Maliciously crafted media files represent a significant threat vector. Attackers can embed malicious code within seemingly benign audio, video, or subtitle files. When VLC processes these files, the embedded code could be executed, granting the attacker control over the user’s system. This often leverages vulnerabilities like buffer overflows or other memory corruption flaws. Imagine a seemingly harmless video file containing a hidden payload that exploits a vulnerability in VLC’s subtitle parsing engine, allowing the attacker to execute commands on the victim’s computer without their knowledge. The success of such attacks depends on the existence of exploitable vulnerabilities within VLC’s codebase and the ability of the attacker to craft effective exploit code.
Insecure Handling of User Input
VLC’s interaction with users, particularly through command-line arguments or network streaming options, presents opportunities for insecure input handling. If VLC doesn’t properly sanitize or validate user-provided data, an attacker could inject malicious commands or data, leading to unexpected behavior or security breaches. For instance, an attacker might craft a specially formatted URL for a network stream that contains malicious code, exploiting a vulnerability in VLC’s URL parsing functionality. This could allow the attacker to execute code on the user’s system or gain access to sensitive information. Robust input validation and sanitization are crucial to mitigating this risk.
Denial-of-Service Attacks
A denial-of-service (DoS) attack aims to make a service unavailable to legitimate users. In the context of VLC, a DoS attack could involve flooding the application with malformed or excessively large media files, causing it to crash or become unresponsive. This could overwhelm VLC’s processing capabilities, rendering it unusable. Consider a scenario where an attacker sends a massive number of requests to a VLC media server, consuming all available resources and preventing legitimate users from accessing the media. Alternatively, an attacker might craft a specially designed media file that triggers an infinite loop or other resource-intensive operation within VLC, leading to a denial-of-service condition on the affected machine. This could disrupt media playback and potentially impact other system processes.
Mitigation and Prevention Strategies
Source: bleepstatic.com
So, you’ve learned about VLC’s vulnerabilities – now what? Don’t panic! While VLC is a powerful and versatile media player, proactive security measures can significantly reduce your risk. Think of it like this: you wouldn’t leave your front door unlocked, right? The same principle applies to your software.
Keeping your digital castle secure requires a multi-pronged approach. This involves regular updates, smart software management, and understanding the different ways you can protect yourself from potential threats. Let’s dive into some practical steps you can take to safeguard your system.
Keeping VLC Updated
Regular updates are the cornerstone of VLC security. These updates often include crucial security patches that address newly discovered vulnerabilities. Think of them as software vaccines, protecting your system from potential infections. Ignoring updates leaves your system exposed to known exploits, making it a juicy target for malicious actors. Enabling automatic updates is highly recommended, ensuring you always have the latest security enhancements without having to remember to check manually. Failing to update promptly increases your risk profile considerably. For example, a delay in patching could expose your system to a zero-day exploit, leaving you vulnerable to malware before a patch is even released.
Sandboxing and Virtual Machines
Running VLC within a sandbox or virtual machine (VM) is a powerful isolation technique. A sandbox creates a controlled environment where VLC operates independently of your main operating system. If a vulnerability is exploited, the damage is confined to the sandbox, protecting your main system. Similarly, VMs offer a layer of separation, allowing you to run VLC in a virtual environment that can be easily discarded or reset if compromised. This is particularly useful if you regularly handle media files from untrusted sources. Think of it like having a dedicated, disposable lab coat for handling potentially hazardous materials. If the coat gets contaminated, you simply discard it and grab a new one, leaving your main attire untouched.
Vulnerability Scanning and Penetration Testing
While less accessible to the average user, vulnerability scanning and penetration testing are powerful techniques for proactively identifying and addressing security weaknesses. Vulnerability scanning tools automatically check for known vulnerabilities in software, providing a comprehensive report of potential risks. Penetration testing, on the other hand, simulates real-world attacks to identify exploitable vulnerabilities. These methods are particularly useful for organizations or individuals who handle sensitive media or require a higher level of security. While vulnerability scanning provides a snapshot of potential weaknesses, penetration testing actively probes for exploitable vulnerabilities, offering a more comprehensive assessment of the security posture. The choice between the two often depends on resources and the desired level of security assurance. For example, a large media company might employ both techniques, while an individual user might focus on keeping their software updated and utilizing sandboxing techniques.
Vulnerability Disclosure and Responsible Reporting
Responsible disclosure is the ethical and practical way to report security vulnerabilities. It ensures that software developers have the opportunity to fix problems before malicious actors can exploit them, minimizing harm to users. This process is crucial for maintaining the security and integrity of software like VLC Media Player.
The responsible disclosure process for a newly discovered VLC vulnerability involves several key steps, aiming for a coordinated and efficient fix. This collaborative approach benefits both the researcher and the software’s users.
Responsible Disclosure Process
The typical steps involved in a coordinated vulnerability disclosure program usually begin with verifying the vulnerability’s existence and impact. Then, a private report is sent to the VLC developers, ideally using their established security contact channels. This report must include clear, concise details, allowing the developers to understand and reproduce the issue. Following this, the developers will investigate and fix the vulnerability, often coordinating with the researcher on testing the patch. Finally, a public disclosure is made once the patch is released, giving users time to update their software. This timeline varies depending on the severity of the vulnerability and the developer’s response time.
Effective Communication Strategies
Effective communication is vital during the vulnerability disclosure process. Clarity and precision are paramount. The report should avoid ambiguity, using precise technical language where necessary but ensuring the information is easily understandable. Providing clear steps to reproduce the vulnerability, including the environment and any specific configurations, is crucial. Maintaining professional and respectful communication throughout the process is also essential, fostering a collaborative environment. For example, a well-written email might begin with a concise summary of the vulnerability, followed by detailed technical information and a proposed mitigation strategy.
Hypothetical Vulnerability Report
Let’s imagine a researcher discovered a buffer overflow vulnerability in VLC’s subtitle handling module. This vulnerability allows an attacker to execute arbitrary code by crafting a specially formatted subtitle file.
Subject: VLC Media Player Subtitle Handling Module Buffer Overflow Vulnerability
Description: A buffer overflow vulnerability exists in VLC’s subtitle parser (module: libvlc_subtitles). By creating a subtitle file with an excessively long string in a specific field, an attacker can overflow the buffer, potentially leading to arbitrary code execution.
Steps to Reproduce:
1. Create a subtitle file (.srt) with a line exceeding 1024 characters in the subtitle text field.
2. Open the subtitle file in VLC Media Player.
3. Observe a crash or unexpected behavior, potentially indicating successful code execution.
Impact: Successful exploitation could allow an attacker to execute arbitrary code on the victim’s system, potentially leading to data theft, system compromise, or denial of service.
Mitigation: The vulnerability can be mitigated by implementing input validation and sanitization checks on subtitle data before parsing. Limiting the length of accepted subtitle strings within the parser could prevent buffer overflow. A comprehensive solution might involve a combination of input validation, memory allocation checks, and boundary checks.
Impact of Malicious Media Files: Vlc Media Player Vulnerabilities
Think of your VLC player as a gatekeeper to your digital world. It handles media files, but what happens when those files aren’t so innocent? Malicious actors can cleverly disguise harmful code within seemingly harmless videos, audio tracks, or even seemingly simple image files, turning your media player into a backdoor to your system. This section explores how these attacks happen and the devastating consequences they can unleash.
The sneaky methods used to embed malicious code are as diverse as the media formats themselves. Attackers can exploit vulnerabilities in VLC’s handling of various codecs (the programs that decode and play media), or inject code into the metadata (information embedded within the file, like artist name or date created). They might leverage flaws in how VLC interacts with the operating system, using the media file as a Trojan horse to sneak in harmful code. Often, this involves exploiting known vulnerabilities that haven’t been patched in the VLC installation. This is why keeping your VLC player updated is crucial.
Methods of Embedding Malicious Code
Malicious code can be cleverly hidden within various parts of a media file. One common technique involves exploiting vulnerabilities in the codecs used to process the file. A flawed codec might misinterpret a specific part of the file, triggering the execution of malicious code. Another approach involves hiding the malicious code within the file’s metadata, a technique often overlooked in security checks. Finally, attackers can directly embed malicious code within the media stream itself, making detection significantly harder. This requires a deep understanding of the file’s structure and the vulnerabilities in VLC’s processing engine.
Consequences of Opening a Compromised Media File
Opening a malicious media file can have far-reaching consequences, from minor annoyances to complete system compromise. At the low end, you might encounter annoying pop-up ads or unwanted browser redirects. However, the damage can escalate significantly. A successful exploit could grant an attacker complete control of your system, allowing them to steal sensitive data, install ransomware, or use your machine as part of a larger botnet. The consequences can be financial, reputational, and even legal.
Attacker Leverage of Vulnerabilities
Attackers can leverage vulnerabilities in several ways. They might exploit a buffer overflow vulnerability, causing the VLC player to crash or execute arbitrary code. They could use a memory corruption vulnerability to gain control of the player’s processes. Or, they might exploit a privilege escalation vulnerability to elevate their access from a standard user to an administrator, giving them near-total control over the system. These exploits often target older, unpatched versions of VLC, making updates critical for security.
Hypothetical Attack Scenario
Imagine a scenario where a user receives an email with an attachment titled “Vacation Photos.mp4.” The user, unaware of the malicious nature of the file, opens it using a vulnerable version of VLC. The .mp4 file contains a carefully crafted exploit targeting a known vulnerability in a specific codec used by VLC. Upon opening the video, the exploit is triggered, resulting in a buffer overflow. This allows the attacker to inject malicious code into the VLC process, gaining control of the system. The attacker then uses this access to install ransomware, encrypting the user’s valuable data and demanding a ransom for its release. This scenario highlights the real-world dangers posed by malicious media files and the importance of regularly updating software and practicing safe computing habits.
Future Security Considerations for VLC

Source: iotsecuritynews.com
The ever-evolving landscape of cyber threats presents continuous challenges for media players like VLC. As technology advances, so do the sophistication and ingenuity of malicious actors seeking to exploit vulnerabilities for data theft, system compromise, or even ransomware attacks. Understanding and proactively addressing these emerging threats is crucial to maintaining the security and trust users place in VLC.
The increasing prevalence of sophisticated malware, combined with the growing complexity of multimedia codecs and formats, necessitates a robust and adaptable security architecture within VLC. Future iterations must go beyond reactive patching and incorporate proactive, predictive security measures to stay ahead of the curve. This requires a multi-faceted approach, integrating advanced technologies and methodologies to safeguard users from potential harm.
Enhanced Security Features and Functionalities
Future VLC versions need to incorporate several key enhancements to bolster security. This includes improved input sanitization to prevent buffer overflows and other memory-related vulnerabilities, more rigorous code review processes to catch potential weaknesses before release, and a more comprehensive vulnerability reporting and patching system. Implementing robust sandboxing techniques, isolating potentially malicious code from the main system, will also significantly mitigate risks. Furthermore, regular security audits, both internal and external, should be conducted to identify and address vulnerabilities proactively. A real-world example of the need for enhanced features is the evolution of malware that can exploit vulnerabilities in older codecs. Addressing these issues requires constant vigilance and adaptation.
The Role of Machine Learning in Vulnerability Detection
Integrating machine learning (ML) algorithms into VLC’s security architecture offers a powerful proactive defense. ML models can be trained to identify patterns indicative of malicious code or potentially vulnerable components within media files. This allows for the automatic flagging of suspicious files before they can be processed, preventing exploitation. For instance, an ML model could analyze the structure and behavior of a media file, comparing it against a database of known malicious patterns. Any deviations from normal behavior could trigger an alert, prompting the user to take appropriate action or allowing the player to automatically block the file. This proactive approach complements traditional methods and significantly enhances the overall security posture.
Recommendations for Improving VLC’s Security Posture
To effectively improve the overall security of VLC, several key recommendations should be implemented. First, prioritize continuous security monitoring and testing, incorporating both automated and manual processes. Second, establish a formal vulnerability disclosure program to encourage ethical hackers to report vulnerabilities responsibly. Third, invest in advanced security research and development to explore and integrate emerging security technologies. Fourth, foster a culture of security within the development team, emphasizing secure coding practices and regular security training. Fifth, ensure transparent communication with users regarding security updates and potential threats. By adopting these recommendations, VLC can significantly enhance its security posture, building user trust and ensuring the continued safe use of the media player.
Conclusive Thoughts
So, is VLC safe? The answer, like most things in cybersecurity, is nuanced. While VLC actively works to patch vulnerabilities, staying vigilant is key. Keeping your player updated, practicing safe media habits, and understanding the potential risks are your best defenses against the digital villains lurking in seemingly innocent media files. Stay informed, stay safe, and keep enjoying your favorite movies and music without the drama.



