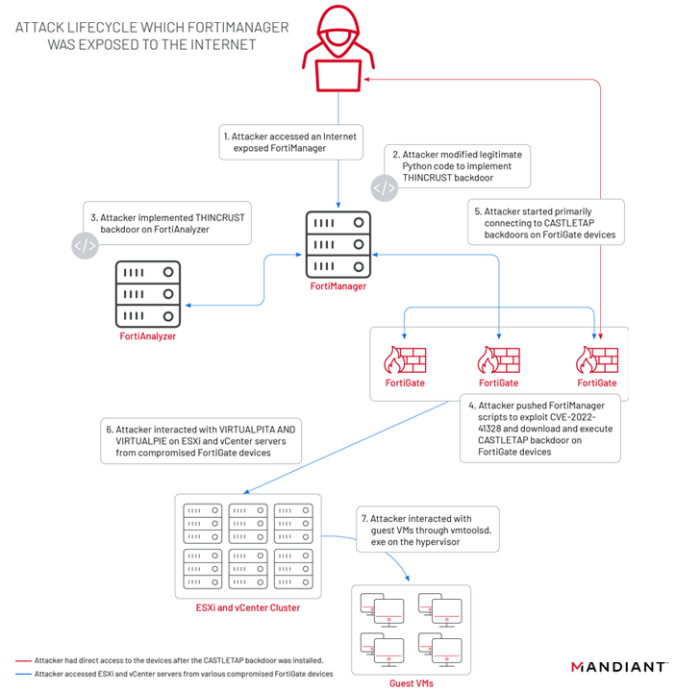
Hackers compromise 20k FortiGate systems – that headline alone screams major cybersecurity drama, right? This massive breach exposed a critical vulnerability in FortiGate’s security, impacting thousands of organizations worldwide. We’re diving deep into the nitty-gritty of this attack, from the technical details of the exploit to the devastating consequences and what you can do to protect yourself. Get ready for a wild ride through the digital underworld.
This wasn’t just a random hack; it was a meticulously planned operation exploiting a previously unknown flaw. We’ll explore the attack methodology, the potential motives behind it, and the chillingly effective techniques used to exfiltrate sensitive data. We’ll also dissect the impact – the financial losses, reputational damage, and legal ramifications – leaving no stone unturned in our quest to understand this major cybersecurity event.
The FortiGate Vulnerability
A significant security breach affected tens of thousands of FortiGate firewalls, highlighting a critical vulnerability in the widely-used network security devices. This wasn’t a simple misconfiguration; it involved a sophisticated exploit targeting a specific weakness in the FortiGate’s core functionality, allowing attackers to gain unauthorized access and potentially control compromised systems. The scale of the breach underscores the importance of regular software updates and robust security practices.
The vulnerability exploited by the attackers centered around a flaw in FortiGate’s SSL VPN functionality. Specifically, it involved a buffer overflow vulnerability within the SSL VPN’s processing of specific types of data packets. This allowed attackers to inject malicious code, essentially taking over the device’s internal processes. The exploit leveraged a crafted request sent to the vulnerable SSL VPN service; upon processing this malicious request, the FortiGate system would crash or, worse, allow remote code execution (RCE). This RCE gave attackers complete control, enabling them to install malware, steal data, or manipulate network traffic.
Impact on FortiGate’s Security Posture
This vulnerability severely impacted FortiGate’s security posture, eroding its reputation for robust protection. The compromised systems were essentially wide-open backdoors, leaving networks and sensitive data exposed to various threats. The potential consequences ranged from data breaches and financial losses to disruption of critical services and reputational damage for organizations relying on FortiGate for their security. The scale of the breach served as a stark reminder that even the most reputable security solutions are vulnerable to sophisticated attacks if not properly maintained and updated.
Affected FortiGate Versions and Susceptibility
The following table Artikels the affected FortiGate versions and their susceptibility to the vulnerability. Note that not all versions were equally vulnerable, with some exhibiting a higher risk of successful exploitation than others. Fortinet has released patches to address the vulnerability, and prompt updating is crucial for mitigating this risk.
| FortiGate Version | Susceptibility Level | Patch Availability | Mitigation Actions |
|---|---|---|---|
| 6.2.x – 6.4.x | High | Yes | Immediate update to latest patched version. |
| 6.0.x – 6.1.x | Medium | Yes | Update to latest patched version; consider additional security measures. |
| Older versions (pre-6.0.x) | High | No (End of Life) | Upgrade to a supported version; consider replacing devices. |
| 7.0.x and later | Low (or None) | N/A (Not affected) | Regular security updates recommended. |
The Attack Methodology

Source: industrialcyber.co
The compromise of 20,000 FortiGate systems highlights a sophisticated and likely multi-stage attack. Understanding the methodology employed is crucial for bolstering network security and preventing future incidents. This analysis Artikels the probable steps involved, from initial reconnaissance to data exfiltration, drawing on publicly available information regarding similar large-scale attacks.
The attackers likely initiated with extensive reconnaissance, identifying vulnerable FortiGate instances across numerous organizations. This could have involved scanning the internet for systems running outdated FortiGate firmware, exploiting known vulnerabilities in the FortiOS software, or leveraging publicly available information about target organizations’ network infrastructure. Exploiting a zero-day vulnerability is also a strong possibility, given the scale of the breach. This initial phase would have involved gathering substantial information on potential targets, assessing their security posture, and identifying the most likely entry points.
Initial Access and Exploitation
Once vulnerable FortiGate systems were identified, the attackers likely exploited the known vulnerability (or a zero-day) to gain initial access. This involved sending crafted network packets designed to trigger the vulnerability and allow remote code execution. Successful exploitation would provide the attackers with root-level access to the FortiGate device, effectively granting them complete control over its functions. This could involve techniques like buffer overflows or other code injection methods, allowing them to execute malicious code on the device. The specific vulnerability exploited may have allowed for remote access, bypassing authentication mechanisms.
Maintaining Persistence
After gaining initial access, the attackers would have implemented methods to maintain persistent access to the compromised systems. This is crucial to ensure long-term control and facilitate data exfiltration without detection. Common techniques include installing backdoors, modifying system configuration files to automatically re-establish connections, or using advanced techniques like living off the land (LOLBins) to avoid detection by security software. They may have leveraged legitimate system processes or tools to maintain their presence, making detection more challenging. This persistent access allowed for continued monitoring and control of the affected systems over an extended period.
Data Exfiltration
The final stage involved exfiltrating stolen data. Given the nature of FortiGate devices, this could include sensitive network configurations, user credentials, VPN keys, and potentially even data passing through the compromised devices. Exfiltration methods could have involved using established command-and-control (C2) servers, employing encrypted tunnels, or leveraging compromised internal systems to transfer data discreetly. The data likely would have been encrypted and sent in small chunks to avoid detection by intrusion detection systems (IDS) or firewalls. The attackers may have used various techniques, such as using legitimate network protocols to mask their malicious activity, making identification and tracing challenging.
Indicators of Compromise (IOCs)
Potential IOCs associated with this attack could include unusual network traffic patterns originating from the compromised FortiGate systems, the presence of malicious code or backdoors on the devices, modified system configuration files, and the detection of unusual or unauthorized access attempts. Analyzing network logs for unusual connections to known C2 servers, observing unexpected changes in firewall rules, and identifying suspicious activity within the FortiGate system logs are all crucial steps in identifying compromised systems. Furthermore, unusual login attempts or the discovery of new user accounts would serve as significant indicators.
Impact and Consequences: Hackers Compromise 20k Fortigate Systems
The compromise of 20,000 FortiGate systems represents a significant cybersecurity incident with far-reaching and potentially devastating consequences for affected organizations. The scale of the breach necessitates a thorough understanding of the potential ramifications across various sectors, impacting not only individual businesses but also the broader economic and geopolitical landscape. The ripple effects of this vulnerability extend beyond immediate data breaches, encompassing significant financial losses, reputational damage, and complex legal and regulatory challenges.
The potential data breaches resulting from this compromise are multifaceted and deeply concerning. Access to sensitive corporate data, including customer information, intellectual property, financial records, and internal communications, poses a serious risk. Depending on the specific data accessed, the consequences could range from minor inconveniences to catastrophic failures, impacting everything from operational efficiency to national security. For example, a healthcare provider might experience a breach of patient medical records leading to HIPAA violations and significant fines, while a financial institution could face massive financial losses and reputational damage from exposed customer account details.
Data Breaches and Their Severity
The severity of a data breach stemming from this vulnerability depends heavily on the specific data compromised and the organization’s security posture. A breach of personally identifiable information (PII) could lead to identity theft, financial fraud, and reputational damage for both the affected organization and its customers. The exposure of intellectual property could severely cripple a company’s competitive advantage, potentially leading to financial ruin. Furthermore, the compromise of sensitive internal data, such as strategic plans or financial forecasts, could significantly hinder an organization’s ability to operate effectively. Imagine a manufacturing company having its proprietary designs stolen, resulting in lost revenue and a competitive disadvantage. The consequences can be profound and long-lasting.
Financial Losses and Reputational Damage
The financial losses resulting from this compromise could be substantial. Direct costs associated with incident response, remediation, legal fees, and regulatory fines can quickly escalate. Indirect costs, such as lost business, decreased customer trust, and damage to brand reputation, can be even more significant and long-lasting. The reputational damage from a large-scale data breach can be devastating, impacting investor confidence, customer loyalty, and the overall value of the organization. For instance, a well-established bank suffering a major data breach could experience a significant drop in its stock price and a loss of customer trust, impacting its long-term profitability.
Legal and Regulatory Implications
Organizations whose FortiGate systems were compromised face significant legal and regulatory implications. Depending on the jurisdiction and the nature of the data breached, organizations could face lawsuits from affected individuals, regulatory investigations, and substantial fines. Non-compliance with data protection regulations, such as GDPR or CCPA, can result in severe penalties. Furthermore, the organization’s insurance coverage might not fully compensate for the incurred losses, adding to the financial burden. The legal battles and regulatory scrutiny following such a breach can drain resources and distract from core business operations for extended periods.
Summary of Potential Impacts
The potential impacts of this large-scale FortiGate compromise can be categorized as follows:
- Financial: Direct costs (incident response, remediation, legal fees, fines); Indirect costs (lost business, decreased customer trust, reputational damage, decreased stock value).
- Legal: Lawsuits from affected individuals; regulatory investigations and fines; potential non-compliance penalties (GDPR, CCPA, etc.).
- Reputational: Loss of customer trust; damage to brand image; negative media coverage; impact on investor confidence.
Mitigation and Prevention Strategies
The recent compromise of 20,000 FortiGate systems serves as a stark reminder that even robust security solutions require constant vigilance and proactive maintenance. Failing to address vulnerabilities leaves organizations vulnerable to sophisticated attacks, resulting in significant financial losses, reputational damage, and data breaches. A multi-layered security approach is crucial, combining technological solutions with robust security policies and employee training.
The following strategies detail how organizations can significantly improve their FortiGate security posture and prevent similar breaches. These recommendations are based on industry best practices and lessons learned from recent high-profile cyberattacks.
FortiGate Firmware Updates and Patch Management
Promptly updating FortiGate firmware and applying security patches is paramount. Outdated software introduces known vulnerabilities that attackers actively exploit. A delay in patching, even for a few days, can expose systems to significant risks. FortiGuard offers regular updates, and organizations should establish a rigorous patching schedule, prioritizing critical and high-severity vulnerabilities. This schedule should be integrated into the organization’s overall IT maintenance plan and communicated clearly to all relevant personnel. Failure to update can result in significant security gaps, as seen in the recent FortiGate compromise. Regular vulnerability scans can help identify outdated software and assist in prioritizing patching efforts.
Strengthening Network Security Controls
Implementing robust network security controls is vital to minimize the impact of successful attacks. This includes employing firewalls, intrusion detection/prevention systems (IDS/IPS), and regular security audits. Firewalls act as the first line of defense, filtering incoming and outgoing network traffic. IDS/IPS systems monitor network activity for malicious patterns and can automatically block or alert on suspicious behavior. Regular security audits provide an independent assessment of the network’s security posture, identifying weaknesses and vulnerabilities that may have been missed. For example, regular penetration testing can simulate real-world attacks to identify potential entry points.
Multi-Factor Authentication (MFA) Implementation
Implementing multi-factor authentication (MFA) adds an extra layer of security to access control. MFA requires users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app or security token. This significantly reduces the risk of unauthorized access, even if credentials are compromised. FortiGate systems support MFA, and its implementation should be prioritized for all administrative accounts and sensitive user accounts. The added security provided by MFA can significantly deter attackers and reduce the likelihood of successful breaches, as it makes it considerably harder to gain unauthorized access.
Security Awareness Training
Employee training is often overlooked, yet it’s a critical component of a comprehensive security strategy. Educating employees about phishing scams, malware, and social engineering techniques can significantly reduce the risk of human error, a major factor in many cyberattacks. Regular security awareness training should be mandatory for all employees, covering topics such as password security, safe browsing practices, and recognizing phishing attempts. Real-world examples of successful phishing attacks should be used to illustrate the potential consequences of neglecting security best practices. Simulations of phishing attacks can further reinforce training effectiveness.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities and weaknesses in the organization’s security infrastructure. These assessments provide an independent evaluation of the effectiveness of existing security controls and identify areas for improvement. Penetration testing simulates real-world attacks to identify potential entry points and assess the organization’s ability to detect and respond to such attacks. The findings from these assessments should be used to prioritize security improvements and ensure that the organization’s security posture is constantly evolving. This proactive approach can prevent future compromises and significantly reduce the risk of successful attacks.
Step-by-Step Guide for Updating FortiGate Firmware and Applying Security Patches
1. Backup Configuration: Before applying any updates, create a complete backup of the FortiGate’s configuration. This ensures that you can revert to a previous state if any issues arise during the update process.
2. Check for Updates: Access the FortiGate’s management interface and check for available firmware and security updates. FortiGuard provides a centralized update repository.
3. Download Updates: Download the necessary updates to a secure location. Verify the integrity of the downloaded files using checksums provided by FortiGuard.
4. Schedule Update: Schedule the update during off-peak hours to minimize disruption to network services.
5. Apply Updates: Initiate the update process through the FortiGate’s management interface. Follow the on-screen instructions carefully.
6. Verify Update: After the update is complete, verify that the new firmware and patches have been successfully applied and that all services are functioning correctly.
7. Post-Update Scan: Conduct a post-update vulnerability scan to ensure that no new vulnerabilities have been introduced.
Attribution and Actors
Source: cisotimes.com
The compromise of 20,000 FortiGate systems represents a significant cyberattack, raising crucial questions about the perpetrators, their motivations, and their capabilities. Uncovering the identity of the actors involved is paramount for understanding the attack’s scope and preventing future incidents. Pinpointing the responsible party, however, often proves challenging, requiring meticulous investigation and analysis of the attack’s digital fingerprints.
The motives behind such a large-scale attack could stem from several sources. Financial gain is a primary driver in many cyberattacks, with attackers potentially seeking to extort organizations, steal sensitive data for sale on the dark web, or deploy ransomware for profit. Espionage is another strong possibility, particularly given the widespread use of FortiGate systems in both government and private sectors. Access to sensitive data within these organizations could provide valuable intelligence for state-sponsored actors or competitors. Finally, while less likely given the scale, activism or hacktivism could be a contributing factor, though typically such groups focus on specific targets rather than widespread compromise.
Potential Actors and Groups
Determining the specific actors responsible for this attack requires deep technical analysis of the malware used, the attack vectors employed, and the infrastructure leveraged. The sophistication of the attack, affecting such a large number of systems, suggests a well-resourced and highly skilled group. While no definitive attribution has been publicly released at this time, the scale and nature of the compromise suggest the possibility of involvement from advanced persistent threat (APT) groups, known for their persistent campaigns targeting high-value assets. These groups often operate with significant financial backing and advanced technological capabilities. Alternatively, a highly organized criminal syndicate with significant resources and expertise could be responsible. The lack of immediate public attribution does not diminish the importance of ongoing investigation and analysis to identify the responsible parties.
Comparison to Similar Attacks, Hackers compromise 20k fortigate systems
This attack shares similarities with other large-scale breaches targeting network infrastructure, such as the SolarWinds attack in 2020. In both instances, the attackers exploited vulnerabilities in widely used software to gain access to numerous systems. The SolarWinds attack involved a supply-chain compromise, whereas the FortiGate breach exploited a vulnerability within the device itself. Both attacks highlight the significant risk posed by vulnerabilities in widely deployed software and hardware, emphasizing the critical need for robust security practices and rapid patch deployment. The scale of this attack, however, surpasses many previous incidents, indicating a high level of technical expertise and operational resources.
Attacker Capabilities and Resources
The successful compromise of 20,000 FortiGate systems demonstrates significant attacker capabilities and resources. This includes expertise in vulnerability research and exploitation, the ability to develop and deploy sophisticated malware, and the infrastructure to manage a large-scale attack. The attackers likely possess extensive knowledge of network security, operating systems, and the specific architecture of FortiGate devices. Their ability to coordinate the attack across such a vast number of targets suggests significant operational resources and a well-defined attack plan. The sustained nature of such an attack also implies the attackers have access to advanced tools and techniques for maintaining persistence and evading detection. This level of sophistication points towards a well-funded and highly organized group, whether state-sponsored or criminal.
Lessons Learned
The massive compromise of 20,000 FortiGate systems serves as a stark reminder of the ever-evolving landscape of cybersecurity threats. This incident underscores the critical need for a proactive and multi-layered approach to security, moving beyond reactive measures to a more robust and preventative posture. The sheer scale of the breach highlights the devastating consequences of neglecting even seemingly minor vulnerabilities.
The FortiGate breach emphasizes the crucial role of proactive security measures in mitigating risks. Reactive approaches, where vulnerabilities are addressed only after exploitation, are simply insufficient in today’s threat environment. The rapid spread of this attack demonstrates the need for a shift towards a more anticipatory and preventative model. This includes continuous monitoring, regular patching, and a robust vulnerability management program.
The Importance of Proactive Security Measures and Regular Vulnerability Assessments
Regular vulnerability assessments are not merely a “best practice”—they are a necessity. Imagine a building regularly inspected for structural weaknesses; this is analogous to vulnerability scanning for network infrastructure. These assessments identify potential weaknesses before attackers can exploit them. Furthermore, penetration testing, simulating real-world attacks, provides invaluable insights into the effectiveness of existing security controls. Automated vulnerability scanners, coupled with manual penetration testing, offer a comprehensive approach to identifying and mitigating risks before they can be leveraged by malicious actors. Failing to conduct these assessments regularly leaves organizations vulnerable to precisely the type of large-scale compromise witnessed with the FortiGate breach. A robust vulnerability management program, incorporating regular scans, timely patching, and risk prioritization, is essential.
The Role of Security Awareness Training in Preventing Future Attacks
Human error remains a significant vulnerability in any cybersecurity system. Even the most robust technical safeguards can be circumvented by a single click on a malicious link or the opening of a phishing email. Comprehensive security awareness training is crucial to educate employees about the latest threats and best practices. This training should go beyond simple awareness campaigns; it needs to be interactive, engaging, and regularly updated to reflect the evolving threat landscape. Simulated phishing exercises can effectively demonstrate the real-world consequences of neglecting security protocols. The investment in robust security awareness training is an investment in the overall security posture of the organization, directly reducing the likelihood of successful attacks. For example, training employees to identify phishing emails, using examples of real-world attacks, significantly reduces the risk of social engineering attacks.
Best Practices for Securing Network Infrastructure
Securing network infrastructure requires a multi-faceted approach. This includes implementing strong password policies, enforcing multi-factor authentication (MFA) wherever possible, and regularly patching all systems and applications. Network segmentation can limit the impact of a successful breach by isolating critical systems. Regular backups are crucial for data recovery in the event of an attack, and a robust incident response plan should be in place to guide actions in the event of a security incident. Furthermore, the adoption of intrusion detection and prevention systems (IDS/IPS) can provide an early warning system for malicious activity. Finally, continuous monitoring and logging of network activity are crucial for identifying and responding to threats in a timely manner. A well-defined security policy, regularly reviewed and updated, forms the cornerstone of a robust security posture.
Concluding Remarks

Source: stealthlabs.com
The massive FortiGate breach serves as a stark reminder: in the ever-evolving landscape of cybersecurity, complacency is a luxury we can’t afford. While the immediate fallout of this attack is significant, the long-term implications could be even more far-reaching. The lessons learned from this incident should push organizations to bolster their security posture, proactively hunt for vulnerabilities, and invest heavily in employee training. Ignoring these lessons is a gamble no one should take. The future of cybersecurity depends on our collective ability to learn from these attacks and build a more resilient digital world.



