POC Exploit Released 2: The sequel’s out, and it’s not a happy ending for everyone. Think of it like this: the first release was a sneak peek at a vulnerability; this second drop is the full-blown invasion. We’re diving deep into the world of proof-of-concept exploits, exploring why they’re released, how they work, and the devastating ripple effect they can have across systems and organizations. Get ready for a technical deep dive, spiced with real-world examples and a healthy dose of ethical dilemmas.
This isn’t just a technical breakdown; it’s a story of cat-and-mouse between security researchers, software developers, and the bad actors looking to exploit weaknesses. We’ll unpack the technical intricacies of these exploits, the motivations behind their release, and the crucial role of vulnerability disclosure policies in shaping the narrative. Prepare for a rollercoaster ride through the dark side of the digital world.
Understanding the “POC Exploit Released 2” Phenomenon
Source: howtofix.guide
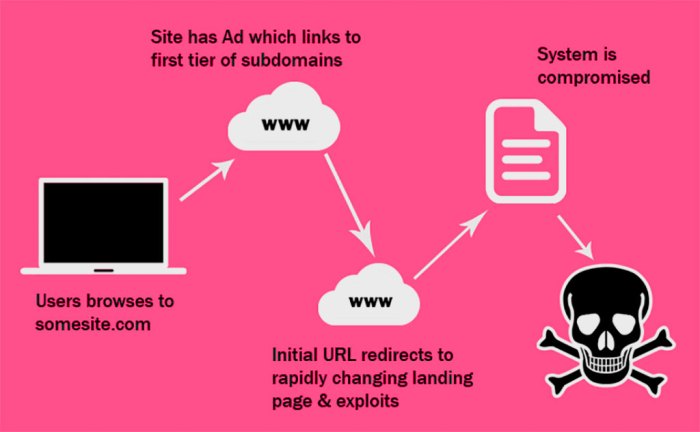
The release of a second proof-of-concept (POC) exploit for a vulnerability, often dubbed “POC Exploit Released 2,” signifies a concerning escalation in the threat landscape. It suggests that the initial disclosure, while potentially prompting remediation efforts, hasn’t fully addressed the underlying weakness, or that the vulnerability is more pervasive or impactful than initially understood. This phenomenon highlights the complex interplay between security researchers, software vendors, and attackers, and underscores the ongoing challenge of securing software in a dynamic environment.
The typical lifecycle of a POC exploit begins with a security researcher discovering a vulnerability. This researcher might then choose to responsibly disclose the vulnerability to the affected vendor, giving them time to patch the flaw before public release. However, if the vendor is unresponsive, or if the researcher believes the vulnerability is too critical to wait, they might release a POC exploit, demonstrating how the vulnerability can be exploited. This public release can then trigger a race: vendors scrambling to patch, attackers attempting to exploit the vulnerability at scale, and other researchers delving into the exploit to potentially discover further vulnerabilities. A “POC Exploit Released 2” often emerges because the initial patch was incomplete, a new attack vector was discovered, or because the initial POC was insufficiently detailed or easily understood.
Motivations Behind Public POC Exploit Releases
The decision to publicly release a POC exploit is rarely taken lightly. Common motivations include pressuring vendors to act swiftly, raising public awareness of critical vulnerabilities, and preventing further exploitation by malicious actors who might have already gained access to the vulnerability details. In some cases, researchers might aim to showcase their skills or highlight systemic weaknesses in software development practices. The release of a second POC could stem from the same motivations, but with a heightened sense of urgency given the perceived inadequacy of the initial response. For instance, if a vendor’s initial patch proved ineffective, a second POC release might serve as a strong call to action, emphasizing the severity and persistence of the threat.
Consequences of a Second POC Release
The consequences of a second POC release are generally more severe than the first. The initial release often leads to some level of mitigation, as vendors and users become aware of the vulnerability. However, a second release suggests that this mitigation was insufficient. This could lead to a wider range of affected systems, an increased likelihood of successful attacks, and a potentially greater impact on individuals and organizations. The window of opportunity for malicious actors widens, potentially allowing more sophisticated and targeted attacks. Consider the case of a widely used web server software: a first POC might have focused on a specific configuration, but a second POC might reveal an exploit applicable to all versions, dramatically increasing the potential damage.
The Role of Vulnerability Disclosure Policies
Well-defined vulnerability disclosure policies play a crucial role in mitigating the risks associated with POC releases. These policies establish clear communication channels between researchers and vendors, outlining the preferred methods for disclosing vulnerabilities and the timelines for remediation. Robust policies can encourage responsible disclosure, minimizing the need for public releases and reducing the likelihood of a second POC becoming necessary. However, inconsistent or inadequate policies can exacerbate the problem, leading to delays in patching, increased exposure, and ultimately, the release of multiple POC exploits as researchers lose confidence in the vendor’s responsiveness. A strong vulnerability disclosure policy should ideally Artikel clear timelines, communication protocols, and a process for acknowledging and crediting researchers for their contributions.
Technical Aspects of the Exploit
Source: anitian.com
Understanding the technical intricacies of a “POC Exploit Released 2” requires delving into the vulnerabilities exploited, the methods employed, and the overall architecture. These second-generation exploits often build upon initial findings, enhancing their effectiveness and circumventing initial defenses. Let’s dissect the key elements.
Common Vulnerabilities Targeted
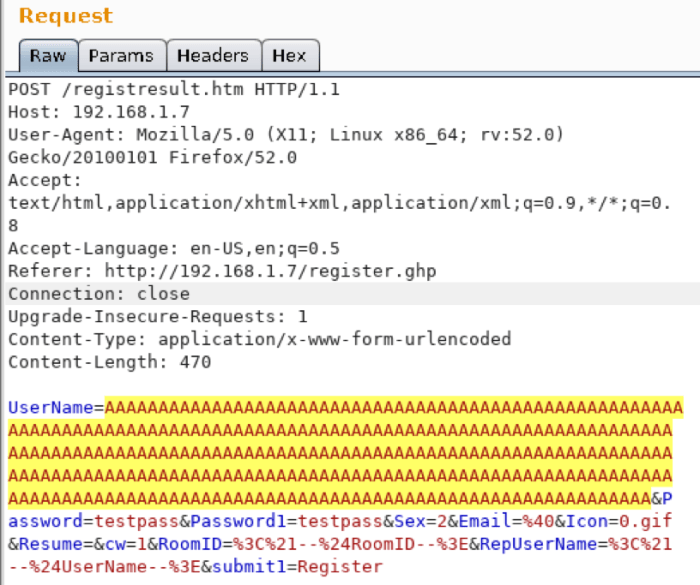
The following table Artikels common vulnerability types targeted by these sophisticated exploits, along with their associated software, exploitation methods, and mitigation strategies. Understanding these vulnerabilities is crucial for effective defense.
| Vulnerability Type | Affected Software | Exploit Method | Mitigation Strategy |
|---|---|---|---|
| SQL Injection | Various Database Systems (MySQL, PostgreSQL, etc.) | Maliciously crafted SQL queries to manipulate database actions. | Input validation, parameterized queries, least privilege access. |
| Cross-Site Scripting (XSS) | Web Applications | Injection of malicious scripts into web pages viewed by other users. | Output encoding, Content Security Policy (CSP), input validation. |
| Remote Code Execution (RCE) | Server-side applications | Executing arbitrary code on the target server. | Secure coding practices, regular patching, least privilege access. |
| Buffer Overflow | C/C++ applications | Overwriting memory buffers to execute malicious code. | Secure coding practices, memory protection techniques (ASLR, DEP). |
Technical Mechanisms for Enhanced Effectiveness
Second-release POC exploits often incorporate advanced techniques to improve their success rate. These might include techniques like:
* Improved Evasion Techniques: Bypassing antivirus and intrusion detection systems (IDS/IPS) through techniques like polymorphism, code obfuscation, and stealthy network communication. This involves modifying the exploit’s code to make it harder to detect. For example, an exploit might use multiple layers of encryption to mask its malicious payload.
* Exploitation of Multiple Vulnerabilities: Chaining together multiple vulnerabilities to achieve a more significant impact. For instance, an initial XSS vulnerability might be used to gain access, followed by an RCE vulnerability to execute malicious code. This allows for a more powerful attack than exploiting a single vulnerability in isolation.
* Advanced Privilege Escalation: Techniques to elevate privileges from a low-level user account to a higher-level account, such as administrator. This often involves exploiting vulnerabilities in the operating system or applications. A successful privilege escalation could grant the attacker complete control over the system.
Hypothetical “POC Exploit Released 2” Code Structure
This hypothetical exploit targets a web application vulnerable to both SQL injection and XSS. The code is structured in a modular fashion for maintainability and flexibility.
The following bullet points describe the key functions within this hypothetical exploit:
* `SQLInjectionModule`: This module handles the SQL injection aspect, crafting malicious queries to extract sensitive data from the database. It includes functions for constructing queries, parsing the results, and handling potential errors.
* `XSSModule`: This module focuses on exploiting the XSS vulnerability to deliver a malicious payload to the victim’s browser. This might involve crafting a JavaScript payload that steals cookies or redirects the user to a phishing site.
* `PayloadDeliveryModule`: This module coordinates the delivery of the malicious payload, integrating both SQL injection and XSS functionalities. It handles the communication between the two modules and ensures the payload is delivered successfully.
* `DataExfiltrationModule`: This module handles the extraction and transfer of stolen data to a remote server controlled by the attacker. This could involve various methods like using HTTP requests or encrypted channels.
* `ObfuscationModule`: This module obfuscates the exploit’s code to make it harder to detect by security tools. Techniques like string encryption and code virtualization might be used.
Hypothetical Exploitation Scenario
This scenario illustrates the step-by-step process of a successful attack:
1. Vulnerability Identification: The attacker identifies a web application vulnerable to SQL injection and XSS.
2. SQL Injection Phase: The attacker uses the `SQLInjectionModule` to extract usernames and passwords from the application’s database.
3. XSS Payload Construction: The attacker crafts an XSS payload using the `XSSModule`, embedding it within a seemingly harmless link or form field.
4. Payload Delivery: The attacker uses social engineering or other techniques to trick the victim into clicking the malicious link or submitting the form.
5. Payload Execution: The XSS payload executes in the victim’s browser, giving the attacker control over the victim’s session.
6. Privilege Escalation (Optional): The attacker might attempt to escalate privileges to gain access to more sensitive data or system resources.
7. Data Exfiltration: Using the `DataExfiltrationModule`, the attacker extracts sensitive data, such as cookies, session tokens, and other valuable information.
Impact and Mitigation Strategies
A second release of a proof-of-concept (POC) exploit significantly amplifies the risk landscape. The initial release often serves as a wake-up call, prompting some organizations to patch vulnerabilities. However, a second release, potentially with improvements or targeting different systems, can catch many off guard, leading to widespread exploitation before adequate defenses are in place. This increased exposure can have severe consequences for businesses and individuals alike.
The impact of a “POC Exploit Released 2” scenario varies depending on the vulnerability exploited, the sophistication of the exploit, and the preparedness of affected organizations. A seemingly minor vulnerability can cascade into significant damage when leveraged effectively. For instance, a vulnerability initially thought to affect only internal systems might be adapted to target external-facing applications, leading to data breaches, service disruptions, and reputational harm. The second release often includes refinements, making it more effective at bypassing security measures.
Real-World Examples of Significant Impact
The 2017 WannaCry ransomware attack, while not strictly a “POC Exploit Released 2” scenario, serves as a relevant example. The initial exploit leveraged the EternalBlue vulnerability, leaked from the NSA. While Microsoft had released a patch, many organizations failed to update their systems. The subsequent widespread infection demonstrates the catastrophic impact of failing to address known vulnerabilities promptly. A hypothetical “POC Exploit Released 2” scenario could involve a refined version of EternalBlue, bypassing rudimentary security measures implemented after the initial attack, causing even greater damage. Similarly, the NotPetya outbreak, although not directly linked to a second POC release, highlights the devastating consequences of exploiting a known vulnerability on a large scale. The rapid spread and the significant financial losses suffered by organizations worldwide underscore the urgency of proactive vulnerability management.
Best Practices for Mitigating Risks
Effective mitigation strategies are crucial to minimize the impact of a “POC Exploit Released 2” scenario. These strategies should be a core component of any robust cybersecurity program.
- Proactive Patching: Implement a rigorous patch management system, ensuring timely updates for all software and hardware components. Automate patching where possible to reduce the window of vulnerability.
- Vulnerability Scanning and Penetration Testing: Regularly scan systems for known vulnerabilities and conduct penetration testing to identify and address potential weaknesses before attackers can exploit them. This proactive approach is far more effective than reacting to an exploit’s release.
- Security Information and Event Management (SIEM): Implement a SIEM system to monitor network activity and detect suspicious behavior. Early detection of malicious activity can significantly limit the damage caused by an exploit.
- Network Segmentation: Segmenting the network into smaller, isolated zones limits the impact of a successful attack. If one segment is compromised, the attacker’s ability to move laterally within the network is restricted.
- Incident Response Plan: Develop and regularly test an incident response plan to guide actions in the event of a security breach. A well-defined plan ensures a coordinated and effective response, minimizing downtime and data loss.
- Employee Training: Educate employees about phishing scams and other social engineering tactics. Many exploits rely on human error to gain initial access to systems. Investing in employee training can significantly reduce this risk.
Improving Vulnerability Management Programs
Organizations can significantly reduce the impact of exploits like “POC Exploit Released 2” by improving their vulnerability management programs. This includes investing in automated vulnerability scanning tools, implementing a centralized vulnerability management system, and integrating vulnerability data into the software development lifecycle (SDLC). A key aspect is prioritizing vulnerabilities based on their potential impact and likelihood of exploitation. This allows organizations to focus their resources on addressing the most critical risks first. Regular security audits and assessments are also vital to identify weaknesses and ensure the effectiveness of implemented security controls. Continuous monitoring and improvement of the vulnerability management program are essential to stay ahead of emerging threats.
The Role of the Security Community: Poc Exploit Released 2
Source: bleepstatic.com
The discovery and responsible disclosure of vulnerabilities is a complex dance involving various players, each with their own set of responsibilities and ethical considerations. The security community, encompassing researchers, vendors, and users, plays a crucial role in mitigating the risks posed by software flaws like the “POC Exploit Released 2” scenario. Their actions, or inactions, directly impact the overall security landscape.
The security research community acts as the first line of defense, often uncovering vulnerabilities through rigorous testing and analysis. These researchers, driven by a combination of intellectual curiosity and a desire to improve online safety, dedicate significant time and resources to identifying and reporting flaws. Their findings are invaluable, allowing vendors to patch vulnerabilities before they can be exploited on a larger scale. This proactive approach is far more effective and efficient than reactive measures taken after a widespread breach.
Security Researcher Responsibilities in Vulnerability Discovery and Disclosure
Security researchers have a significant responsibility in the vulnerability disclosure process. Their primary role is to identify vulnerabilities, thoroughly document them, and responsibly disclose them to the affected vendor. This involves providing sufficient detail to allow the vendor to understand and address the issue without unnecessarily revealing information that could be misused by malicious actors. The goal is to balance the need for public awareness with the need to prevent widespread exploitation. A crucial aspect is adhering to established responsible disclosure guidelines, which often involve a coordinated effort with the vendor to release patches and inform the public in a timely manner. Failure to do so can lead to severe consequences, including legal repercussions and reputational damage.
Stakeholder Responsibilities in Addressing POC Exploit Releases
The responsibilities of different stakeholders in addressing a POC exploit release, such as “POC Exploit Released 2,” are distinct yet interconnected. Security researchers are responsible for the initial discovery and responsible disclosure, emphasizing detailed information while minimizing the risk of misuse. Vendors bear the primary responsibility for patching vulnerabilities promptly and communicating effectively with users. They must prioritize timely remediation and clear communication about the vulnerability, its severity, and the steps users should take to protect themselves. Users, in turn, are responsible for updating their software regularly and maintaining a high level of security awareness. This collaborative approach is essential to effectively mitigating the risk posed by publicly released exploits.
Ethical Considerations Surrounding Public Release of POC Exploits
The ethical considerations surrounding the public release of proof-of-concept (POC) exploits are multifaceted. While the release of POCs can raise awareness and encourage faster patching by vendors, it also carries the risk of malicious actors leveraging the information to exploit vulnerable systems. The potential for widespread damage must be carefully weighed against the benefits of increased transparency. The debate often revolves around the balance between promoting security awareness and preventing harm. Responsible disclosure practices aim to strike this balance, prioritizing the safety and security of users while encouraging proactive vulnerability remediation. A key ethical question is whether the potential benefit of public awareness outweighs the potential harm caused by increased exploitation.
Hypothetical Dialogue: Researcher and Vendor
Researcher: “We’ve identified a critical vulnerability in your software, CVE-2024-XXXX, allowing for remote code execution. We’ve prepared a detailed report with steps to reproduce the issue and suggest mitigations. We’re proposing a 90-day disclosure window to allow you time to patch before public release.”
Vendor: “Thank you for bringing this to our attention. We’ll immediately initiate an investigation and work to develop a patch. We appreciate your responsible disclosure and will coordinate with you throughout the process to ensure a smooth and timely resolution.”
Future Trends and Predictions
The rapid evolution of technology and the increasingly interconnected nature of our digital world mean that the “POC Exploit Released 2” phenomenon is not a one-off event. We can expect to see more sophisticated attacks, faster exploit development cycles, and a constant arms race between attackers and defenders. Understanding the future trends is crucial for building resilient security systems.
The landscape of vulnerability disclosure and exploit development is poised for significant shifts. We’ll likely see a rise in automated exploit generation, fueled by advancements in artificial intelligence and machine learning. This automation will drastically reduce the time between vulnerability discovery and the availability of working exploits, shrinking the window of opportunity for patching. Furthermore, the increasing prevalence of software-defined everything (SDx) environments will present new attack vectors and complexities, demanding more proactive and adaptive security strategies.
Automated Exploit Generation and AI’s Role, Poc exploit released 2
The integration of AI and machine learning into the exploit development process is rapidly accelerating. Tools are emerging that can analyze vulnerability descriptions, automatically generate exploit code, and even test its effectiveness. This automation will lead to a faster release cycle for exploits, potentially overwhelming security teams’ ability to respond effectively. Imagine a scenario where a vulnerability is disclosed, and within hours, multiple automated tools generate and test working exploits, making patching a race against time. This automation will necessitate a shift towards proactive security measures, including automated vulnerability detection and patching systems.
Evolution of Vulnerability Management Strategies
The traditional “patch-and-pray” approach to vulnerability management will become increasingly inadequate. Organizations will need to adopt a more proactive and integrated approach, incorporating threat intelligence, automated vulnerability scanning, and continuous monitoring. We can expect to see a rise in the use of vulnerability prioritization systems that consider not only the severity of a vulnerability but also its exploitability and the potential impact of a successful attack. Think of companies like Microsoft, who are constantly refining their patch management systems and incorporating threat intelligence to prioritize vulnerabilities that pose the most immediate risk. This shift requires a move beyond reactive patching to a more predictive and adaptive security posture.
Hypothetical Future Scenario: A Sophisticated “POC Exploit Released 2” Event
Imagine a future where a critical vulnerability in a widely used cloud platform is disclosed. Within minutes, multiple automated exploit generation tools create and disseminate functional exploits. The vulnerability allows attackers to gain complete control of affected systems, leading to widespread data breaches and service disruptions. The speed and scale of the attack overwhelm traditional security responses. Organizations lacking robust automated patching systems and proactive threat intelligence face significant financial losses, reputational damage, and legal repercussions. This scenario highlights the urgent need for proactive vulnerability management and improved collaboration within the security community.
Improvements in Vulnerability Disclosure Practices
A more structured and coordinated approach to vulnerability disclosure is crucial. This includes:
- Establishing clearer guidelines for responsible disclosure, ensuring that vendors have sufficient time to patch vulnerabilities before public release of exploits.
- Developing standardized vulnerability reporting mechanisms that streamline the process and facilitate quicker response times.
- Promoting greater collaboration between researchers, vendors, and security professionals to share information and enhance collective security.
- Investing in research and development of automated vulnerability detection and remediation tools.
These improvements will create a more secure and resilient digital ecosystem by reducing the time between vulnerability discovery and mitigation.
Closing Summary
The release of a second POC exploit is a stark reminder of the ever-evolving cybersecurity landscape. It highlights the crucial need for proactive vulnerability management, responsible disclosure practices, and a collaborative approach between researchers, vendors, and users. While the technical details might seem daunting, the core message is simple: staying vigilant and informed is the best defense against the next big threat. The game of cat and mouse continues, but with knowledge and preparedness, we can tip the scales in our favor.



