Mozillas 0day investigative network – Mozilla’s 0Day Investigative Network: Ever wondered how Mozilla tackles those sneaky, zero-day vulnerabilities before they wreak havoc? It’s a high-stakes game of cat and mouse, involving a dedicated team of security experts who race against time to identify, analyze, and neutralize these digital threats before they can be weaponized. Think of it as a digital SWAT team, constantly on alert, ready to spring into action at a moment’s notice.
This intricate network operates behind the scenes, a silent guardian protecting millions of users from potential cyberattacks. From initial vulnerability reports to the deployment of critical security patches, the process is a complex dance of investigation, collaboration, and strategic communication. This deep dive will unravel the mysteries of Mozilla’s 0Day Investigative Network, revealing the inner workings of this crucial security operation.
Mozilla’s Security Response Team
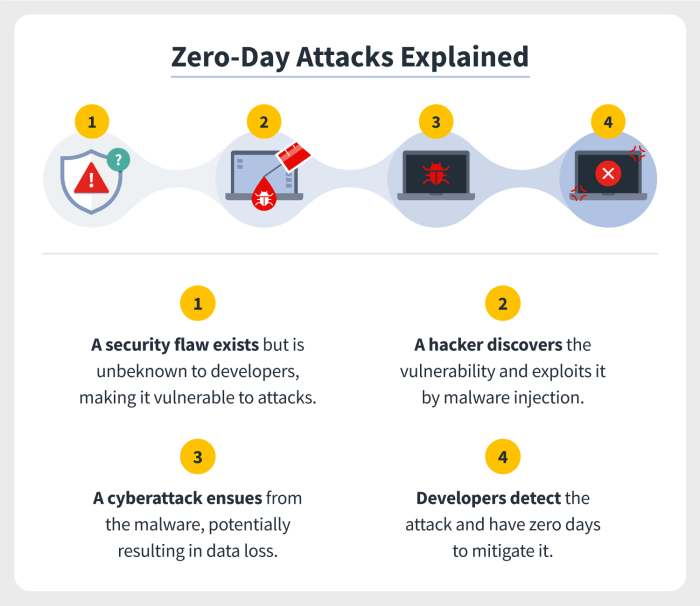
Source: norton.com
Mozilla’s commitment to user security is deeply ingrained in its operations. This commitment manifests most clearly in the work of its dedicated Security Response Team, a group responsible for identifying, analyzing, and mitigating security vulnerabilities, particularly the critical zero-day exploits that can compromise user data and privacy. Understanding their structure and processes is key to grasping Mozilla’s proactive approach to online safety.
Organizational Structure of Mozilla’s Security Team
Mozilla’s security team isn’t a monolithic entity. Instead, it’s a network of specialists working in coordinated fashion. While the precise internal structure isn’t publicly available in detail due to security concerns, we can infer a structure involving distinct groups focusing on vulnerability research, incident response, and software engineering. These groups likely collaborate closely, with clear communication channels ensuring rapid and effective responses to emerging threats. This collaborative approach allows for expertise in various areas to be efficiently leveraged. For example, researchers might identify a vulnerability, while the incident response team manages the communication and patching process, and engineers implement the necessary fixes within the Firefox codebase.
Roles and Responsibilities within the Security Response Process, Mozillas 0day investigative network
The process of handling a zero-day vulnerability involves several distinct roles. Vulnerability researchers are responsible for identifying and analyzing the vulnerability, detailing its impact and potential exploits. The incident response team is crucial in managing the communication with affected users and coordinating the release of security patches. Software engineers are responsible for developing and implementing the necessary code changes to fix the vulnerability. Legal and public relations teams manage the communication of vulnerabilities to the public, ensuring transparency and minimizing potential harm. Finally, a dedicated team likely handles the coordination of the entire process, ensuring efficient communication and collaboration across the various teams involved.
Workflow for Handling Reported Zero-Day Vulnerabilities
A simplified flowchart illustrating the typical workflow might look like this:
1. Vulnerability Report: A vulnerability is reported, either internally or externally (e.g., through a bug bounty program).
2. Triaging and Analysis: The report is reviewed, the vulnerability is verified, and its severity is assessed.
3. Patch Development: Software engineers develop a patch to address the vulnerability.
4. Testing and Validation: The patch is rigorously tested to ensure it effectively addresses the vulnerability without introducing new problems.
5. Patch Release: The patch is released to users through automatic updates or manual downloads.
6. Public Disclosure (if applicable): Information about the vulnerability and the patch is publicly released, often after a coordinated disclosure period to allow users time to update.
Comparison of Security Response Processes Across Major Browser Vendors
Direct comparisons of response times and internal processes across vendors are difficult due to the competitive nature of the industry and the sensitivity of security information. However, a general comparison can be made based on publicly available information and observed timelines.
| Vendor | Initial Response Time (Estimated) | Patch Release Time (Estimated) | Public Disclosure Policy |
|---|---|---|---|
| Mozilla | Varies, generally aims for rapid response | Varies depending on vulnerability severity | Generally follows a coordinated disclosure approach |
| Google (Chrome) | Known for rapid response | Relatively fast patch release | Generally follows a coordinated disclosure approach |
| Microsoft (Edge) | Rapid response, often integrated with Windows updates | Patch release frequency tied to Windows update schedule | Generally follows a coordinated disclosure approach |
| Apple (Safari) | Response times vary, often tied to OS updates | Patch release frequency tied to OS update schedule | Generally follows a coordinated disclosure approach |
The Investigative Process for Zero-Day Vulnerabilities
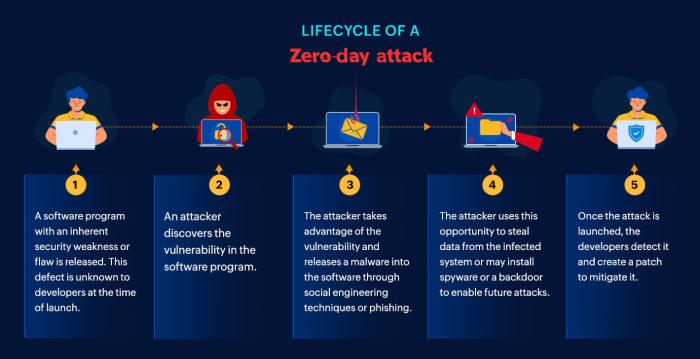
Source: manageengine.com
Uncovering zero-day vulnerabilities—flaws unknown to the software vendor—is a high-stakes game of digital cat and mouse. Mozilla’s Security Response Team (SRT) employs a rigorous process to investigate these reported vulnerabilities, ensuring the safety and security of its users. This process is crucial, as a single undetected zero-day could expose millions to significant risk.
The investigation begins the moment a credible report surfaces. This report might come from an external security researcher, an internal audit, or even a user encountering unusual behavior. The speed and thoroughness of the investigation are paramount, as the longer a zero-day remains unpatched, the greater the potential for exploitation.
Vulnerability Verification and Impact Assessment
Once a report is received, the SRT meticulously verifies the vulnerability’s existence. This involves replicating the reported issue within a controlled environment, confirming its reproducibility, and assessing its severity. The team employs various techniques, including fuzzing (automated testing to find unexpected inputs), static analysis (examining the code without execution), and dynamic analysis (running the code to observe its behavior). The goal is to determine the vulnerability’s impact—could it allow remote code execution, data theft, or denial-of-service? A detailed risk assessment is crucial for prioritizing the fix.
Root Cause Analysis and Exploit Mechanism Determination
With the vulnerability confirmed, the SRT delves into its root cause. This involves a deep dive into the affected codebase, identifying the precise flaw that allows exploitation. Reverse engineering techniques might be employed to understand how an attacker could leverage the vulnerability. The team carefully analyzes the exploit mechanism—the specific steps an attacker would take to exploit the flaw—to understand its complexity and potential impact. This detailed understanding is vital for crafting an effective patch that addresses the root cause, not just the symptoms.
Examples of Successful Zero-Day Vulnerability Investigations
Mozilla’s SRT has a long history of successfully investigating and mitigating zero-day vulnerabilities. While specific details of past investigations are often kept confidential to prevent future exploitation, the general approach remains consistent. Successful investigations often involve:
- Rapid Response to a Memory Corruption Vulnerability in Firefox: A reported vulnerability allowed attackers to execute arbitrary code by exploiting a memory corruption issue in the browser’s rendering engine. The SRT quickly reproduced the issue, pinpointed the flawed memory management routine, and developed a patch that addressed the root cause, preventing further exploitation. The response time was measured in days, not weeks.
- Mitigation of a Cross-Site Scripting (XSS) Vulnerability in Thunderbird: A vulnerability allowed attackers to inject malicious JavaScript code into emails, potentially stealing user credentials or installing malware. The SRT analyzed the vulnerability’s root cause—improper sanitization of user-supplied data—and developed a comprehensive patch that included robust input validation and output encoding. The team also conducted a thorough review of similar code segments in other Mozilla products to prevent future vulnerabilities of this type.
- Addressing a Privilege Escalation Vulnerability in Firefox’s Extension System: A flaw in Firefox’s extension management system allowed malicious extensions to gain elevated privileges, potentially compromising user data. The SRT meticulously analyzed the extension system’s architecture, identified the vulnerability’s source, and implemented a revised access control mechanism to prevent privilege escalation. This involved a comprehensive audit of existing extensions and a revised approval process for new ones.
Mitigation Strategies and Patch Development
The race against time to secure users’ data and systems is the defining characteristic of handling zero-day vulnerabilities. Mozilla’s response involves a complex interplay of immediate mitigation strategies and the rapid development and deployment of security patches. This process is crucial, as even a short delay can expose millions of users to significant risks.
The process of developing and deploying security patches for zero-day vulnerabilities is a high-pressure, multi-stage operation. It begins with the initial vulnerability report, often from external researchers or internal security audits. The vulnerability is then rigorously analyzed to determine its impact, exploitability, and potential reach. Once confirmed, the team works to develop a patch that addresses the root cause without introducing new instability or compatibility issues. This requires extensive testing across various operating systems and configurations to ensure it works seamlessly.
Patch Development Process
Developing a security patch isn’t a simple code fix; it’s a meticulous process that involves several key steps. First, developers isolate the vulnerable code segment and carefully craft a solution. This solution might involve modifying existing code, adding new security checks, or implementing entirely new functionalities. Then, rigorous testing begins, simulating various attack vectors to verify the patch’s effectiveness. This testing process frequently involves automated testing tools, but also manual review and penetration testing by security experts. Finally, the patch is integrated into the main codebase and undergoes further testing before release. The entire process, from identification to release, is heavily documented and reviewed at every stage to maintain the highest standards of quality and security.
Challenges in Patch Development
Creating effective and compatible patches is challenging. A patch needs to address the vulnerability completely without breaking existing functionality. Compatibility across various operating systems, hardware configurations, and browser extensions adds complexity. For instance, a patch might work flawlessly on a modern system but cause conflicts on older versions. This necessitates extensive testing and careful consideration of backward compatibility. Furthermore, the patch needs to be deployed seamlessly without disrupting user workflows. A poorly designed patch could cause more harm than good, leading to application crashes, data loss, or further security vulnerabilities.
Timeline for Patch Development and Deployment
The timeline for patch development and deployment varies greatly depending on the severity and complexity of the vulnerability. In critical situations involving widespread exploitation, the process can be incredibly fast, sometimes completed within days. However, for less critical vulnerabilities, the process can stretch to weeks. For example, a critical vulnerability that allows remote code execution might be patched and deployed within a week, while a less severe vulnerability might have a longer release cycle. This speed is crucial, as a faster response reduces the window of opportunity for attackers to exploit the vulnerability. Regular security updates and a well-established deployment infrastructure are essential for minimizing the response time.
Mitigation Strategies Before Patch Release
Before a patch is ready, Mozilla employs various mitigation strategies to minimize the impact of zero-day vulnerabilities. These include deploying temporary workarounds (such as disabling certain features or restricting access to vulnerable functionalities), releasing updated detection signatures for antivirus software, and actively monitoring for exploitation attempts. For instance, if a vulnerability is found in a specific browser component, Mozilla might temporarily disable that component or limit its functionality until a permanent patch is available. This approach reduces the attack surface and prevents attackers from exploiting the vulnerability until a permanent fix is deployed. These temporary measures, while not ideal, provide a critical layer of defense until the full patch is available.
Communication and Public Disclosure

Source: manageengine.com
Mozilla’s approach to communicating about zero-day vulnerabilities is a delicate balancing act. They need to protect users while also maintaining the integrity of their security efforts and avoiding unintended consequences, like providing attackers with more information than necessary. Transparency is crucial, but so is responsible disclosure.
The decision to publicly disclose information about a zero-day vulnerability is based on several key factors. These include the severity of the vulnerability, the potential impact on users, the availability of a patch, and the likelihood of exploitation. Mozilla prioritizes user safety and will generally opt for quicker disclosure if a vulnerability is actively being exploited in the wild or poses a significant risk. They also collaborate closely with other organizations and researchers to coordinate disclosures and ensure a unified response.
Mozilla’s Communication Strategy
Mozilla employs a multi-pronged communication strategy for zero-day vulnerabilities. This involves internal communication within their security team and with affected product teams, coordinated disclosure to relevant parties (like operating system vendors or other affected software providers), and finally, public announcement once a patch is available and appropriate. This phased approach ensures a controlled and effective response, minimizing disruption and maximizing user protection. For instance, if a vulnerability affects a widely used component, Mozilla might engage with other organizations to simultaneously release patches to reduce the window of vulnerability.
Criteria for Public Disclosure
Several criteria guide Mozilla’s decision on when and how to disclose zero-day vulnerability information publicly. Severity, the existence of active exploitation, the availability of a patch, and the potential for misuse are all critical factors. A high-severity vulnerability that is actively exploited will necessitate quicker and more prominent disclosure compared to a less severe vulnerability with no known exploitation. The goal is always to inform users effectively while minimizing the risk of malicious actors using the disclosed information.
Sample Press Release
FOR IMMEDIATE RELEASE
Mozilla Patches Critical Zero-Day Vulnerability in Firefox
[City, State] – [Date] – Mozilla today announced the release of a security update for Firefox that addresses a critical zero-day vulnerability (CVE-[Insert CVE Number Here]). This vulnerability could allow a malicious actor to [brief, non-technical description of the impact, e.g., execute arbitrary code on a user’s system].
The vulnerability was discovered by [mention the discoverer if appropriate and with their permission], and Mozilla worked quickly to develop and deploy a patch. Users are strongly urged to update their Firefox browser to the latest version ([version number]) immediately.
More information about the vulnerability and the patch can be found at [link to Mozilla security advisory].
Contact:
[Mozilla Press Contact Information]
Reporting a Potential Zero-Day Vulnerability to Mozilla
Developers who believe they have discovered a zero-day vulnerability in Mozilla products should follow these steps:
- Gather Evidence: Thoroughly document the vulnerability, including steps to reproduce it, the affected software versions, and the potential impact.
- Submit a Report: Submit a detailed report through Mozilla’s security bug bounty program or their dedicated vulnerability reporting system. The exact method will be clearly indicated on their website. Ensure the report includes all necessary information gathered in step 1.
- Maintain Confidentiality: Refrain from publicly disclosing the vulnerability until Mozilla has had a chance to investigate and release a patch. Public disclosure before a patch is available can significantly increase the risk to users.
- Collaborate with Mozilla: Work with Mozilla’s security team to provide any additional information they may need to address the vulnerability effectively.
Following these steps helps ensure a swift and coordinated response, protecting Mozilla users from potential harm. Mozilla values responsible disclosure and appreciates the efforts of security researchers who help them maintain the security of their products.
Collaboration and Partnerships: Mozillas 0day Investigative Network
Mozilla’s fight against zero-day vulnerabilities isn’t a lone wolf operation. Success hinges on a robust network of collaborators, sharing intelligence and resources to swiftly neutralize threats before they can wreak havoc. This collaborative approach is crucial, given the complexity and speed at which these vulnerabilities emerge and spread.
The effectiveness of Mozilla’s zero-day response directly correlates with its ability to foster and maintain strong partnerships. This involves not only internal coordination within the Security Response Team but also the cultivation of external relationships with security researchers, other tech companies, and even government agencies. The benefits far outweigh the challenges, creating a powerful ecosystem for proactive threat mitigation.
Key Partners and Collaborators
Mozilla’s zero-day response network includes a diverse range of partners. This network encompasses independent security researchers who often discover vulnerabilities first, other major tech companies facing similar threats (like browser vendors or operating system developers), and government agencies involved in cybersecurity initiatives. These partnerships allow for the rapid dissemination of critical information, leading to faster patch development and deployment. For example, collaboration with other browser vendors ensures that a patch for a shared vulnerability is simultaneously rolled out across different platforms, maximizing its impact and minimizing the window of vulnerability.
Benefits and Challenges of Collaboration with External Security Researchers
Collaborating with external security researchers offers several significant advantages. Researchers often possess specialized knowledge and cutting-edge techniques for identifying vulnerabilities, providing a fresh perspective and enhancing Mozilla’s detection capabilities. Their independent analysis helps validate findings and ensures a more robust and thorough assessment of the threat. However, challenges exist. Managing communication and coordinating disclosure timelines with numerous researchers requires careful planning and well-defined processes. Maintaining confidentiality and protecting sensitive information until a patch is ready is also paramount. Establishing clear communication protocols and using secure channels for information exchange are crucial to address these challenges.
Mechanisms for Coordinating Vulnerability Disclosure and Patch Deployment
Mozilla utilizes several mechanisms to ensure smooth coordination during vulnerability disclosure and patch deployment. These include established communication channels, such as secure email or dedicated communication platforms, for direct and timely interaction with partners. Pre-arranged disclosure timelines help manage expectations and ensure a coordinated rollout of patches. Regular meetings and information-sharing sessions further strengthen collaboration and facilitate proactive threat mitigation. A well-defined vulnerability disclosure policy provides a clear framework for how information is shared and managed, ensuring transparency and accountability throughout the process. This policy Artikels the responsibilities of all parties involved, fostering trust and mutual understanding.
Information Sharing Agreements and Efficient Response
Formal information sharing agreements (ISAs) are vital in streamlining the response to zero-day threats. These agreements Artikel the responsibilities of each partner, including confidentiality obligations, disclosure timelines, and communication protocols. ISAs help to foster trust and transparency, allowing for the rapid and efficient exchange of critical information. By clearly defining the roles and responsibilities of all parties, ISAs reduce ambiguity and streamline the process of vulnerability disclosure and patch deployment. This coordinated approach ensures that patches are released simultaneously across different platforms, minimizing the window of vulnerability and maximizing the impact of the mitigation efforts. For instance, a well-defined ISA could stipulate that a vulnerability is disclosed to all participating parties simultaneously, allowing for coordinated patch releases across different operating systems and software versions.
The Impact of Zero-Day Vulnerabilities on Mozilla’s Reputation and User Trust
Zero-day vulnerabilities represent a significant threat to Mozilla, impacting not only its users but also its hard-earned reputation and the trust placed in its products. A successful exploit can lead to widespread data breaches, financial losses for users, and a severe erosion of confidence in Mozilla’s security practices. The consequences can ripple far beyond the immediate impact of the vulnerability itself, affecting long-term user loyalty and the company’s overall market position.
The potential consequences of a major zero-day exploit are far-reaching. Imagine a scenario where a sophisticated attack compromises millions of Firefox users, allowing malicious actors to steal sensitive information like passwords, financial details, or even control users’ systems. The resulting public outcry, negative media coverage, and potential legal repercussions could be devastating. Such an event would severely damage Mozilla’s reputation as a trustworthy steward of user data and a provider of secure browsing technology. This could lead to a significant drop in user base, impacting advertising revenue and overall market share.
Mozilla’s Response to Previous Zero-Day Incidents and Their Impact
Mozilla has a documented history of addressing zero-day vulnerabilities. While specific details of many incidents are kept confidential for security reasons, their public responses generally follow a pattern: rapid investigation, patch development and deployment, and transparent communication with users and the security community. For example, in instances where vulnerabilities have been discovered and exploited, Mozilla has quickly released updates to address the flaws. These rapid responses, while sometimes imperfect, have generally been met with understanding from the user base, demonstrating the importance of swift action and open communication in mitigating the negative impacts. However, the impact of each incident varies based on factors such as the severity of the vulnerability, the scale of exploitation, and the effectiveness of Mozilla’s response. A slower response or a less effective patch could lead to significantly greater damage.
Best Practices for Maintaining User Trust During Security Threats
Maintaining user trust during security threats requires a multi-pronged approach. Proactive security measures, including rigorous code reviews and penetration testing, are crucial for preventing vulnerabilities in the first place. A robust vulnerability disclosure program, encouraging ethical hackers to report flaws responsibly, is equally important. When vulnerabilities are discovered, rapid and transparent communication with users is essential. Clear, concise updates on the situation, including the nature of the vulnerability, the steps taken to address it, and the timeline for deploying a patch, help maintain trust and demonstrate accountability. Openly acknowledging shortcomings and outlining plans for improvement further solidifies a commitment to user security. Finally, actively engaging with the security community, sharing information and collaborating on solutions, demonstrates a commitment to collective security and reinforces trust.
Hypothetical Scenario: A Zero-Day Vulnerability and Mozilla’s Response
Let’s imagine a hypothetical scenario: a zero-day vulnerability in Firefox’s rendering engine allows attackers to inject malicious code simply by visiting a compromised website. This vulnerability is quickly exploited, resulting in thousands of user accounts being compromised. Mozilla’s response would involve immediately forming an incident response team, rapidly investigating the root cause, and working tirelessly to develop a patch. They would simultaneously issue a public advisory, urging users to update their browsers immediately. Transparency would be key – regular updates on the progress of the patch development and deployment would be shared via their blog and social media channels. Mozilla would also coordinate with law enforcement and other security organizations to identify and neutralize the attackers. While the initial impact would undoubtedly be negative, a swift and effective response, coupled with transparent communication, would be crucial in mitigating long-term damage to Mozilla’s reputation and user trust. The focus would be on regaining user confidence by demonstrating their commitment to security and accountability.
Outcome Summary
Mozilla’s 0Day Investigative Network isn’t just about patching holes; it’s about proactive defense and fostering a culture of security. Their collaborative approach, combining internal expertise with external partnerships, underscores a commitment to digital safety. While the fight against zero-day vulnerabilities is a continuous battle, Mozilla’s dedication to transparency and rapid response provides a crucial layer of protection in the ever-evolving landscape of online threats. Understanding their methods gives us all a better appreciation for the unseen efforts that keep our digital world a little safer.



